Initial revelations and results of the Citadel botnet operation
Posted by Richard Domingues Boscovich
Associate General Counsel, Microsoft Digital Crimes Unit
Just over two weeks after Microsoft, financial services industry leaders, technology industry partners and the FBI took action against more than 1,400 Citadel botnets, I am pleased to share that at least 2 million computers have been freed from the cybercriminals.
As Reuters reported, we believe this is a very conservative number. Our preliminary data shows that from June 9 to June 15, nearly 1.3 million unique Internet Protocol addresses have checked into our system (known as a sinkhole) from computers infected with Citadel. Currently, we are associating one IP address with one infected computer, but there could be multiple infected computers using one address. For example, preliminary results show that there were more than 1.9 million infected computers when we analyze unique IPs + User-Agents. A user agent is an application that connects to the Internet and includes things like browsers. Over the next few weeks, we’ll dig further into our data to determine exactly how many individual computers are associated with each IP we’ve identified.
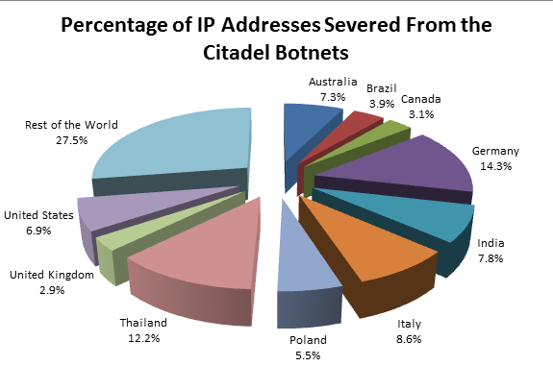
According to our data, the highest number of infections were found in Germany, followed by Thailand, Italy, India, Australia and the U.S. Because the court order only allowed us to take control of Citadel infrastructure hosted in the U.S. and our partners overseas severed the other half of the botnets, it’s possible that the total number of freed computers around the globe could exceed our conservative 2 million figure.
We believe this was a very successful disruptive action, and are confident that we were able to sever most of the Citadel botnets we set out to target. This was also an extremely challenging operation, technologically and logistically, and we’re extremely pleased with what we’re seeing. As stated from the outset, the goal of this operation was to protect the public by strategically disrupting Citadel’s operation, helping to quickly release victims from the threat, and making it riskier and more costly for the cybercriminals to continue doing business. As we have done in prior botnet operations, Microsoft is now able to use the intelligence gained from this operation to partner with organizations around the world to help rescue people’s computers from the control of Citadel, helping to reduce the size of the ongoing threat that these botnets pose, and make the Internet safer for consumers and businesses worldwide. In addition, just as we have done in prior operations such as Rustock and Zeus, we use the evidence gathered in our civil actions to refer cases to law enforcement for criminal prosecution when possible.
Meanwhile, we are also working closely with key researchers to further protect the public from Citadel. The security research community is doing important work on monitoring this threat and other malware variants in the wild. Microsoft is working to get essential information from our system as quickly as possible to researchers such as Shadowserver to support victim notification, and most importantly, remediation. Microsoft’s commitment to trustworthy partnership with the research and enforcement community to help protect the public from cyber threats remains unchanged. We will continue to partner with the security community around the world in our disruptive actions as we strive to help protect our customers and increase the risk and costs for cybercrime to both deter crime and put cybercriminals out of business.
This case and operation are ongoing, and we’ll continue to provide updates as they become available. To stay up-to-date on the latest developments on the fight against cybercrime, follow the Microsoft Digital Crimes Unit on Facebook and Twitter.