Hi @Matt Browne
unfortunately by default, public access is disabled by default, and you cannot enable it, the App-assigned address option is grayed out and you lose public access.
Best
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
I'm trying to configure an app service such that it has a private link setup into our VPN enabled vnet but also allow public access (e.g. to allow front door and our devops agents access).
The docs (https://learn.microsoft.com/en-gb/azure/app-service/networking/private-endpoint) note that "by default" public access is disabled, to me that sounds like it is possible to not have the default, is that actually possible?
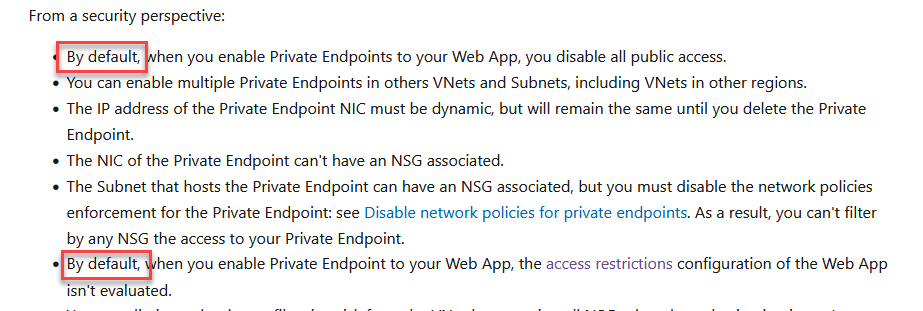
I'd rather not route everything through our vnet (using hub and spoke design) because to my mind that adds a single point of failure we don't need, e.g. having front door connect to the app service over the MS backbone means it isn't reliant on my vnet infrastructure. But the vpn access is useful for internal access direct to the app service.

Hi @Matt Browne
unfortunately by default, public access is disabled by default, and you cannot enable it, the App-assigned address option is grayed out and you lose public access.
Best