Monitoring for GPO Modifications with SCOM
--Updated 8/16/16--
I recently had a request to assist in monitoring to changes to Group Policies using System Center Operations Manager 2012 R2. We found an existing TechNet article that described the process, but the steps were slightly outdated and referred to a SCOM 2007 Environment. However, it provided a good starting point. https://social.technet.microsoft.com/wiki/contents/articles/3862.scom-monitoring-gpo-changes-using-scom-and-powershell.aspx. The new process involves Auditing on Domain Controllers, Custom SCOM Rules to alert on Audit Events, A PowerShell Script that parses alert data, merges it with GPO details, and creates a new Custom Event on the SCOM Management Server, followed by an additional custom Rule in SCOM based on the new custom event.
Following are the steps to configure this custom monitoring solution for System Center Operations Manager 2012 R2:
1. Directory Services Auditing:
Ensure that ‘Directory Services Changes’ are being audited. This change can be achieved via GPO or Command line. The process is described here: https://technet.microsoft.com/en-us/library/cc731607(v=WS.10).asp. To find out if Directory Services Changes are being audited run the following from an administrator command prompt: ‘auditpol /get /subcategory:”directory service changes"'
2. Create Collection and Alerting Rules in SCOM to capture the Audit Events.
Collection Rule:
- In the Authoring Pane of the SCOM Console Expand Management Pack Objects > Rules.
- Right click and Select ‘Create a new Rule’. For Rule Type, select Collection Rules > Event Based > NT Event Log.
- Enter a name the clearly identifies the Collection Rule such as 'Collection Rule: GPO Audit Events' and Choose ‘Windows Domain Controller’ as the Rule Target.
- For the Event Log Type Enter ‘Security’ as the Log Name.
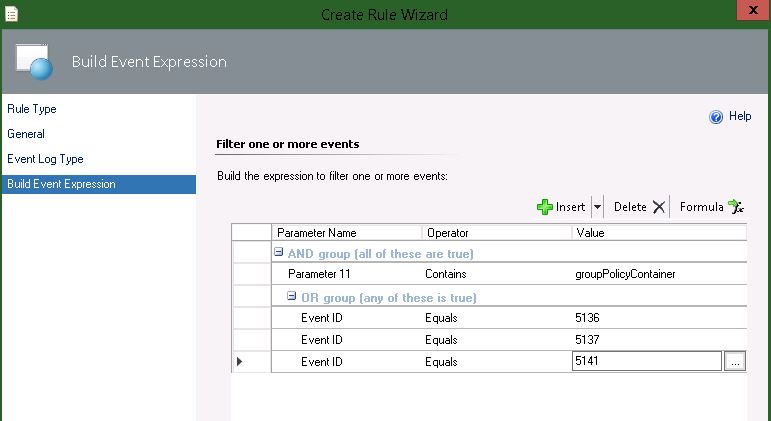
- For the Build Event Expression section Use the default AND group and Insert an OR Group Below it. In the OR group enter Event ID’s 5136, 5137, & 5141. In the AND Group enter 'Parameter 11' Contains 'groupPolicyContainer' as shown below.
Alert Rule: To create the Alert rule follow the exact steps as the collection rule with the following exceptions.
- Choose Alert Generating Rules instead of Collection Rules
- On the Configure Alerts Section change the Severity to 'Information'
- Select 'Alert suppression' and check the following boxes: Event ID, Parameter 4 (user name), Parameter 10 (GUID), & Parameter 11 (Class)
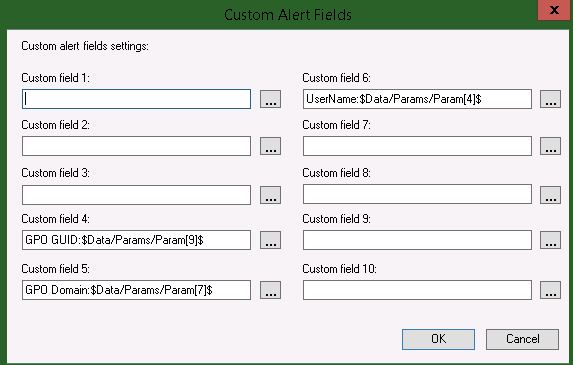
- Select 'Custom alert fields' Choose 3 Custom Fields to save unique alert data that will be used later. I chose 4, 5, & 6 because they were not used by any of my other custom rules. Other additional parameters can be used if additional data is needed. Enter the following values:
- GPO GUID:$Data/Params/Param[9]$
- GPO Domain:$Data/Params/Param[7]$
- UserName:$Data/Params/Param[4]$
- Click Ok and finish the Rule Wizard.
