Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Summary
This blog will guide you through the steps required to configure, test and troubleshoot sending / receiving e-mail from SharePoint to Exchange using TLS encryption.
Steps (there are many, only because I have included many tips along the way)
Install SMTP and Telnet on the SharePoint App Server using server manager
Or with PowerShell (why? ... because it's fun and good to practice). To install SMTP with PowerShell, check out my script in the link below.
Configure SMTP with IIS 6 manager
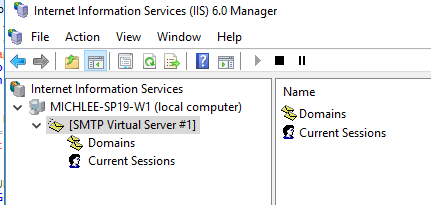
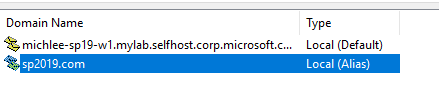
Go to domain and add a new alias for your SharePoint Farm.
Example: sp2019.com
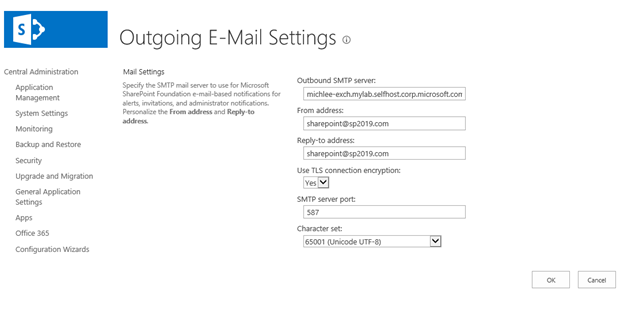
Configure incoming email settings from Central Admin.

Configure Outgoing Email Settings.
Port 587 will use secure e-mail settings from the Exchange receive connector
You can see this from the properties of the "Client Frontend Receive connector" in Exchange.
Example
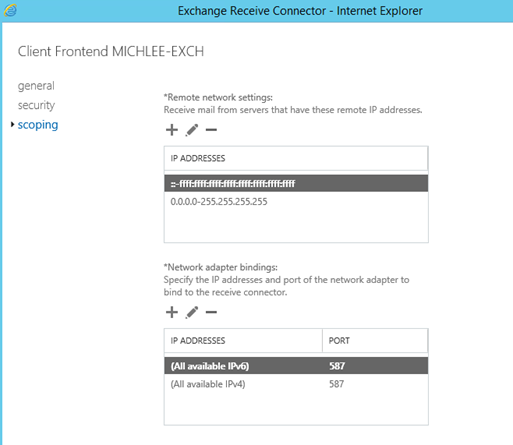
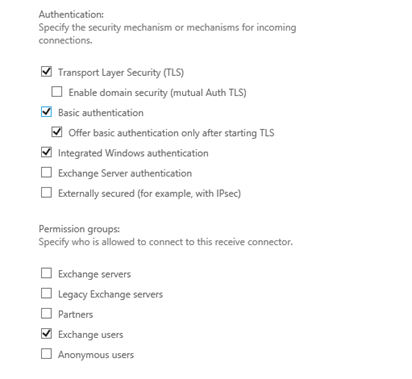
Note: that Anonymous is not enabled.
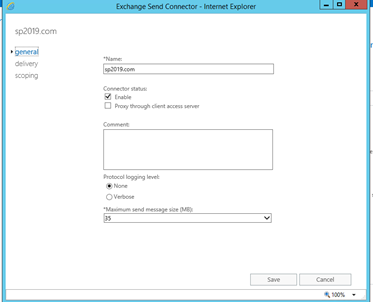
Now you need a send connector in Exchange.
Create a new send connector with the name and scope of the domain used when you configured the domain in SharePoint.
Example:
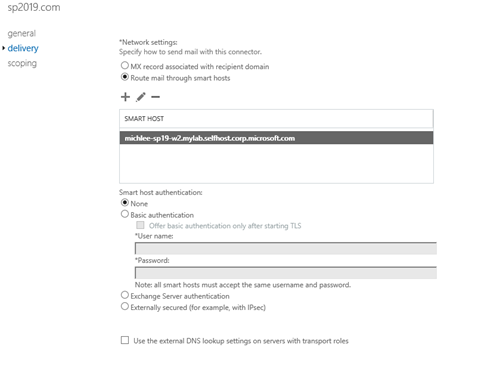
On the delivery page, use the SharePoint Server as the Smart Host using the FQDN.
