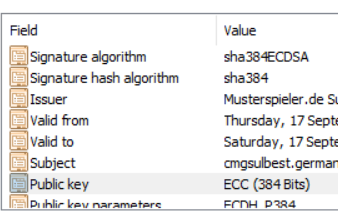
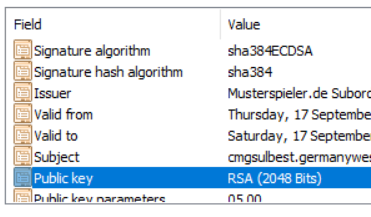
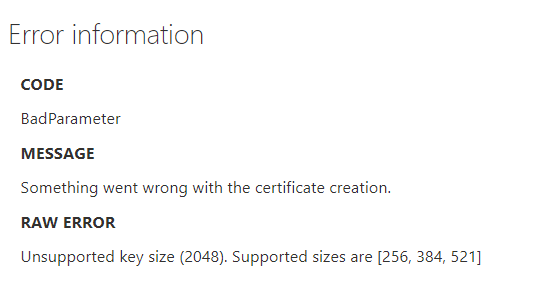
Ok, I was able to do it today. The following certificate can be uploaded successfully. Redoing the CA and retracting my steps and recreating all certificates was a pain, but apparently worth it. Apparently I selected the wrong algo somewhere down the setup. These are the exact same certificate templates, these were not touched. Seems I somewhere configured ECDSA to be the default instead of ECDH.
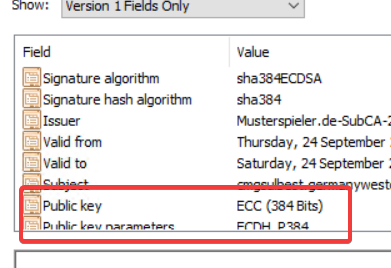
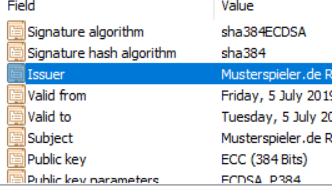
Root now looks like this:
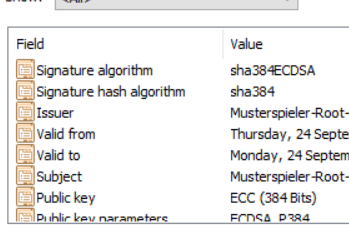
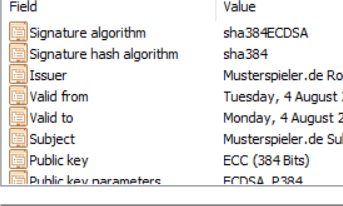
And SubCA like this:
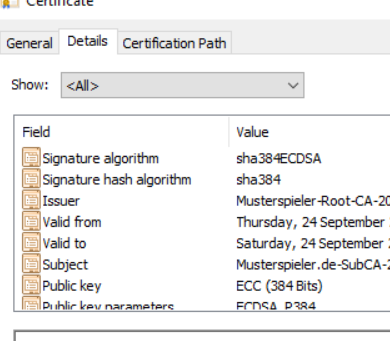
So as long as the customers didn't do the same mistakes I did (wherever these were made), this works.
Additional Info:
- Root CA and Sub CA Registry Info 1+2 (EncryptionCSP and CSP) - however according to the registry backup these are the same as before
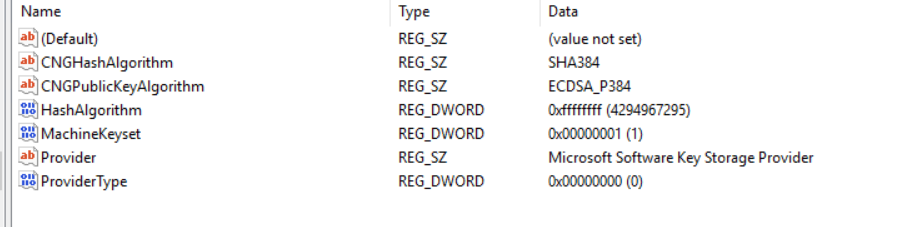
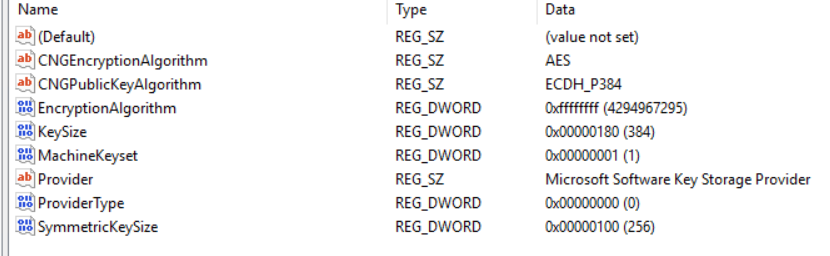
- The template now has the following settings available (where it only had ECDSA before)
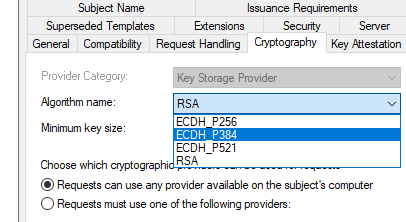
Only issue that still remains, but is unrelated to key vault is the MEMCM Console crashing when using an ECDH_P384.
This topic should be answered with this. Thanks for your support.