@Heimdallr , Thanks for posting in our Q&A. If we onboard Windows devices to Defender for Endpoint via Intune policy, then switch the workload to Intune is necessary.
https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/configure-endpoints-mdm?view=o365-worldwide
When we switch the Endpoint workload, the Configuration Manager policies stay on the device until the Intune policies overwrite them. This behavior makes sure that the device still has protection policies during the transition. For Device configuration policy, when the workload is switch, we can still deploy settings from Configuration Manager to co-managed devices even though Intune is the device configuration authority. You can see more details in the following link:
https://learn.microsoft.com/en-us/mem/configmgr/comanage/workloads#endpoint-protection
In addition, to validate workloads and determine where policies and apps come from in a co-management scenario, we can check the logs under %WinDir%\CCM\logs\CoManagementHandler.log. Here are some frequently asked questions about workloads in the following link. You can read it to see if it helps.
https://learn.microsoft.com/en-us/troubleshoot/mem/intune/troubleshoot-co-management-workloads
For bitlocker issue, after the Device configuration workload switch to Intune, try to configure the bitlocker policy and sync on the device side. Then check if the Bitlocker policy deployment is successful in Intune portal. If there's any error, try to troubleshoot according the following link:
https://techcommunity.microsoft.com/t5/intune-customer-success/support-tip-troubleshooting-bitlocker-policies-in-microsoft/ba-p/863670
Hope it can help.
If the answer is helpful, please click "Accept Answer" and kindly upvote it. If you have extra questions about this answer, please click "Comment".
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.
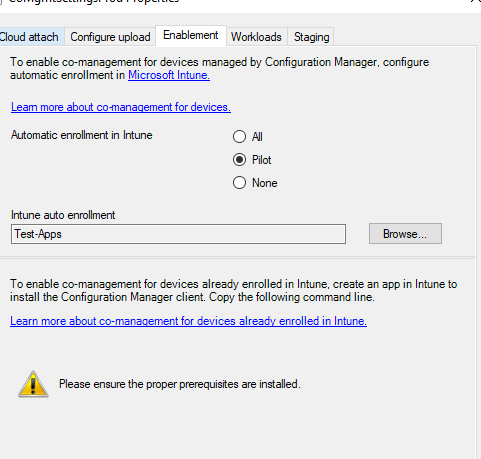
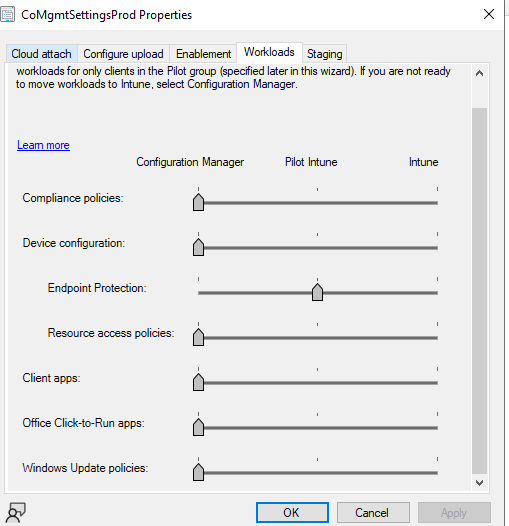 - When I was in doubt that Defender forwards that from cloud to ConfigMGR, I've moved the defender policy to Pilot collection, so tried also without it.
- When I was in doubt that Defender forwards that from cloud to ConfigMGR, I've moved the defender policy to Pilot collection, so tried also without it. 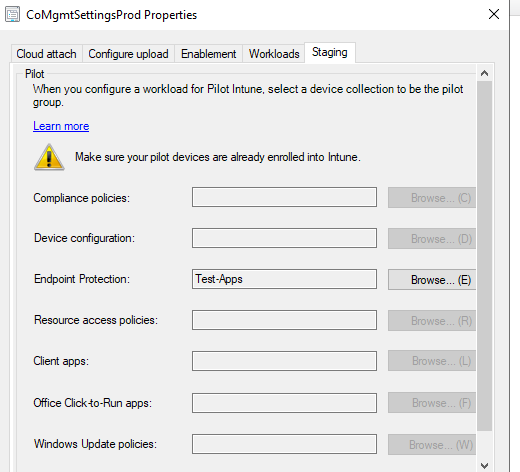
 + group sync
+ group sync