3. Create New SCOM Subscription.
Create Command Channel:
- In the Administration Pane of the SCOM Console Section right click and select New Channel > Command.
- Enter a name such as PowerShell GPO.
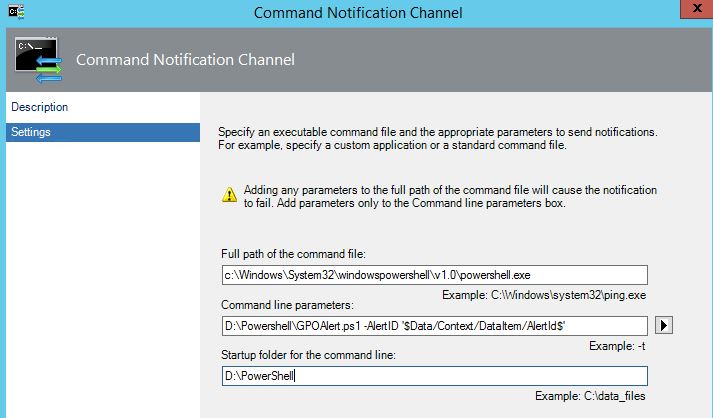
- For full path of the command file enter ‘c:\Windows\System32\windowspowershell\v1.0\powershell.exe’.
- For Command Line Parameters enter something like ‘D:\Powershell\GPOAlert.ps1 –AlertID ‘$Data/Context/DataItem/AlertId$’ (change the location to match wherever you save the PowerShell script created in the next step).
- For Startup folder for the command line enter the same Folder Location as used above.
Create Subscriber\Subscription:
- In the Administration Pane of the SCOM Console right click and select ‘New Subscription’.
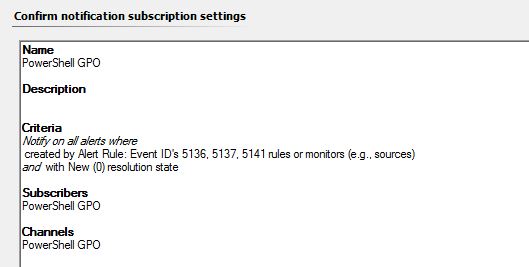
- Name the Subscription ‘GPO Change Notification by PowerShell’ (or something that clearly describes the subscription).
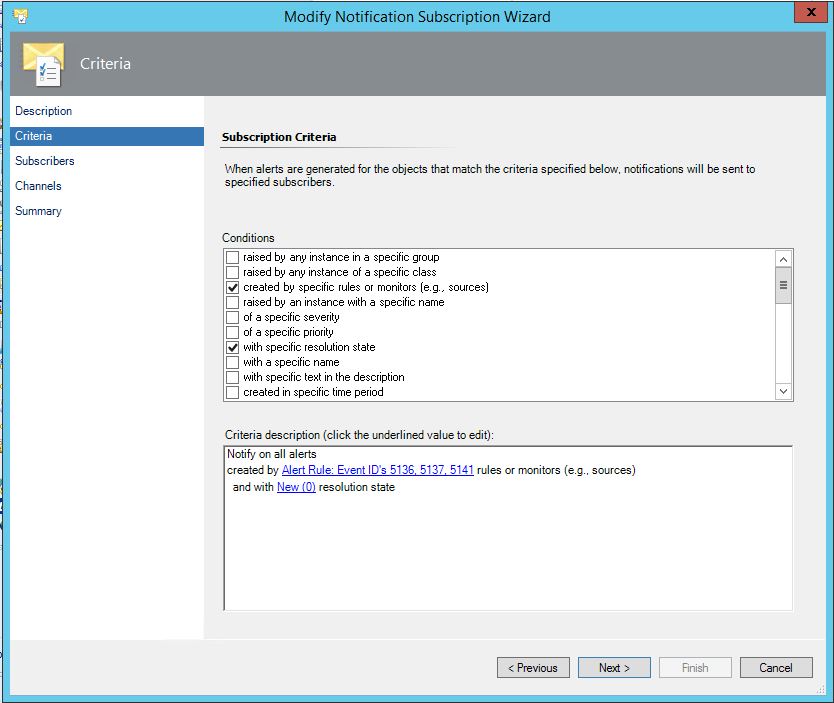
- On the Criteria tab select the checkbox for ‘created by specific rules or monitors (e.g., sources)’ and select the checkbox for 'Alert rule previously created', Choose 'with a specific resolution state' and select 'New (0)'.
