Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Hello together,
today I am writing together with my friend Julien Reisdorffer (@JReisdorffer) just after the fantastic PowerShell Conference Europe.
Nearly one year passed since I have written a comprehensive summary around PowerShell Security, which you can find here:
As you can recognize by only taking a look at the length of this article, there are many security controls which need to be known and configured. But the problem for most admins is 'Where to start and where to end?' .
Therefore, Julien and I have been working on this project. You can find the material of our talk in the official Github of the PSConfEU2018 here and the video in the official Youtube channel here (will follow asap).
Introduction - the Challenge:
Let us start with a short introduction. Unfortunately, many customer still think of PowerShell as this:

Due to this thought we encounter also some other interesting feedback from the field. Here are probably our best catches till today:
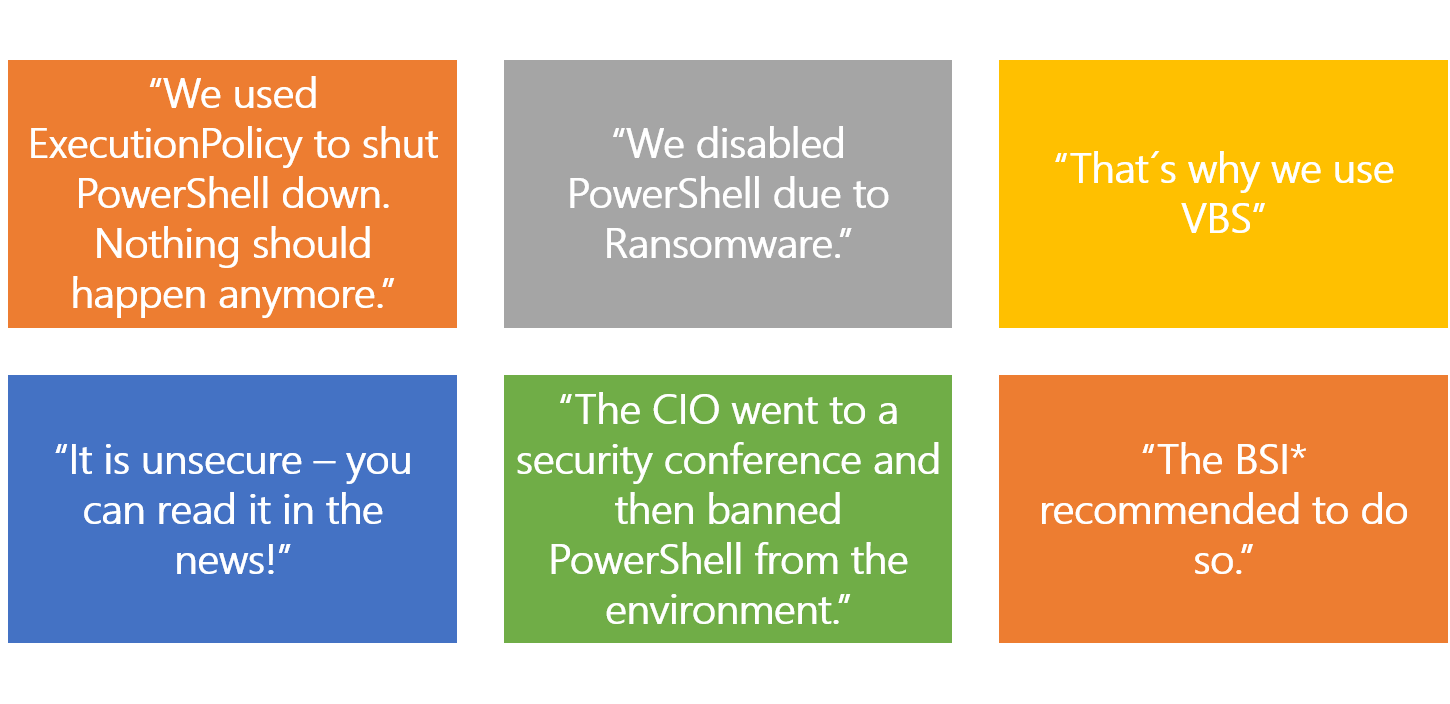
* Bundesamt für Sicherheit, Federation of Information Security (Germany)
Someone could call this funny, though professionally speaking this is more than sad. Sure - there are some challenges which come around PowerShell Security:
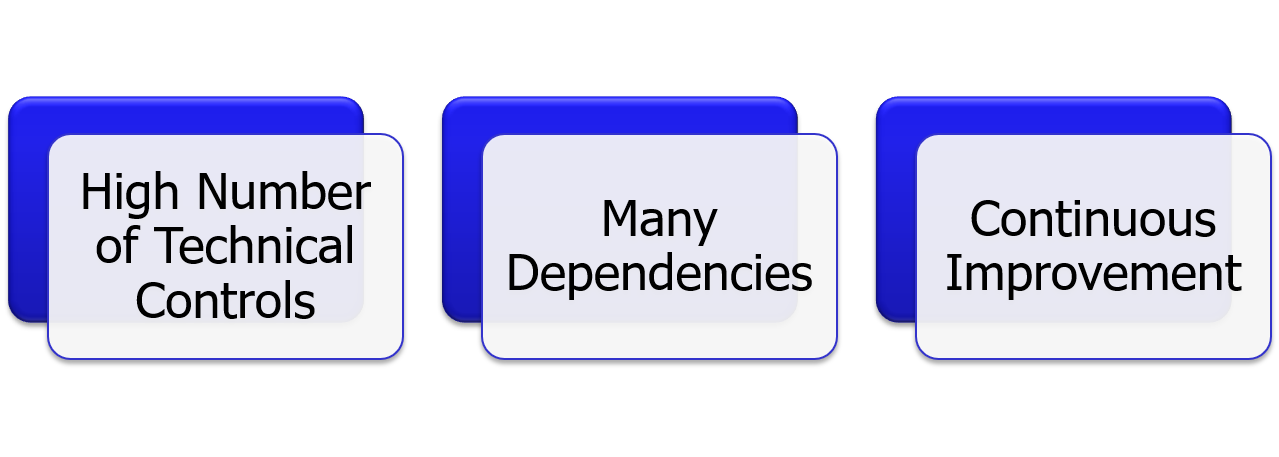
There is an extreme high number of technical security controls, which need to be validated. They itself have a lot of dependencies to each other or some to other technical implementations. In addition, with Windows as a Service, there is also a continuous movement in these security controls - speaking of frequently adjusted or new technical security controls arriving every half a year and raising the whole complexity. This complexity is also combined with the following challenges on-site: 