Example:
Finally scoping, use the name space that matches the domain name used in SharePoint and specify an Exchange server to host the connector.
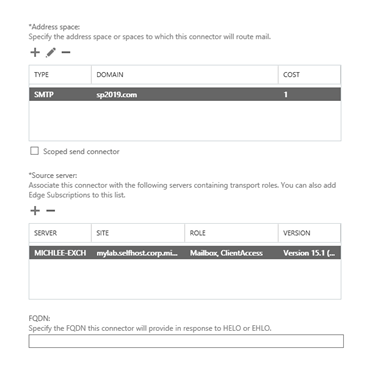
Complete the connector setup.
Back to the SharePoint server for testing.
Create a new document library and add an incoming email alias.
Example:
Subscribe to alerts on the new library so you can test receiving mail from SharePoint as well.
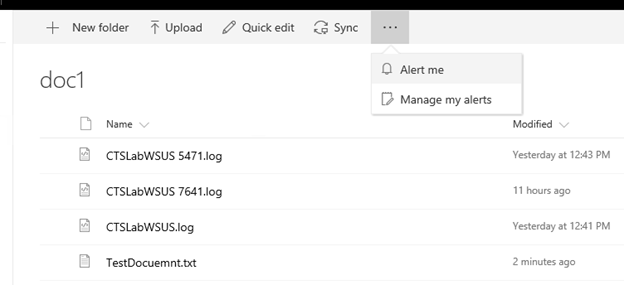
Note: Keep all the default alert settings.
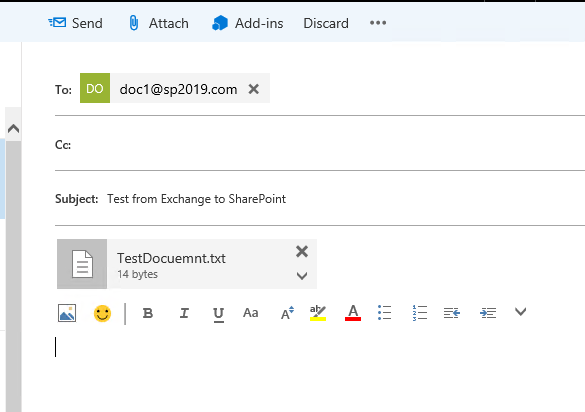
Send mail from Exchange using Outlook or OWA to the email address of the document library.
After sending the E-mail, watch the progress from ULS with a filer of "category contains e-mail".
Example:
12/07/2017 18:57:17.94 OWSTIMER.EXE (0x0408) 0x15A0 SharePoint Foundation E-Mail 6871 Information The Incoming E-Mail service has completed a batch. The elapsed time was 00:00:00. The service processed 0 message(s) in total. b163349e-cea7-101d-e655-81bcc502273a 12/07/2017 18:58:17.18 OWSTIMER.EXE (0x0408) 0x1BB0 SharePoint Foundation E-Mail 6871 Information The Incoming E-Mail service has completed a batch. The elapsed time was 00:00:00. The service processed 0 message(s) in total. c063349e-1e1e-101d-e655-807f49513997 12/07/2017 18:59:19.08 OWSTIMER.EXE (0x0408) 0x2798 SharePoint Foundation E-Mail 6871 Information The Incoming E-Mail service has completed a batch. The elapsed time was 00:00:01.6876203. The service processed 1 message(s) in total. The service successfully processed 1 message(s): Message ID: <09866b7f69a84eb0b392c8641253f8b6@mylab.selfhost.corp.microsoft.com> ce63349e-6ed1-101d-e655-86b37f8794b 12/07/2017 18:59:32.44 OWSTIMER.EXE (0x0408) 0x23E0 SharePoint Foundation E-Mail axudz Monitorable SPMailMessageHelper.IsManagedSmtpClientRequired: Returning true - the managed SMTP client is required by flight or debug flag settings. d263349e-fe7c-101d-e655-885cf85017f0 12/07/2017 18:59:32.46 OWSTIMER.EXE (0x0408) 0x23E0 SharePoint Foundation E-Mail axudz Monitorable SPMailMessageHelper.IsManagedSmtpClientRequired: Returning true - the managed SMTP client is required by flight or debug flag settings. d263349e-fe7c-101d-e655-885cf85017f0 12/07/2017 18:59:32.46 OWSTIMER.EXE (0x0408) 0x23E0 SharePoint Foundation E-Mail axudz Monitorable SPMailMessageHelper.IsManagedSmtpClientRequired: Returning true - the managed SMTP client is required by flight or debug flag settings. d263349e-fe7c-101d-e655-885cf85017f0 12/07/2017 18:59:32.46 OWSTIMER.EXE (0x0408) 0x23E0 SharePoint Foundation E-Mail ay53q Monitorable SPMailMessageHelper.IsOutboundMailPortAndEnableSslEnabled: Returning true - the OutboundMailPortAndEnableSsl