Microsoft Teams: Protecting against advanced threats
How well do you trust your employees? What about your vendors? I'm constantly coming across organizations that are storing intellectual property and other sensitive data in Microsoft Teams, so they can collaborate with that data in a centralized manner. I'm also learning that most of those organizations are enabling guest access, and allowing outside vendors to have access to that data and the resources within the team. A good example of this is an outside marketing agency that you contract with for event marketing, online marketing, etc. What if a guest of that team (or employee), accidently (or intentionally) uploads malware to the team (but masks it as a file called MarketingRoadmap.pptx), and an employee of the organization opens the file? The malware could now spread throughout your environment.
This is where Office 365 Advanced Threat Protection (ATP) comes in. ATP can help to safeguard your organization from this threat by "detonating" (executing) files uploaded to Microsoft Teams (specifically the SharePoint/Office 365 Group on the back-end) to validate it is a legitimate file and contains no malicious code that can do harm. This feature comes with Microsoft 365 E5, Office 365 E5, or available as an add-on to an existing Office 365 subscription.
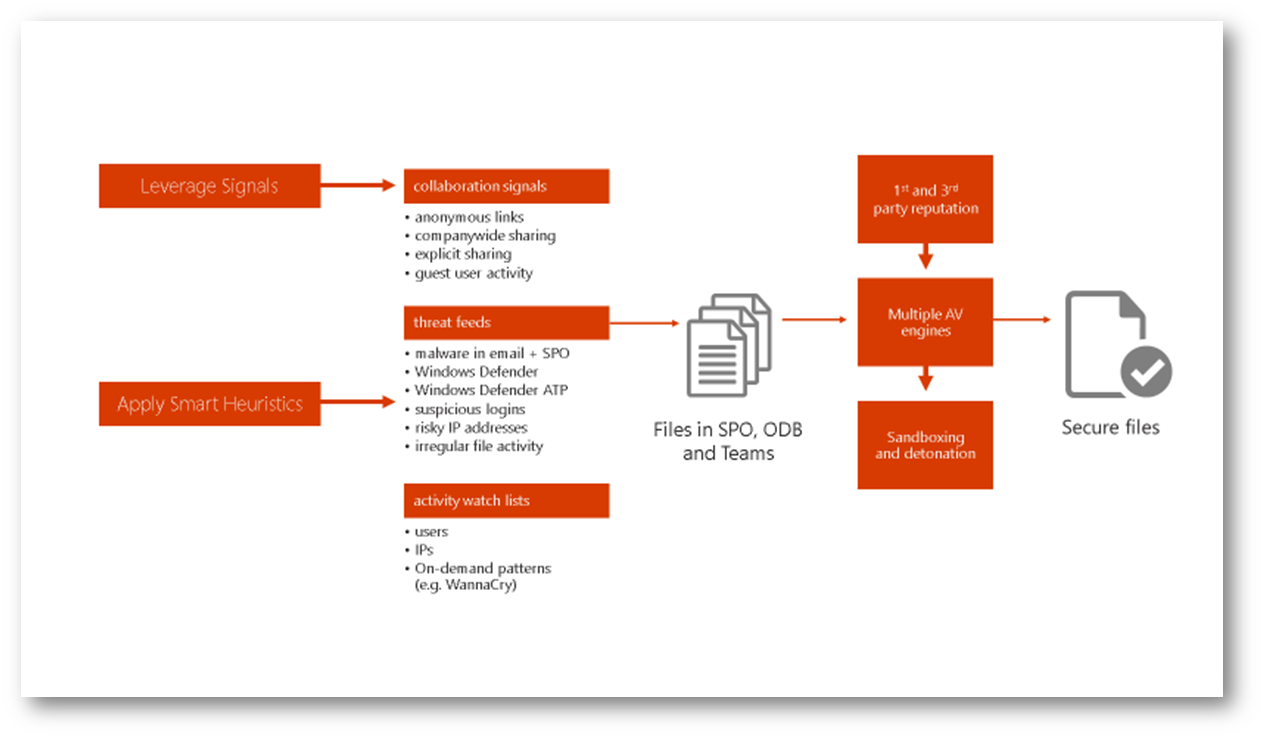
Too Long Don't Read (TLDR): In this blog, I'm going to describe how to enable this feature, perform a test, and show you alerting. For details on how Office 365 Advanced Threat Protection for SharePoint, Microsoft Teams, OneDrive works and it's architecture, see the below diagram – and read the following article: Office 365 ATP for SharePoint, OneDrive, and Microsoft Teams
Office 365 Advanced Threat Protection Architecture:
How to enable Office 365 Advanced Threat Protection:
Note: I will not be discussing Office 365 ATP for Exchange Online.