And - What is the final result of this?
Well - what do you think? Customers are facing this problems on top of the Windows 10 migration, which in addition comes along with Windows as a Service. Therefore, most of our customers completely ignore the topics around PowerShell Security. But this is not only true for the topic PowerShell Security. Customers are also very often misled into complete wrong directions like pushing all their resources into centralized logging without really taking value out of it.
The idea is simple - we need a tool to give the customer a recommendation, where they should invest time, resources and money in. In detail - on what should you focus first, because it is
- of a very high importance
- brings a good mitigation and can be implemented fast
- is a preleminary, necessary requirement for other controls
As with every very complex topic you start simple and make sure that your solution is dynamically extendable. We will need to add more and more complexity to it. Therefore, the initial steps are of very high importance, and sometimes you have even to just restart your idea from scratch. Did this also happen to us? Sure it did. We started first with an idea:

The first challenge were Technical Security controls. As going forward we decided to do a brainstorming and clustering into topics and adding dependencies to it. We started simple with the following first three topics:
- PowerShell
- Moderizing Environment
- Securing Privileged Access
Next, we added all the Technical Security Controls to it. This was easy by using a SmartArt and resulted for the first shot in this graph:

Good - this kind of graphs we had actually also before in my blog article from past year. Now it was time to extend the security controls with additional properties to finally make them filterable by any mean.
