
Hi,
to answer to myself:
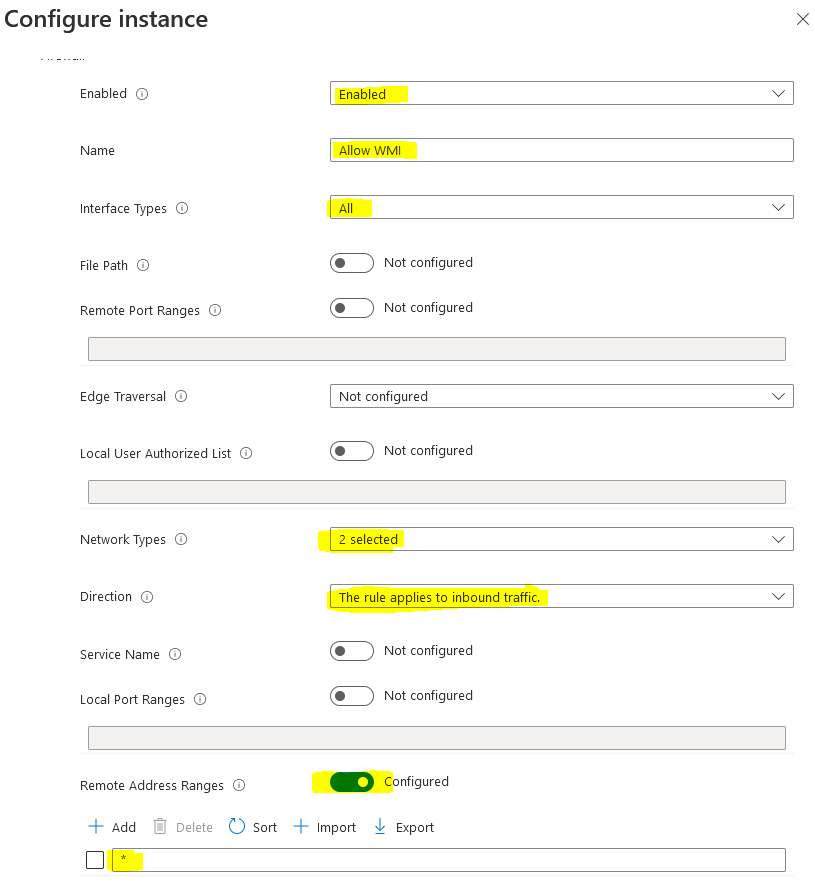
In screenshot nr.1 under "Network Types" I have selected FW_PROFILE_TYPE_DOMAIN and PRIVATE.
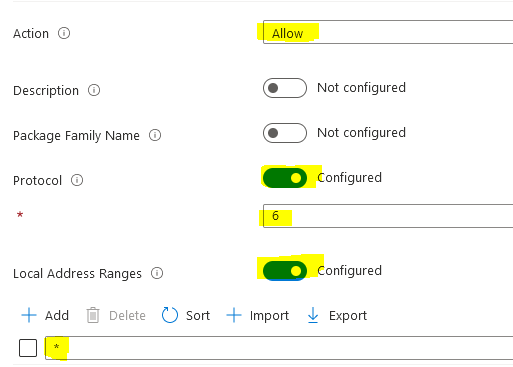
Protocol 6 can be found in windows local firewall under "advanced settings":

Cheers!
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.

Hi,
I would like to know how to setup an allow rule for Windows Management Instrumentation (WMI-in), aka this:

into Endpoint Firewall:
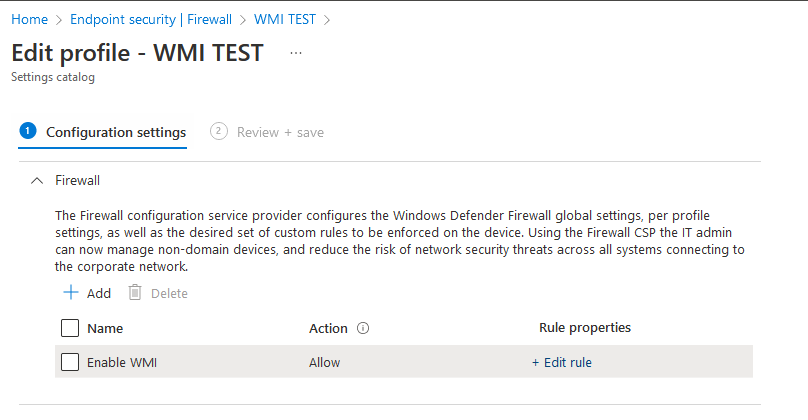
I dont know why but the interface is complicated and i cannot just simply "transfer" the rule from client to Endpoint.
I have tried also the migration tool (https://learn.microsoft.com/en-us/mem/intune/protect/endpoint-security-firewall-rule-tool) but the PS is hanging about 20min as i am writing this so that is a no go.
Thank you


