Whats the exact message and when do you see it?
It sounds normal however if its letting you continue and more of a warning then a blocker.
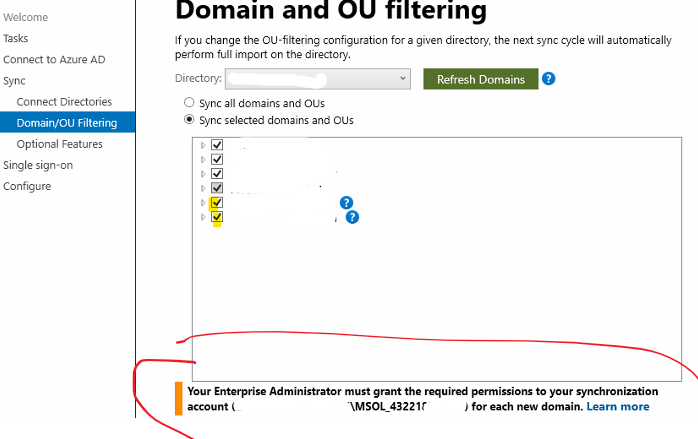
You're Enterprise Administrator must grant the required permissions to your synchronization account

I have an AD Connect setup with two forests. Each forest has it's own MSOL_ service account. When adding a new subdomain I am getting a message about ensuring the MSOL_ service account has the correct permissions. It is asking this of the MSOL_ account in the separate Forest.
I feel like this error is probably a non issue but wanted to reach out if others had experienced this.
6 answers
Sort by: Most helpful
-
 Andy David - MVP 145.6K Reputation points MVP
Andy David - MVP 145.6K Reputation points MVP2022-09-01T17:23:41.373+00:00 -
 JimmySalian-2011 42,071 Reputation points
JimmySalian-2011 42,071 Reputation points2022-09-01T17:35:10.823+00:00 Hi Computer,
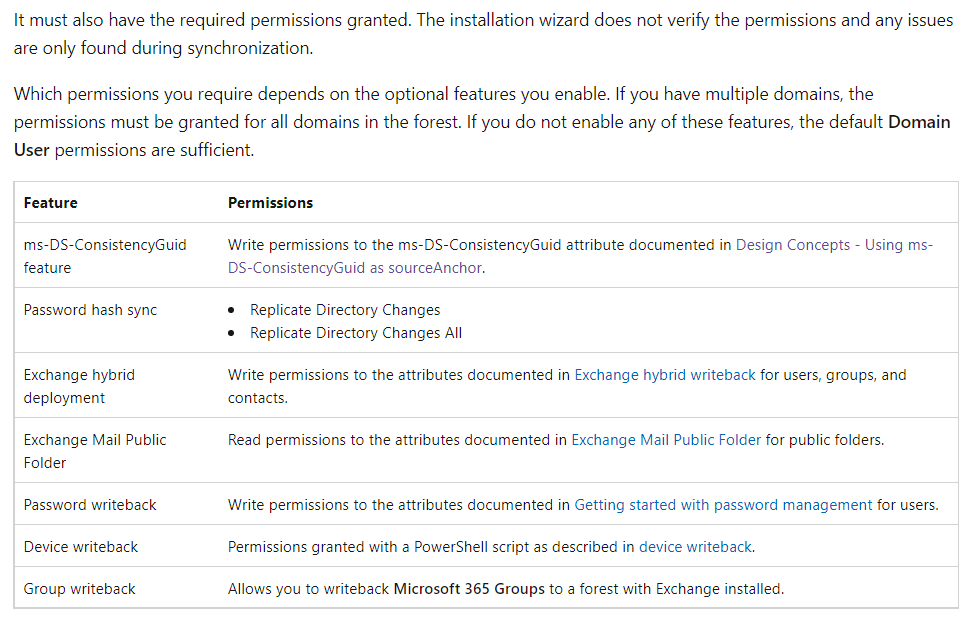
Not sure what type of installation you used express or custom? If Express installation the configuration will take care of all the permissions and access required for that MSOL account, if custom installation you will need to make sure it has appropriate permissions.
So in short I would not worry if you are not blocking anything on the OUs, for Azure AD Connect Express installation, an automatically generated account (MSOL_nnnnnnnnnn) is created in Active Directory with all the necessary permissions, so there’s no need to use ADSyncConfig module unless you have blocked permissions inheritance on organizational units or on specific Active Directory objects that you want to synchronize to Azure AD.
