Patch Management, a key step towards compliance!
As you might have read, I recently blogged about my infrastructure and the future of a platform towards a better management of compliance – honestly, I actually played with our latest technology .
I wrote about
Now, a necessary and very important next step towards compliance as well as a secure environment is a sound Patch Management process and then – in the second place - the underlying technology. I blogged several times already about Patch Management as I see a lot of companies failing to deliver on this. I recently wrote a post called Patch Management – Cover the whole 9 yards. in there I mention different papers you could/should read:
and I reference Christopher Budd’s Ten Principles of Patch Management:
- Service packs should form the foundation of your patch management strategy
- Make Product Support Lifecycle a key element in your strategy
- Perform risk assessment using the Severity Rating System as a starting point
- Use mitigating factors to determine applicability and priority
- Only use workarounds in conjunction with deployment
- Issues with Security Updates are documented in the Security Bulletin Master Knowledge Base Article
- Test updates before deployment
- Contact Microsoft Customer Support Services if you encounter problems in testing or deployment
- Use only methods and information recommended for detection and deployment
- The Security Bulletin is always authoritative
First of all (and you see that in the articles referenced above) it is of outmost importance to have a process in place. Basically the core schema to run such a process is:
![Cc700845.secmod193_1(en-us,TechNet.10)[1] Cc700845.secmod193_1(en-us,TechNet.10)[1]](https://msdntnarchive.blob.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/rhalbheer/WindowsLiveWriter/PatchManagementthefirststeptowardscompli_D7A6/Cc700845.secmod193_1(en-us,TechNet.10)%5B1%5D_3.gif)
I have seen different complexities to deploy such processes. From highly complex to pretty simply and straight-forward ones. The ones of you who know me know, that my preference is KISS (Keep it Simple, Stupid). So, make the process as complex as necessary and as slim as possible.
So, once you have the process in place and take a conscious decision, the question is about deployment and reporting.
So, let’s talk about technology now.
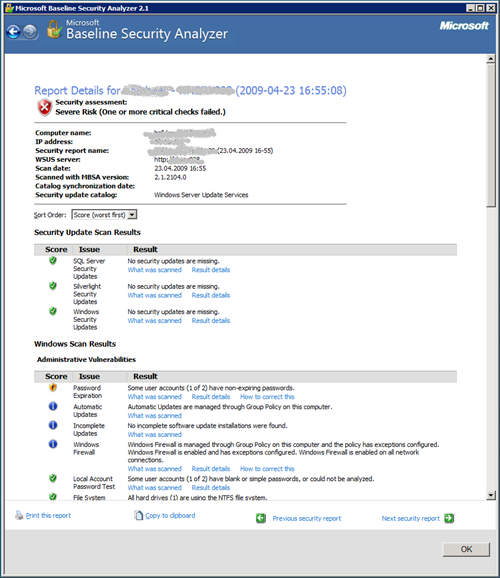
In order to get an overview over the state of your computers, you might use the Microsoft Baseline Security Analyzer. This is an excellent tool to scan your Windows machines and get an overview of the security state of the machines. It might not deliver the same level of sophistication as very expensive tools, but the difference is: We provide it for free and – in my opinion – it gives you a good starting point to look at vulnerabilities including the level of Security Updates of a given PCs. Here is an example of one of these assessments:
But this does not really resolve your base problem about the Security Update compliance of the computers on your network as well as the distribution of them. From my point of view, there are different options to do so:
- If you are a small and medium business, one of the coolest solutions for you to go is System Center Essentials. It is System Center Configuration Manager, System Center Operations Manager and Windows Server Update Services in one package. However, it is limited to 30 servers and 500 clients. If you are in this limit, it rocks.
- System Center Configuration Manager: If you already use this technology to distribute software and configurations, leverage this.
- Windows Server Update Services: It is kind of unbelievable but this is free! So, to be clear – we do not charge for it! You can download and install it and it scales even for large Enterprises (did I tell you already that it is free
?).
- A third-party solution
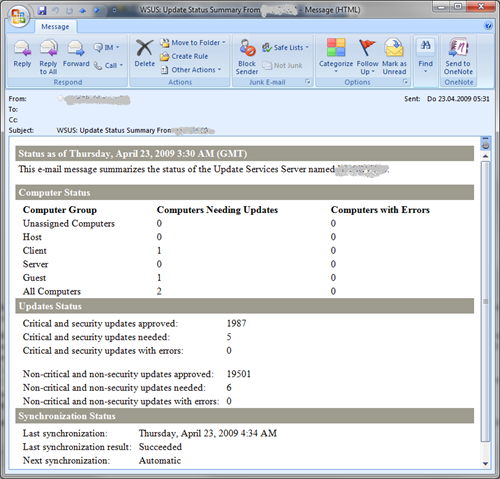
I am using WSUS and am more than happy with it. The way I am organized is, that I get regularly a mail from WSUS with the current state of “the nation”:
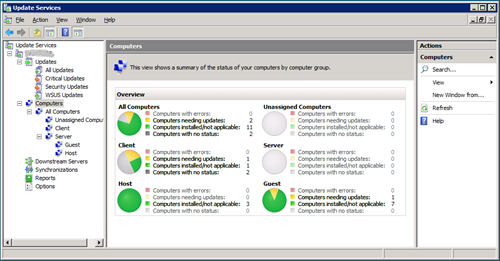
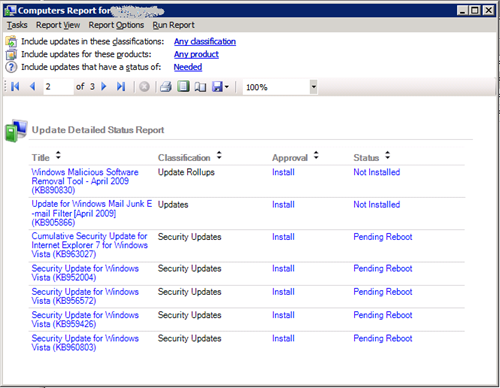
As I am mail-driven, this allows me to see, what I have to do with regards to WSUS. I then can log-on to my WSUS server to get more granular reports:
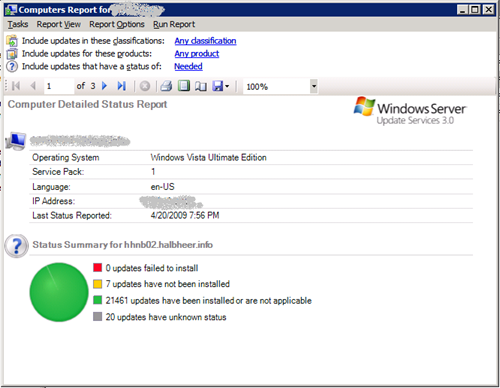
From here on, I can decide, which actions I want to take, based on detailed reports I can get by clicking one of the texts in the UI:
BTW: this machine is patched in the meantime – so do not even think about it
Even if you cannot enforce the security update level technically that way (and we will talk about Network Access Protection in a later post), it at least helps you to understand, where you stand and what you have to do in order to get compliant.
Again (as I did so often) my call to action to you: Make sure that you have a straight-forward process in place and then use technology (like WSUS) to deploy the updates and ensure that you have deployed them correctly!
Roger
Comments
- Anonymous
January 01, 2003
thank you