- On the Subscriber tab click New, Enter a name for the subscriber such as PowerShell GPO.
- On the schedule tab ensure that the button for always send notifications is selected.
- For the Address name you can use the same name as for the subscriber.
- For Channel Type select the drop down for Command, on the Command Channel drop down select the recently created PowerShell GPO Channel, click next and Finish.
- On the Channel Section search for the previously created Channel again, select it, click add, and click ok. Click finish and close the wizard.
4. PowerShell Script.
Save the attached file as GPOAlert.ps1 on the D:\PowerShell location on your Management Server (or whatever location was specified when creating the channel in the earlier step. The script should be updated to use additional parameters as needed. As it exists now the script simply gathers some applicable data from the previously created alert in SCOM, correlates it to GPO information from Active Directory, closes the original alert, and creates a new Event on the SCOM Management Server that can be used to generate a new more useful Alert. The Management Server needs to have the Group Policy Management Feature installed for the get-gpo command in the script to work correctly.
- Make sure to update the $MS parameter in the Script to reflect the SCOM Management Server being used.
- note: If different custom fields were used in the previously updated Alert Rule it is necessary to update the $gpoGUID, $gpoDomain, & $gpoUser lines in the script to reflect the custom fields used.
-------------------------------------------------------------------------------------------------------
[CmdletBinding()]
param(
[parameter(Mandatory=$true, Position=0)] [ValidateNotNull()] [string] $AlertID
)
$MS = "OM1"
Import-Module "OperationsManager"
New-SCOMManagementGroupConnection $MS
Import-Module "grouppolicy"
$scomAlert = Get-SCOMAlert -Id $AlertID
$AlertDescription = $scomAlert.Description
$gpoGUID = $scomAlert.CustomField4.Substring(($scomAlert.CustomField4.IndexOf("{")+1),36)
$gpoDomain = $scomAlert.CustomField5.Substring(($scomAlert.CustomField5.IndexOf(":")+1))
$gpoUser = $scomAlert.CustomField6
$gpoName = get-gpo -Guid $gpoGUID
$Text = "A Group Policy Has been Modified`n User: $($gpoUser)`n GPO GUID: $($gpoGUID) `n GPO Changed: $($gpoName.DisplayName) `n Modified: $($gpoName.GpoStatus) `n $($AlertDescription)"
Write-EventLog -LogName "Operations Manager" -Source "OpsMgr Connector" -EventId 11101 -ComputerName $MS -Message $Text
$resState =$scomAlert.ResolutionState
$scomAlert.ResolutionState=255
$scomAlert.Update("")
-------------------------------------------------------------------------------------------------------
5. Create final Alert Rule:
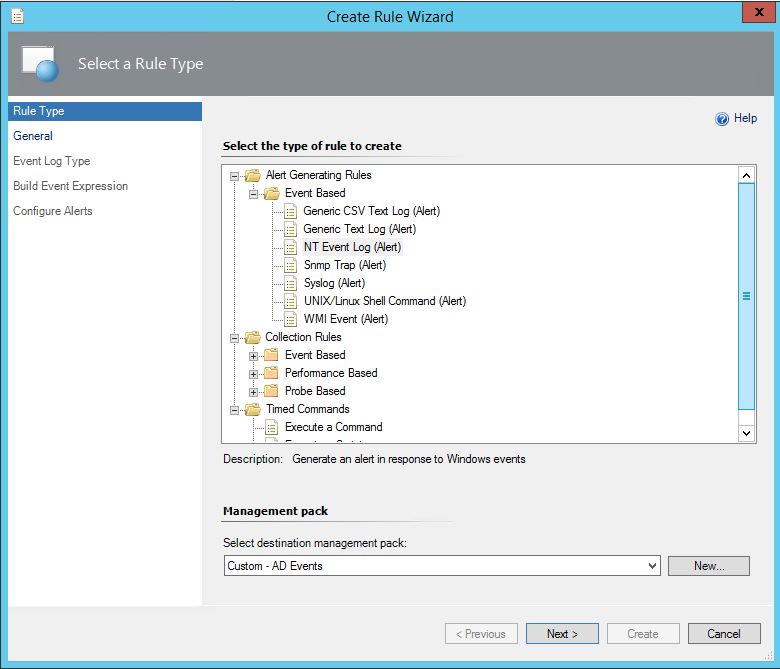
- From the Authoring pane of the SCOM Console expand Management Pack Objects and right click on Rules. Select Create a new rule.