Classification of the Technical Security Controls
So, we created a high-level specification, what properties could be relevant in the long-term perspective and ended up with this smart-art.
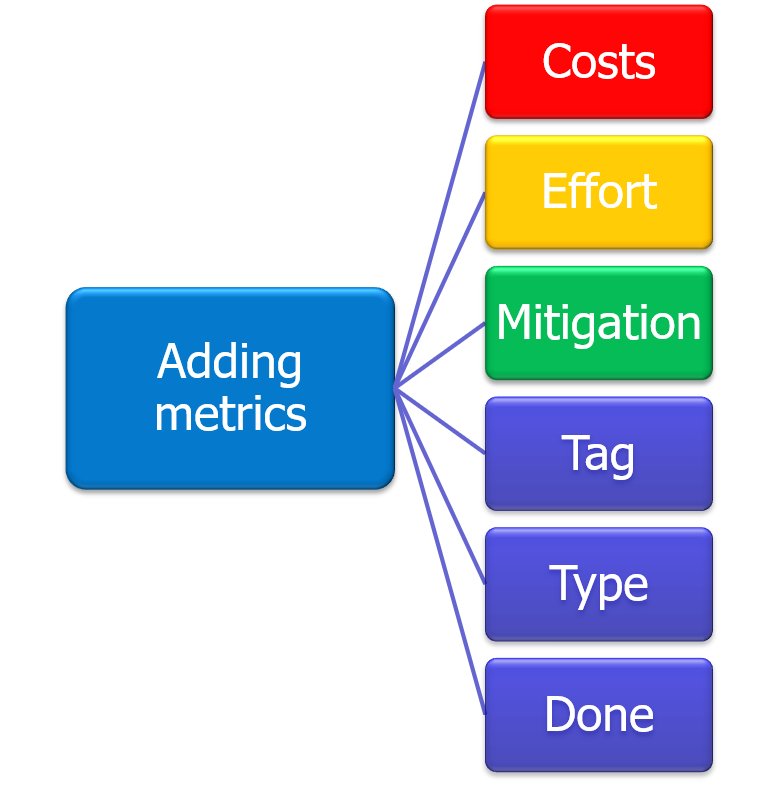
Here we added three important properties:
- Costs - How many sales costs in Dollar does the project or technology cost.
- between 1 - 100; 100 is very expensive
- Effort - How many time and resources will it consume.
- between 1 - 100; 100 is a high resource and time consumption
- Mitigation - What is the mitigation value
- between 1-100; 100 is a very good mitigation or benefit
Out of these three values we can now easily calculate a priority factor:
- Costs * Effort * (101-Mitigation) = Priority
- between 1-1000000; 1 is the highest priority

Looks good? Not bad - yes. But we thought that this is a very subjective validation.
First, we wanted to visualize the data in a graph and make some calculations with it. As you can see in the table, we also just added the property 'done' with Boolean values.
Working with the Graph
We made use of Neo4j and worked together with the PowerShell module ImportExcel (https://github.com/dfinke/ImportExcel) and PSNeo4j (https://github.com/RamblingCookieMonster/PSNeo4j).
