Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
With single sign-on deployments, a connection between an Outlook client and Exchange Online requires authentication with ADFS (Active Directory Federation Services) or third-party ID providers. However, there are scenarios where the authentication process with ADFS or ID providers can be skipped with the help of caches for a certain amount of time after a successful authentication.
We will explain how authentication cache works in two different scenarios; Basic authentication and Modern authentication.
Basic authentication
Exchange Online caches a successful authentication for up to 24 hours. However, these caches may be deleted sooner depending on the server-side spare capacity. It is also difficult to say exactly how long Outlook can use the cache in each case because multiple factors have to be taken into account, but it usually varies from a few hours to 24 hours.
As mentioned before, when the client is allowed to use the cache, the authentication process with ADFS or ID providers is skipped. Therefore, for example, a newly added claim rule in ADFS won't be applied to the client as long as the authentication in ADFS is skipped with the help of caches.
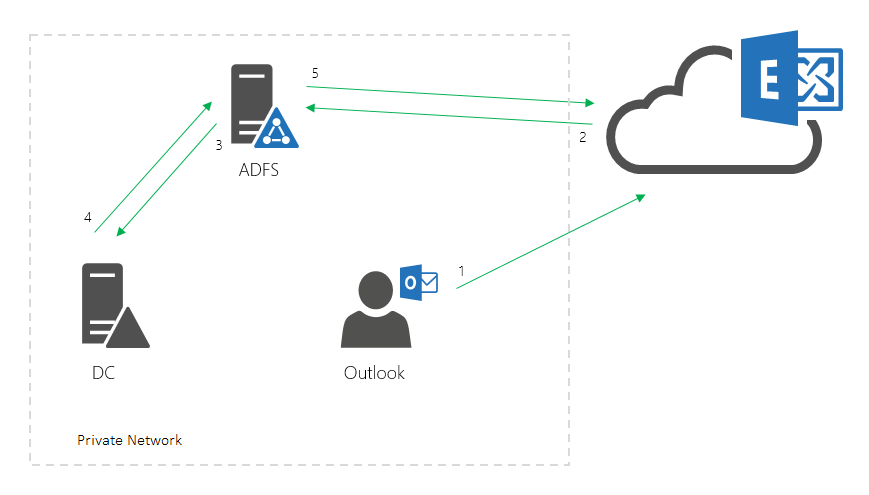
Here is a simplified diagram of single sign-on basic authentication. It focuses on the process where Exchange Online receives the client request, and then requests a security token.
Modern authentication
With modern authentication, tokens are provided to the client side after a successful authentication. While these tokens are valid, the authentication process with ADFS or ID providers can be skipped.
For details on token lifetimes, please refer to the article below.
Title: Session timeouts for Office 365
URL: https://support.office.com/en-us/article/37a5c116-5b07-4f70-8333-5b86fd2c3c40
Modern authentication uses access tokens and refresh tokens to grant uses access to Office 365 resources using Azure Active Directory. An access token is a JSON Web Token provided after a successful authentication and is valid for 1 hour. A refresh token with a longer lifetime is also provided. When access tokens expire, Office clients use a valid refresh token to obtain a new access token. This exchange succeeds if the user’s initial authentication is still valid.
Refresh tokens are valid for 14 days, and with continuous use, they can be valid up to 90 days. After 90 days, users will be asked to re-authenticate.
Refresh tokens can be invalidated by several events such as :
- User’s password has changed since the refresh token was issued.
- An administrator can apply conditional access policies which restrict access to the resource the user is trying to access.
Session lifetimes with modern authentication are dependent on the validity of access tokens and refresh tokens, and the caches on the Exchange Online side do not affect the duration.
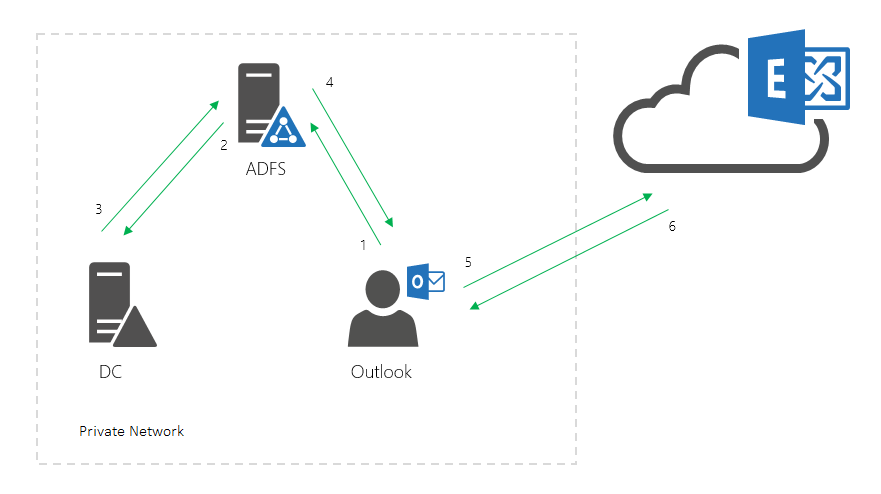
Here's a diagram of modern authentication. This is simplified and the prior authentication process is left out for a comparison purpose. It focuses on the process of the client requesting and receiving the token.