Not sure if what's you're looking for but...
If you are looking at ways to use MFA to open a session on a Windows 10 or 11 machines using more than just a password, there are three supported methods:
- Smartcard (as suggested by @Philippe Levesque ). The user uses a PIN and its smartcard to open a session. It will require you to deploy a PKI and users will needs needs the smartcard as well as a physical reader attached to their device. It's a bit legacy but that sill works.
- Windows Hello for Business, the user uses biometrics, and/or a PIN to open a session. Although there are ways to make it work for independently of Azure AD the recommended deployments will require the user to be synchronized in Azure AD and have an MFA method register on the account.
- FIDO2, the user uses a FIDO key to open a session. Like for Windows Hello for Business, it will require the user to be synchronized in Azure AD.
Although it can be challenging to configure, you can set your account to log in only with those methods.
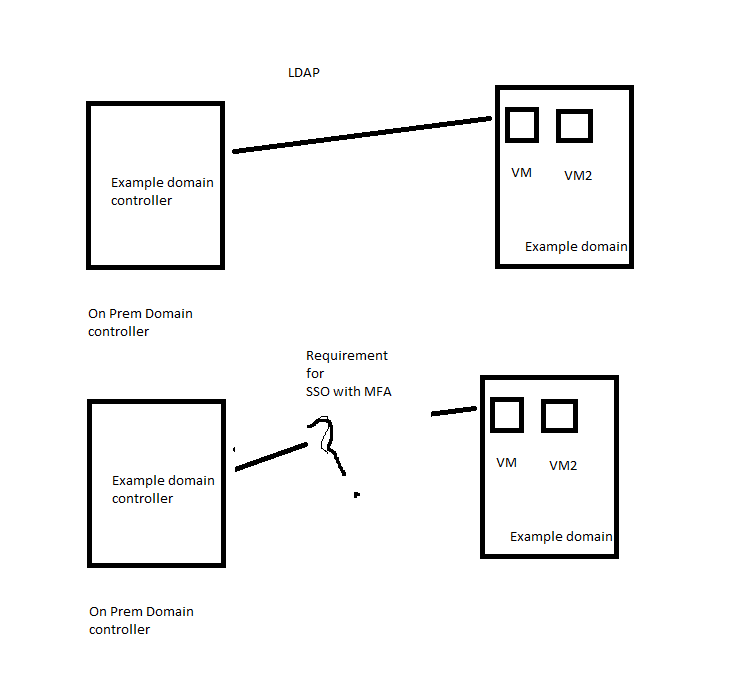
You can also protect On-Premises applications with Azure AD MFA. Again, assuming your identities are synched in Azure AD and have MFA. Using Azure AD Application Proxy, you can public application externally but also just integrate with Azure AD. Essentially your application becomes visible in Azure AD and you can trigger MFA based on Conditional Access Policies. That requires the users to use the correct URL to access the app though. And that's not MFA handled by the on-prem AD, it's MFA for the applications. So in that case AD doesn't know what's happening (unlike the 3 methods suggested above). But sometimes what you need is MFA when you access the data, so it might fit the bill.
If you are looking at ways to do MFA for VPN (or anything using RADIUS) you can use the Azure AD MFA Adapter for NPS. But now the recommendation is to integrate the VPN clients/servers directly with Azure AD (check the guide here and look for your remote access product) to get the MFA and other security features (such as Conditional Access Policies).
Then you have third-party products allowing you to integrate with Windows in different ways. I'll let the community chime in on those :)