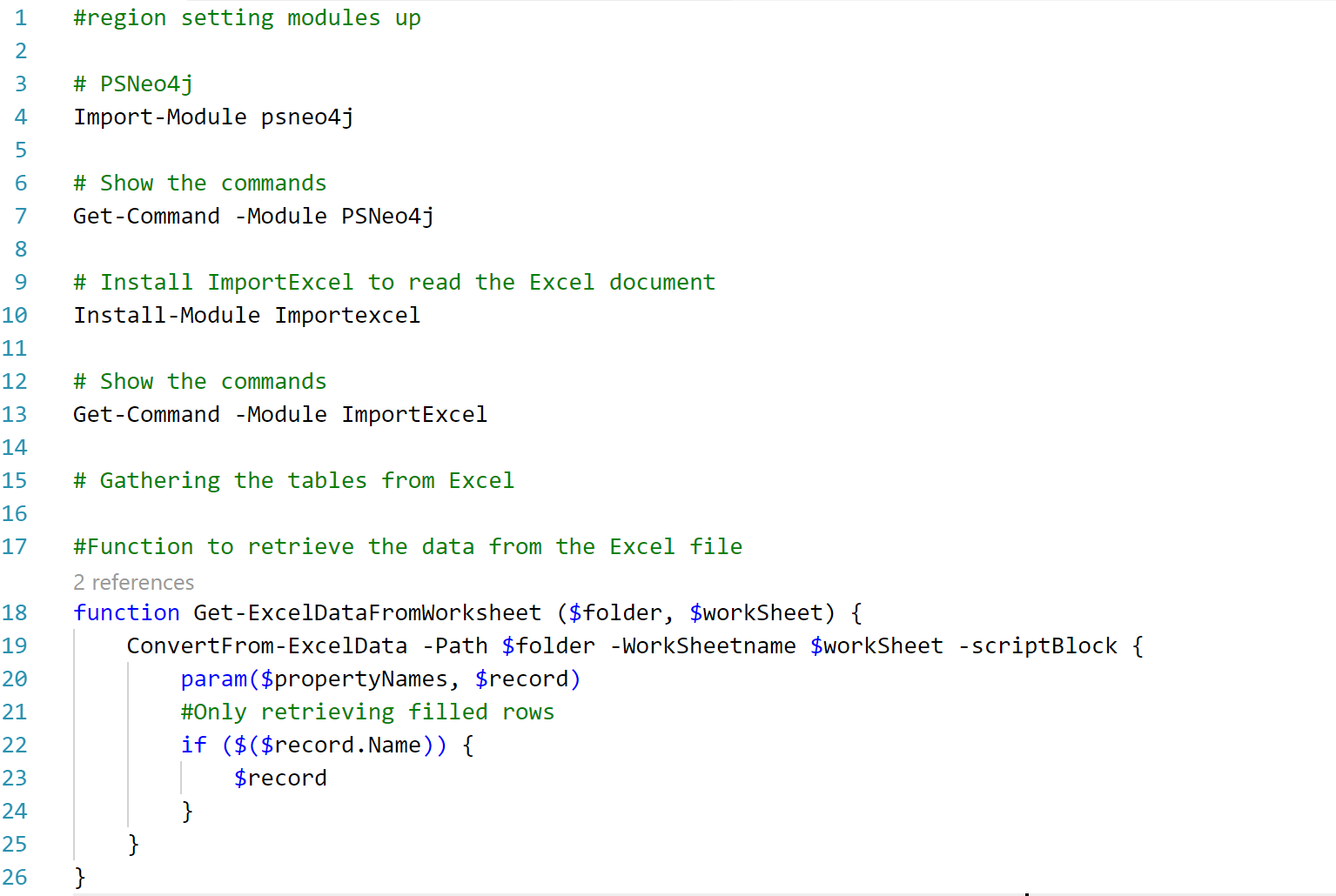
We also created a very small function to retrieve the data from the excel tables, which are included in different worksheets.