flight is enabled.d263349e-fe7c-101d-e655-885cf85017f0 12/07/2017 18:59:32.46 OWSTIMER.EXE (0x0408) 0x23E0 SharePoint Foundation E-Mail a2ymj Monitorable SPMailMessageHelper.CreateHeaders: X-SpMailMessageId = 7d97c051-221b-4031-95fc-cd71013d3d86d263349e-fe7c-101d-e655-885cf85017f0 12/07/2017 18:59:32.46 OWSTIMER.EXE (0x0408) 0x23E0 SharePoint Foundation E-Mail ayrng Monitorable SPMailMessageHelper.ShouldSendViaEws: Delegate control flight is OFF, so don't send mail via EWS. d263349e-fe7c-101d-e655-885cf85017f0 12/07/2017 18:59:32.46 OWSTIMER.EXE (0x0408) 0x23E0 SharePoint Foundation E-Mail ax1n2 Monitorable SPSMTPClient.TrySend::start d263349e-fe7c-101d-e655-885cf85017f0 12/07/2017 18:59:32.46 OWSTIMER.EXE (0x0408) 0x23E0 SharePoint Foundation E-Mail awwa4 Monitorable SPSMTPClient.Send::start d263349e-fe7c-101d-e655-885cf85017f0 12/07/2017 18:59:32.46 OWSTIMER.EXE (0x0408) 0x23E0 SharePoint Foundation E-Mail ajs4v Medium Beginning attempt 1 to send mail to recipients: Administrator@mylab.selfhost.corp.microsoft.com. Mail Subject: doc1 - TestDocuemnt.txt. d263349e-fe7c-101d-e655-885cf85017f0 12/07/2017 18:59:32.46 OWSTIMER.EXE (0x0408) 0x23E0 SharePoint Foundation E-Mail ajs4x Medium Attempting to send mail to recipients: Administrator@mylab.selfhost.corp.microsoft.com. Mail Subject: doc1 - TestDocuemnt.txt. d263349e-fe7c-101d-e655-885cf85017f0 12/07/2017 18:59:32.75 OWSTIMER.EXE (0x0408) 0x23E0 SharePoint Foundation E-Mail ajs4y Medium Succeeded in sending mail to recipients: Administrator@mylab.selfhost.corp.microsoft.com. Mail Subject: doc1 - TestDocuemnt.txt. d263349e-fe7c-101d-e655-885cf85017f0Important note: If you are running a min-role server, SMTP will only be processed on the APP servers.
You should see from the logs that incoming and outgoing email was processed, but let's look at the document library to ensure it was processed as expected.
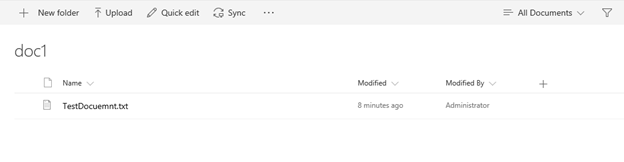
Everything went smooth, did yours? I didn't think so!
What should you do when email is not delivered as planned? If you followed the above steps you may have ran into a problem because I left out one particularly important piece
Let's test sending email from PowerShell, using the SPUtility]::SendEmail" API.
Note: This is just an easier way to troubleshoot this issue, because you are testing and viewing logs from a single place and you get to play with PowerShell and SharePoint APIs.
https://blogs.technet.microsoft.com/mikelee/2017/12/23/test-email-from-sharepoint-using-powershell
This script will write the exception to a log file and let you know why it's not working. If you followed the instructions, you should see the following error.
