Protecting Email on Any iOS/Android Device
As organizations are moving their mail to the cloud, we have heard from our customers that they want to easily protect their Exchange Online data on mobile devices. One of the most exciting features of Intune is the ability to protect your corporate data even on mobile devices that aren't enrolled in an MDM. With Intune App Protection (aka "Intune MAM"), we can give employees secure access to corporate data with minimal end user effort.
The best part of all? Setting up and deploying MAM can be completed in a matter of hours (and that's with testing)!
Today, we're going to cover the basics of Intune app protection, how to get it configured for Outlook, and (most importantly) how to successfully deploy it to your organization.
What is Intune App Protection?
(Already know the basics? Skip down to the "Configuration" section)
Intune app protection applies protection at the app level for iOS and Android devices. If you want to enable your employees to access their corporate email on their personal (BYOD) devices without taking control of the entire device, MAM allows you to manage only the corporate content within targeted apps (such as Outlook). You can use Intune MAM to protect a number of applications, but today we are going to focus on the Outlook app and securing access to email with MAM.
The benefits of applying MAM policies?
- Minimal end-user set up- If they already have the Outlook app installed, they will receive a one-time pop up to inform them of the new policy. If they don't have it installed already, all they need to do is install the app and log in! (For Android, they also need to download the Company Portal in the background)
- Wipe the corporate data- If an employee leaves your organization or loses their device you can wipe the Exchange Online data from the Outlook app!
- Prevent data leakage- MAM policies can be configured to prevent cut/copy/paste and restrict Save-As to unmanaged locations
- Ensure app-layer protections- Prevent unauthorized users from accessing the application but enforcing a PIN on the Outlook app itself
- Protect your employees' privacy and autonomy- MAM is only applied to the corporate account, so you can protect corporate data without touching personal data! Using MAM-only for BYOD devices eliminates the chance that an employee would have their entire device wiped by IT (and lose precious family photos in the process!)
Configuration
To get your app protection policies configured, follow these steps:
1. Identify your target user group(s)
For testing purposes, you should identify a group of pilot users. When ready to fully deploy, you can use a broader user group (such as an "all users" group). Make sure that the security group(s) have synced to Azure AD.
NOTE: Make sure that the users have an Intune/EMS license! If they don't, you can quickly assign licenses to the groups with group-based licensing.
2. Decide on your policy settings
When you create a new MAM policy the settings will have the default values. You should review the available settings and customize them to fit your security requirements.
3. Create the Outlook app protection policies
You will need to create two policies: one for Android and one for iOS. Detailed instructions on this with screenshots can be found here
When you create the policy you will select the target app(s)- for this example we are choosing Outlook, since we are focused on email access. But you can also select and include other Microsoft apps to expand your protection. Then, configure the policy settings. Once done, make sure to click "OK" to save
4. Deploy the policies
Once the policies are ready, deploy them to your pilot user group. Detailed instructions here.
After testing with the pilot users, you can deploy to your broader organization by simply selecting the appropriate group(s) under "user groups". However, before you deploy the policy make sure you have communicated this change to your end users (as described in the "Deployment & Adoption" section below).
5. Enforce protection- set up conditional access
Corporate email in the native mail apps on iOS and Android cannot be managed or wiped unless the device is enrolled with an MDM. You can prevent users from utilizing native mail apps on personal devices and enforce use of the protected Outlook app with app-based conditional access. App-based conditional access (powered by Azure AD Premium) ensures that only apps which support MAM can access your company data.
Note: This will not impact users' ability to access personal email on whichever application they choose.
To configure app based conditional access follow these instructions, ensuring that you configure it for "Exchange Online".
Wait to deploy this policy until you have taken the end-user notification actions in the below section. Once you're ready, you will add the same group you used for the MAM policy under the "restricted user groups" tab to enforce conditional access.
Deployment & Adoption
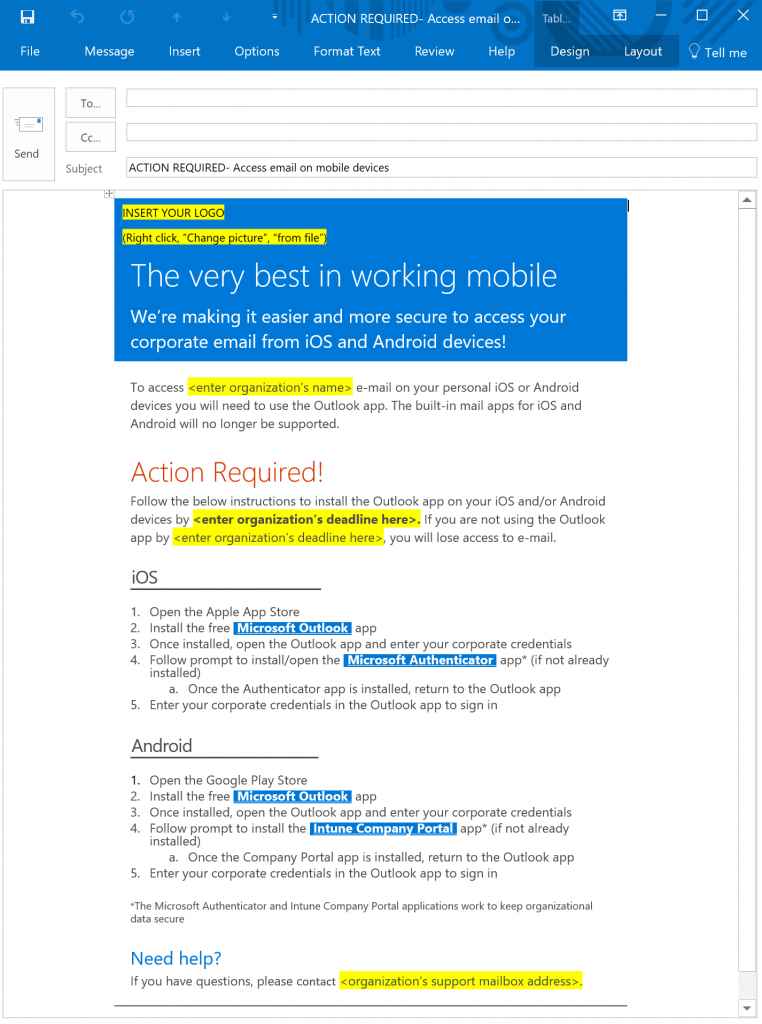
Now that you have gotten MAM configured it is time for the most important step… deployment and end-user awareness! As with any roll-out of new technology, it is important that you are up-front with your end-users and help them understand the benefit of this change
If you followed the above steps for the configuration, this roll-out will mean that end-users will be empowered to access their corporate email on Outlook for iOS and Android but will be prevented from accessing corporate email in their native mail clients.
To inform your end-users of this change, you can use this customizable e-mail template. The template includes instructions on how to set this up for iOS and Android, as well as a field for you to complete which informs them of the deadline to switch to Outlook mobile if they aren't already using it.
Once end-user communications have been sent out and you have reached the deadline you specified for end-users to move to Outlook, you are ready to turn on the conditional access policy (step 5 above)
You can also post this information internally, so end users have an easy way to learn more about what this means for them and how Intune app protection works. Consider adding information to your internal website on what end users can expect when their Android or iOS app is managed by app protection.
Now that you have deployed Intune app protection, you can monitor user adoption from the Azure portal.
Congrats-- you can now breathe easier knowing that your corporate email is protected across iOS and Android devices!
Questions? Post them in the comments below.
-Sarah and Josh