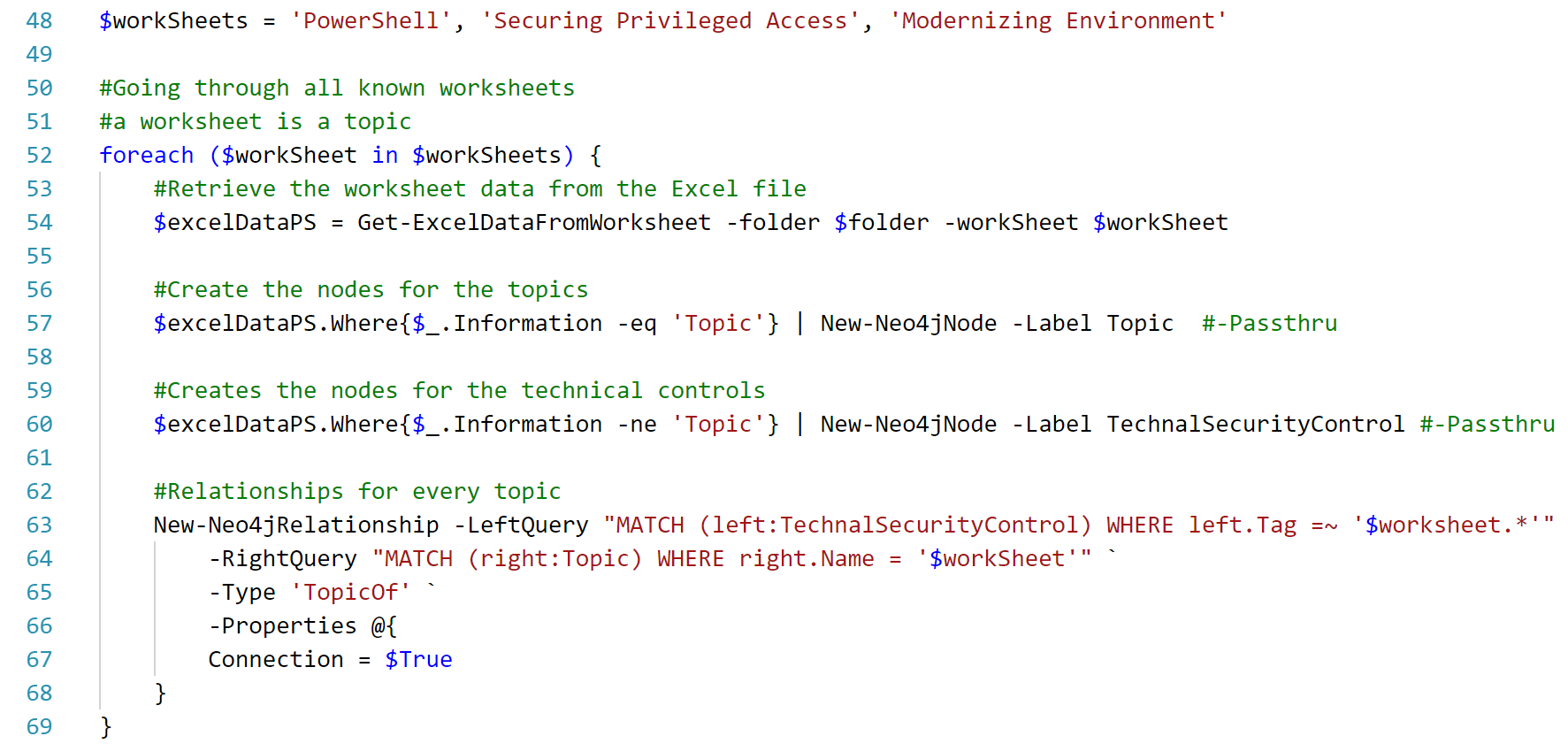
Out of this data, we created new nodes in the Neo4j of type 'Topic' and 'TechnicalSecurityControl' and also the regarding relationships between these nodes. In addition, we added the types (Prevention, Detection, Respond) to the graph and their relationships:

After finishing these easy tasks, we had our first visualisation ready and going:
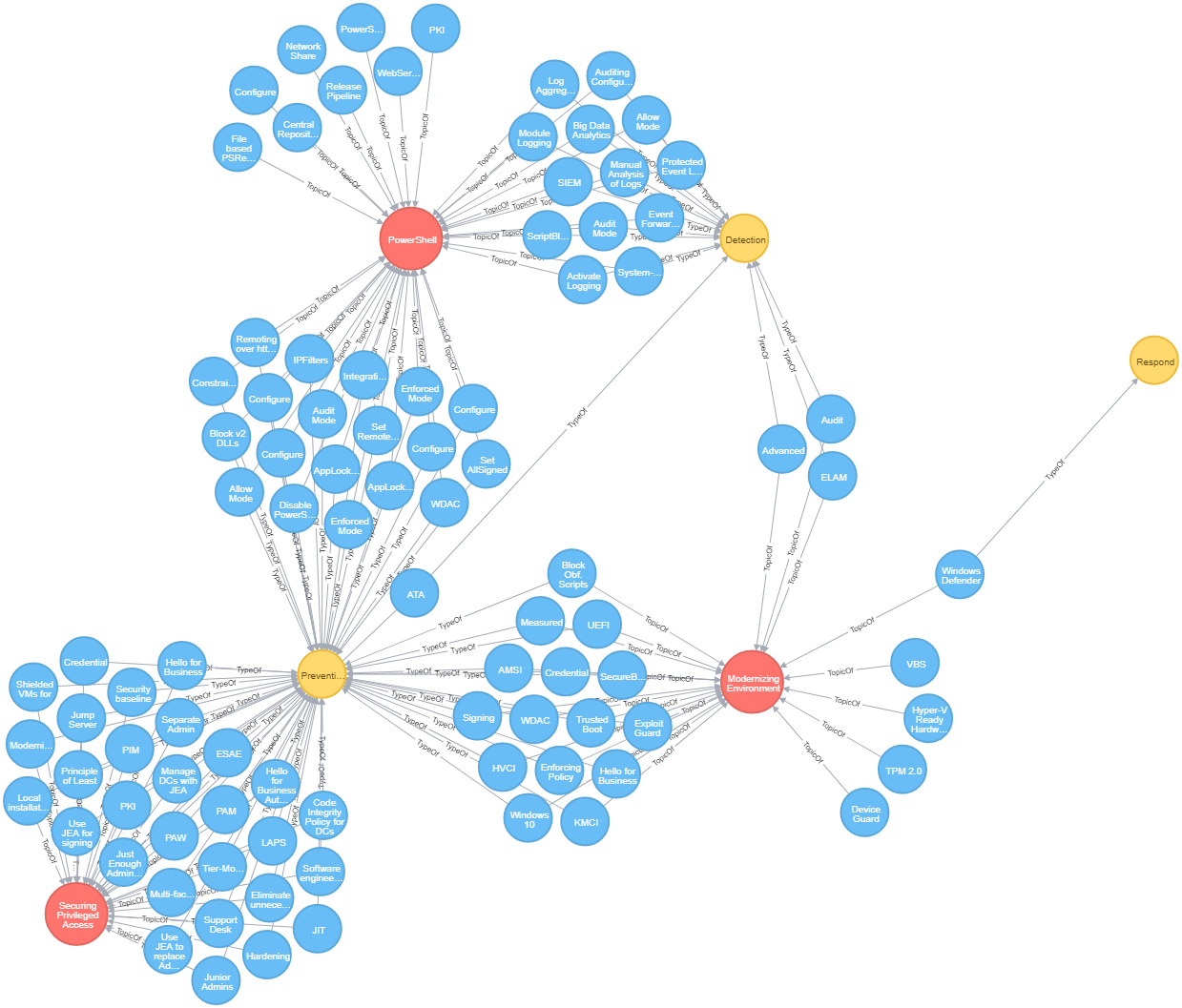
What can you now do with our first implementation?
