Monitoring Certificates In SCOM
In almost every SCOM environment I have been involved with the need to monitor certificates has come up. This is the standard management pack I use.
Requirements:
- Powershell - The management pack works on Windows 2003, but it does need powershell to be present on all agent computers.
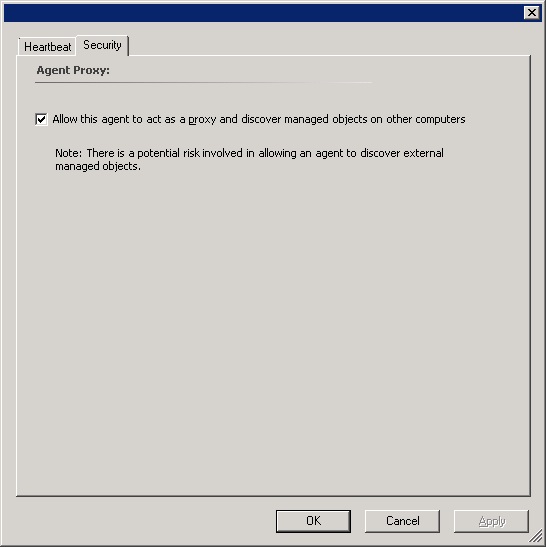
- Agent Proxying - To prevent an alert storm if the same certificate is about to expire on many machines, we monitor identical certificates as a non-hosted entity. To discover this, agents must be allowed to proxy. Agent Proxying is not enabled by default. Please note that if you enable proxying after deploying this management pack, you will need to restart the agent health service to get the agent to resubmit the discovery.
- SCOM 2007 R2 or SCOM 2012.
You can also enable agent proxying via powershell.
SCOM 2012 Syntax:
Get-SCOMAgent | where {$_.ProxyingEnabled.Value -eq $False} | Enable-SCOMAgentProxy
SCOM 2007 Syntax:
$agentlist = get-agent | where {$_.ProxyingEnabled.Value -eq $False}
Foreach ($agent in $agentlist)
{
$agent.ProxyingEnabled = $true
$agent.ApplyChanges()
}
This is a library management pack. So be default it doesn't do anything. I'm including an example management pack that uses it. I have found that certificates are used so differently by organizations that it is hard to make a discovery rule that would result in just the right level of monitoring for the organization.
I provided one discovery data source
- Microsoft.Windows.Certificates.Discovery.DS - You can target it at a windows computer, or any class hosted by a windows computer. There are options to discover or ignore all certificates in the computer's Personal, Root, and Intermediate certificate stores.
I can't possible anticipate the needs of every organization, so if you need a more granular discovery, I'm providing an unsealed version of the management pack, so you can edit the "WHERE" part of the powershell script to suit your own needs. Just change this line in Microsoft.Windows.Certificates.Discovery.DS
$colcert = Get-ChildItem -recurse cert:localmachine\ | WHERE {$_.Thumbprint -ne $null}
To something like this, or whatever meets the needs of your organization.
$colcert = Get-ChildItem -recurse cert:localmachine\ | WHERE {($_.Thumbprint -ne $null) -and ($_.Subject -notmatch "abcd") -and ($_.Issuer -match "qwerty")}
I provided two monitor types
- Microsoft.Windows.Certificates.Expiration.Monitor - Checks to see if a certificate is nearing expiration. If the certificate does not exist, this is not considered to be an error.
- Microsoft.Windows.Certificates.Exists.Monitor - Checks to see if a certificate exists. The certificate's expiration date is ignored.
The monitors do not have to be targeted at certificates. You can target them at any hosted class so long as you can provide a valid principal name, thumbprint, and store.
Values to use for Store
- My = Personal
- Root = Trusted Root CA's
- CA = Intermediate CA's
Thumbprints should be provided without spaces. For example: 97817950d81c9670cc34d809cf794431367ef474
There are also a couple of state views that show the discovered certificates as both hosted and non-hosted.
The example management pack does the following:
- Discover all certificates in the personal certificate store of all windows computers
- Overrides their expiration warning threshold to 14 days
- Checks to see if the "GTE CyberTrust Global Root" certificate exists in the trusted root certificate store
I deliberated for quite a while about whether or not to put in an active monitor by default. Since nothing will be discovered by just the library MP, I decided to place an expiration monitor with a default warning threshold of 10 days on all hosted certificates, and an alerting monitor on the non-hosted class that contains them. You can override the threshold and/or disable the monitor if you want to.
Comments
Anonymous
August 14, 2013
Interesting posting In an environment where mobile endpoiints are used by multiple users, could this be used or edited to enumerate certificates from all users who enrolled for certificates on the endpoint or is this restricted to the local machine account only ?Anonymous
October 01, 2013
What is the relation between your MPs and Certificates Services ... 6.0.7231? Thanks, DomAnonymous
October 01, 2013
There is a request for Microsoft.Windows.Certificates 1.0.0.0 where could I find it? Thanks, DomAnonymous
November 16, 2013
You can download the Microsoft.Windows.Certificates MP in the .ZIP file from this blog post. This MP is totally separate from Active Directory Certificate Services. This is intended for the general monitoring of client and server certificates on all machines, regardless of domain role. If you need to monitor ADCS, you should get that management pack from here for Windows Server 2012 and 2012 R2 www.microsoft.com/.../details.aspx or here for older versions of Windows www.microsoft.com/.../details.aspxAnonymous
March 31, 2014
Very helpful MP, thank you! I was wondering, is there a way to change it to monitor each computer entity so my alerts tell me which machines have expiring certs? I don't often have the same cert on multiple servers.
Thanks!Anonymous
May 01, 2015
Helpful, how can this be used for monitoring certificates on a Load Balancer (URL)??
ThanksAnonymous
May 28, 2015
When we run the Certificate Reports we get "The 'Columlist' parameter is missing a value".Anonymous
April 04, 2016
Apparently I am not importing this correctly, as there are no discoveries, or monitors. Could you explain the installation process? Thanks.