To enable, simply browse to the Office 365 Security & Compliance Center (protection.office.com) -> Threat Management -> Policy and click ATP Safe Attachments: 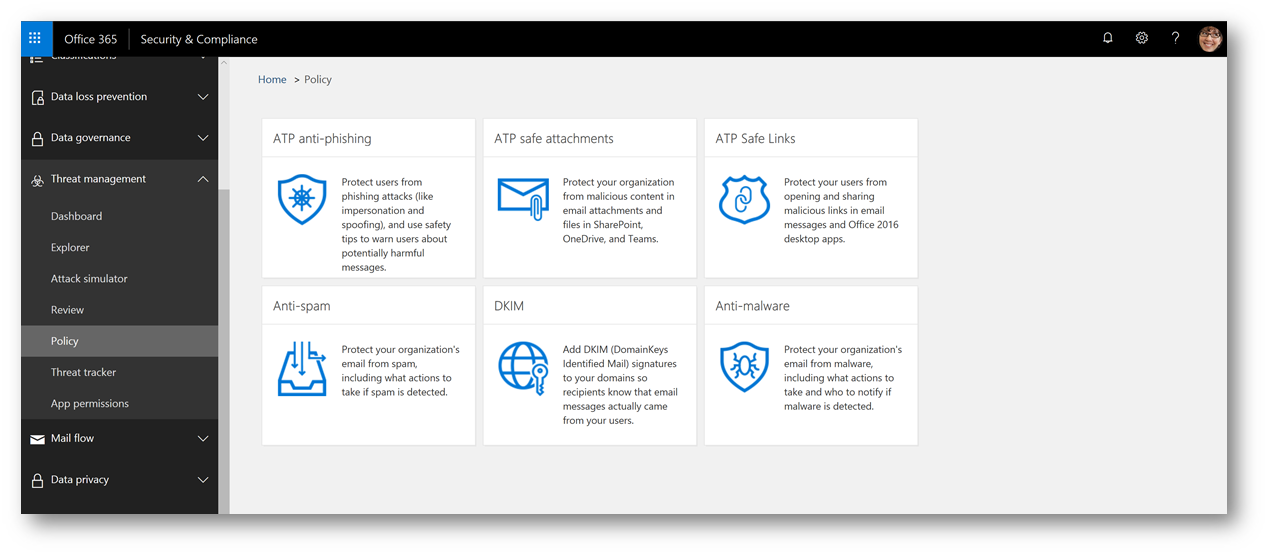
Once in ATP Safe Attachments, check the box Turn on ATP for SharePoint, OneDrive and Microsoft Teams and click Save:
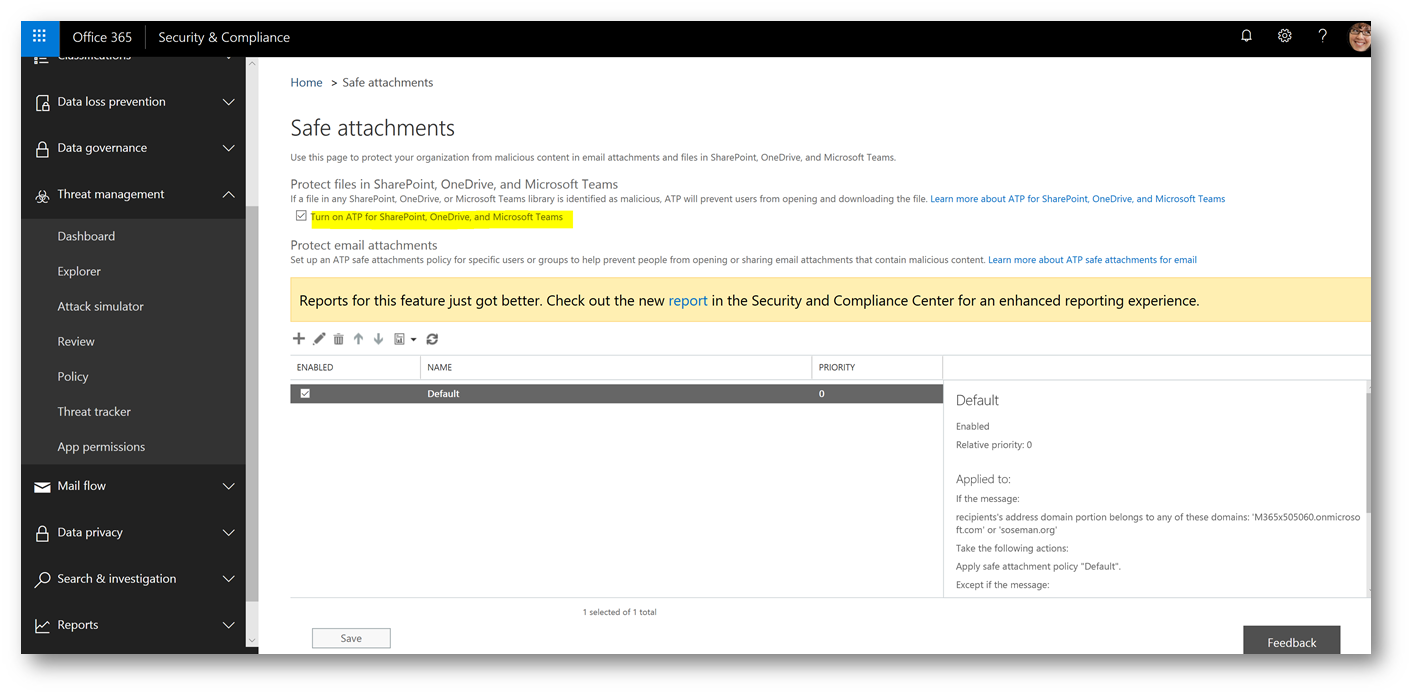
IMPORTANT: Review the Safe Attachment policies and configure as appropriate. Consider running Set-SPOTenant to DisallowInfectedFileDownload in PowerShell for the SharePoint tenant to ensure the malicious files cannot be downloaded. For more information see Turn on Office 365 ATP for SharePoint, OneDrive, and Microsoft Teams