12/06/2017 12:01:04.99 OWSTIMER.EXE (0x1F08) 0x0F64 SharePoint E-Mail aibbaaibba Monitorable
Failed attempt 1 sending mail to recipients: Administrator@mylab.selfhost.corp.microsoft.com. Mail Subject: doc1 - CTSLabWSUS.log. Error: Exception while sending email: System.Security.Authentication.AuthenticationException: The remote certificate is invalid according to the validation procedure.
at System.Net.Security.SslState.StartSendAuthResetSignal(ProtocolToken message, AsyncProtocolRequest asyncRequest, Exception exception)
at System.Net.Security.SslState.CheckCompletionBeforeNextReceive(ProtocolToken message, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.ProcessReceivedBlob(Byte[] buffer, Int32 count, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.StartReceiveBlob(Byte[] buffer, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.CheckCompletionBeforeNextReceive(ProtocolToken message, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.ProcessReceivedBlob(Byte[] buffer, Int32 count, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.StartReceiveBlob(Byte[] buffer, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.CheckCompletionBeforeNextReceive(ProtocolToken message, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.ProcessReceivedBlob(Byte[] buffer, Int32 count, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.StartReceiveBlob(Byte[] buffer, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.CheckCompletionBeforeNextReceive(ProtocolToken message, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.ForceAuthentication(Boolean receiveFirst, Byte[] buffer, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.ProcessAuthentication(LazyAsyncResult lazyResult)
at System.Threading.ExecutionContext.RunInternal(ExecutionContext executionContext, ContextCallback callback, Object state, Boolean preserveSyncCtx)
at System.Threading.ExecutionContext.Run(ExecutionContext executionContext, ContextCallback callback, Object state, Boolean preserveSyncCtx)
at System.Threading.ExecutionContext.Run(ExecutionContext executionContext, ContextCallback callback, Object state)
at System.Net.TlsStream.ProcessAuthentication(LazyAsyncResult result)
at System.Net.TlsStream.Write(Byte[] buffer, Int32 offset, Int32 size)
at System.Net.Mail.SmtpConnection.Flush()
at System.Net.Mail.ReadLinesCommand.Send(SmtpConnection conn)
at System.Net.Mail.EHelloCommand.Send(SmtpConnection conn, String domain)
at System.Net.Mail.SmtpConnection.GetConnection(ServicePoint servicePoint)
at System.Net.Mail.SmtpClient.GetConnection()
at System.Net.Mail.SmtpClient.Send(MailMessage message)
at Microsoft.SharePoint.Email.SPSmtpClient.SendOnce(MailMessage msg, Boolean useAlternateServer)
at Microsoft.SharePoint.Email.SPSmtpClient.Send(MailMessage msg)
