OMS security notable issues
Summary: Notable Issues in the OMS Security and Audit dashboard help you understand issues and their severity.
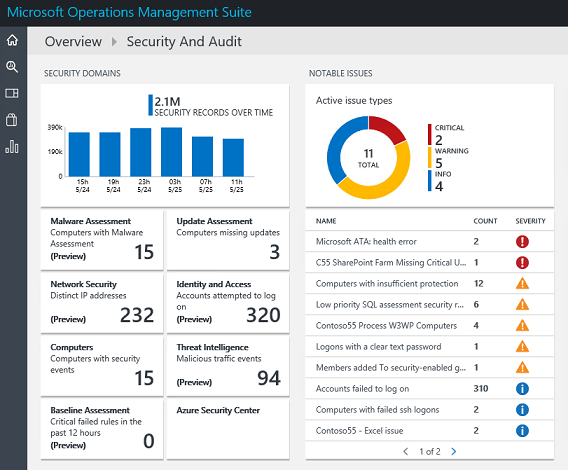
One of the main capabilities of OMS Security and Audit solution is to enable IT Operations to have an accurate view of active issues in all monitored systems. This becomes imperative for hybrid environments that will have resources on-premises and in the cloud. The Notable Issues, located in the OMS Security and Audit dashboard, gives you this snapshot of current issues and their severity as shown in the following screen:
This week we released more details about these notable issues that can assist IT Operations to better understand the type of issue that they are dealing with. You can use the Search tab to drill down on one of the following computer notable issues:
- Computers with cleaned event logs
- Computers with detected threats
- Computers missing security updates
- Computer with guest account logons
- Computers with system audit policy changes
- Computers with insufficient protection
- Computers missing critical updates
- Remote procedure call (RPC) attempts
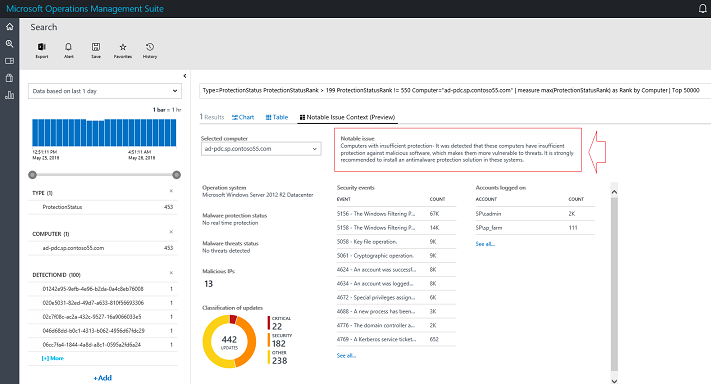
Let’s use the example from the previous screen, in particular the Computers with insufficient protection warning issue, which currently have 12 occurrences. When you click it, the notable issues description is shown beside the computer name as highlighted in the following screen:
The query, which is the notable issue result at first, affects only the list of computers that are relevant for that particular notable issue. All other information is about the selected computer. At the top-left part, you can select one of the computers that the selected notable issue applied on. You can narrow this list by narrowing the notable issue query results (filter to computers with specific operating systems, for example). When you select a computer, you will see some summarized information about it. This can give you some sense about its status and why the notable issue occurred. In this dashboard you can also click:
- Some of the items to further refine the search. For example, select a specific security event to see its details.
- One of the update types to see the raw events for the selected computer.
- One of the security events to see its raw events for the selected computer.
- The security events (See all…) to see all the events that happened on the selected computer (not only the first 10 as in the list).
- One of the accounts to see its raw sign-in events for the selected computer.
- The accounts (See all…) to see all the accounts signed in to the selected computer (not only the first 10 as in the list).
Make sure to explore this feature and send us your feedback!
Yuri Diogenes
Senior Content Developer, CSI
Enterprise Mobility, Azure Security, OMS Security