You can fill up your implemented technical security controls and filling also the 'done' property and afterwards use the following filters to retrieve your personal prioritization list:
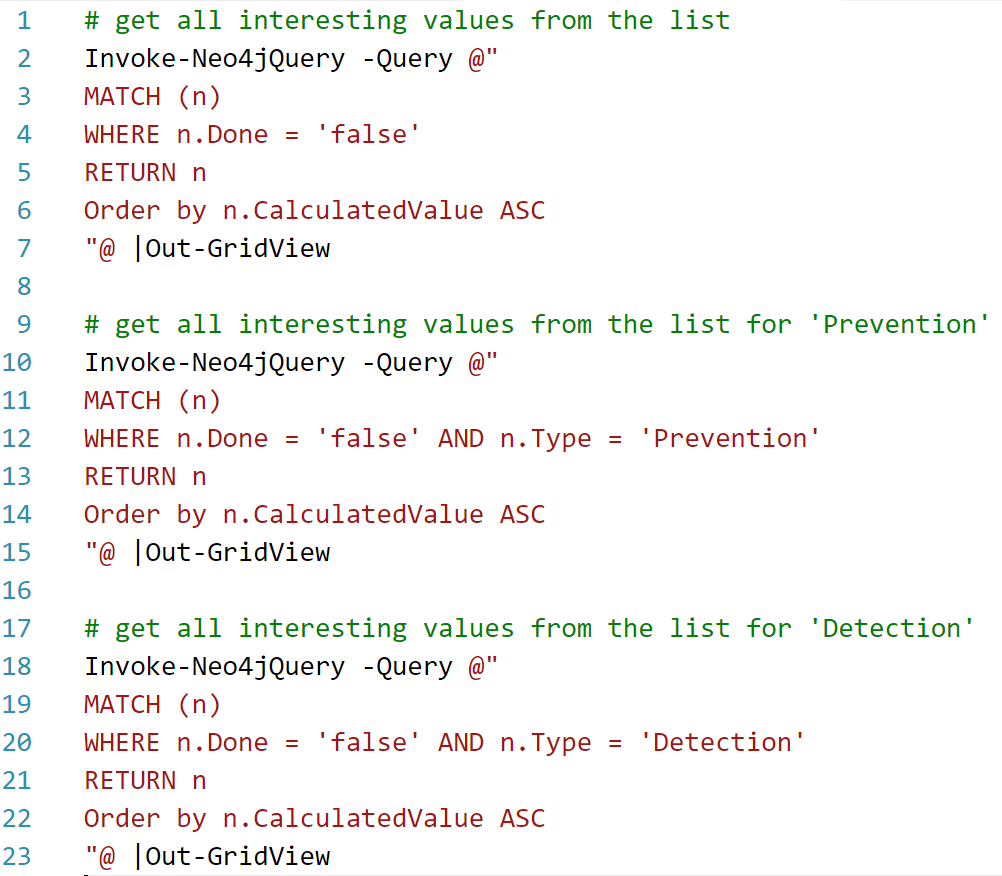
As a result, you will get a similar list as this one, which is sorted on the CalculatedValue attribute:

So far - not bad, but we have just started this project. We now recognized that the graph has much more potential and therefore we will need to completely restructure our data.
And what are our next goals?
