PART 2 - SCEP certificate enrolling using ConfigMgr 2012, CRP, NDES and Windows Intune
After many feedback from customers and partners, I’ve decided to write another post with more detailed information on how to successfully implement NDES in combination with ConfigMgr and Intune. I hope this helps you implement quicker.
Update 1: Consider reading my other post on adding a reverse proxy.
Update 2: Publish NDES via Azure AD Application Proxy as described in my other post.
Update 3: Updated 16/3/2016 with more detailed info (thanks Kevin Myrup)
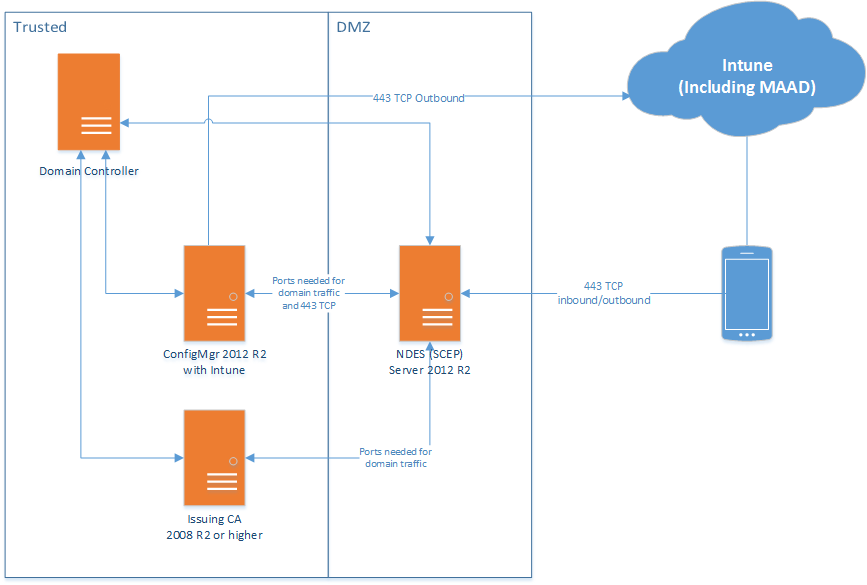
NDES Design High level architecture:
Pre-requirements:
- The issuing CA needs to be Windows Server 2008R2 (with KB2483564) or preferable an higher Windows Server OS.
- The NDES server needs to be Windows Server 2012 R2.
- The NDES server needs to be domain joined to the same domain as the issuing CA. Please consult this TechNet article in case you want to deploy in a separate forest, isolated network or internal domain.
- The NDES server cannot be the same as the issuing CA, even though that configuration is not blocked by setup, the policymodule will not work as expected in those conditions
Update 21/10/2014, please check my "Part 3" blog for more information on how to use an additional Web Application Proxy in front of the domain joined NDES server.
Network
From internet to DMZ:
- Allow port 443 from all hosts/IP’s on the internet to the NDES server
From DMZ to trusted:
- Allow all ports and protocols needed for domain access on the domain joined NDES. The NDES servers needs access to the Certificates Servers, DNS Servers, ConfigMgr Server(s) and Domain Controllers.
Now let’s start with the actual configuring, if something isn’t clear please leave a reply (a reply is always welcome)
Issuing Certificate Authority:
- Log in as a Enterprise Administrator
- Install all Windows Updates.
- If your issuing Certificate Authority is Windows Server 2008 R2, install the hotfix mentioned earlier from here. Preferably use a newer Windows Operating system for your issuing CA.
- Create certificate template(s) on the CA by duplicating an existing one
- It’s easiest to duplicate the template from the included “User Template” and modify that.
- Match purpose NDES template type (sig -> sig, crypt -> crypt, sig/crypt -> generalpurpose)
- Make sure “Supply in Request” is selected on Subject Name Tab
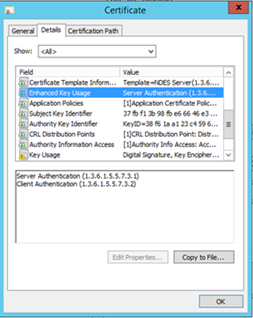
- Client Auth must be specified in the application policy
- Have a look at these template configurationscreenshots.
