Microsoft Advanced Threat Analytics
Tracking down security vulnerabilities has always been a game of cat and mouse. Certain safeguards can be put in place to prevent security vulnerabilities such as blocking firewall ports, requiring multi-factor authentication and so on. Granted, no system can capture every single security vulnerability, however if a layered security approach is taken, there’s a better chance of catching security vulnerabilities and threats.
There’s also those deep vulnerabilities you’ve only read about but don’t have the necessary tools in place to capture or even check if they are occurring inside your network. Did you know that the average time attackers stay in a network before detection is over 200 days? If that is the case, then there is a lot to worry about including stolen passwords, confidential company data, customer data, and much more.
We’ve all seen the news where highly visible companies are compromised where credit card and customer information is stolen, and worse yet, published online. Have you been one of those affected? If not, what if it happened to the company you worked for? Would you be affected then? My guess is probably, one way or another.
What if you had a solution that was simple to deploy and began learning about your environment within minutes? Look no further, Microsoft Advanced Thread Analytics has a lot to offer, even with your existing security systems in place.
What is Microsoft Advanced Threat Analytics (ATA)?
Microsoft ATA is an on-premises solution that begins by learning about your environment, analyzing behaviors, and alerting on anomalous activity, attacks, and threats. Microsoft ATA will also integrate with existing SIEM’s.
How does ATA work?
Microsoft ATA works by capturing network traffic from domain controllers and by using machine learning, learns about behaviors within your network and alerts on abnormal behaviors.
There are four steps ATA takes:
Analyze – analyzes all Active Directory traffic as well as SIEM events.
Detect – looks for anomalies and known security attacks and issues.
Learn – leans about users and user behavior, devices, and resources then builds a graph mapping common behaviors.
Alert – ATA raises alerts on suspicious activities and provides a timeline of activities of who, what, where, and when.
What types of issues are alerted by ATA?
ATA detects the following:
Abnormal user behavior: e.g. Anomalous logins, Password sharing, Lateral movement.
Malicious attacks: e.g. Pass-The-Ticket, Pass-The-Hash, Golden Ticket, Bruteforce attacks, remote execution, a much more.
Known security issues and risks: e.g. Broken Trust, Weak Protocols, Known protocol vulnerabilities.
What do alerts look like?
The following are a few example of actual alerts:
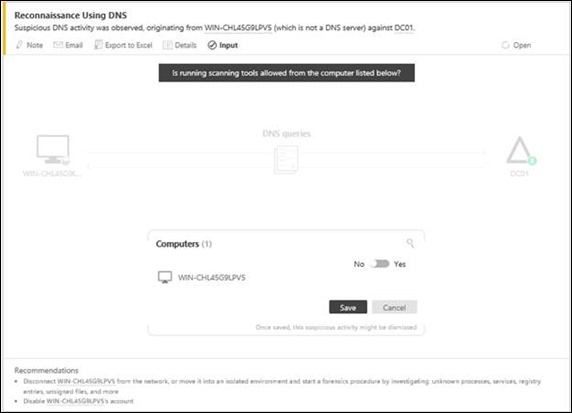
Reconnaissance Using DNS
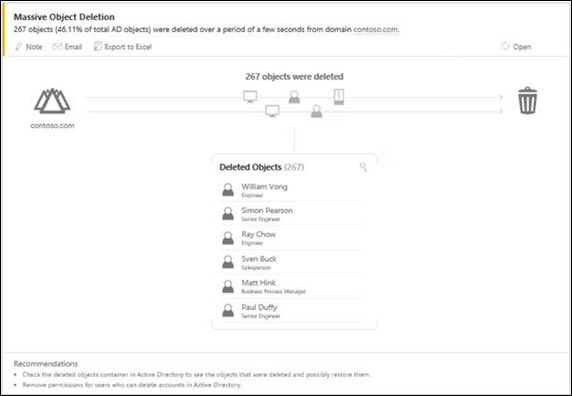
Massive Object Deletion (from Active Directory)
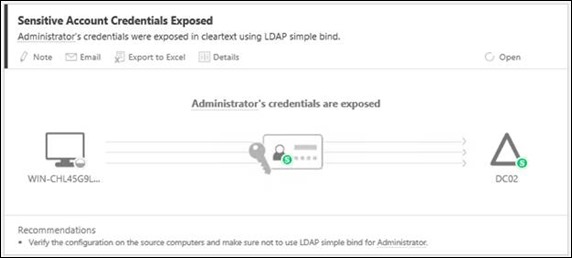
Sensitive Credentials Exposed
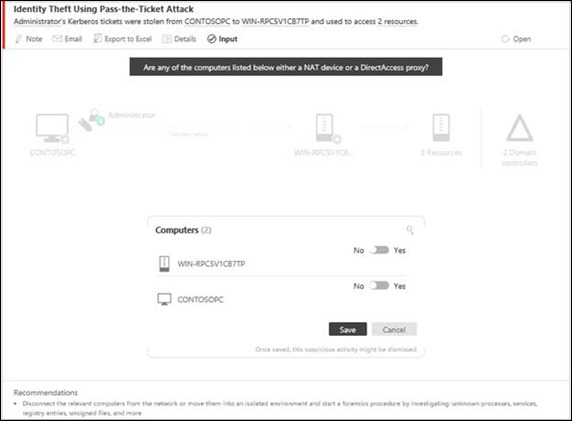
Pass-The-Ticket Attack
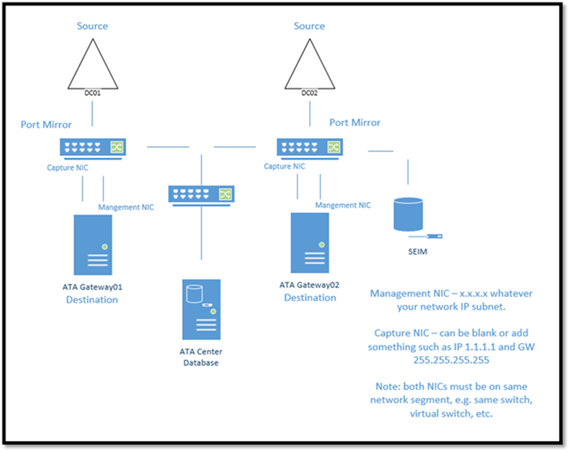
What about architecture?
The architecture of ATA is very simple. It consists of a “Central Server” and one or more “Gateway Servers”. Both can be deployed to VMs or physical machines. Again, ATA is currently an on premises solution.
- Central Server: Central admin console (http) and the database (MongoDB).
- Gateway Server(s): Destination for port mirrored network traffic from domain controllers.
Additionally, ATA uses self-signed certificates to communicate securely from the Gateway Server to the Central Server. Lastly, port mirroring is required from your domain controllers (source) to the Gateway Server(s) (destination).
For example, it took me about 10 minutes to set up, end-to-end, in my environment where I have two domain controllers.
Links to deployment information is under Additional Resource below.
The following is a sample architecture of ATA:
Download and try ATA today, because having more information about attacks, threats, and behaviors across your network is better than guessing.
Additional Resources
Learn more here: https://www.microsoft.com/en-us/server-cloud/products/advanced-threat-analytics/
Additional ATA resources such as release notes, deployment guides, operational guides , FAQ’s and more are located here: https://www.microsoft.com/en-us/server-cloud/products/advanced-threat-analytics/Resources.aspx