Conditional Access | Scenarios for Success (1 of 4)
Hello folks! Conditional Access is quickly becoming one of the most popular features our customers want to implement- it allows you to secure your corporate resources (such as Office 365) with quick and simple policies.
We have identified 3 common scenarios that customers implement using conditional access. These scenarios secure your environment from different angles, enabling more holistic coverage. These are by no means the only policies that you can or should implement, but we have found them to be successful in addressing the most common customer scenarios we see.
This post is the first installment of a four-part series on securing your environment with these conditional access scenarios. In this series, we will identify the requirements for each of these scenarios and cover configuration steps so you can implement them in your environment.
In today's post, we will introduce the three scenarios, their goals, and when they may be appropriate for you- stay tuned for posts on how to enable these scenarios in the coming weeks!
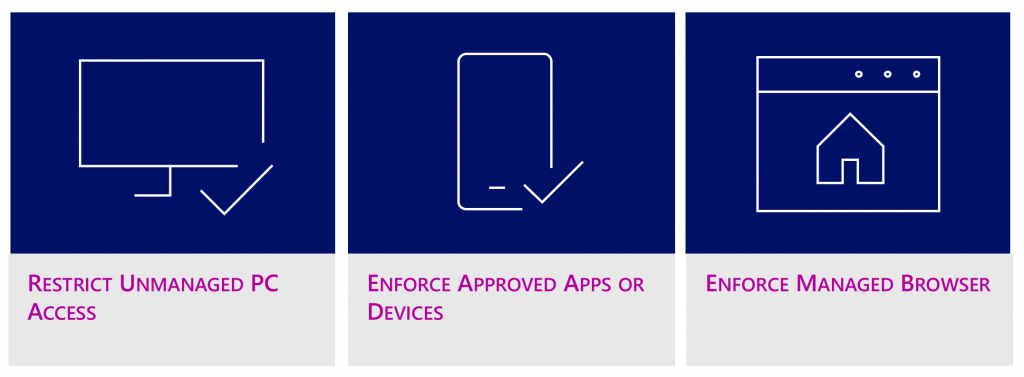
SCENARIOS
Restrict Unmanaged PC Access
Scenario Goal: Allow only Domain Joined devices to access corporate data using thick clients, but restrict unmanaged device access to the browser with MFA
Scenario Scope: Windows PCs
Recommended when…
- You want to enable remote access to web resources on personal PCs
- You only want full resource access from corporate PCs
- You want a strong, yet flexible, security posture for Windows PCs
Enforce Protected Apps or Devices
Scenario Goal: Enable users to access corporate data on their mobile devices in a way that you can protect and wipe. You want to ensure users are accessing corporate data in Office 365 using either an Intune managed device (MDM) or using an application that supports Intune App Protection policies (MAM).
Scenario Scope: iOS/Android devices
Recommended when…
- You need to protect mobile access to Office 365
- You allow end-users to access corporate data using their personal devices
- You have an end-user population who uses native email apps today
- You want to provide options to end-users in how they access Office 365 data
Enforce Managed Browser/Manage Mobile Browser Access
Scenario Goal: Ensure end-users access web resources (OWA, SPO, app proxy published resources, etc.) from an app with Intune App Protection policies applied the Intune Managed Browser
Scenario Scope: iOS/Android devices
Recommended when…
- You allow browser access to corporate data on mobile devices
- You are already using Intune App Protection for Office 365 apps
- You want to extend Intune App Protection capabilities to the browser
In the next few weeks we will talk more in depth about the steps required to enable each of these scenarios.
Have questions? Let us know in the comments below!