Federated Identities to Windows Azure Pack through AD FS – Part 1 of 3
In few of the previous posts, Anders Ravnholt discussed Installation & Configuration of WAP and Reconfiguration with FQDNs, ports and Trusted Certificates in detail. In this series, I will discuss how to configure AD FS and enable it to provide Identities to your WAP installation.
Scenario
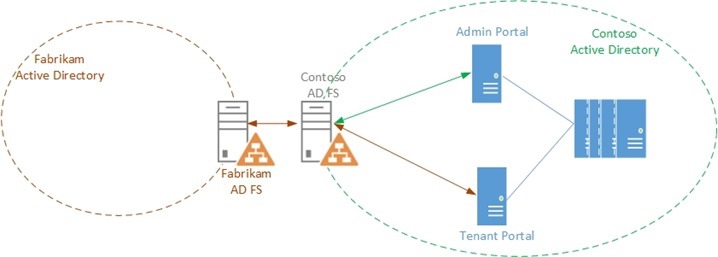
Contoso Inc. is a Service Provider that hosts a private cloud stack and offers Compute resources to their customers. Contoso wants to install a Windows Azure Pack stack and
- Provide administrative access to users from its own Active Directory
- Provide self-service access to the Tenant Portal to users from Fabrikam Corp, one of its customers.
We will run through this scenario in 3 parts:
In this first part of the blog series, we will discuss how Contoso can set up an AD FS instance in their Corp domain.
In the second part, we will discuss how Contoso can set up trust between the AD FS instance and the WAP Admin Portal and provides its users, access to the Management Portal.
In the third part, we will discuss how Contoso can enable Fabrikam's users to access the Tenant portal by establishing trust between Fabrikam's AD FS and Contoso's AD FS.
 Personas
Personas
Rob is a Fabric Administrator who is responsible for maintaining the infrastructure. Rob was tasked with installing the Windows Azure Pack Stack for Contoso Inc.
Mary is the Domain administrator for pcloud.contoso.corp domain in Contoso's Active Directory. Mary has necessary permissions to configure the AD FS linked to the domain.
Alan is a Tenant Administrator who is responsible for Creating and Managing Plans and Subscriptions in Windows Azure Pack.
Assumptions and Scope
- In this scenario, we assume the following about the environment:
- Windows Azure Pack is already set up in the pcloud.contoso.corp domain
- All the components in the environment have been configured with certificates from a Trusted CA
- We also assume the following about you, the reader:
- You are familiar with the installation of the Windows Azure Pack. For more information about Windows Azure Pack deployment, visit https://technet.microsoft.com/en-us/library/dn296432.aspx
- You are familiar with some fundamentals of Claims based Authentication (Refer white paper at https://download.microsoft.com/download/6/F/7/6F7BB9DD-0D65-492F-9180-75A47A520F80/Claims-Based Authentication in WAP.docx )
- You are familiar with AD FS and the AD FS Console. For more information about AD FS visit
https://technet.microsoft.com/en-us/library/hh831502.aspx
- This post will not discuss enabling and configuring AD FS using PowerShell. Details about PowerShell based configuration can be found in the Windows Azure Pack Installation Guide at https://technet.microsoft.com/en-us/library/dn296436.aspx
Enabling the AD FS Role
Mary is the Domain Administrator for the domain ‘pcloud’ which is a domain in the ‘Contoso.corp’ forest. She has the necessary permissions to add an AD FS instance to the pcloud domain.
