SharePoint End User Security
Security covers a number of topics when it comes to software. Everything from locking down a system to end user security. There is absolutely no doubt that security is extremely important and should be taken seriously. And it's no surprise that security is one of the most frequently asked questions when I present to executives and IT professionals.
So here's my attempt at providing the SharePoint End User Security 101 covering different aspects of what enterprises need to think about. By no means is this article comprehensive, but touches upon aspects of SharePoint end user security that I get asked about frequently.
1. Web Single-Sign On. SharePoint is a web application. So the first question you have to think about is how users get authenticated to SharePoint. Simply put, authentication is the process of finding out who the user is. Out-of-the-box, SharePoint provides integration with Active Directory for NTLM authentication. There are many benefits of using AD, one of which include seamless Office integration. SharePoint, because it's built on ASP.NET, also supports the ability for enterprises to use other authentication systems with the pluggable authentication provider model. Office SharePoint Server, out-of-the-box, ships with an LDAP provider. When deciding what authentication model to use and how to configure authentication, you must read the following articles written by Steve Peschka. Steve Peschka is a rockstar SharePoint Microsoft Consultant - and that's an understatement:
- Part 2: Membership and Role Provider Samples
- Part 3: Forms Authentication vs. Windows Authentication
2. SharePoint Authorization. SharePoint provides in-built tools and interfaces to configure authorization. Once a user is authenticated, SharePoint needs to make sure the user is authorized to view/edit the content. There are many different access levels and those rights can be applied to a single piece of content (list item) like a document or a page, a group of content like a folder or library, or a collection of content like a site or site collection. By default, security is inherited from the parent which makes it easier to manage security. However, security can be managed separately for an entity allowing for greater control when needed.
SharePoint also has the notion of "groups". You can create a SharePoint group that contains users who have the same set of rights. For examples, "Contoso Readers" for all the users who can read from the Contoso site. SharePoint also respects AD groups which has the benefit of a new employee, for example, automatically getting access to SharePoint when he/she is added to an AD group.
It's also important to note that SharePoint also supports anonymous users. This could prove to be useful in Internet scenarios, for example. In any case, if you do have content that you want to give anonymous users access to, make sure you appropriately configure your web application through Central Administration before you attempt to make the list "anonymous".
Needless to say, authorization can be set at many different levels and can be delegated to Site Administrators. One of the neat features of SharePoint is that content is "security trimmed" (see #3) which means that content is only displayed if a user has access to it. Ted Pattison has done a good job in this video walking through the various controls.
3. Security Trimming. The SharePoint UX framework doesn't display links to content & actions that the user doesn't have access to. For example, a list will only show items/folders that a person has access to - not just that, but will only show drafts that a person has access to; navigation controls will only show menu items a person has access to; My Site controls only show documents people have access to; Search only shows results that a person has access to. This avoids clutter, confusion & inadvertent communication of the existence of a piece of content.
While security trimming is out of the box, it works for content managed by SharePoint. Links to external content that are authored by someone, for example in a Content Editor Web Part, won't be security trimmed; it's feasible to develop a web part/field control that does do this. As for search, security can be captured at index time via a protocol handler or trimmed during rendering time with a custom security trimmer.
4. Content Security. As I mentioned in the previous section, SharePoint handles authorization for content that lives in SharePoint. If you are looking to have security rights "stay" with the document when it leaves SharePoint, you can configure Information Rights Management (IRM). By configuring IRM at the document library level, when a piece of content is downloaded from the library, SharePoint will apply an IRM wrapper on the content ensuring the rights carry forward with the document. By applying the wrapper at download time & leveraging SharePoint security while the content lives in SharePoint, the search indexer is able to effectively index the content - which is a great feature.
5. Accessing/Authenticating to SharePoint from the Outside. ISA and IAG offer fantastic solutions to access SharePoint in a secure way from outside the corporate firewall as well as provide additional security based on user roles & the state of the machine. If you've always wanted to publish your SharePoint solution for external access in a secure way, take a look. Very compelling and ties in with your SharePoint authentication whether you're using AD or some other system using FBA.
