Hi @Ariel Gonzalez
Did you allow traffic forwarder?
Can you review this article to compare it with your environment?
https://thewindowsupdate.com/2020/12/11/using-azure-firewall-as-a-network-virtual-appliance-nva/
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.

Today I was trying to do something that I thought would be very simple and it was to make my own NVA so devices from different VNets/subnets could reach the internet while maintaining traffic control through the NVA.
Currently I've set up 3 different VNets in a hub-and-spoke fashion. I've already configured VNet peering from the spokes to the hub and I was able to successfully communicate between spokes through the NVA using it as a default route for each spoke. Here are my routes:
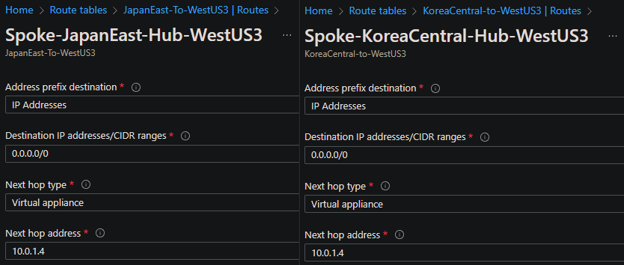
At first, I set up the destination IP address/CIDR in a more specific way, defining the destination subnet at the other side instead of 0.0.0.0/0 and it worked nicely while maintaining internet connection. After that I configured it as you can see in the screenshots to use the NVA as my gateway to the internet but that’s when I started getting very confused.
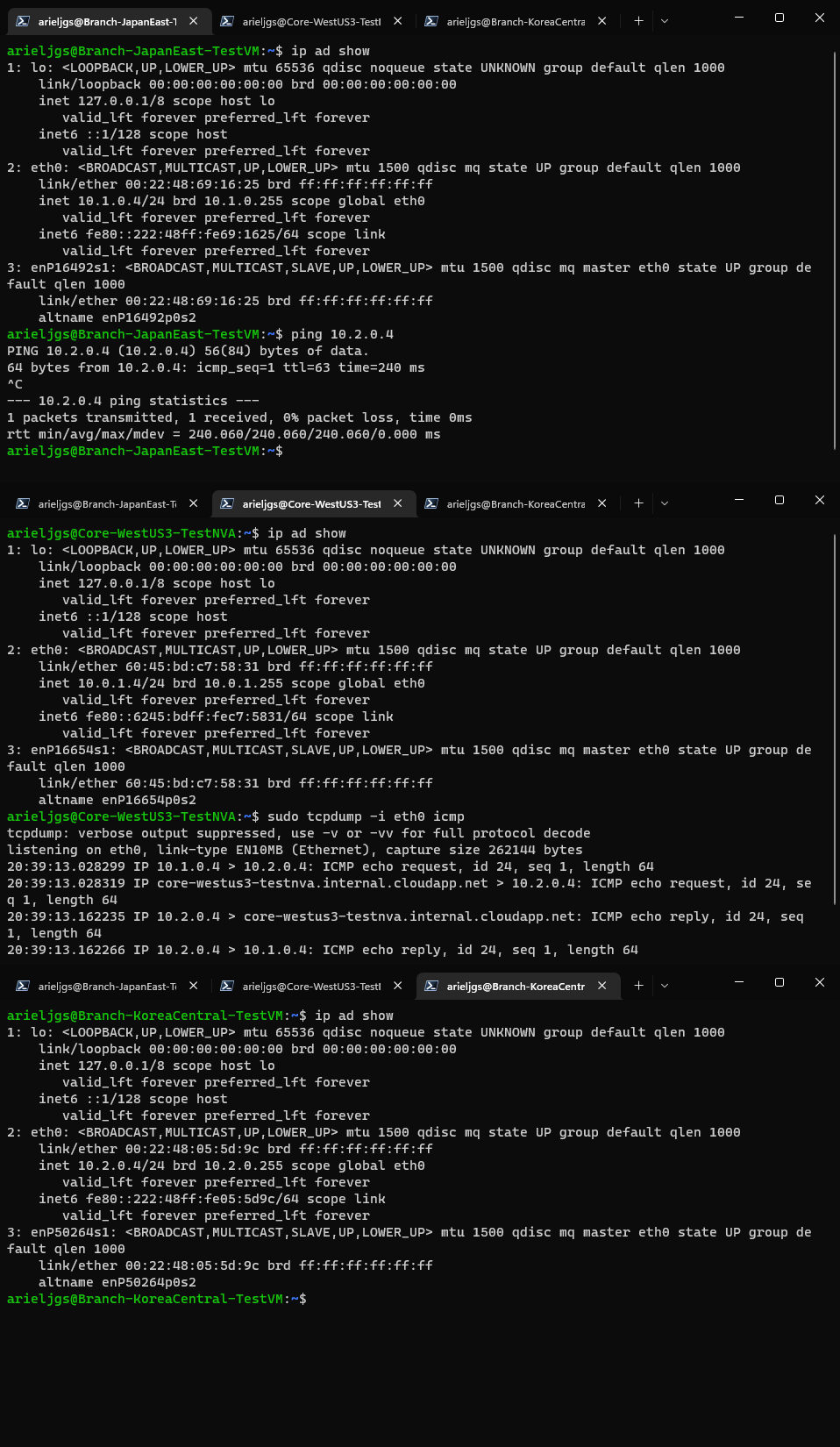
With this configuration the NVA is not even able to see traffic that the spokes send over to the internet, only traffic between spokes. Here are some basic connectivity tests that I’ve made:
Traffic between spokes working perfectly:
Traffic sent to the internet is not even seen by the NVA:
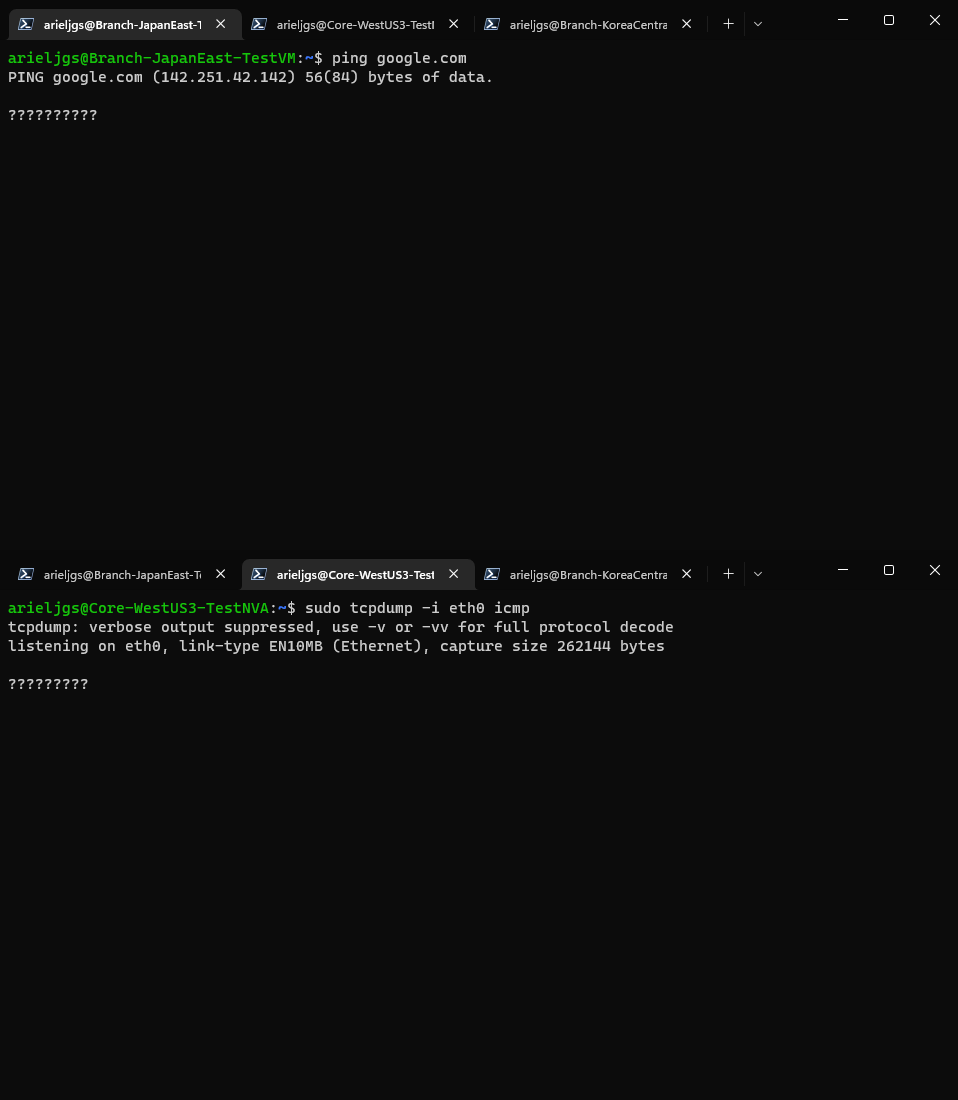
I’ve read through the documentation that when you need to communicate to the internet through the NVA you must proxy or NAT internal traffic to your own NVA internal IP address, then it is sent to Azure’s default gateway but as you can see I’m not able to get any traffic from the spoke.
