Answers to UAG SP1 DirectAccess Contest 1–Round 2/Quiz 4and Contest 2 Round 1/Quiz 4
This is the big day! The results are in for the last quiz in Contest 1.
First, I’ll go over the questions and answers and explain some interesting things that came up when I reviewed the answers I received, which had the effect of leading to two correct answers for one of the questions.
At the end I’ll post the “unofficial” results. The reason why they’re unofficial is that I like to wait until the next day to hear from anyone who might not have their answers scored correctly, in which case I update the leaderboard.
When the results are official on Wednesday, I’ll post the winners and the prizes (yes – there is going to be more than one prize!).
So let’s get to it!
================================================
Question 1:
Regarding Certificate Revocation List (CRL) checks, which is the following answers is true? (Choose all true answers):
A. If the client certificate CRL check fails, the IPsec tunnels cannot be established
B. If the server certificate CRL check fails, the IP-HTTPS tunnel cannot be established
C. You must publish the private CRL Distribution Point if you use a commercial CA for your IP-HTTPS listener
D. A CRL check is not performed when the DirectAccess client connects to the NLS
The answer to question 1 is B.
Answer A is incorrect because if the CRL check on the client certificate fails, the DirectAccess IPsec tunnels can be established. This is one of the reasons why revoking the computer certificate of the DirectAccess client is not the recommended way to blocking connections from potentially compromised DirectAccess clients. For more information check out https://blogs.technet.com/b/tomshinder/archive/2011/01/25/certificate-related-questions-and-test-lab-guide-guidance.aspx
Answer B is correct because the if the CRL check on the certificate bound to the IP-HTTPS listener on the UAG DirectAccess server fails, then the IP-HTTPS session establishment will fail. This is a hard coded option which is not configurable. For more information check out https://technet.microsoft.com/en-us/library/ee382307(WS.10).aspx
Answer C is incorrect because the commercial certificate provider publishes the CRL for you – there is no need for you to publish the CRL for the commercial certificate provider. The only time you would need to publish the CRL yourself is if you choose to bind a private certificate to the IP-HTTPS listener.
Answer D is incorrect because a CRL check is done when the client connects to the Network Location Server (NLS). For more information on this requirement, please see https://technet.microsoft.com/en-us/library/ee382275(WS.10).aspx
================================================
Question 2:
True or False: The DirectAccess client can use IP-HTTPS to connect to the UAG DirectAccess server when located behind an authenticating proxy where authentication is required:
A. True
B. False
The answer to this question is A or B.
When I wrote this question I had it in mind that the proxy would be transparently authenticating connections in the background for each new connection, like what the TMG firewall does. IP-HTTPS will not work in this scenario because there is no mechanism available to configure the IP-HTTPS client component to send credentials to the authenticating proxy.
However, there are other types of authenticating proxies that require you to authenticate you once (for example, what you see in hotels with captive portals). After you authenticate with the portal, the proxy will allow you outbound access without requiring credentials (except in the case where there is a time-out period and you have to authenticate again). Since several of your explicitly called out this scenario (the one that I didn’t think of when writing the question), I decided that both answers are correct because of the ambiguity of the question. So congrats to everyone! You all got this one right ![]() .
.
For more information on this issue, please see https://technet.microsoft.com/en-us/library/ee844126(WS.10).aspx
================================================
Question 3:
For the default settings for end-to-end Authentication and encryption with UAG SP1, which of the following statements are true (select all true statements):
A. End to End security uses IPsec tunnel mode from DA client to intranet server
B. End to End security uses Authentication with null encapsulation
C. End to End security authenticates only the first packet to the destination server
D. End to End security uses ESP-NULL
The answer to this question is D.
Answer A is incorrect because End-to-End security uses IPsec transport mode to connect the DirectAccess client to the secure server on the intranet. IPsec tunnel mode is used to connect the DirectAccess client to the UAG DirectAccess server. For more information on this, check out https://blogs.technet.com/b/tomshinder/archive/2010/12/01/uag-directaccess-and-the-windows-firewall-with-advanced-security-things-you-should-know.aspx
Answer B is incorrect because by default, End-to-End security uses IPsec with null encapsulation, sometime referred to as ESP-NULL. This is different from Authentication with null encapsulation, when is enabled by AuthIP and available only when the secure server is Windows Server 2008 R2 – ESP-NULL is available when connecting to Windows Server 2008 and Windows Server 2008 R2. This is a configurable option. You can find more information on this at https://technet.microsoft.com/en-us/library/ee382325(WS.10).aspx and https://blogs.technet.com/b/tomshinder/archive/2010/09/12/a-short-introduction-to-uag-directaccess-end-to-end-security.aspx
Answer C is incorrect because this describes the behavior you see with IPsec Authentication with null encapsulation, which is not used by default, as discussed in the previous question.