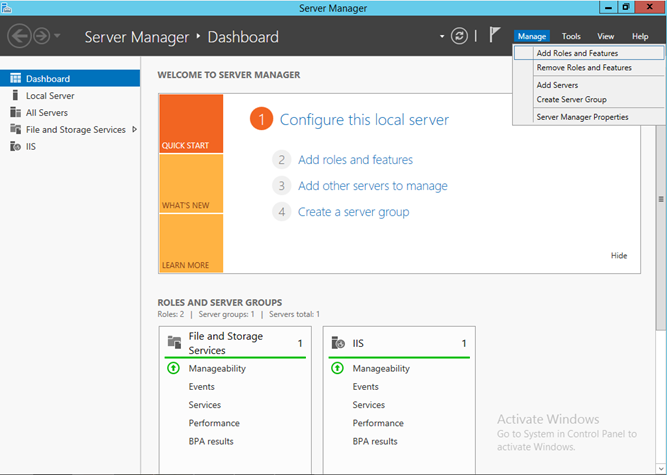
- Mary logs into a machine that is joined to the pcloud domain and which will host the AD FS service. She enables the AD FS role from the Server Manager by clicking on ‘Manage’ and selecting ‘Add Roles and Features’
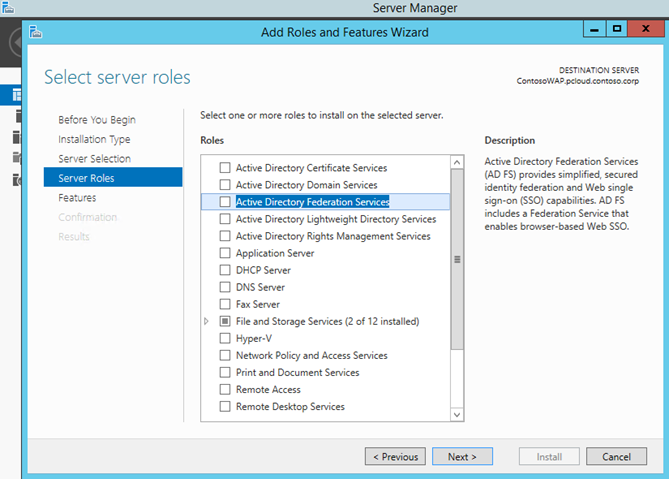
- After selecting the local server, she selects ‘Active Directory Federation Services’ from the Server Roles tab and clicks ‘Next’. The rest of the steps are standard and nothing needs to be changed, so she clicks through the wizard and Clicks ‘Finish’. This will install the AD FS instance on the server
Configuring the AD FS server
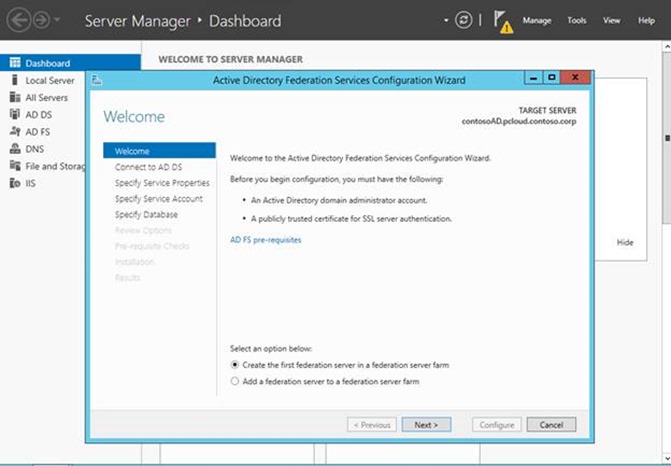
Once Installation completes, Server Manager will show an Exclamation mark in the Notifications to indicate that the role has not been configured yet. Mary clicks on the notification to open the AD FS Configuration Wizard. This is the first server in the AD FS farm, so she selects ‘Create the first federation server in a federation server farm’ and moves on to the next step
She Selects the current user (herself) as the one configuring the farm
