Group Policy processing events collection with Powershell
Updated: 02/05/2014
The script has been optimized thanks for my colleague Pierre Audonnet.
You can also now export to csv and html format.
=============================================================
When troubleshooting GPO processing we have a lot of tools available to us.
Since Windows Vista, we especially have a new Event Log that register all events related to GPO processing.

One "new" feature is that each GPO event is assigned an Activity ID that is unique for a GPO processing.
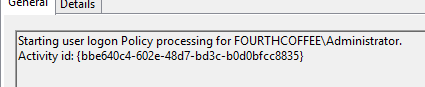
Tools such as GPlogview can use that Activity ID to sort large event logs and focus on a specific GPO processing.
You can also create a custom event log view to sort them using the following "Query":
<QueryList><Query Id="0" Path="Application"><Select Path="Microsoft-Windows-GroupPolicy/Operational">*[System/Correlation/@ActivityID='{INSERT ACTIVITY ID HERE}']</Select></Query></QueryList>
More details in the following article: https://technet.microsoft.com/en-us/library/cc749336(v=WS.10).aspx
Problems with those tools are that:
- You need to have GPLogView already installed on a computer to collect locally or remotely. You also need to know the Activity ID corresponding to the GPO processing you want to analyze.
- If using the Custom Log view, you need to either export the log on your computer or create the custom log view on the computer you want to analyse.
What about if you could list the lasted Activity IDs log on a computer and then sort only those events corresponding to these Activity ID.
That was the starting point of this little project.
Getgpoprocessing.ps1
An Activity ID is assigned at each new GPO processing. As you might know there is eight events that will trigger a new GPO processing:
- Computer Boot
- User Logon
- Computer background refresh
- User background refresh
- Computer Network Change
- User Network Change
- Computer Manual Update
- User Manual Update
Each of those event is logged in the group policy event log with a specific event ID:
Computer Boot: event ID 4000
User Logon: event ID 4001
Computer Background Refresh: event ID 4006
User Background Refresh: event ID 4007
Computer Network Change: event 4002
User Network Change: event 4003
Computer Manual Update: event 4004
User Manual Update: event 4005
To access the Group Policy event log, you can use the powershell cmdlet: get-winevent
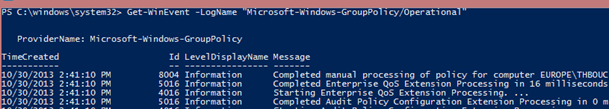
So what my script does is simple:
- Collect the group policy events over a period of hours that you specify on a local or remote computer
- Display the events corresponding to a new GPO processing
- Have you select the one you are interested in and gives you all corresponding events base on the Activity ID.
Here is an example:
Getgpoprocessing –hours 2
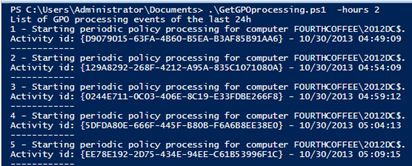
Here you can see that we have a periodic policy refresh for the computer every 5 minutes. This is normal as it is collected on a DC.
The same command to collect on a remote member server:
Getgpoprocessing –hours 2 –computer 2012MS
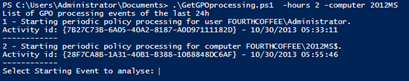
Once you have the "Starting" events, all you need is to enter the number of the one you want to review.
Following the collection on member server 2012MS, I will select 1 to review the background User GPO processing for user "Administrator" with Activity ID {7B27C738-6A05-40A2-8187-A0D97111182D}
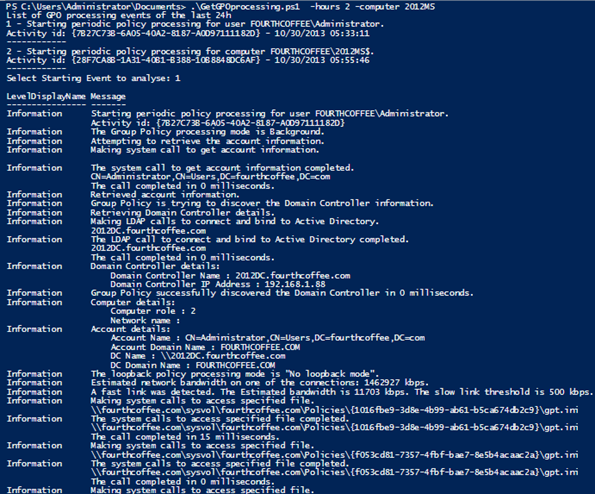
I now have the list of events from the Group Policy event log of member server 2012MS, with Activity ID {7B27C738-6A05-40A2-8187-A0D97111182D}.
The script only display the LevelDisplayName (Information, Warning, Error) and the message in the event.
You can also chosse to export the results to csv or html or both by adding the -csv $true or -html $true switches
The file name format are:
<computername>-<ActivityID>-gpoprocessing.csv
<computername>-<ActivityID>-gpoprocessing.html
If you do not specify a computer, meaning you run the script locally the <computername> is replaced by "LocalHost"
Requirements:
I order to use this script, you will need to have access to the Event logs, locally or remotely.
As usual you can find the script here