Answer D is correct because ESP-NULL is the default method used by End-to-End security.
================================================
Question 4:
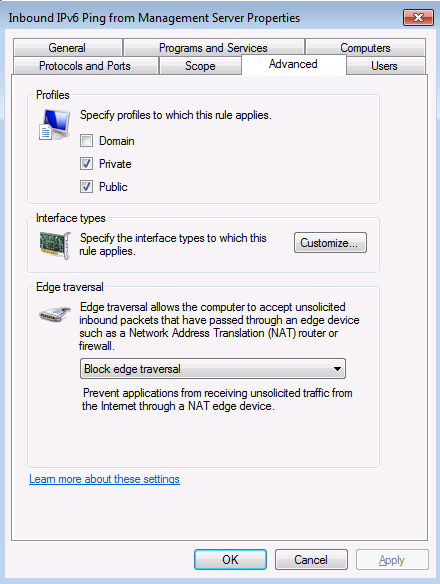
Bob wants to enable a “manage out” scenario where intranet management servers can initiate connections to DirectAccess clients over the Internet. To do some basic testing, he wants the intranet management servers to be able to ping the DirectAccess client. When Bob tries to ping the DirectAccess client from the management server, the ping requests fail.
Bob checks the Firewall Rule he created to support inbound ping to the DirectAccess client and sees the following:
Which of these figures most likely explains the ping failure (Pick one)?:
A. Figure A
B. Figure B
C. Figure C
D. Figure D
The answer to question 4 is D.
There isn’t a whole lot of information contained in these screenshots except for the last one.
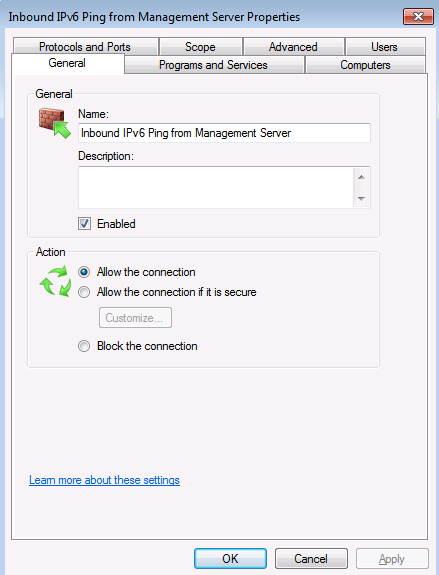
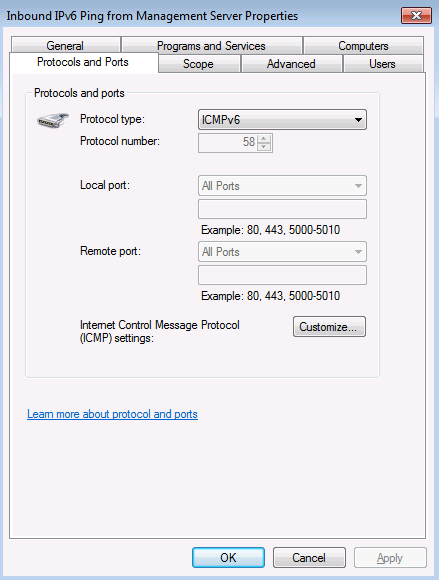
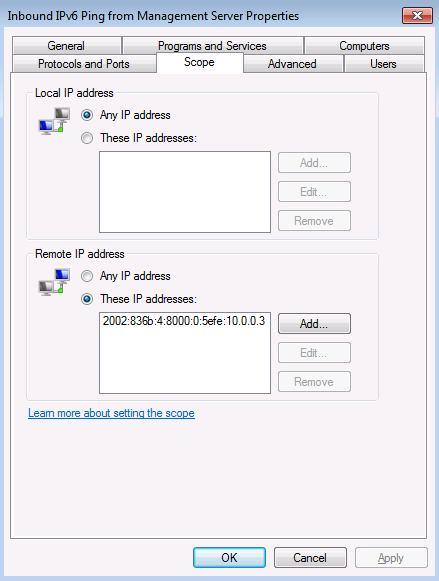
The first screenshot (A) just tells us that the connection is allowed.
The second screenshot (B) shows that ICMPv6 is allowed, so that shouldn’t be a problem.
The third screenshot (C) shows that the connection is allowed between the DirectAccess client and the IP address of the management station. There is a possibility that this is the wrong IP address, but there is nothing in the question that indicates that maybe the wrong IP address was included in the firewall rule. I’d keep this in mind, but look for a better explanation.
