Hi,
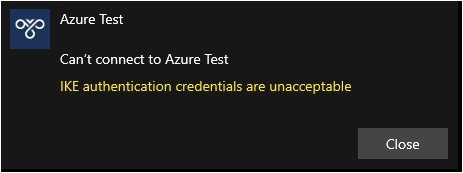
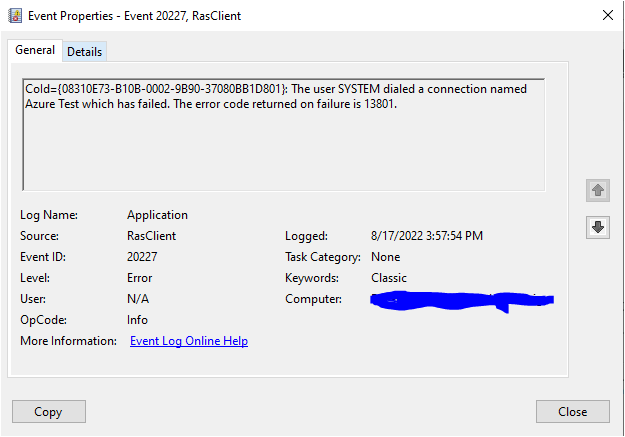
The error code you are getting (13801) indicates an issue with certificate authentication, Microsoft's documentation says:
"Verify that the VPN client connects by using the FQDN of the VPN server as presented on the VPN server's certificate."
https://learn.microsoft.com/en-us/windows-server/remote/remote-access/vpn/always-on-vpn/deploy/always-on-vpn-deploy-troubleshooting
With your configuration, the subjectName on the certificate presented (from the VPN Gateway) will never match the address you are connecting to (TM Front-end). I'm not aware of any way to bypass this check within Windows. You could verify that this is the issue by creating a generic CNAME DNS record which points to the your VPN gateway and attempting to connect to that, I suspect you will get the exact same error.
One thing you could try is adding your Traffic Manager DNS address as a Subject Alternate Name on VPN Gateway Certificate, if you have a custom cert configured.
You may need to use an alternate method to direct end-users to the correct VPN gateway, I'd suggest different MEM/SCCM policies for machines in different locations.
Kind regards,
Tristan