Introducing SecurityNow
Mark Curphey here.....
A few months back I challenged some of my team to build a "Proof of Concept" (POC) that would;
- demonstrate how we could apply some of the ideas and concept we had been talking about such as BPM and BI
- show how Microsoft's technology stack can be applied to the security management space
With just a few weeks of work (we really do have an incredibly talented team) we produced "SecurityNow". The POC took it's name from the excellent connected systems demo called DinnerNow. We wanted to take a specific scenario and in this case chose to look at line of business application security assessments in a corporate environment. We could have easily chosen incident management, risk assessment, network vulnerability management etc. but the information security team here has the ACE Team who are responsible for security assessment of our Line of Business (LOB) applications and it was what Tom Cruise would call a "target rich" scenario. The scenario we chose was actually made up of a set of smaller scenarios and in my experience is typical of how many corporations would like to do their line of business application security assessments.
Scenario 1 - The systems owner schedules an assessment
Scenario 2- We automated the execution of security assessment tools
Scenario 3 - The system hands off to a trained analysts to do the manual assessment
Scenario 4 - Automated the tracking of the assessment status
The POC specifically looked at applying Windows Workflow Foundation (WWF) and PerformancePoint server (we have some stuff in the brew looking at WPF, Oslo and WCF now so watch the blog in the future).
The engineers will be blogging about the specifics in detail in the coming weeks so I will just provide a high-level overview by way of introduction with some teaser screen shots.
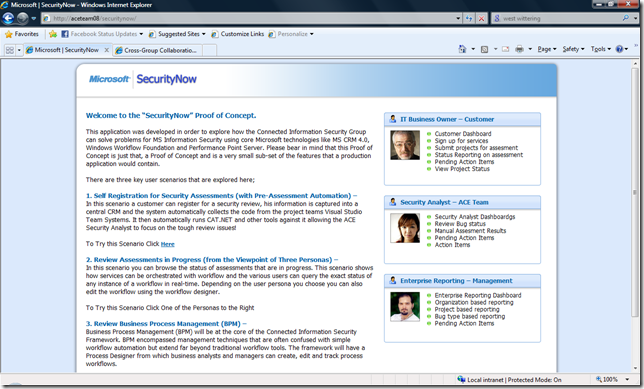
When you first go the POC you get the coverage below to navigate to the various scenarios.
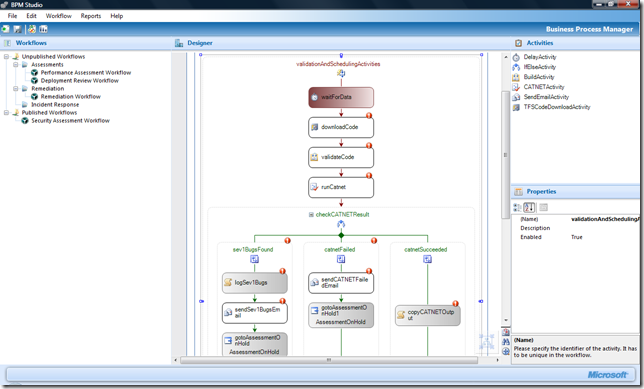
It's worth jumping straight to the business process designer. Behind the POC is a state machine workflow (what's shown below is actually one of the states) which then executes on the business process engine and is monitoring by business activity monitoring (or BAM). We re-hosted the .NET workflow designer and built a state machine and set of activities to automatically pull code from Team Foundation Server, compile it (check) and run our manage code review tool CAT.NET (you'll be hearing lots more about that on the blog in the coming weeks).
We believe visual modelling and simulation of security processes will be huge. You can literally drag and drop activities onto the design surface and build an application in minutes. I posted about the Tenets of BPM for Security on my personal blog a while back.
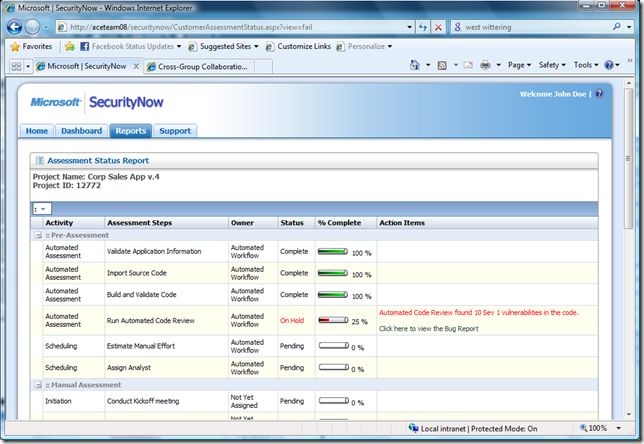
We built a simple UI (not shown here) that allows the user to come along and schedule an assessment by providing the location of the code in his / her Team Foundation Server. We capture his / her project details from the GAL (Active Directory) and capture some additional project related information. It takes less than 60 seconds to request and schedule an assessment!! When submitted we automatically pull the code from the project teams team Foundation Server, compile it and run our automated tools over it. We then (and this is where it gets good) automatically enter any defects back to the team as TFS work items. If they have any Sev 1 bugs we put the work flow on hold until they have closed off those bugs. When they interact with the workflow we of course verify that they have indeed closed them out before handing off the assessment to the analyst who picks up his review of the things automated tools can't (or do a bad job of) finding. The screen shot below is a status report which basically queries the workflow in operation. You can see this particular case is on hold as there were Sev1 bugs found (this is all dummy data of course).
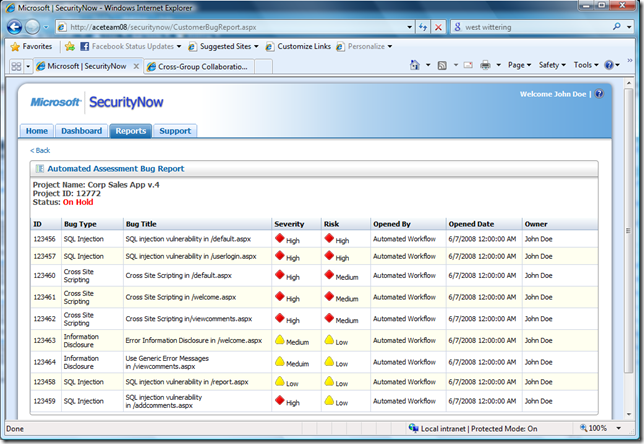
The analyst or the system owner can query the status of the process and any results in real time. Below is the current status of the security defects that were found. The reports below are build using PerformancePoint, our Business Intelligence suite. Our development team in India has vast experience in building huge high performance data warehouses and you should expect to hear a lot from us about data warehouses for security in the coming months.
I'll leave it there for now. It was just an introduction. The engineers will follow-up with a series of posts about the nuts and bolts and I expect to follow-up in a few weeks with some news and more details about our plans for security management tools.