User Experience:
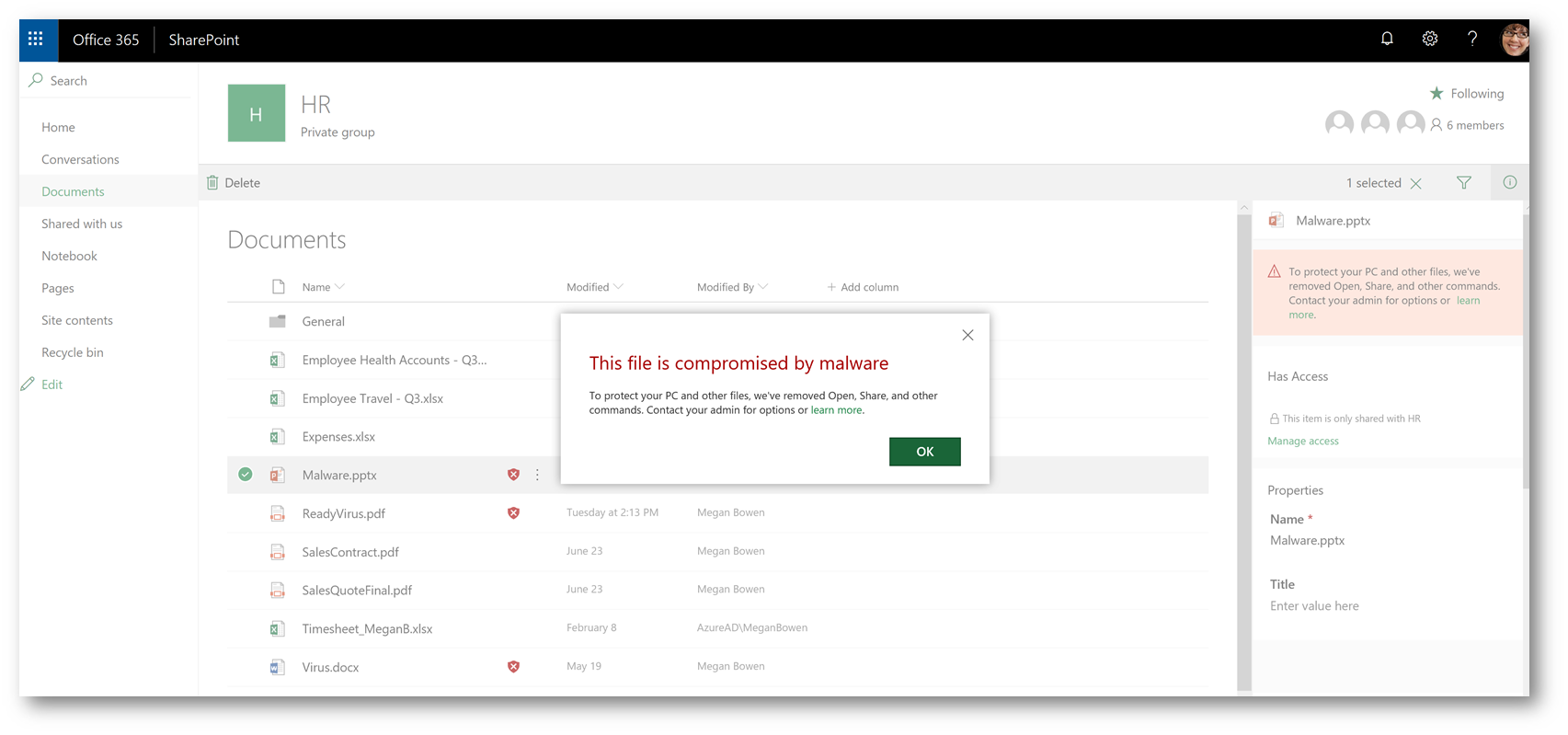
If a malicious file is uploaded, and detected by ATP, the user will be unable to open the file. If the user browses to the Office 365 Group or SharePoint site where the file is stored, and attempts to run from there, they will be presented with the following:
Setting up an alert:
As the admin, I want to be notified when this activity occurs. Using Office 365 Alerts I will create an Alert Policy to notify me so I can take action:
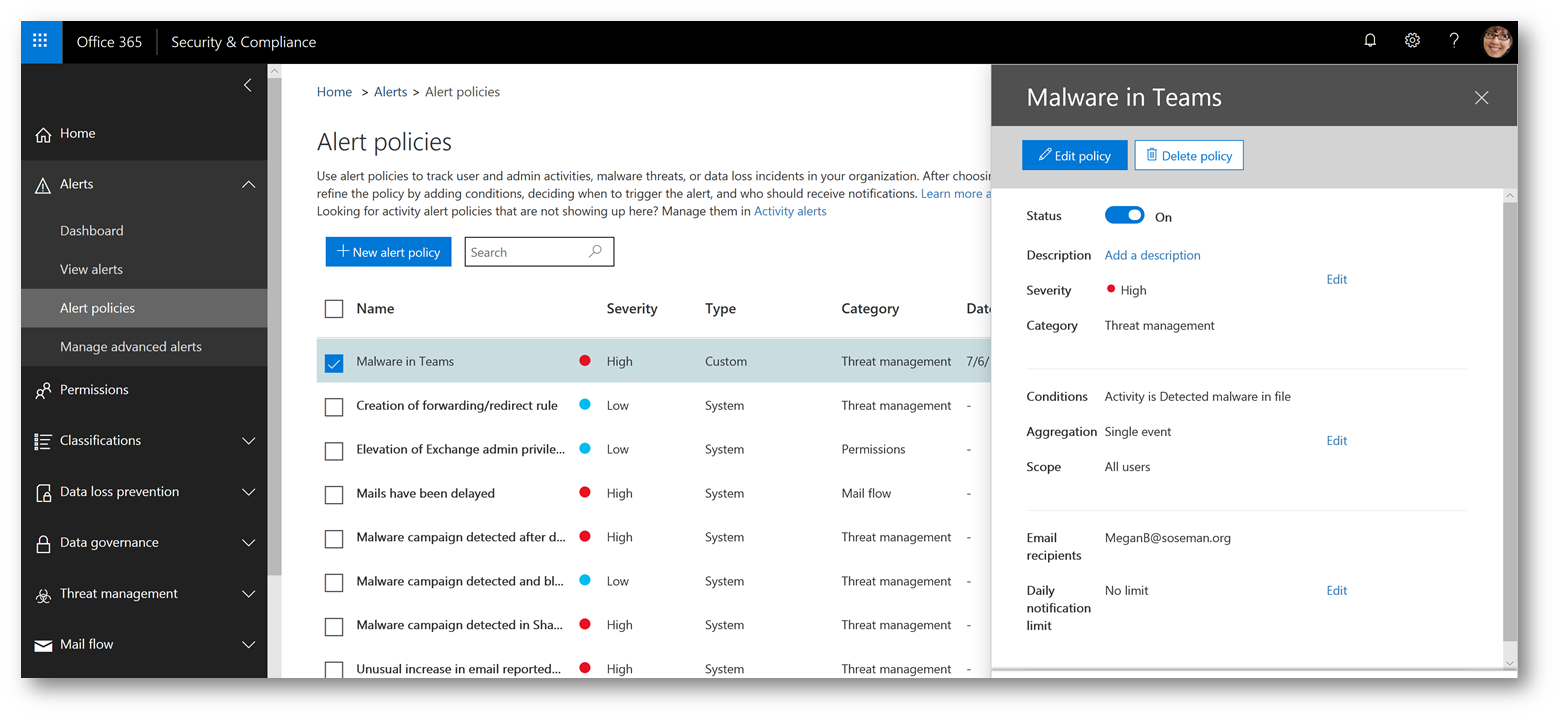
When the alert notification arrives via email, here is an example of what it looks like:
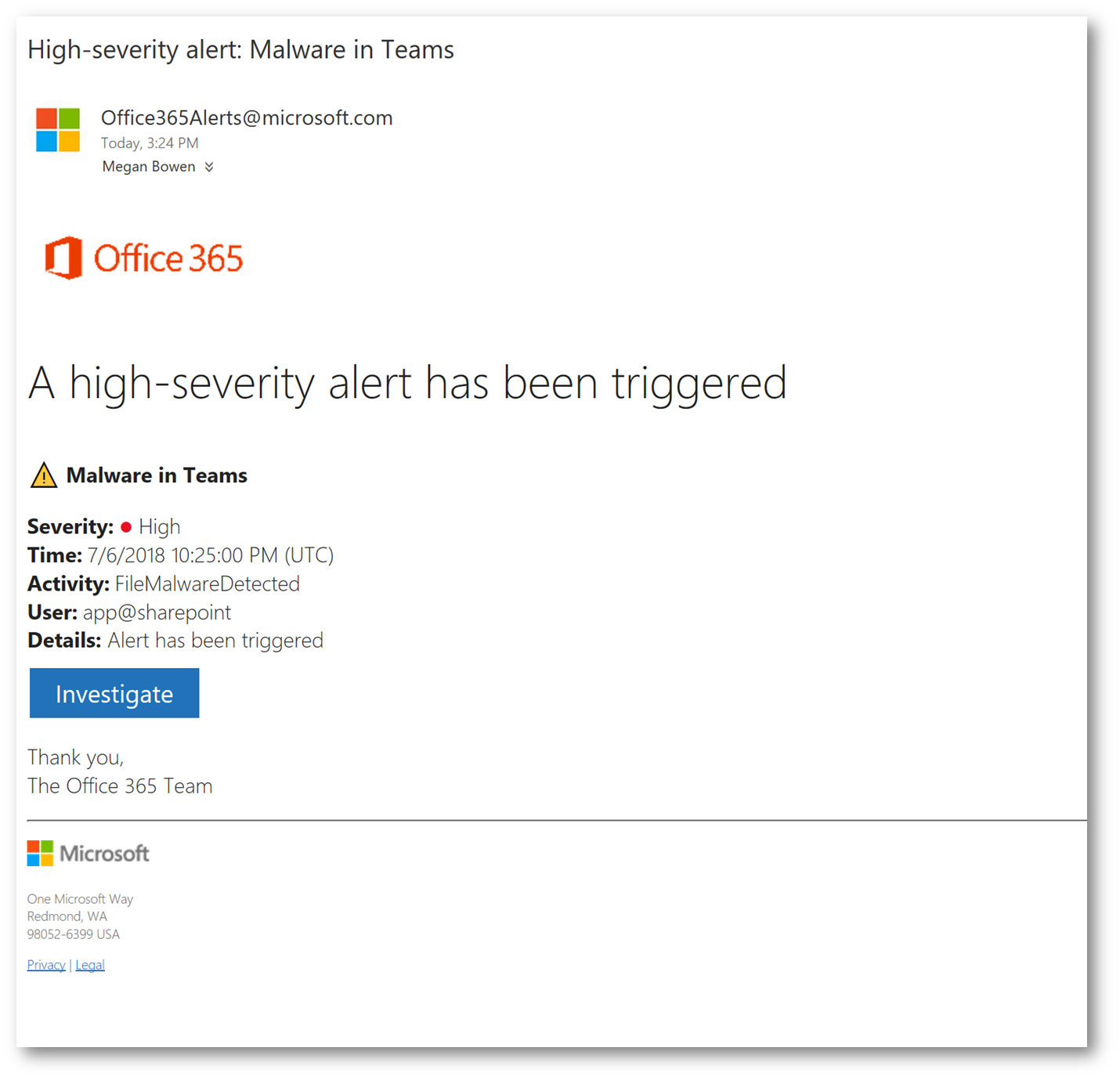
Clicking Investigate will launch the alert in Office 365 Alerts (notice I can suppress, or notify users):
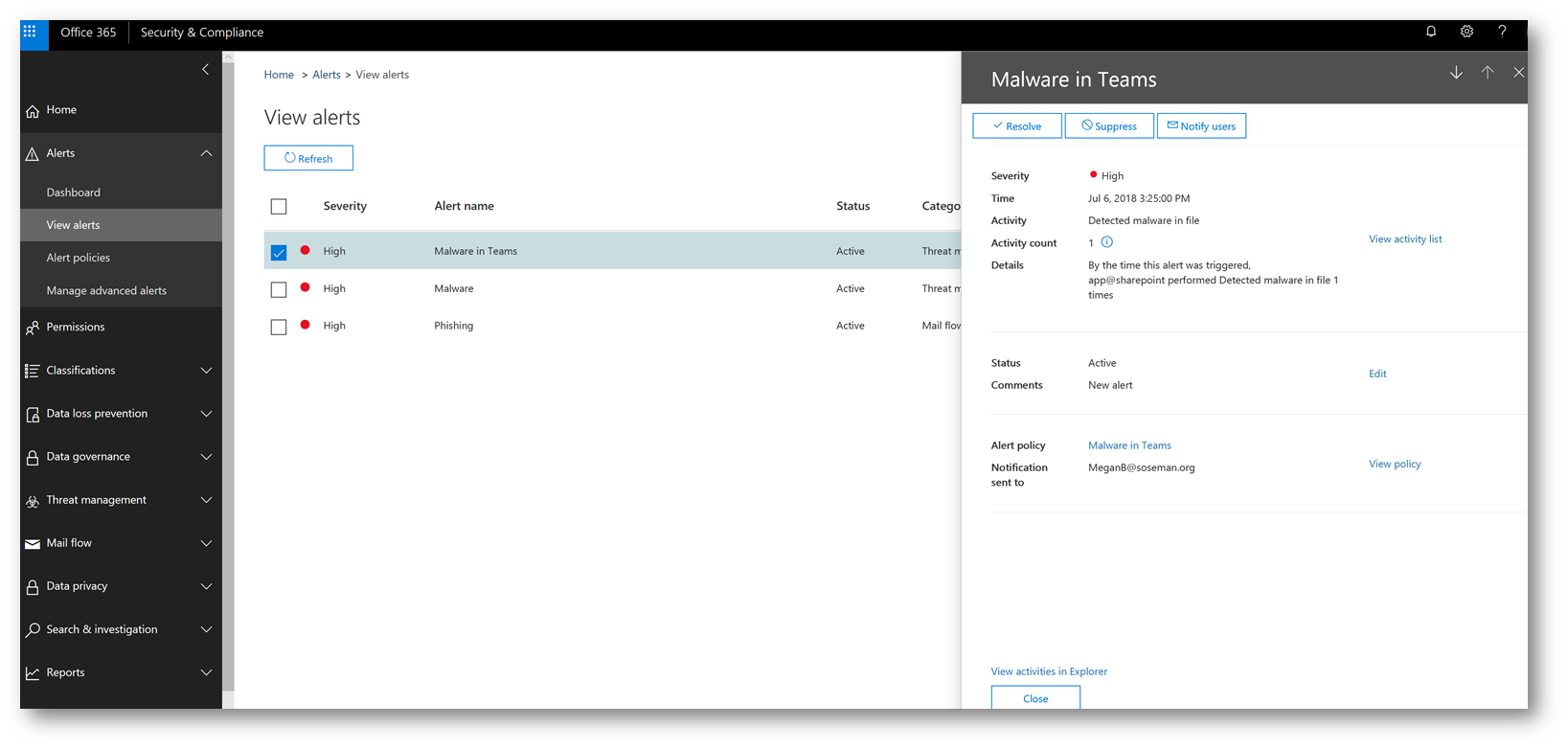
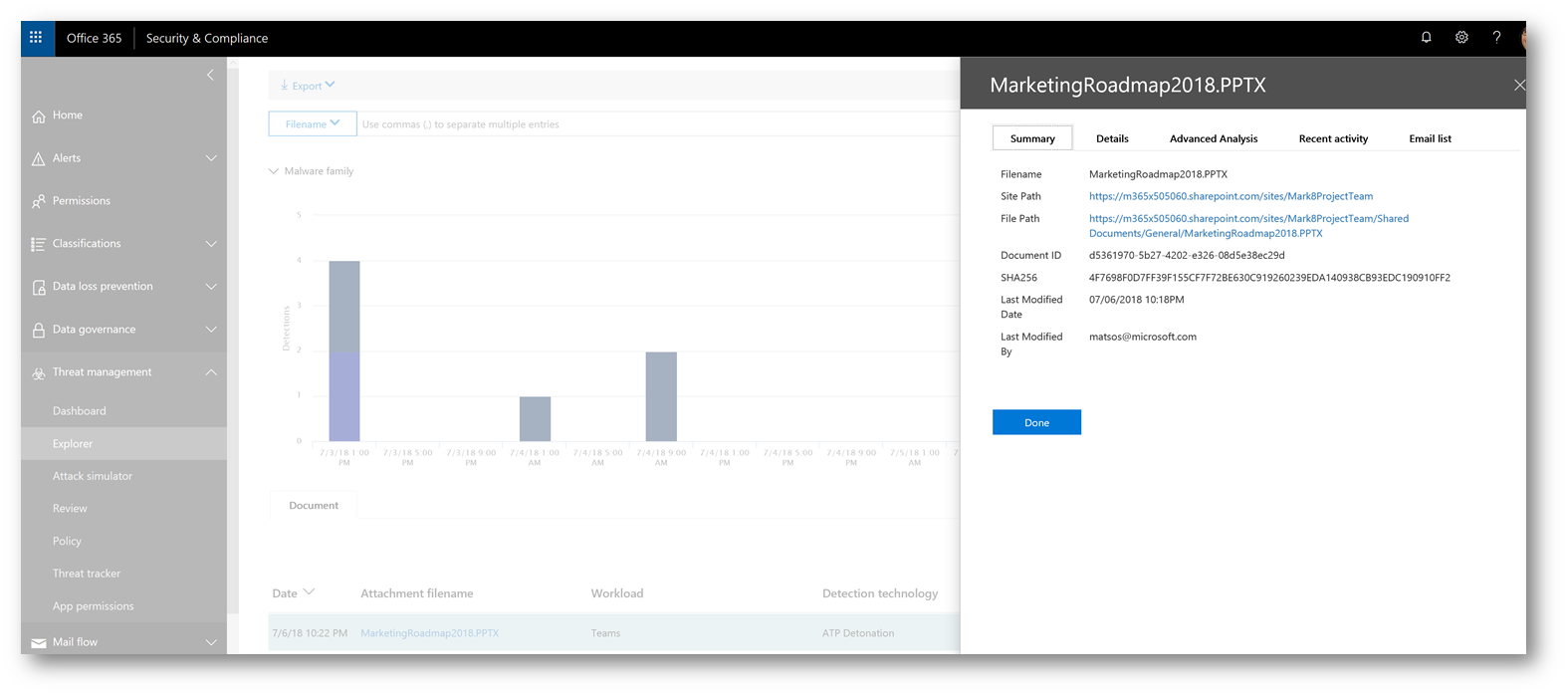
Accessing the event via Threat Explorer gives me access to additional details and advanced analysis that could be helpful in my investigation of the threat:
Conclusion
Office 365 Advanced Threat Protection is one of the many layers in your defense in depth approach to cyber security, and with it's ease of administration and use, it can be a valuable tool to protect your organization. Enjoy! –Matt Soseman