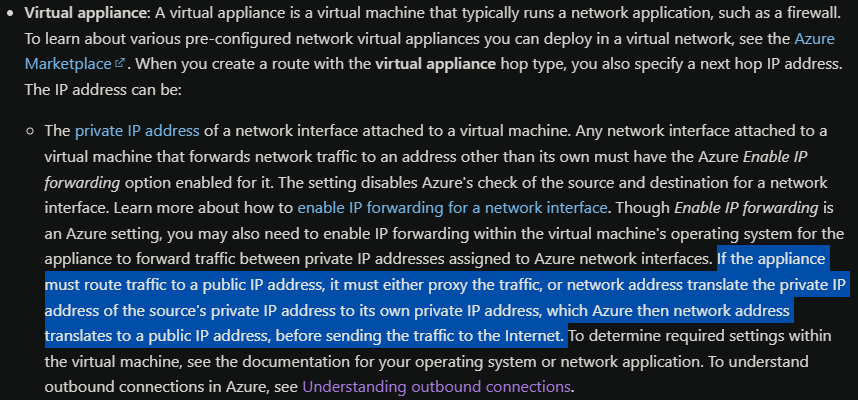
Just in case (because I can’t see any traffic) I set up some IP tables to NAT the source internal network to the NVA’s private address but it didn’t work either:
iptables -t nat -A POSTROUTING -s 10.1.0.0/24 -o eth0 -j MASQUERADE
iptables -t nat -A POSTROUTING -s 10.2.0.0/24 -o eth0 -j MASQUERADE
I’ve also seen these requirements in the documentation, and I think I’ve them all, but I could be wrong:
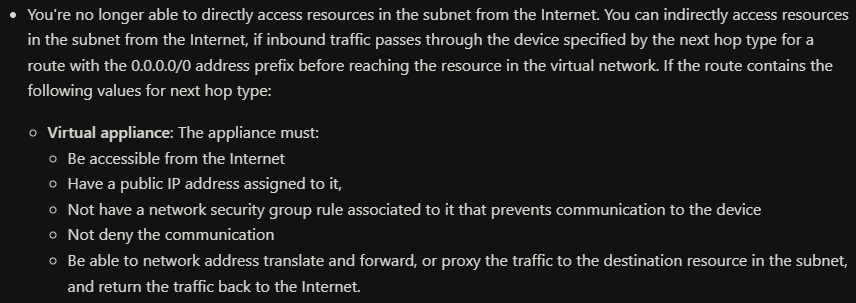
Can someone please point me in the right direction? I’ve been trying so hard to make this work and after hours of trying different things I’m still not able to see any traffic from the spokes to the internet or make any successful connection to the internet at all.

Hi @Ariel Gonzalez
Did you allow traffic forwarder?

Can you review this article to compare it with your environment?
https://thewindowsupdate.com/2020/12/11/using-azure-firewall-as-a-network-virtual-appliance-nva/

Hello @Ariel Gonzalez
Thank you for the post.
@Jackson Martins hi buddy : )
I just wanted to add a couple of observations for this case scenario.... One thing that brought my attention was that you were mentioning that you are you using an NVA(Network Virtual Appliance) so, based on your response this is your NVA "ubuntu machine as my NVA"
If this Ubuntu is acting as your NVA device and it is hosted as your HUB on this Hub-and-Spoke topology (Please any of your correct me if I am mistaken)
I wonder if this is set up as a Routing device or a Stateful/stateless Firewall... Which is one the role planned?
If it is acting as your FW device... I have 2 questions for this scenario which are:
Do you have security zones configured?
Do you configure any intra/inter security rule to allow traffic from different security zone? Or Any PBF rule??
Moreover, If it is your FW device or Router Device... Did you configure any VRF/Routing instance?
Finally, This other concern that I have is.... Have you checked your forwarding table as well?
Looking forward to your feedback,
Cheers,
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.