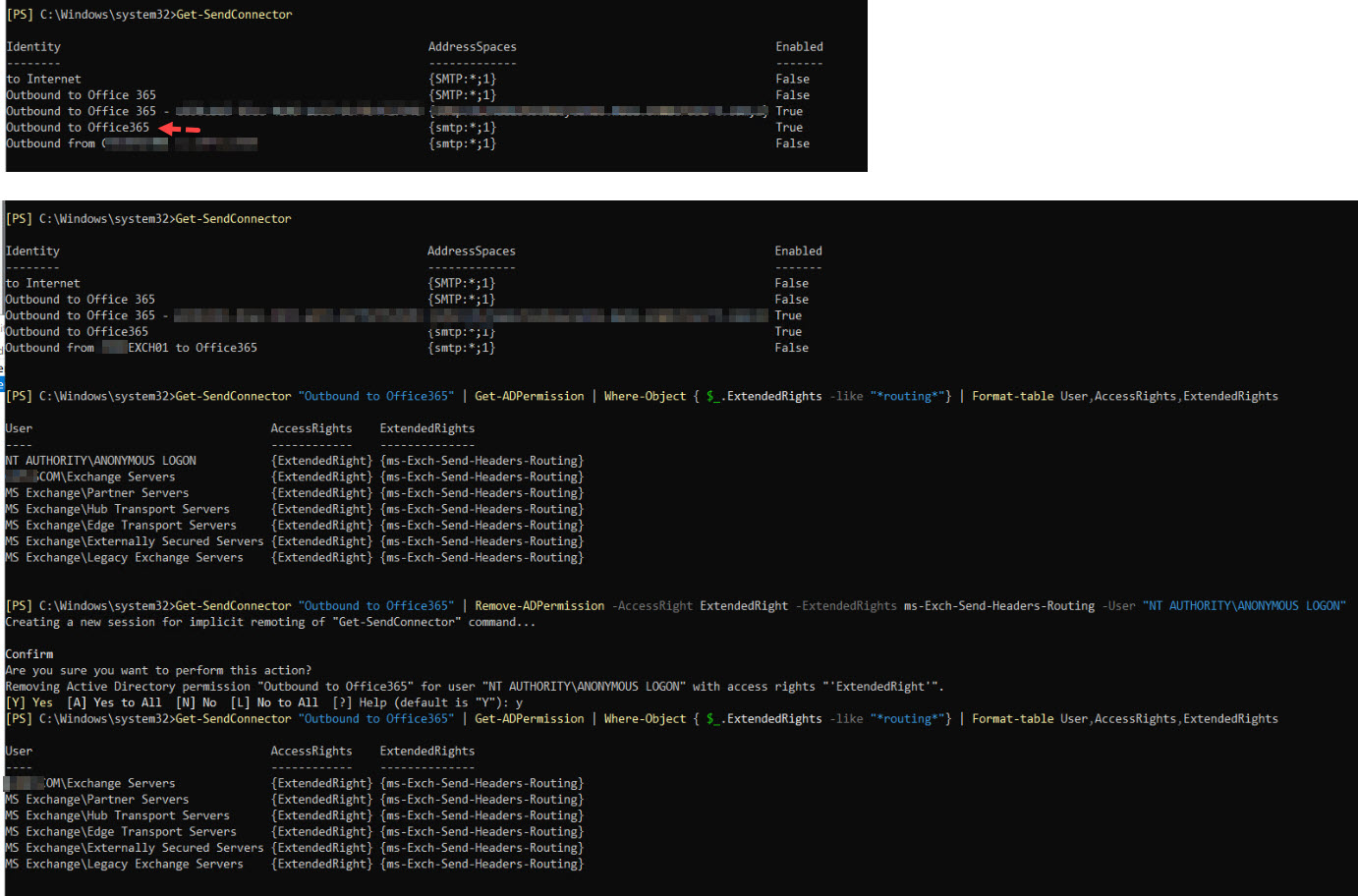
Fix for : Microsoft Exchange Client Access Server Information Disclosure ( Applied in exchange 2019 - Server 2019)
Step 1 : Find send connecter name in use and change "" in step 2
Step2 : Get-SendConnector "Outbound to Office365" | Get-ADPermission | Where-Object { $_.ExtendedRights -like "routing"} | Format-table User,AccessRights,ExtendedRights
Step3 : Get-SendConnector "Outbound to Office365" | Remove-ADPermission -AccessRight ExtendedRight -ExtendedRights ms-Exch-Send-Headers-Routing -User "NT AUTHORITY\ANONYMOUS LOGON"
Step4 to Recheck permission : Get-SendConnector "Outbound to Office365" | Get-ADPermission | Where-Object { $_.ExtendedRights -like "routing"} | Format-table User,AccessRights,ExtendedRights
Result were positive. Only Exit Ip ( Public ip was visible in next email, not the server original IP)