If you are not sure on the MSOL account and would like to confirm follow the cmdlets for this configuration - reference-connect-adsyncconfig
==
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.
-
 ComputerHabit 861 Reputation points
ComputerHabit 861 Reputation points2022-09-01T18:26:11.693+00:00 I just tried to add the sub domains and ignore the error. It let me complete the wizard but it didn't add the domains.
When I went back to edit the configuration again the boxes were unchecked. Just did it twice.
So I guess the MSOL account from the other forest truly does need permissions!
Uggg!
-
 JimmySalian-2011 42,071 Reputation points
JimmySalian-2011 42,071 Reputation points2022-09-01T19:47:56.597+00:00 If it is a custom install you will have to provide permissions and access to the top level domain so it filters down the OUs.
==
Please "Accept the answer" if the information helped you. This will help us and others in the community as well. -
 ComputerHabit 861 Reputation points
ComputerHabit 861 Reputation points2022-09-02T18:15:51.32+00:00 I ran this through a lab and was able to reproduce the error.
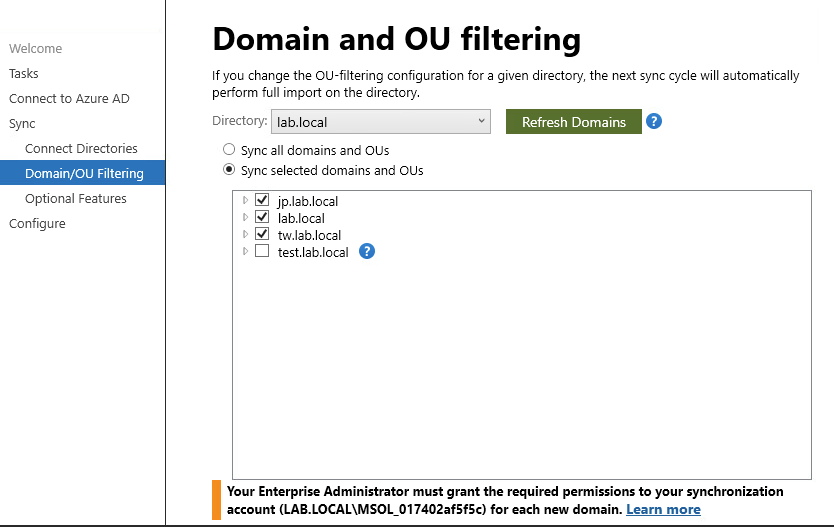
The link in the error message takes you to: https://learn.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-configure-ad-ds-connector-account
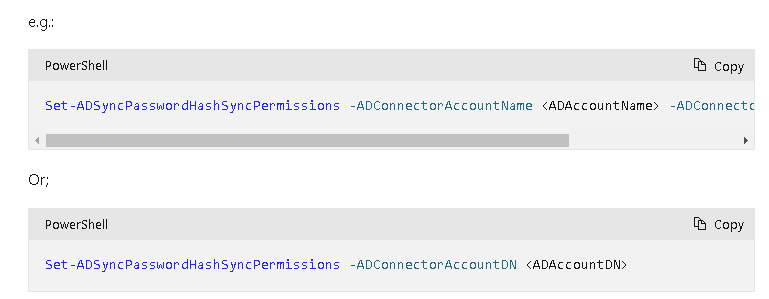
Following the instructions I ran:
Set-ADSyncBasicReadPermissions -ADConnectorAccountName <String> -ADConnectorAccountDomain <String> [-SkipAdminSdHolders] [<CommonParameters>]and
Set-ADSyncMsDsConsistencyGuidPermissions -ADConnectorAccountName <String> -ADConnectorAccountDomain <String> [-SkipAdminSdHolders] [<CommonParameters>]
- I only have this setup in lab. You would need to run each command to add each set of permissions required for each component of AD Connect that you use.
I ran the wizard again to add the new subdomain. It still showed the error like before, but it did add it to the sync.
The only difference on this was in lab it complained about the 'correct' account not having access to the subdomain. By correct I mean the service account in the Forest I was working in and not the second Forest joined to AD Connect where there is a different service account. :)
On Tuesday I'll give production a try.
*There was part of me that was worried that somehow these commands would replace the existing service account. You can't replace the service account at all. The commands can update the permissions on an account though. And I guess if you reinstalled you could use it.