6. The World outside of SharePoint.
a) Other Web Portals
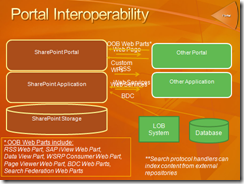
There are a number of ways you can integrate with other web portal technologies. It really depends on what you are attempting to achieve and the standards the third party portal supports. This slide which I created outlines some of the ways you can integrate with 3rd party portals. This comes from a build slide, so it looks a little cluttered. You can find the original deck here.
From a security perspective, the different portal systems will typically manage their own authentication and authorization. By leveraging a common directory for webSSO and using cookies, you can make the experience more seamless. For example, when someone logs onto SharePoint or vice-versa, you essentially log them into the other portal and make sure you set the right cookies.
Another important consideration is "how" you choose to integrate. By using iFrames (for example, the Page Viewer Web Part uses iFrames), the browser is actually requesting a particular web resource and passing its credentials - whether its windows credentials with NTLM & passing a cookie if you've used Forms Based Authentication (FBA). This avoids the double hop challenge you would have if the actual application code (for example, the web part was calling another system) was making the call. For these types of scenarios, you need to consider taking advantage of kerberos - a protocol that SharePoint supports or the Enterprise SSO service which I talk about briefly later in this article. Incidentally, there's been a lot of rambling on how the RSS Web Part doesn't work without kerberos - and there's good reason for that! Otherwise, credentials would be "double hopping"! :-) Clearly, RSS feeds for "anonymous lists" will work just fine out-of-the-box.
b) Search
As I mentioned earlier, the SharePoint UX framework does security trimming and this includes the search service. However, this only works when SharePoint knows who has access to the content and who doesn't. Out-of-the-box you can configure SharePoint to crawl content and "store" ACL information for a number of sources including file shares, SharePoint content and Notes Databases. Check out this article for a more detailed description of how security works with Search including pointers on how to develop your own custom security trimmer.
c) Application Integration
I decided not to spend time walking through the nuances and meaning of Single-Sign On (SSO). The term Single-Sign On is used very often when discussing authentication across different systems. SSO can generally be broken up into two categories: WebSSO (which I described earlier) and Enterprise SSO. Enterprise SSO generally refers to the seamless end user integration with back-end systems. For example, let's say a user logs into a web portal and takes a look at a dashboard where data is coming from all different kinds of systems: SQL, SAP, custom LOB, et cetera. Each one of these systems will have a separate authentication system. By having an Enterprise SSO strategy and system in place, the user logging into the web portal gets access to all the different systems seamlessly without having to sign into each system individually. The magic happens in the background and is typically achieved by managing and retrieving different username (or group) passwords from a secure store that maps to the webSSO username. SharePoint Server 2007 (you need the Enterprise CAL) ships with an out-of-the-box SSO service and you also have the option of plugging in your own SSO Provider.
d) Business Data Catalog (BDC)
You can configure security with the BDC at the entity level. Many customers want more granular security. Granular security is possible when it comes to searching BDC content. More specifically, you can control what the returning search result set looks like by implementing a custom security trimmer. Here's an example of how you would do it.
7. Managing SharePoint User Security
There are a number of articles that describe best practices for managing SharePoint security. The truth is it really depends on what your existing directory and SSO infrastructure look like and how you are looking to integrate that with SharePoint. And as I've pointed out in this article, there are many aspects to "security" that you really need to consider - authentication, authorization, integration, et cetera.
As for SharePoint security specifically, there are a lot of tools out there in the community to help manage SharePoint security. Instead of providing a list of resources, I wanted to comment on one particular technology I recently came across: iDevFactory's Universal SharePoint Manager. From what I've seen, it's absolutely fantastic. It's not too expensive & offers a rich set of features that allows you to really get a handle on what users have access to what assets. Not only does it do reporting, but it also allows you to manage and change credentials in a very intuitive way.
Comments
- Anonymous
May 09, 2008
PingBack from http://www.basketballs-sports.info/basketball-chat/?p=1269 - Anonymous
May 09, 2008
Thanks Arpan for this article in 7 points - Anonymous
May 28, 2008
Thanks...Very Nice article - Anonymous
September 18, 2008
A little while ago, I published a blog entry around end-user security . Since then, I've been asked many