- Important note regarding the additional Application Policies (in the 4th screenshot), only add the application policies required. Consult your security department to ensure the appropiate configuration is done.
- Enable the certificate template on the issuing CA.
NDES Server:
- Log in as a Enterprise Administrator
- Install all Windows Updates.
- Make sure the NDES server is domain joined and has access to DNS, ConfigMgr, Certificate Authority and Domain Controller servers.
- Go to Add Roles and Features.
- Install Request Filtering which is located under Web Server (IIS) -> Web Server –> Security
- Install Active Directory Certificate Services (ADCS) role. (Uncheck Certificate Authority component, and instead check Network Device Enrollment Service)
- In parallel create a domain user/service account, e.g. “NDESUser”
- Make sure the user has the "Logon Localy", "Logon as a Service" and "Logon as a batch job" rights. This should be the case by default, however some companies have hardening policies in place to disallow/remove these rights.
- Make this user a member of the local IIS_IUSRS group.
- Make sure this user has Enroll permissions on he certificate templates which will be used to issue user certificates via NDES (and which later will be configured in the registry on the NDES server under HKLM\Software\Microsoft\Cryptography\MSCEP).
- Make sure the ConfigMgr admins who will create SCEP profiles have Read rights to the template so they can browse to it when creating SCEP profile configuration items in the ConfigMgr admin console.
- In parallel create a domain user/service account, e.g. “NDESUser”
- Create a Service Principal Name (SPN) for the NDESUser
- Open an elevated command prompt and type the following command (change the FQDN for the NDES server, Domain and NDESUser account to match your environment)
- setspn -s http/ndesserver.mydomain.local mydomain\NDESUser
If the SPN is not created; NDES to CA call may fail Kerberos authentication. If you are truly using a user account (not a service account e.g. network service or local service); then the fallback to NTLM will work just fine and you will not see any issues apart from some entries in security event log. If you block NTLM in your environment, this step is mandatory.
- Continue to configure the Network Device Enrollment Service
- CA for NDES – browse and locate your CA server using CA name or Computer name.
- RA Information – you can leave the defaults.
- Cryptography for NDES – Configure the CA value to be used by NDES server Make the key length match what is configured in your CA template – 1024 or 2048)
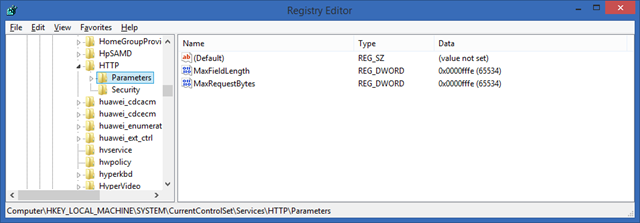
- The NDES server will receive very long URL’s (queries) and therefore a few changes are needed. Open the registry editor and add two entries:
Location: HKLM\SYSTEM\CurrentControlSet\Services\HTTP\Parameters
Value: MaxFieldLength
Type DWORD
Data: 65534 (decimal)
Location: HKLM\SYSTEM\CurrentControlSet\Services\HTTP\Parameters
Value: MaxRequestBytes
Type DWORD
Data: 65534 (decimal)
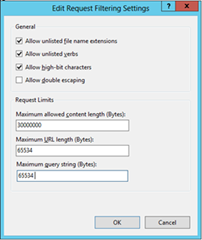
- Open IIS manager, browse to the Default Web Site and select Request Filtering. On the right side of the console hit Edit Feature Setting and change the Maximum URL length and Maximum query string to 65534
- After this reboot the server. This is mandatory – restarting IIS is not sufficient.
