A Quick Look at P3P
Internet Explorer supports a cookie-restricting privacy feature called P3P. Web developers often get tripped up by it because no other browser implements the P3P standard.
I’ve written about IE’s cookie control features previously (and more comprehensively), but here’s a summary of the “least you need to know.”
P3P Made Simple
By default, IE will reject cookies coming from 3rd-party contexts. A 3rd-party context is one where the domain on the content is different than the domain of the page that pulls in that content. Possible third-party contexts include pretty much any element that accepts a URL: <script>, <img>, <link>, <frame>, <iframe>, <audio>,<video>, et cetera. It also includes cross-domain XmlHttpRequests which attempt to send cookies when the withCredentials flag is set.
For instance, consider a webpage with a subframe, like this:
The 1st-Party Context is domain1.com and the 3rd-Party Context is domain2.com. By default, if the HTML content in the IFRAME tries to set a cookie, it will fail to do so. IE will behave as if the cookie from domain2.com doesn’t exist.
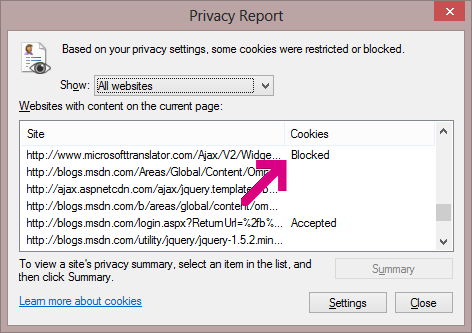
Unfortunately, IE’s F12 Developer Tools won’t show a warning when this happens. In older versions of IE, you’d see a little “eye” icon in the IE status bar, but that was removed in IE9. Today, to see that a cookie has been rejected, you have to click View > Web Page Privacy Policy.
That command will show you a summary of what happened to cookies during the loading of the page. For instance, loading this blog post yields the following:
Declare Your Policy
To get IE to accept cookies from your server in a 3rd-party context (or to get IE to resend a previously-set cookie to your server when it is accessed in a 3rd-party context), you must declare the privacy policy that governs how your cookies will be used. That declaration takes the form of a P3P header on the HTTP response (or, less commonly, a META tag with the same content).
For instance, this blog sends the following:
P3P: CP="ALL IND DSP COR ADM CONo CUR CUSo IVAo IVDo PSA PSD TAI TELo OUR SAMo CNT COM INT NAV ONL PHY PRE PUR UNI"
Each token in the Compact Policy (CP) attribute has a particular meaning that explains in a machine-readable way how the cookie will be used. Fiddler’s Cookies Response Inspector breaks down the policy into English (well… legalese, at least :-)
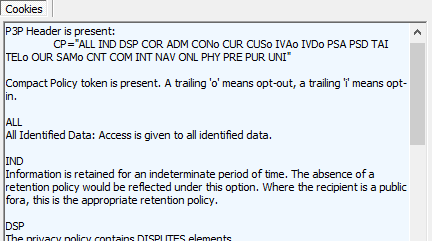
Upon receiving a cookie, IE will automatically the cookie’s privacy policy to the user’s configured preferences when deciding whether or not to accept, restrict, or block the cookie.
The P3P statement must be provided by the 3rd party content. In our example:
…when the subframe tries to set a cookie, IE only considers the P3P statement from domain2.com. Adding a P3P statement to domain1.com will NOT change the cookie handling for the subframe.
A P3P statement is a legal declaration of how your cookie will be used. You shouldn’t just throw “whatever works” into a P3P header, or you might find yourself in violation of national privacy laws and/or subject to civil lawsuits.
Can’t Get Enough?
There’s tons more to learn about P3P (see this and this) but here are a few quick notes:
- P3P is only evaluated for certain security zones (Internet and maybe Trusted)
- Users can reconfigure their P3P controls to be more or less restrictive
- Beyond accepting or blocking cookies, P3P can also leash (cookie will only be sent in a 1st party context) or downgrade (persistent cookie will be converted into a session cookie and discarded at the end of the session)
- For April Fools Day in 2011, I jokingly proposed an evolution of P3P called P5P.
-EricLaw
MVP – Internet Explorer
Update: P3P is currently non-functional in the current Windows 10 preview build; although all of the UI remains present, it has no effect. No announcement has been made about the future of P3P.
Comments
Anonymous
September 17, 2013
The comment has been removedAnonymous
September 17, 2013
There is an option called "Enable Strict P3P Validation" in Internet OptionsAdvanced. What does it do and why is it not enabled by default?Anonymous
September 18, 2013
@Whale: Great question, and it's related to Mog0's question. Google and Facebook send a P3P policy which asserts that they do nothing with the cookies they send (obviously counterfactual). I wrote about that behavior here: blogs.msdn.com/.../google-bypassing-user-privacy-settings.aspx The "Enable Strict P3P Validation" setting causes statements with undefined tokens (like Google and Facebook) to be treated as missing. There's a test page which allows you to explore this setting here: http://webdbg.com/test/cookie/Anonymous
September 29, 2013
Some resources for P3P generation are listed here: www.p3ptoolbox.org/.../resources1.shtml