- Choose Alert Generating Rules > Event Based > NT Event Log (Alert)
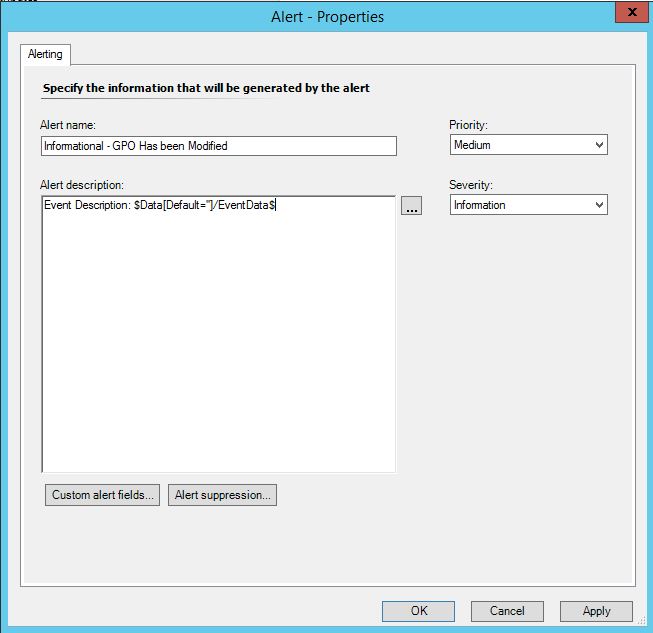
- Choose a Rule Name that clearly identifies the GPO modification such as 'Informational - GPO Has been Modified"
- Set 'Management Server' as the Rule Target (since the custom event created earlier is saved to the Management Server Event Log).
- Enter 'Operations Manager' as the Log name in the Event Log Type section
- Enter Event ID for Parameter Name, Operator Equals, and Value of 11101 in the Build Event Expression Section.
- On the Configure Alerts section it is recommended to change the Severity to Informational. The Alert description field should be modified to be: 'Event Description: $Data[Default="]/EventData$'
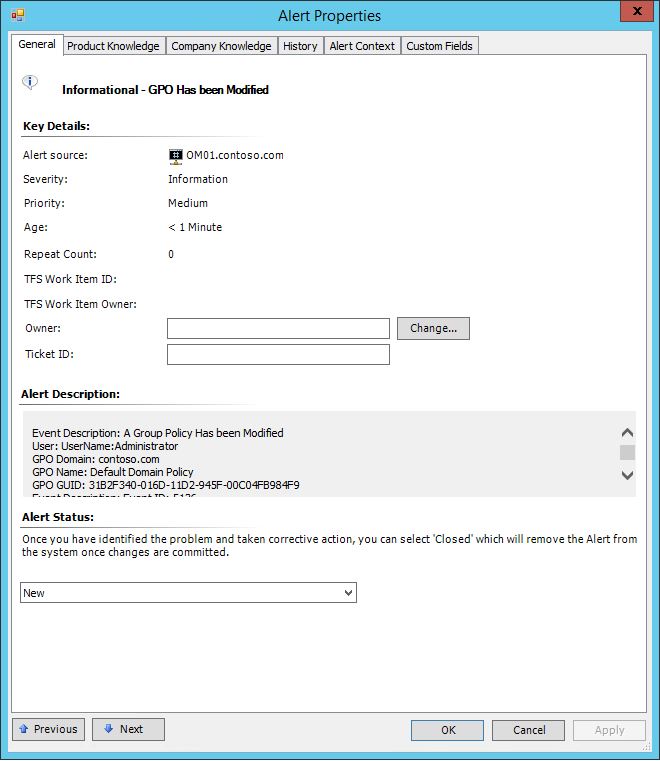
- The Generated Alert Should look something like this:
From Here it is easy to create custom email subscriptions or custom Alert Views so that these Alerts can be easily viewed by those who have a need to Monitor for GPO Changes.