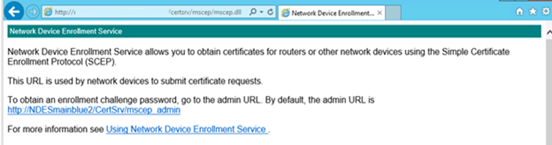
- Next, browse to https://FQDN/certsrv/mscep/mscep.dll and you should receive a NDES page similar to the one below.
If you get an error 503 "Service unavailable", check the eventviewer. It's likely that the application pool is stopped due to a missing right for the NDESuser.
This website will be hardened later on – don’t worry.
- The NDES server will need two certificates (or one with two EKU's - read on for more info), make sure you request those from the CA:
-
- Traffic between the NDES server and the CRP (Certificate Registration Point) needs to be encrypted using SSL. The NDES server needs a certificate with Client Authentication Enhanced Key Usages (EKU’s)
- A certificate using with a Server authentication EKU that it will use as it's SSL certificate for the IIS web server (to supply an https url for NDES so clients can connect using https to NDES server – absolutely recommended but not required).
- If you request a certificate from your local CA, double check you have the correct EKU's in place.
- The two mentioned certificates can be the same certificate (if the certificate has both capabilities), but they do not have to be. In case you want to have different expire lifetimes of the certificates e.g. you could generate one SSL certificate to last for 2 years, but client authentication certificate to expire after 1 year.
- I prefer to take the easy way and requested a certificate with both the Client Authentication and Server Authentication EKU’s and used them for both scenarios.
Update 16/3/2016 by request - for both NDES and CRP SSL certificates (and the NDES client auth certificate) some more info related to the Subject Alternative Name (SAN):
CRP:
SAN on the SSL certificate should contain the internal DNS name of the CRP server (which the NDES server will use when contacting it for cert verification requests). This DNS name should match what is entered as the CRP URL when installing the policymodule on the NDES server.NDES:
SAN on the SSL certificate should contain the public external DNS name of the NDES server (the one which will be a part of the uURLrl that devices will be provided to use for certificate enrollment requests). If using a WAP or other reverse proxy, this name should match what is published there.
SAN on the client auth certificate should contain the internal DNS name of the NDES server (which it will use to authenticate itself over the internal network to the CRP server). It may also contain the public DNS name.
- In IIS manager, go to “Edit Bindings” of the Default Web Site and add a port 443 binding.
- Add the certificate to the HTTPS binding.
- Consider changing the SSL settings to “Require” SSL but “Ignore” client certificates.
- Verify you can access the same URL with SSL this time: https://FQDN/certsrv/mscep/mscep.dll
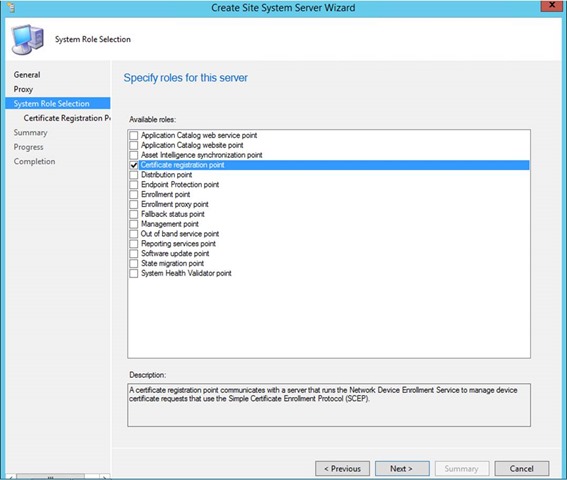
CRP Site Server Role in ConfigMgr:
- Install IIS - if it isn’t installed already.
