Identity Delegation and Security Context Flow Through Physical Tiers
This post lists solution approaches for flowing identity and security context through physical tiers in distributed applications.
Use this as your decision map when deciding how to implement identity flow through physical tiers when implementing on-premise, cloud, and hybrid solutions.
Enabling technologies
- Active Directory
- Windows Identity Foundation (WIF)
- Windows Azure AppFabric Access Control Service (ACS) v2
- Active Directory Federation Services AD FS v2
Impersonation
In this scenario:
- Identities are managed by Active Directory.
- Original caller is authenticated by Active Directory
- Resources of the server needed to be accessed by the original identity – one hop.
image source
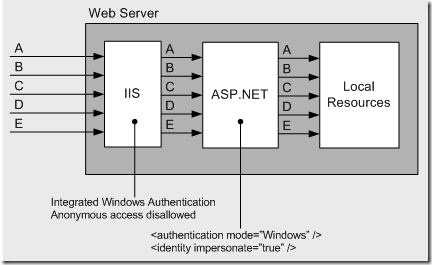
Solution:
Windows delegation
In this scenario:
- Identities are managed by Active Directory.
- Original caller is authenticated by Active Directory
- Resources of the downstream server needed to be accessed by the original identity – multiple hops.
image source
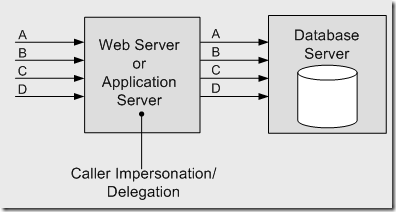
Solution:
- How To: Implement Kerberos Delegation for Windows 2000
- How To: Use Impersonation and Delegation in ASP.NET 2.0
- Credentials and Delegation
Protocol transition
In this scenario:
- Identities are managed by Active Directory
- Original identity authentication by proprietary authentication mechanism.
- Resources of the downstream server needed to be accessed by the original identity – multiple hops.
image source.
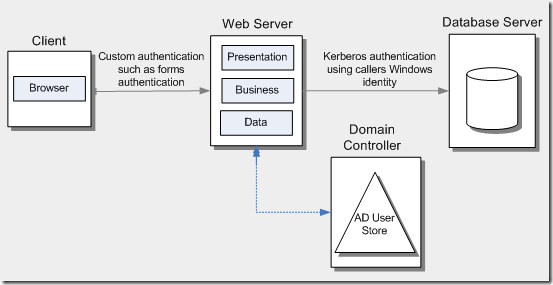
Solution:
- How To: Use Protocol Transition and Constrained Delegation in ASP.NET 2.0
- Using Protocol Transition—Tips from the Trenches
Claims and ActAs
In this scenario:
- Identity is managed by Identity Provider.
- Original caller is authentication by Security Token Service (STS)
- ActAs is for delegation. Final recipient has details about immediate client and the original requestor.
image source
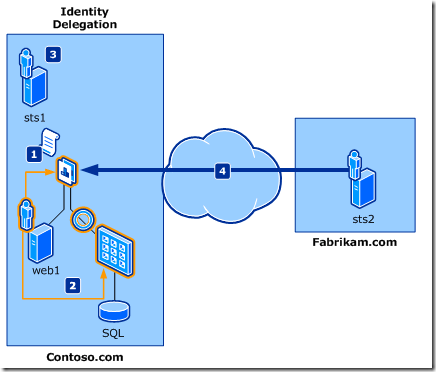
Solution:
Claims and OnBehalfOf
In this scenario:
- Identity is managed by Identity Provider.
- Original caller is authentication by Security Token Service (STS)
- OnBehalfOf is for impersonation. Final recipient has no clue about the original requestor.
Claims and OAuth 2.0
In this scenario:
- Identity is managed by Identity Provider.
- Original caller is authentication by Security Token Service (STS)
- Token is issued by OAuth 2.0 Authorization Server
- Identity flow requires consent of the end user
- Protected resource is RESTful web service
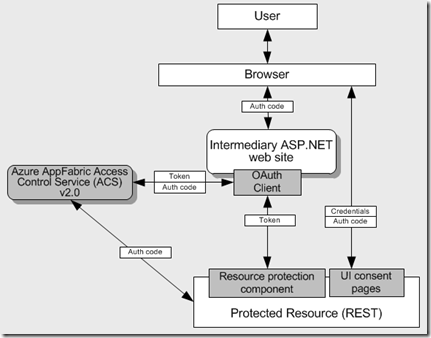
Solution:
Related Info
- Windows Identity Foundation (WIF) and Azure AppFabric Access Control (ACS) Service Survival Guide
- Video: What’s Windows Azure AppFabric Access Control Service (ACS) v2?
- Video: What Windows Azure AppFabric Access Control Service (ACS) v2 Can Do For Me?
- Video: Windows Azure AppFabric Access Control Service (ACS) v2 Key Components and Architecture
- Video: Windows Azure AppFabric Access Control Service (ACS) v2 Prerequisites
- Windows Azure AppFabric Access Control Service 2.0 Documentation
- Windows Identity Foundation (WIF) Fast Track
- Windows Identity Foundation (WIF) Code Samples
- Windows Identity Foundation (WIF) SDK Help Overhaul
- Windows Identity Foundation (WIF) Questions & Answers