24. Ok, we have a cert error, so let's Enable CAPI2 Logging. 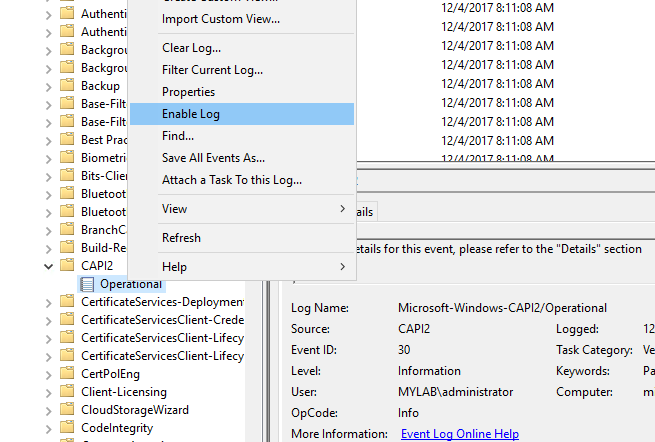
25. Run the script again and look at the CAPI2 log.
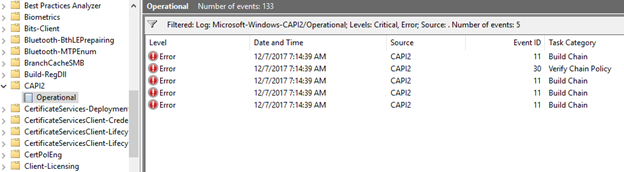
26. Looking at the XML from the critical error, we can see the following information.
<Event xmlns="https://schemas.microsoft.com/win/2004/08/events/event">
<System>
<Provider
Name="Microsoft-Windows-CAPI2" Guid=" {5bbca4a8-b209-48dc-a8c7-b23d3e5216fb} " />
<EventID>11</EventID>
<Version>0</Version>
<Level>2</Level>
<Task>11</Task>
<Opcode>2</Opcode>
<Keywords>0x4000000000000003</Keywords>
<TimeCreated SystemTime="2017-12-07T15:20:59.907316800Z" />
<EventRecordID>203</EventRecordID>
<Correlation ActivityID=" {D1DCD0B2-6D1D-0002-4E57-ECD11D6DD301} " />
<Execution ProcessID="6000" ThreadID="2908" />
<Channel>Microsoft-Windows-CAPI2/Operational</Channel>
<Computer>michlee-sp19-w1.mylab.selfhost.corp.microsoft.com</Computer>
<Security UserID="S-1-5-21-3829927642-1719813900-539600818-500" />
</System>
<UserData>
<CertGetCertificateChain>
<Certificate fileRef="013D37285D4D1E8B459D3E7CA52F137B7F04E062.cer" subjectName="michlee-exch" />
<ValidationTime>2017-12-07T15:19:15.662Z</ValidationTime>
<AdditionalStore>
<Certificate fileRef="03ED211BFEFB109869BA41D87D64832FD077FEB2.cer" subjectName="Microsoft Exchange Server Auth Certificate" />
<Certificate fileRef="ADED905DE483725B676C44043D741F6A613960AC.cer" subjectName="SharePoint Root Authority" />
</AdditionalStore>
<ExtendedKeyUsage />
<Flags value="40000000" CERT_CHAIN_REVOCATION_CHECK_CHAIN_EXCLUDE_ROOT="true" />
<ChainEngineInfo context="machine" />
<CertificateChain chainRef=" {1596272B-11E5-46AA-AAE7-766B70D6C4F9} ">
<TrustStatus>
<ErrorStatus value="20" CERT_TRUST_IS_UNTRUSTED_ROOT="true" />
<InfoStatus value="100" CERT_TRUST_HAS_PREFERRED_ISSUER="true" />
</TrustStatus>
<ChainElement>
<Certificate fileRef="013D37285D4D1E8B459D3E7CA52F137B7F04E062.cer" subjectName="michlee-exch" />
<SignatureAlgorithm oid="1.2.840.113549.1.1.5" hashName="SHA1" publicKeyName="RSA" />
<PublicKeyAlgorithm oid="1.2.840.113549.1.1.1" publicKeyName="RSA" publicKeyLength="2048" />
<TrustStatus>
<ErrorStatus value="20" CERT_TRUST_IS_UNTRUSTED_ROOT="true" />
<InfoStatus value="10C" CERT_TRUST_HAS_NAME_MATCH_ISSUER="true" CERT_TRUST_IS_SELF_SIGNED="true" CERT_TRUST_HAS_PREFERRED_ISSUER="true" />
</TrustStatus>
<ApplicationUsage>
<Usageoid="1.3.6.1.5.5.7.3.1" name="Server Authentication" />
</ApplicationUsage>
<IssuanceUsageany="true" />
</ChainElement>
</CertificateChain>
<EventAuxInfo ProcessName="powershell_ise.exe" />
<CorrelationAuxInfo TaskId=" {C546DBC3-950A-4DF2-A98A-02946E669730} " SeqNumber="3" />
<Result value="800B0109">A certificate chain processed, but terminated in a root certificate which is not trusted by the trust provider. </Result>
</CertGetCertificateChain>
</UserData>
</Event>
27. There is 3 important pieces of information in the error.
- The certificate subject name subjectName="michlee-exch" />
- Error status: <ErrorStatus value="20" CERT_TRUST_IS_UNTRUSTED_ROOT="true" />
- Result value: A certificate chain processed, but terminated in a root certificate which is not trusted by the trust provider.
28. So, what does this all mean? You configured your Outgoing E-mail from SharePoint to use TLS and you don't trust the Exchange self-signed certificate.