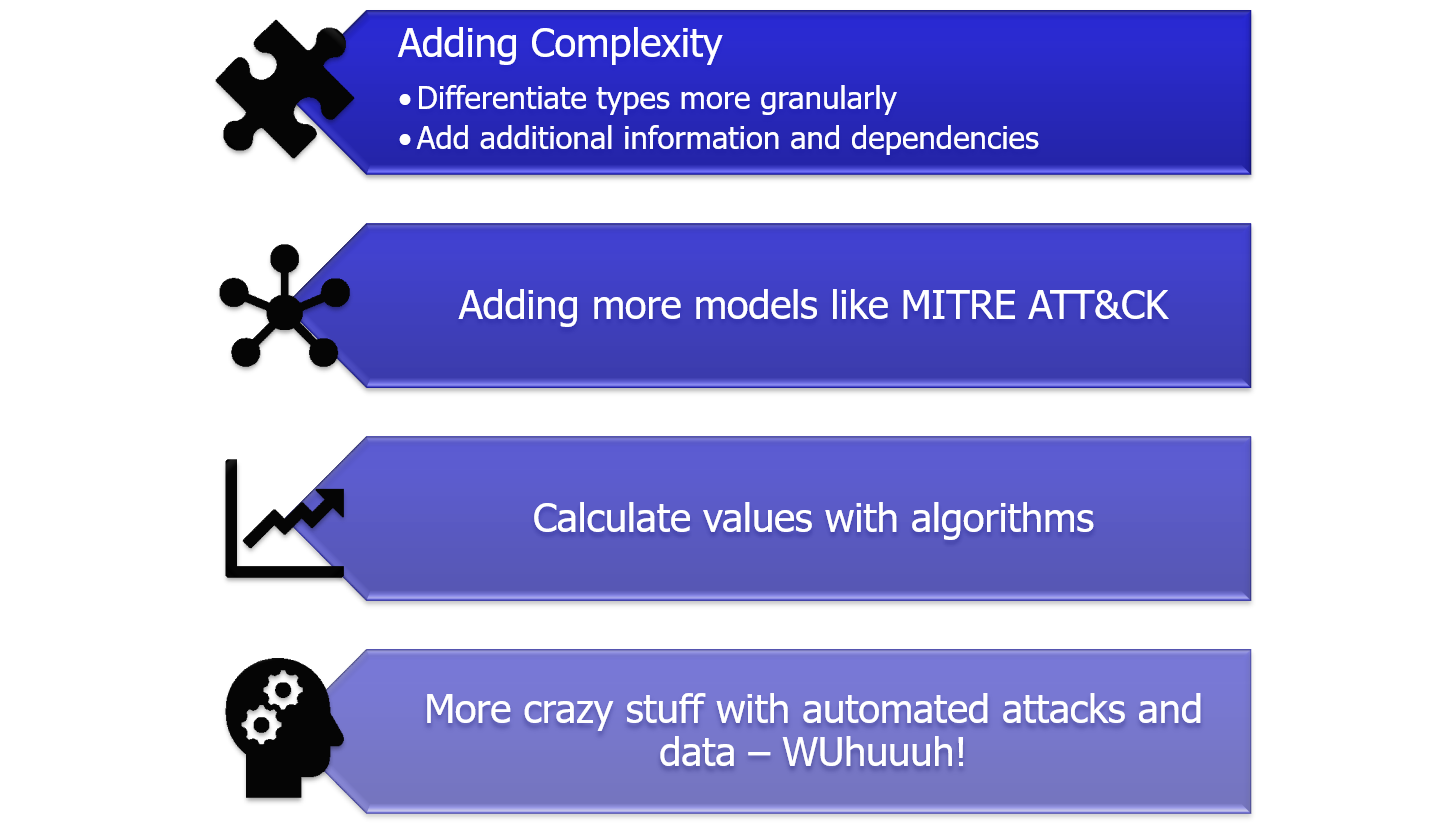
We want to clean up the data a little bit more and extend it with complexity - adding network and forensic analysis etc. In addition, we will add some more models to it, making the connections between them and adding algorithms underneath to make this prioritization list a little more objective. But we also plan to add more automation into the graph itself and possibly work with some models out of the Machine Learning area to retrieve more information and use-cases for it. We have some great plans - don´t miss it!
Call to Action!
Here is now what you have to do. Yes - exactly - you! Try to prioritize your current security controls and if you missed some of the high prioritized controls, implement them asap.

General Recommendation
And last, but not least - here are some recommendations, which you should always implement:

Thank you very much for reading. We will continue to work on this project with high ambition and stay tuned.
All the best,
David das Neves
Premier Field Engineer, EMEA, Germany
Windows Client, PowerShell, Security
Julien Reisdorffer
Sr. Consultant, EMEA, Germany
Global Cybersecurity Practice