Hi,
to answer to myself:


In screenshot nr.1 under "Network Types" I have selected FW_PROFILE_TYPE_DOMAIN and PRIVATE.
Protocol 6 can be found in windows local firewall under "advanced settings":

Cheers!
We're battling the same issue...
I think I'm missing something, how exactly do we get to screenshot #1? We've tried ""Network Types" I have selected FW_PROFILE_TYPE_DOMAIN and PRIVATE." but don't see the same options.
Can you please explain it as you would to a 5 year old. I'd really appreciate it.
Thank you!

So Konrad, if i understood you correctly you are wondering how to get to MY 1st screenshot in my ORIGINAL question.
When this is the case then you need to create or edit an existing policy in Endpoint Manager -> Endpoint Security - > Firewall
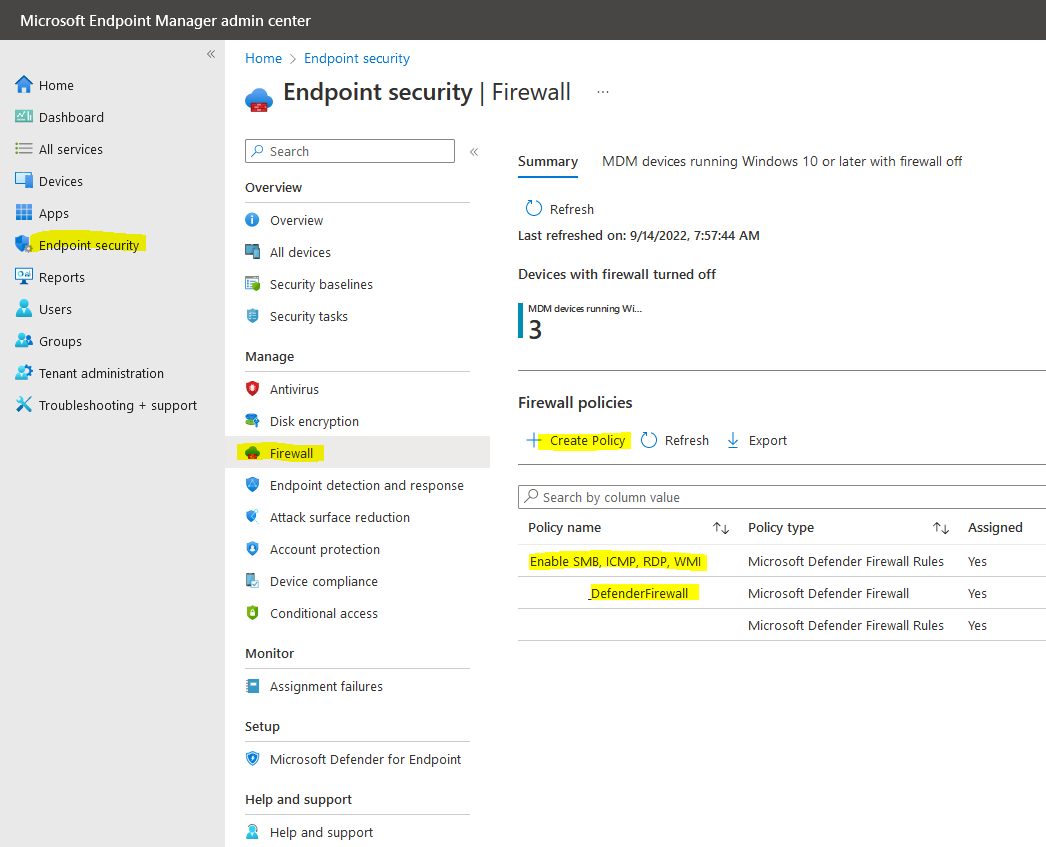
If you are referring to my screenshot in my ANSWER then:
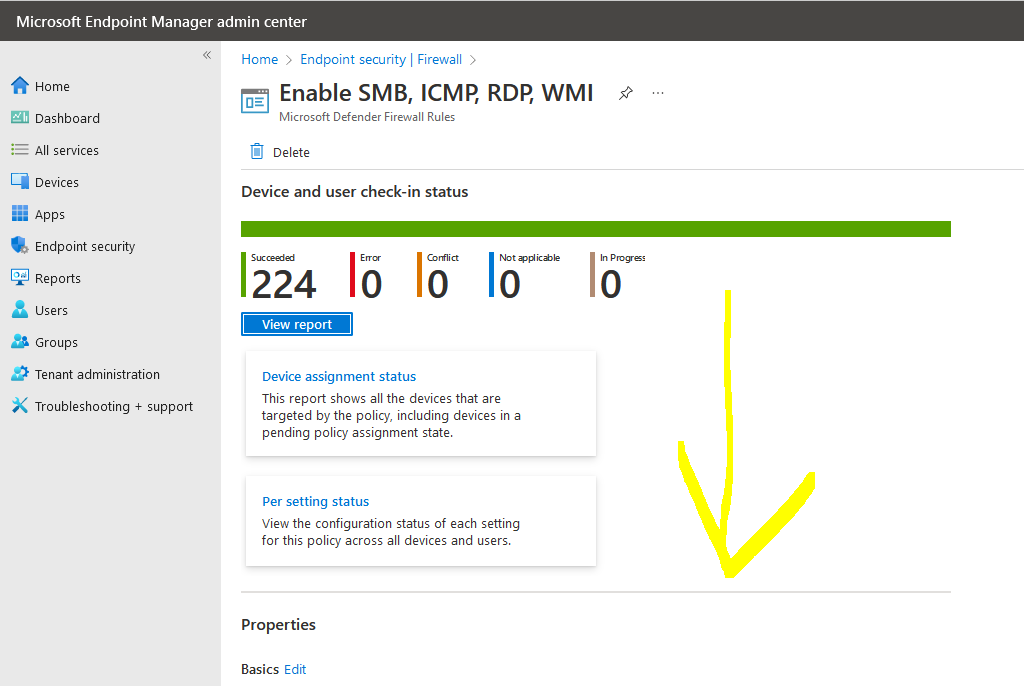
You click on your existing rule:

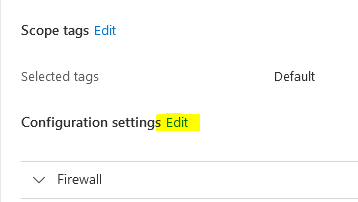
Scroll down until you see "configuration settings"->Edit:
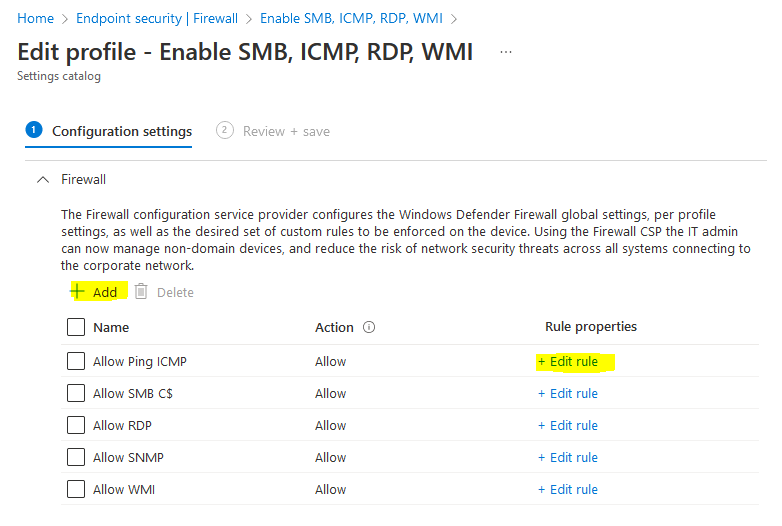
After you click edit your are presented with the possibility to add your rules or edit the existing ones:
editing an existing rule or creating a new one - it is all the same and then you will be on the correct path to "configure instance" like in my answer:
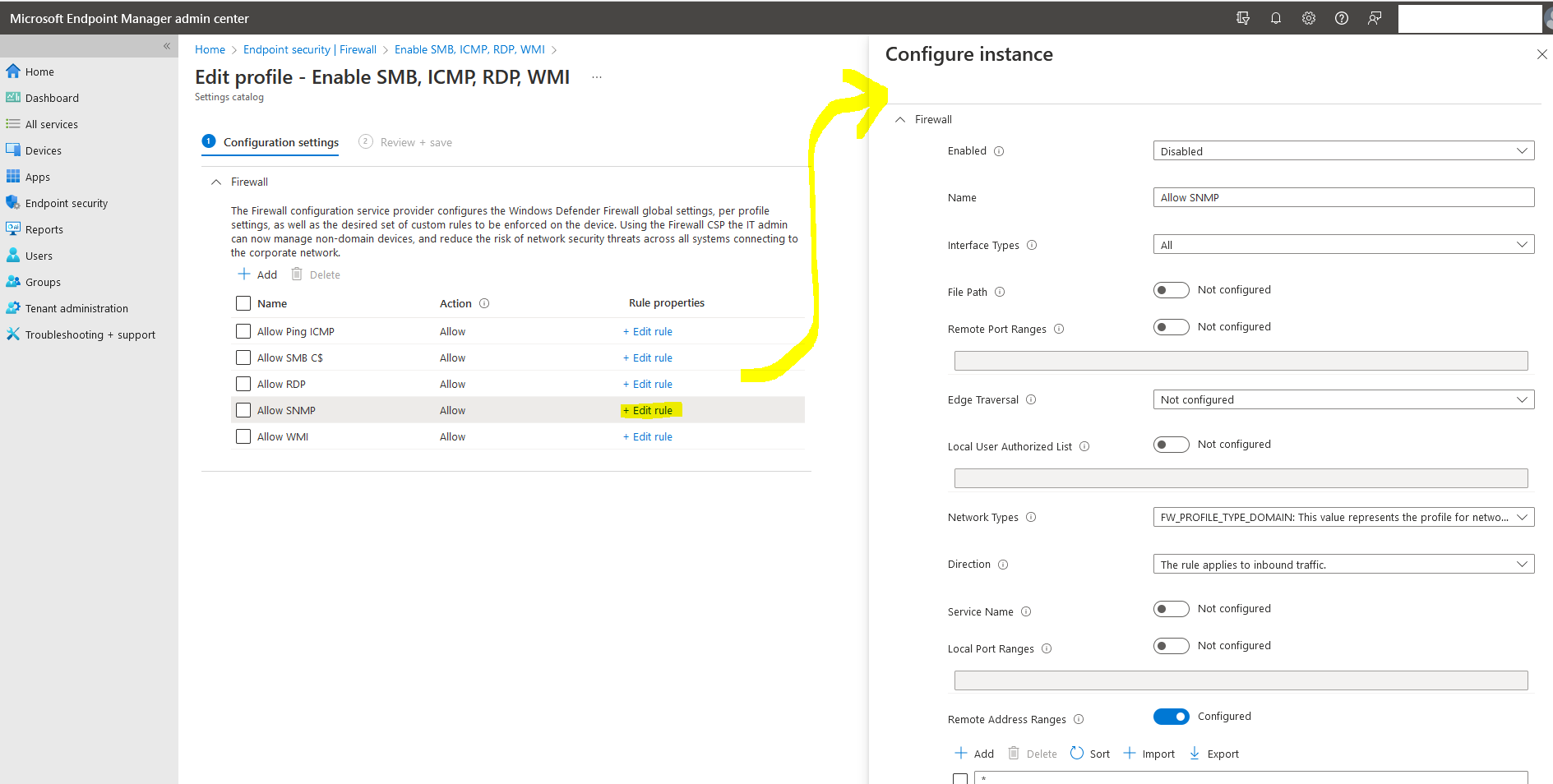
Cheers!
Very much appreciated Sir! Thank you!
Will be implementing this on Friday. Hopefully the Nessus scan goes without a hitch after these changes.
Came across this while looking for an answer, and just want to note that in your screenshots you are really just creating an "any any" rule for TCP. Protocol 6 is TCP, not WMI specifically. This would be opening pretty much everything up, and not what you would likely want to do.
I ended up exporting a GPO policy with the WMI set there, and then used the group policy analytics tool to see what to set. In the end, these are the settings I have and feel comfortable its locked down in intune and seems to have worked for me.
set to enabled
interface types all
filepath: %SystemRoot%\system32\svchost.exe
then network types I just did Domain.
set the local port ranges to 135,49152-65535
Set a Description to something that made sense to me
Set the direction to inbound traffic
Enabled protocol, set the protocol to 6
Enabled service name, set to "winmgmt" (this was found by looking through the output of Get-Service in powershell on my local pc)
I set my remote address range to just the IP of the server I wanted WMI access