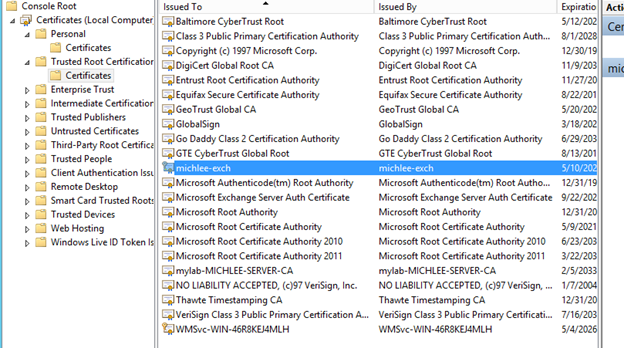
29. Now go to the Exchange Server and find the matching certificate from the certificate snap-in.
30. Export the certificate from Exchange 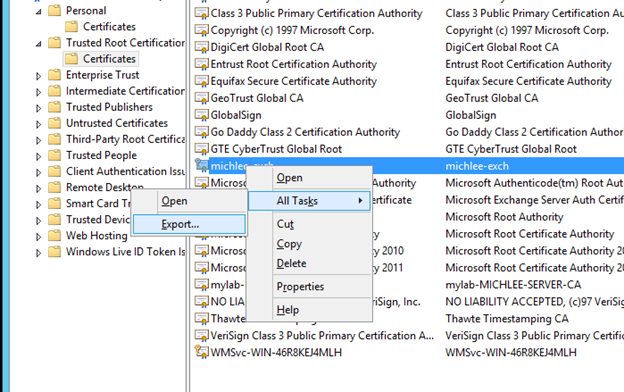
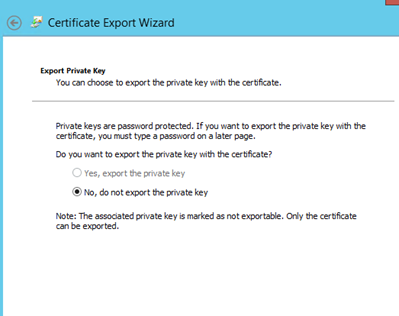
31. Chose "do not export private key"
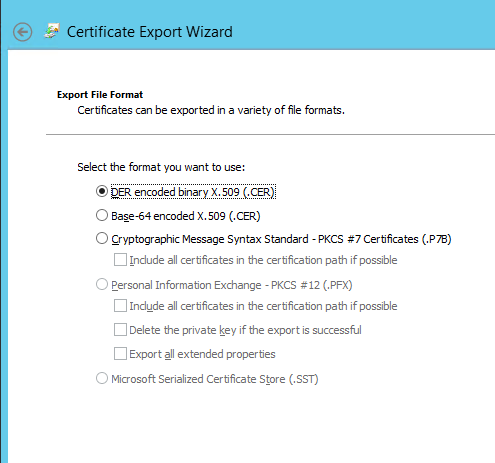
32. Choose DER Encoded format
.
33. Copy the exported certificate onto the SharePoint Server(s).
34. Import the certificate into the SharePoint Servers.
35. Open the Exchange Cert from the SharePoint Server
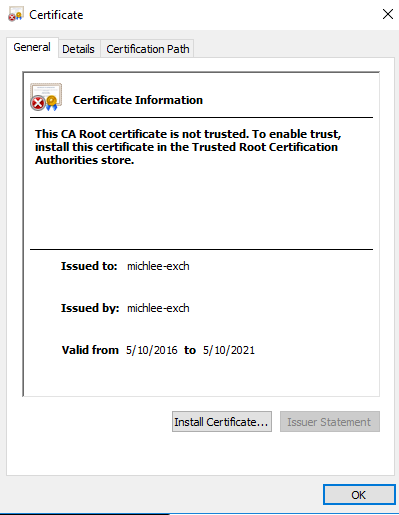
36. Notice when opening the Exchange Certificate from the SharePoint Server, you get a warning stating that the CA Root is not trusted.
