Microsoft Advanced Threat Analytics support in OMS Security
Summary: Introducing Microsoft Advanced Threat Analytics support in OMS Security.
Currently, OMS Security offers basic integration with Microsoft Advanced Threat Analytics. This integration is based on the event logs that Microsoft Advanced Threat Analytics provides. The advantage of these capabilities is that you can see suspicious activities that Microsoft Advanced Threat Analytics triggers along with other detections related to OMS Security in one single place, which is the OMS Security dashboard.
We are just releasing a new improvement in this integration. The intent is to bring a more detailed explanation about suspicious activities based on Advanced Threat Analytics Syslog. In the following example, the Microsoft Advanced Threat Analytics portal shows a suspicious activity that indicates an attempt to perform a brute force attack.
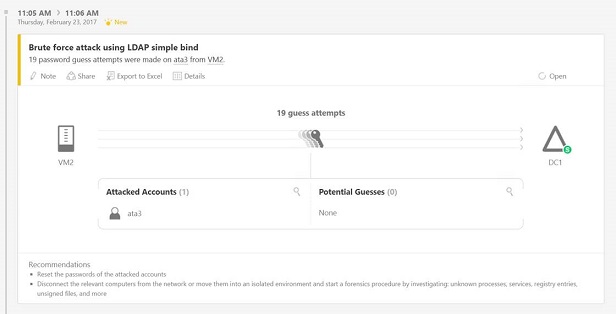
If this Advanced Threat Analytics was integrated with OMS Security, this is the log activity that you would see in OMS Security event log:
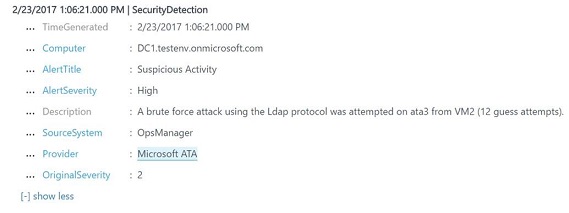
While this log brings some valuable information, the new log experience brings more details about this suspicious activity as shown in the following screenshot:
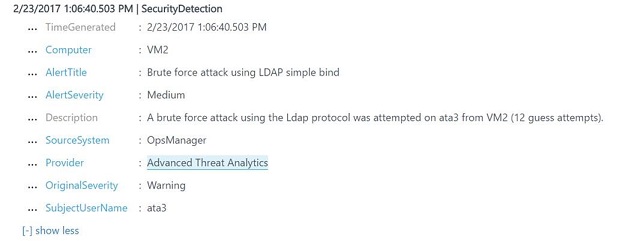
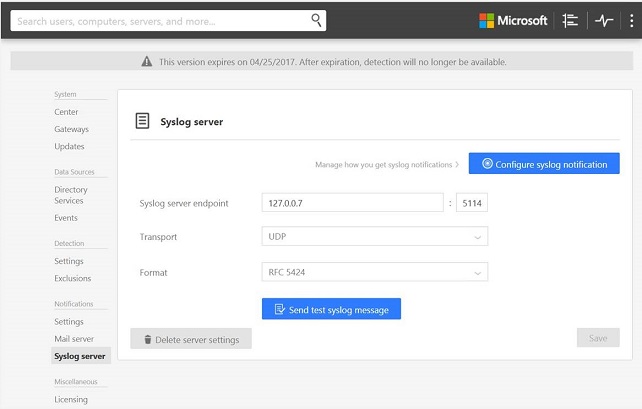
To configure this integration, use the following steps:
- In the Advanced Threat Analytics portal, click Syslog server in the left pane. In the Syslog server endpoint field, type 127.0.0.7 (it must be this address), and type 5114 on the port (recommended). While the port number is a recommendation, any unique port should work.
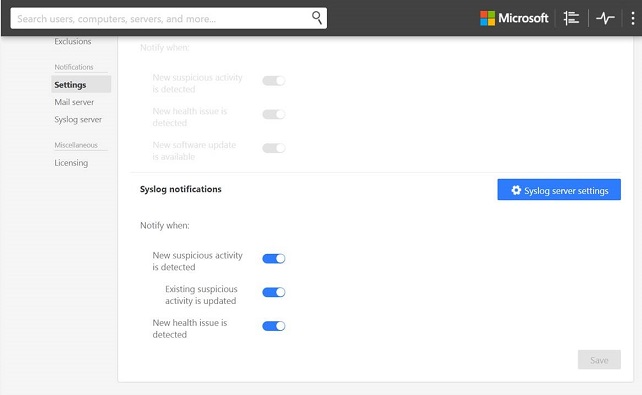
- Click Settings in the left pane, and enable all the Syslog notifications (strongly recommended) as shown in the following screenshot:
- Install OMS agent on the Advanced Threat Analytics Center computer, and configure the agent to use your workspace.
The new capabilities will start to work only after you manually configure at the Advanced Threat Analytics portal as previously described. The new capabilities will not disable the old Advanced Threat Analytics collection capabilities, which means that you might see the following behaviors:
- Suspicious Activities will be received twice (Event log + Syslog).
Such behavior can occur in most scenarios.
- Suspicious Activities will be received only by the new capabilities. Updates are not being sent to Event log.
Such behavior can occur only in some scenarios.
It is also important to mention that the old Advanced Threat Analytics collection capabilities, which are based on Event log, are going to be deprecated in the future.
We hope you enjoy this new integration, and please send us feedback about your experience.