Security Focus: Resetting 'Smart card is required for interactive logon'
Last week I mentioned that there are a number of configuration options we recommend for high privileged users and we discussed 'Account is sensitive and cannot be delegated' .
This week let's look at 'Smart card is required for interactive logon' (SCRIL).
Smart Card Good, Post-It Note Bad
'Smart card is required for interactive logon' forces two factor authentication at logon: i.e. something we have (the smart card), and something we know (a PIN). This increases account security. When SCRIL is configured, the account’s password hash is replaced with a hash derived from a 120-character random value.
We still have a hash... even though SCRIL users are using a smart card and not a password for interactive logon, a high-entropy secret is created to prevent a dictionary attack on NTLM network logons... and, where there are hashes, there's the potential for a Pass-The-Hash attack from a compromised system. Now, here's the rub: the hashes for SCRIL users don't change, so if their credentials are stolen, the attacker can reuse these ad infinitum.
However, unsetting and setting the SCRIL option on a user generates a new hash based on a 120-character random value. Here's some PowerShell to perform SCRIL password resets:
Get-ADUser -Filter {SmartCardLogonRequired -eq $true} | ForEach-Object {
Set-ADUser -Identity $_ -SmartcardLogonRequired $false
Set-ADUser -Identity $_ -SmartcardLogonRequired $true
}
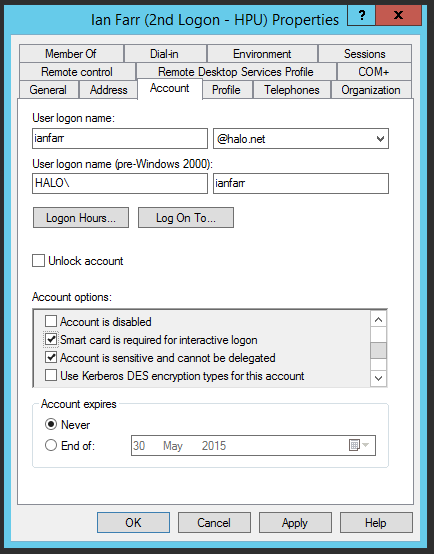
We use Get-ADUser with a filter that gets us all users that are required to use a smart card for interactive logon. We then use Set-ADUser to switch the value of and then back on again. This is the equivalent of unticking and ticking the box in the user properties page (see above). That's it.
Here's how to check which high privileged users have the option set:
Get-ADUser -Filter {(AdminCount -eq 1) -and (SmartcardLogonRequired -eq $true)} | Select-Object DistinguishedName
Of course, you'll need the infrastructure to support smart cards and that's a completely different, more expensive post...
Post Script: when you configure “Smart card required for interactive logon” (SCRIL), do not manually set a password for the account. Doing so undermines the benefits of SCRIL!
Comments
- Anonymous
February 12, 2016
Muy buen post.
Muchas gracias por contribuir al blog - Anonymous
September 08, 2017
just fyi, if users are logged in with cached credentials doing this will lock their AD account. figuring out now how to mitigate that... most likely have them log off and log in on the domain - Anonymous
September 14, 2017
The comment has been removed - Anonymous
September 15, 2017
One area that many managers are looking to have at hand is to detect and be notified "when and who" is the admin that has unchecked this option in AD for a specific user at a specific time. The main reason is to prevent any person that has access to uncheck this option in AD in order to impersonate specific users by simply unchecking the SCRIL for a few minutes then resetting their AD password, impersonate the person then checking back the SCRIL. Is there an easy way through some script other than going through the security event logs on the Domain Controllers to get this information?