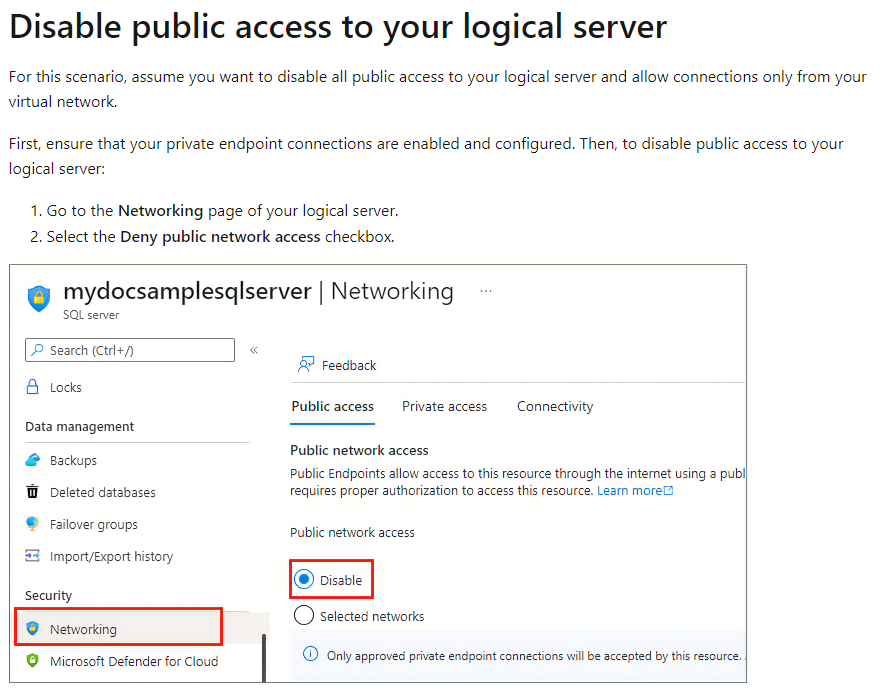
Hi,
I have a question on the network traffic between two Azure SQL DB servers connected to network via private endpoint.
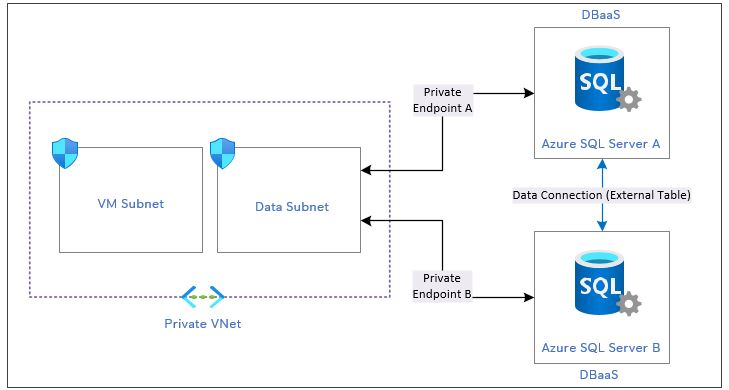
The setup is as below in Azure.
- A private VNet with two subnets - one for VMs and another one for data services.
- Two SQL database servers for two different projects. DB Server B should connect to DB Server A to retrieve some common data to reuse. This is done
using external table approach. i.e. DB Server B has external tables linked to DB Server A's tables.
- Private endpoint between DB Server A to Data Subnet and DB Server B to Data Subnet and the setup is identical.
- Both SQL Server firewalls allow "Public Access" but "Allow all azure IP" disabled due to security reasons.
When I queried the external table from database inside Server B, it throws an error that the IP address of server B is not allowed to access database in Server A. The IP address that it shows in the error seems to be a public IP and belongs to Azure DC of the resource's said location.
I can make it work by allowing this public IP of Server B in Server A's firewall but it's not allowed in our security policy to whitelist a public IP of Azure DC. If it's a public IP of our org, then it's allowed.
Any idea how can I establish a private connection between these two SQL servers to make external tables work using this setup?