The fourth screenshot (D) has the interesting information – this graphic shows that Edge Traversal is blocked. When the DirectAccess client is using either Teredo or IP-HTTPS, Edge Traversal must be enabled for protocols that you want to allow inbound to the DirectAccess client from management stations on the intranet. This is not required when the DirectAccess client is using 6to4 to connect to the DirectAccess server. For more information on this, check out https://technet.microsoft.com/en-us/library/ee649264(WS.10).aspx (note that IP-HTTPS isn’t called out, but if you perform your own test, you’ll see that it is required for IP-HTTPS as well). While we don’t know for sure that the client isn’t using 6to4, it is the most likely answer to this question.
================================================
Question 5:
Review the following figure:
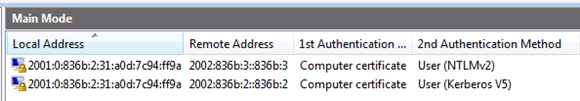
Based on this figure, which of the following can you state are correct (pick all correct answers)?:
A. The intranet tunnel is active
B. The infrastructure tunnel is active
C. The DirectAccess client is using IP-HTTPS as its active IPv6 transition technology
D. The DirectAccess client is a domain member
The answer to question 5 is A, B, and D.
Answer A is correct because the DirectAccess client needs to authenticate using a computer certificate and machine account (NTLMv2) to establish the infrastructure tunnel. The intranet tunnel enables the DirectAccess client to connect to machines that you define in the “management servers” list in the UAG DirectAccess server configuration.
Answer B is correct because the DirectAccess client need to authenticate using a computer certificate and user account (Kerberos V5) to establish the intranet tunnel.
Answer C is incorrect because DirectAccess clients that use IP-HTTPS always use 2002 for their high order “quartet”, and the screenshot shows that the client is using 2001.
Answer D is correct because all DirectAccess clients must be domain members. The DirectAccess client doesn’t need to be a member of the same domain as the UAG DirectAccess server, but it must be a domain member for authentication and Group Policy assignment.
================================================
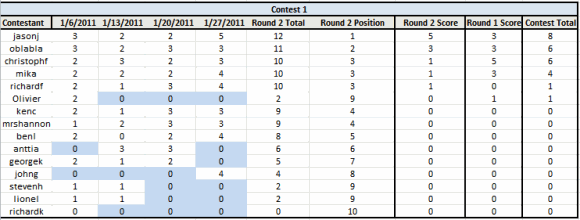
Final Score for Contest 1
Now for the scores! The figure below shows the final score for Round 2 in Contest 1 (which is also Round 1 in Contest 2).
The final score for Contest 1 is based on the points assigned to the top three finishers in Round 1 and the points assigned to the top three finishers in Round 2. You can see the Round 1 and Round 2 points in the chart. If there was a tie for the first, second or third places in a Round, each member of the tie received the points for that position. The top score for a Round received 5 points, the second highest score received 3 points and the third highest score received 1 point.
The unofficial Contest 1 Results (note that these results are not official until FRIDAY – this is to make sure you have time to tell me I might have made a mistake on the scoring of your entry – therefore, like they say in horse racing, hold on to your tickets until the results are declared official!) are:
WINNER:
jasonj – 8 points PRIZE: Personalized Starbucks Card and Hard Copies of our UAG and TMG books!
2nd PLACE:
oblaba – 6 points PRIZE: Hard Copies of our UAG and TMG books!
christophf – 6 points PRIZE: Hard Copies of our UAG and TMG books!
3rd PLACE:
mika – 4 points PRIZE: Hard Copy of either our UAG or TMG book (your choice)
In addition, I’d like to acknowledge the participation of those who didn’t end up in the top three – but participated in each of the quizzes in the second round. It was a long haul and for those who stuck it out this long deserve some recognition. Therefore richardf, kenc, mrshannon and benl will all receive PDF copies of our UAG and TMG books.
I will be writing to each of you to obtain your mailing information after the results are made official. As for the unofficial winner – Jason Jones is a Forefront MVP and will be attending the MVP worldwide conference next month, so I will be able to present him his prizes in person.
So there you go! Thanks for participating in the Contest! It was a ton of fun and I hope you all learned some things along the way (I know I did!).
We’ll start Round 2 of Contest 2 next week – so you can take the rest of this off ![]() .
.
See you then!
Thanks!
Tom
Tom Shinder
tomsh@microsoft.com
Principal Knowledge Engineer, Microsoft DAIP iX/Identity Management
Anywhere Access Group (AAG)
The “Edge Man” blog : https://blogs.technet.com/tomshinder/default.aspx
Follow me on Twitter: https://twitter.com/tshinder
Facebook: https://www.facebook.com/tshinder
Visit the TechNet forums to discuss all your UAG DirectAccess issues https://social.technet.microsoft.com/Forums/en-US/forefrontedgeiag/threads Stay up-to-date with “just in time” UAG DirectAccess information on the TechNet wiki https://social.technet.microsoft.com/wiki/tags/DirectAccess/default.aspx |