Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
We are here today with another post that focuses on using Graph API to automate actions in Azure AD! Today, our post will be focusing on how to create device groups that only contain the devices belonging to users in a certain security group. As we talked about in a previous post, dynamic groups are powerful feature in Azure AD that allow you to automatically populate groups based on their user or device attributes. We oftentimes have customers ask how they can create a dynamic device Group based on user groups. In today's Dynamic Device Groups UI, you cannot base the membership of a dynamic device group on the owning users' attributes. However, if you look beyond the UI, we can absolutely achieve this with Graph API!
Today's Goal: Populate a device group with devices belonging to users in a particular security group
To achieve this goal, we have written a script that you can run a few different ways, depending on how you want to populate your device group. We have 3 scenarios…
- I want to populate users' devices in to a device group if they are a member of a particular security group
- I want to populate users' corporate devices in to a device group if they are a member of a particular security group
- I want to populate users' personal devices in to a device group if they are a member of a particular security group
How do I run this script?
First, download a copy of the script from the TechNet Gallery: https://gallery.technet.microsoft.com/Create-Device-Group-Based-73eb063e
Once you have a copy, you will need to ensure you have the Azure AD PowerShell module installed. If you do not, you can simply launch PowerShell and run: Install-Module -Name AzureAD
You will also need to run this with a Global Admin account to ensure you have the right permissions to achieve everything the script is doing. If you want to try and delegate permissions, take a look at this blog post where I address delegating rights: https://blogs.technet.microsoft.com/smeems/2017/12/18/automate-dep-assignment/#delegate
The script written is set up to be run to meet one of these 3 scenarios. Depending on the scenario you want to achieve, you will start script execution a certain way. In the order of the scenarios above…
- .\Add-SpecificDevicestoAADGroup.ps1
- .\Add-SpecificDevicestoAADGroup.ps1 -CorporateOnly
- .\Add-SpecificDevicestoAADGroup.ps1 -PersonalOnly
Depending on how you choose to start the script, that will determine which types of devices the script will find and add to your specified device group.
Now that we know how to start the script, let's talk about what to expect when you run it…
So what exactly does the script do?
Once you start the script using one of the options above, a few things happen. The first thing it does is ensure you did not run the script using both the -CorporateOnly and -PersonalOnly switches. If you did, the script will stop right there and inform you that you should start it again and choose only one switch. If you want to run the script and get all devices for users in a group, simply execute it with no switch selected.
The next thing it does is ask you two important questions…
- Enter the Azure AD user group name that contains the users who have the devices you are adding to a group:
- Enter the Azure AD device group name where devices will be assigned as members:
For the first question, you need to specify the AAD group that contains the users who have devices that you want to add to a device group. This group needs to be created in advance of running the script. The name you enter is not case sensitive, and as soon as you enter it we do validation to ensure it is indeed a group in AAD and pull the members from it.
For the second question, you need to specify the group that you are using as the destination for all the user's devices. This group needs to be created in advance of running the script. Again, once you enter the name (not case sensitive), we validate that the group does indeed exist in AAD and pull the current list of members in the group. We pull the members in this group so that way we can check that devices we find for users in the first group are not already members of the destination group.
Once we have this info, this is where we start pulling devices from Intune and adding the AAD object to the destination group you specified. We do some validation to ensure that when we try to add the device that it does not already exist. Below are some screenshots that show the 2 experiences for what can happen with a device…
- Device does not already exist in the Device Group (destination)
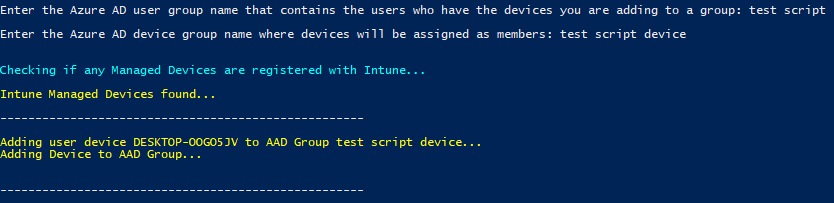
- Device does already exist in the Device Group (destination)
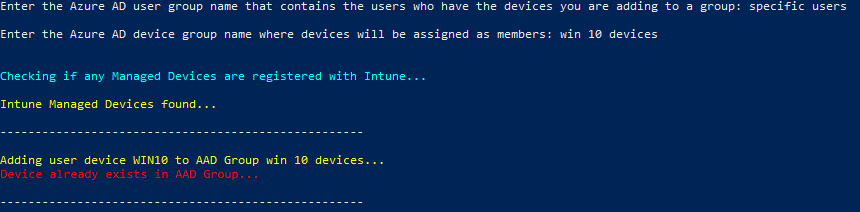
There is also the scenario that a user in the group does not have any Intune registered devices. If this happens, you will see this output:
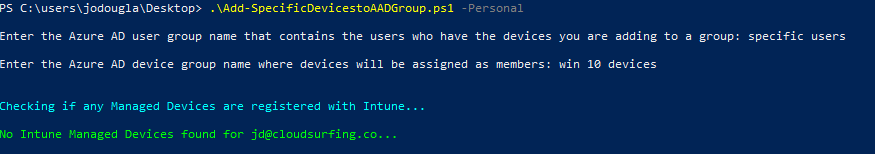
Once the script finishes executing (as long as we added at least 1 device to the group, or 1 device existed in the group) you will get a summary of the number of devices that were added to the group, and also the number of devices that already existed in the group. That output looks like this:
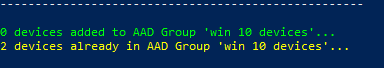
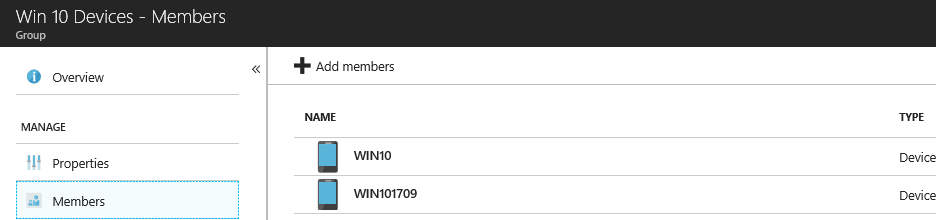
You can then go and check out your group in AAD, and see that the devices you added are indeed now included in the group:
Bringing It All Together
You now have everything you need to download the script and start creating device groups based on the membership of a security group. You can run this script as many times as you need, and we will handle ensuring that the appropriate devices are added to the group you specify, and if they are already there, we will let you know directly in the PowerShell window. So feel free to start using this to build your device groups based on security group membership!
To ensure that this script updates the group membership as users get new devices, you can create a scheduled task to ensure that the script runs every day. We covered how to set this up in one of our previous blog posts here: https://blogs.technet.microsoft.com/smeems/2017/12/18/automate-dep-assignment/#create
If you are interested in learning more about automation opportunities with Intune, go check out our PowerShell samples on Github: https://github.com/microsoftgraph/powershell-intune-samples
The script written today started by downloading a sample and modifying it to meet our needs: https://github.com/microsoftgraph/powershell-intune-samples/blob/master/ManagedDevices/ManagedDevices_Add_ToAADGroup.ps1
These samples can be very handy in putting together scripts that will help with your automation opportunities. Looking for guidance on how to automate other Intune and AAD actions? Let us know in the comments below.
Happy scripting!
-Josh and Sarah