37. Choose "Install Certificate", this will start the import wizard 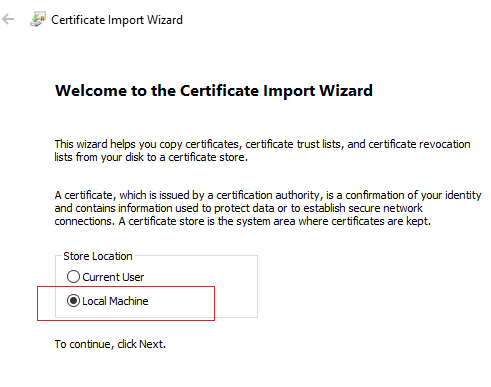
38. The import wizard will start and choose "Local machine".
39. Chose "Place All certificates in the following Store", and choose "Trusted Root Certificate Authorities"
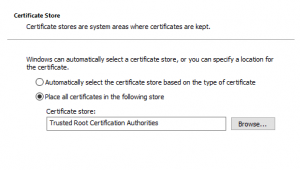
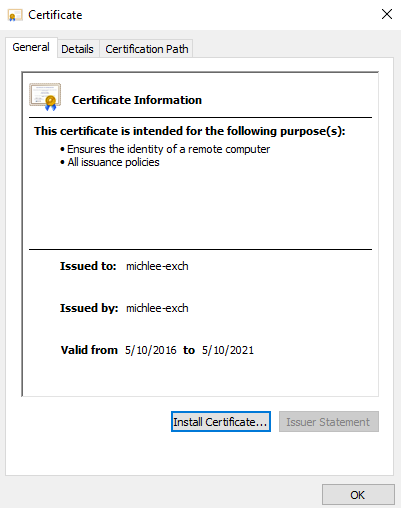
40. Now you should see the certificate is in good shape.
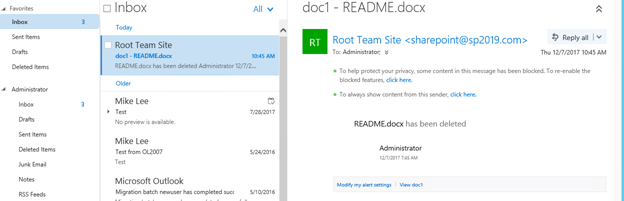
41. Now when SharePoint sends e-mail, it will use TLS encryption and succeed.
42. So, it's working from the OWSTimer inside Sharepoint but failing from PowerShell.
12/07/2017 07:45:34.03 OWSTIMER.EXE (0x0408) 0x1AD0 SharePoint Foundation E-Mail ax1n3 Monitorable SPSMTPClient.TrySend::success 413d349e-9e91-101d-e655-85e7317ffb19
2/07/2017 07:45:34.04 OWSTIMER.EXE (0x0408) 0x1AD0 SharePoint Foundation E-Mail ajs4z Medium Successfully sent e-mail message to recipients: Administrator@mylab.selfhost.corp.microsoft.com. Mail Subject: doc1 - README.docx 413d349e-9e91-101d-e655-85e7317ffb19
43. Sending email will still fail when sent from PowerShell, because the script is passing authenticating at the SMTP level through SharePoint (yet).
12/07/2017 07:48:59.72 PowerShell_ISE.exe (0x1770) 0x0B5C SharePoint Foundation E-Mail ax1n4 MonitorableSPSMTPClient.TrySend::Exception caught; return value from TrySend will be false. Exception: System.Net.Mail.SmtpException: The SMTP server requires a secure connection or the client was not authenticated. The server response was: 5.7.57 SMTP; Client was not authenticated to send anonymous mail during MAIL FROM
at System.Net.Mail.MailCommand.CheckResponse(SmtpStatusCode statusCode, String response)
at System.Net.Mail.MailCommand.Send(SmtpConnection conn, Byte[] command, MailAddress from, Boolean allowUnicode)
at System.Net.Mail.SmtpTransport.SendMail(MailAddress sender, MailAddressCollection recipients, String deliveryNotify, Boolean allowUnicode, SmtpFailedRecipientException& exception)
at System.Net.Mail.SmtpClient.Send(MailMessage message)
at Microsoft.SharePoint.Email.SPSmtpClient.SendOnce(MailMessage msg, Boolean useAlternateServer)
at Microsoft.SharePoint.Email.SPSmtpClient.Send(MailMessage msg)
at Microsoft.SharePoint.Email.SPSmtpClient.TrySend(MailMessage msg, EmailStatusCode& errorCode)
Conclusion (Great, you made to the end!)
If you made it this far, I hope you have e-mail working between SharePoint and Exchange using TLS encryption, or learned some new ways to troubleshoot issues that involve certificates and mail flow from SharePoint.