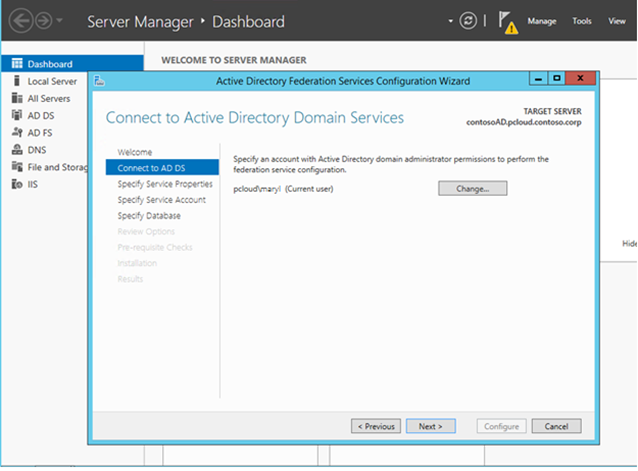
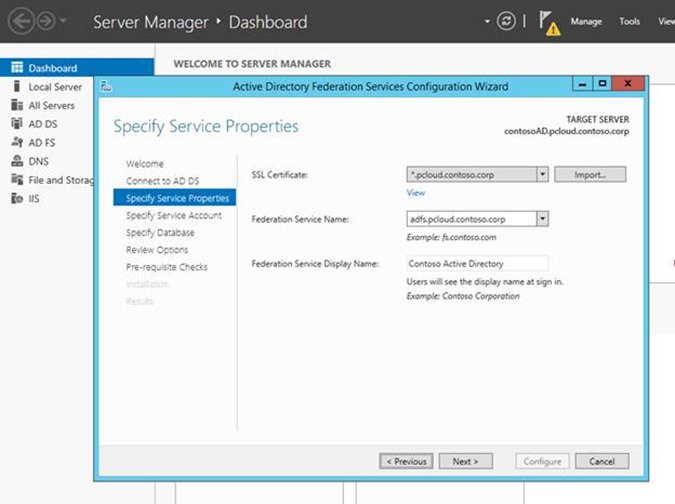
The next step is to configure the Federation Service Name. Note that this can be different from the actual AD FS Machine name. This is the name that will be used by other services to reach AD FS.
In this step, Mary also has to provide a certificate for SSL/TLS based access. This certificate needs to be issued by a trusted Public CA as this is presented to the users when they attempt to login. She already has a wild card cert for *.pcloud.contoso.com that she can use to configure the AD FS server.Note: In case a wild card certificate is not available, the certificate subject name should match with the AD FS Federation Service name
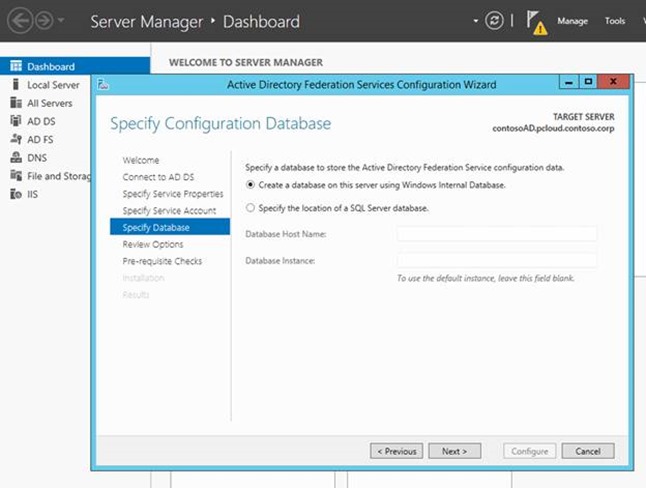
In the Specify Database Step, Mary decides which database to use to store AD FS install. She can either use a Windows Internal Database or a SQL Server.
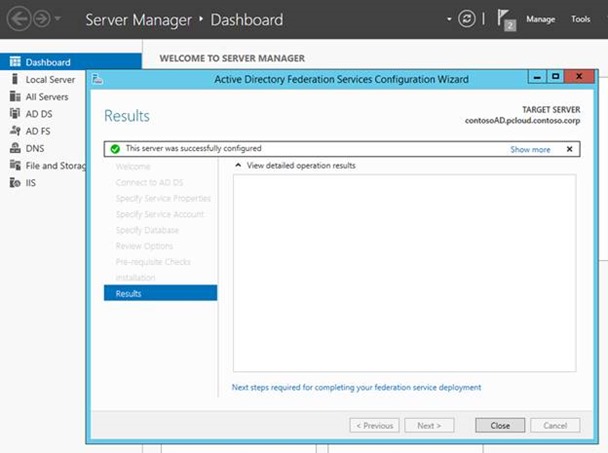
Once all the options are reviewed, she clicks on ‘Configure’ to configure AD FS
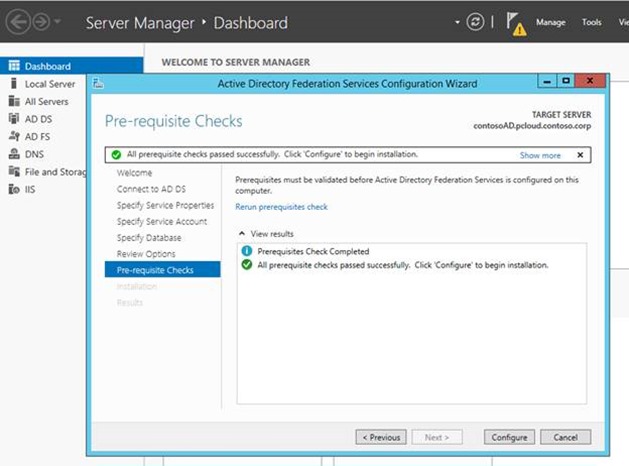
That’s it!
