Hi @Brandon Early ,
The solution you described sounds like a great option since the accounts would still be protected by MFA and need to meet the MFA requirements to close the Correlate incident. I don't see any reason to keep the false positive incidents open and based on your description can't think of any concern with that strategy.
Another option if you want to grant access to specific users traveling to specific countries is to create a universal "exclude" group in your Conditional Access policies and add the users to that group when they are traveling. Then if you have MFA enforced for untrusted locations and have those users added as an exemption to your "block international countries" policies, any attempts to access those accounts outside of your trusted locations will still be prompted for MFA.
But the method you suggested with MFA enforced is definitely a more secure option and a better long-term strategy.
As for suggestions to automate closing the incident based on underlying incidents closing, the feature is still in preview right now but you should be able to define the action of closing out the related incident based on the condition of the other incidents being closed. Based on what currently exists in the portal you could create the automation conditions based on the rule itself, the IP address, incident tags, or any of the other defining properties.
https://learn.microsoft.com/en-us/azure/sentinel/automate-incident-handling-with-automation-rules
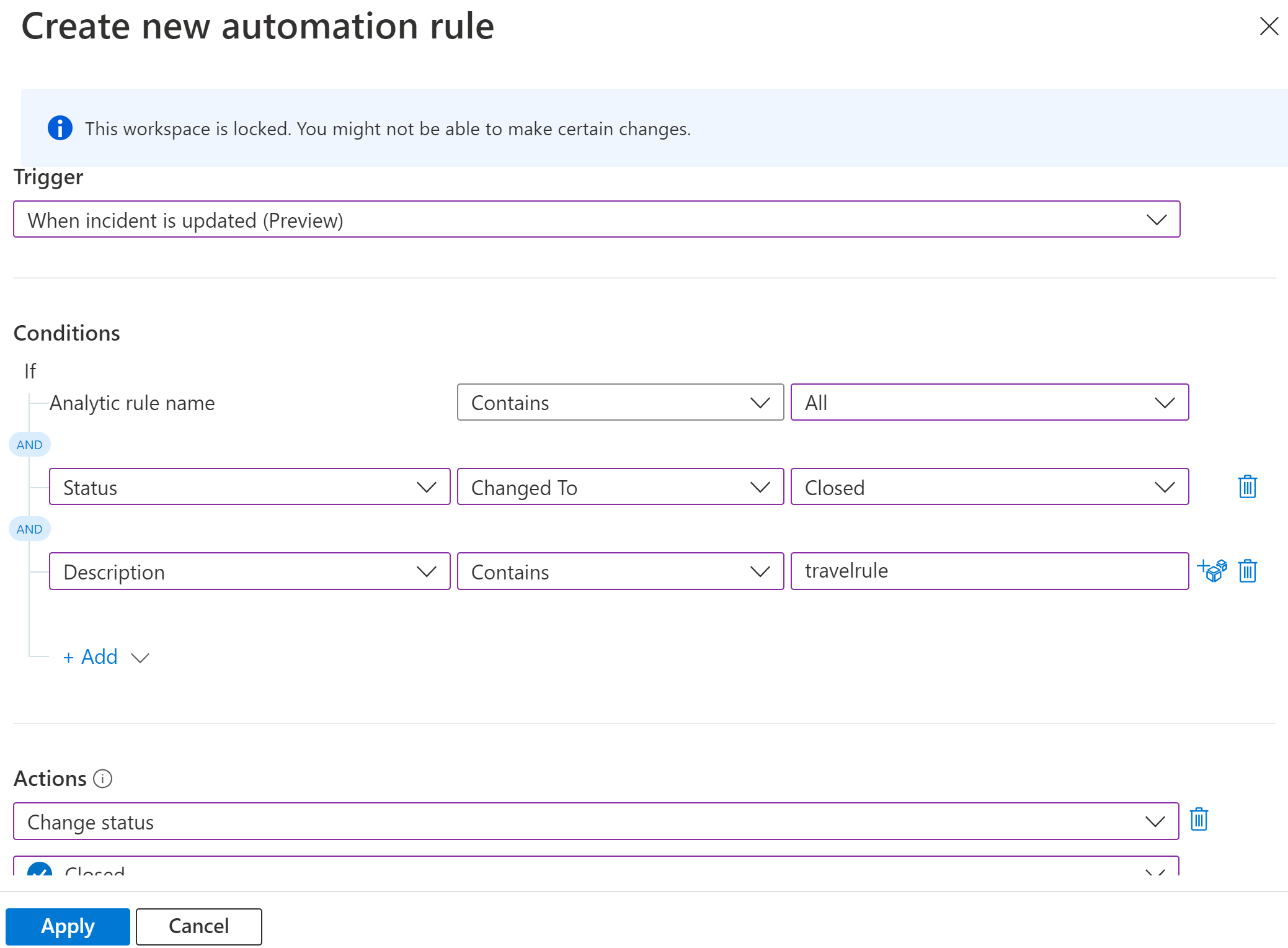
You can combine playbooks with automation rules to customize further.
https://learn.microsoft.com/en-us/azure/sentinel/tutorial-respond-threats-playbook?tabs=LAC
https://github.com/MicrosoftDocs/azure-docs/blob/main/articles/sentinel/automate-responses-with-playbooks.md
Let me know if this helps and if you run into any issues with this. I haven't tested the preview feature yet so I will try to create a proof-of-concept for this in my lab as well.
-
If the information helped you, please Accept the answer. This will help us and other community members as well.