Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
To compliment their AD object auditing, one of my customers asked for a script sample to demonstrate an immediate analysis of membership updates to high privileged groups. Before I embarked upon a nice bit of scripting, I had a quick look to see if anyone had already produced something along those lines. My search quickly turned up this excellent post by Mr Ashley McGlone, aka Goatee PFE:
Forensics: Monitor Active Directory Privileged Groups with PowerShell
Please have a read before continuing...
Welcome back!
Unfortunately, my customer can't use the Active Directory Replication cmdlets introduced in Windows Server 2012. I needed to adapt Ashley's function to work with Windows Server 2008 R2. Here's what I did...
Normally, I wouldn't advise using executables with PowerShell unless you really have to. In this instance, given the information that repadmin /showobjmeta provides, there's justification. However, this would mean parsing text rather than dealing with objects... but, if I'm honest, I thoroughly enjoyed the process - 'twas tinged with nostalgia!
Ode to Text
Ah, text and AWK,
How I miss thee.
Sed memory:
Sweet reverie.
Eh? Oh, yeah. I adapted Ashley's function to work with repadmin. Here's my version:
Get-ADPrivilegedGroupUpdates Function (featuring Repadmin.exe)
repadmin helpfully identifies the 'type' of group members:
- LEGACY - this indicates that the member does not support LVR - see here for more information.
- ABSENT - this indicates that the member has been deleted from the group and is tombstoned
- PRESENT - this indicates that the member is a member of the group
Using the 'type' information I can report on whether a member has been added, removed or if the group contain non-LVR members.
Speaking to Ashely once I'd finished, he pointed me in the direction of another excellent post:
Constructed Properties and LVR (Linked-Value Replication)
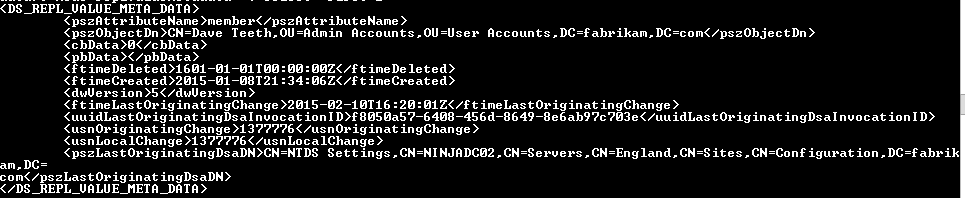
Now, I must admit, I wasn't aware of the constructed attribute msDS-ReplValueMetaData. I've come across a few other constructed attributes, but not that one. Had I known about it, I wouldn't have gone down the repamin route (despite the Joy of Text). Anyway, let's take a closer look:
(Get-ADGroup -Identity "Schema Admins" -Properties msDS-ReplValueMetaData)."msDS-ReplValueMetaData" | Select -First 1
Each member value has its replication metadata stored in XML format for easy parsing. Not only could I use the XML child nodes to work out if the group had been updated in the allotted time frame by using Ashley's comparison, I could also use the fTimeDeleted and fTimeCreated values to work out if a member had been added or removed. Man, more reasons to love PowerShell.
At some point I'll write a new function to make use of msDS-ReplValueMetaData.
Comments
- Anonymous
February 13, 2015
thanks