 the pcloud domain now has an AD FS instance that is associated with it and can be used to provide administrative users to the WAP installation
the pcloud domain now has an AD FS instance that is associated with it and can be used to provide administrative users to the WAP installation
You can find more information about AD FS at https://technet.microsoft.com/en-us/library/hh831502.aspx
Visit Part 2 of this blog series for a walkthrough on how Contoso uses this AD FS instance to provide Admin identities to WAP.
Visit Part 3 of this blog series for a walk through on how Contoso uses this AD FS instance to federate with Fabrikam’s AD through a Fabrikam AD FS to provide tenant Identities to WAP.
Comments
- Anonymous
December 17, 2013
Pingback from Federated Identities to Windows Azure Pack through AD FS ??? Part 2 of 3 - Building Clouds Blog - Site Home - TechNet Blogs - Anonymous
December 17, 2013
Pingback from Federated Identities to Windows Azure Pack through AD FS ??? Part 2 of 3 - Building Clouds Blog - Site Home - TechNet Blogs - Anonymous
December 18, 2013
Pingback from Federated Identities to Windows Azure Pack through AD FS ??? Part 3 of 3 - Building Clouds Blog - Site Home - TechNet Blogs - Anonymous
December 18, 2013
Pingback from Federated Identities to Windows Azure Pack through AD FS ??? Part 3 of 3 - Building Clouds Blog - Site Home - TechNet Blogs - Anonymous
December 20, 2013
Pingback from Windows Azure Pack Blog Post Overview on Building Clouds & TechNet - Building Clouds Blog - Site Home - TechNet Blogs - Anonymous
December 20, 2013
Pingback from Windows Azure Pack Blog Post Overview on Building Clouds & TechNet - Building Clouds Blog - Site Home - TechNet Blogs - Anonymous
December 20, 2013
Pingback from Windows Azure Pack Blog Post Overview on Building Clouds & TechNet - Building Clouds Blog - Site Home - TechNet Blogs - Anonymous
December 26, 2013
Pingback from Federated Identities with Windows Azure Pack through AD FS | SME IT guy - Anonymous
January 06, 2014
Pingback from Federated Identities to Windows Azure Pack through AD FS ??? Part 3 of 3 - Anonymous
January 17, 2014
Authentication in Windows Azure Pack follows Claims-based principles and works with a customized ASP - Anonymous
February 19, 2014
In few of the previous posts, Anders Ravnholt discussed Installation & Configuration of WAP and Reconfiguration - Anonymous
May 08, 2014
原文链接: http://blogs.technet.com/b/privatecloud/archive/2013/12/06/windows-azure-pack-installing-amp-configuring - Anonymous
May 12, 2014
原文链接: http://blogs.technet.com/b/privatecloud/archive/2013/12/10/windows-azure-pack-reconfigure-portal - Anonymous
May 18, 2014
原文链接: http://blogs.technet.com/b/privatecloud/archive/2013/12/17/federated-identities-to-windows-azure - Anonymous
May 27, 2014
原文地址: http://blogs.technet.com/b/privatecloud/archive/2014/01/17/setting-up-windows-azure-active-directory - Anonymous
August 04, 2014
These Steps are just too complicated to follow, They need to be simplified to an installer or a Configuration Portal rather than a 3 Page blog where things can go wrong so easily. If this is a Customer scenario why is it hard to configure ? - Anonymous
September 21, 2014
Depuis fin 2013, je suis tombé dans le monde de Windows Azure Pack. C'est un peu comme DirectAccess - Anonymous
November 20, 2014
Great Work!!