Hi,
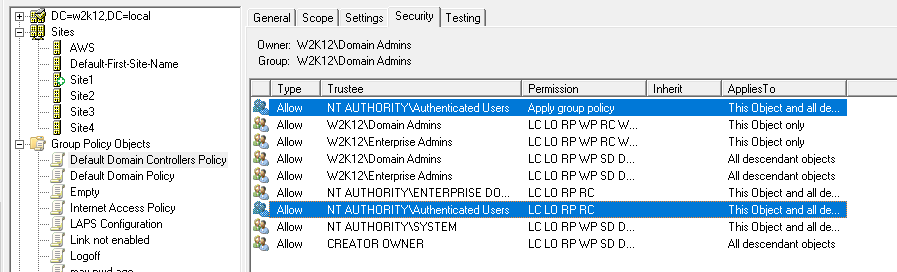
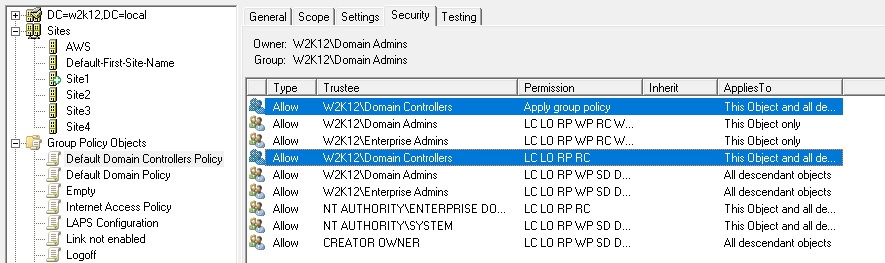
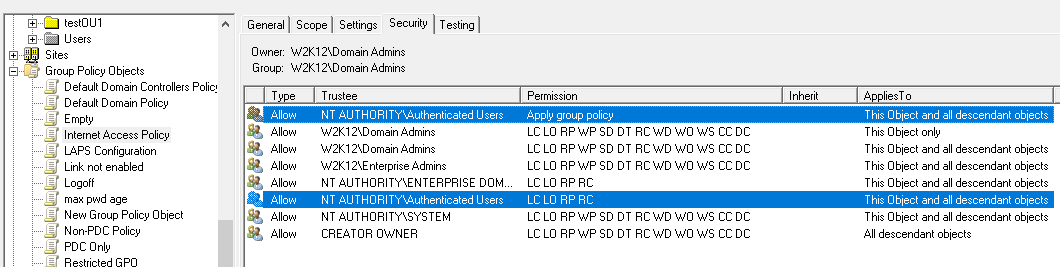
It depends if you are trying to stop users from reading both machine and user based GPOs. For user based GPO it's a little more difficult as the user's account needs to be able to read the policies so they can be applied, you could make the allocation more specific rather than based the authenticated users group. For machine based policies it's a little easier, if you remove the authenticated users read and apply gpo permissions and apply the permissions to a specific group that only contains machine accounts. However, as machine group memberships are picked up on the next reboot, you just need to make sure you sequence the changes over a few days, so the machines still have access to read and apply the policies.
Changing the authenticated users to a user or machine specific group will limit who can read the policy settings.
Gary.