Azure Firewall, a step towards a "managed" NVA?
Hi,
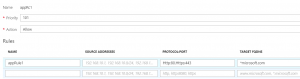
Microsoft recently made Azure Firewall available in public preview. This Firewall as a Service offers a new way to protect and control network traffic via both network and application rules. At the time of writing, Azure Firewall is used to control outbound traffic only. Network rules are similar to what you can do with NSG but application rules allow URL based rules as shown below:
This cannot be achieved with NSGs as they only allow the usage of IP addresses. So, with NSGs, the only way to achieve similar results is to get all the static IPs (should they be static) corresponding to some domains and white list them within a NSG rule. However, this is a little tedious and sometimes, IPs could be dynamic instead of static. So, working with URLs is more convenient.
To let Azure Firewall govern the network traffic, one must associate one (or more) subnet(s) to a User Define Route aka Route Table that defaults to the Azure Firewall instance. Does this ring a bell? Yes of course, that's also what you need to do when working with Network Virtual Appliances (NVA).
If Microsoft also includes inbound traffic in scope, the Azure Firewall might represent a very interesting alternative to NVAs there would be no more underlying infrastructure to manage/patch etc., plus this native Azure Service integrates with Log Analytics which facilitates the whole monitoring work. Of course, we're not there yet as the service is in its very early days and still in public preview phase but it's definitely interesting to keep an eye on it.
If you can't wait to give it a try, you can follow this tutorial or just deploy this quickstart template which deploys a sandbox in a matter of minutes.