- Make sure to add the following optional role services (which will trigger several other dependent components to be added also)
- Windows Server 2012 R2:
- ASP .NET 3.5
- ASP .NET 4.5
- WCF HTTP Activation
- Windows Server 2008 R2:
- ASP.NET
- WCF HTTP Activation
- (not in wizard but also do this) aspnet_regiis.exe –i (run this from .NET 4 folder: ex. C:\Windows\Microsoft.NET\Framework\v4.0.30319)
- IIS 6 Management Compatibility (including IIS 6 Management WMI Compatibility also)
- Windows Server 2012 R2:
- Bind the CRP cert to https 443:
- In IIS Manager select Default Web Site
- Right-click and choose Edit Bindings
- Choose https (it will use port 443 by default)
- Add or choose a CRP SSL certificate. (If you don't have this, request a default webserver certificate and add that)
- Make sure after the certificate is selected, you see bindings for all IP address - * like in below screenshot below
Note: If you are installing CRP to a remote machine from the site server, you will need to add the machine account of site server to the local administrators group on the CRP machine (by default remote site role is installed using site server machine account). Alternatively, you can specify a specific user to install as in the CRP site role installation wizard, and in that case this user would need to be added as a local administrator on the remote CRP site machine.
- Test if you can browse to the destination CRP server \\ipaddress\c$, if not make sure to enable “File and Sharing” firewall port
- Deploy CRP as new site system from site server (CAS or Primary Site)
- Open the Configuration Manager Admin Console
- Navigate to Administration -> Site Configuration -> Servers and Site System Roles
- Right click on primary site and select the Add Roles –> CRP
- If you are installing on a site server not CAS or Primary Site, configure an account that will perform the installation by changing the “Site System Installation Account”
- Specify the URL for NDES (for at least one NDES server), now this is important:
This URL will be part of the profile send to the devices. This means that the device – out there somewhere on the internet – needs to access this URL. Specify the internet facing URL, not any internal FQDN’s.
- Specify/browse to the exported trusted root certificate (.cer file) for the server who signed the NDES client authentication certificate.
- Verify that the CRP installed successfully by opening the following logfiles (locations might be different depending on the ConfigMgr installation path):
- C:\Program Files\Microsoft Configuration Manager\Logs\CRPMSI.log
- This log must read “Installation success or error status: 0”
- C:\Program Files\Microsoft Configuration Manager\Logs\crpsetup.log
- This log must read “CRP.msi exited with return code: 0”
- If errors like “GetIISWebServiceStringProperty failed” are listed, make sure the correct SSL certificate is bound and no “hostname” is specified in the “Edit Site Bindings”
C:\Program Files\Microsoft Configuration Manager\Logs\crpctrl.log
- It should show that CRP status is 0 (online) like this line:
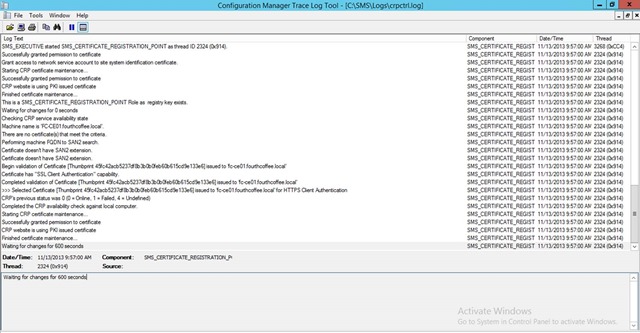
“CRP's previous status was 0 (0 = Online, 1 = Failed, 4 = Undefined) SMS_CERTIFICATE_REGISTRATION_POINT 4/25/2014 9:50:21 PM 6496 (0x1960)”
However, right after installation of CRP, it might not show that yet. The self-health check runs every 10 minutes, so after 10 minutes it should change from 4 to 0 (online). This can be speed up by restarting the SMS_CERTIFICATE_REGISTRATION_POINT thread if desired.
- C:\Program Files\SMS_CCM\CRP\Logs\CRP.log
- This log should not contain any errors.
- If you see a "Security Exception is thrown in reading inbox path" error, grant the "Network Service" account read permissions to the HKLM\SOFTWARE\Microsoft\SMS\MPFDM\Inboxes registry key.
- Open a browser on the CRP server and browse to https://FQDN/CMCertificateRegistration
- You should get a 403 Forbidden error. If you get anything else (e.g. a 404 or 500, stop right there and check all logs files and/or reboot the server)
- If you receive a 404, open IIS Manager and navigate to CMCertificateRegistration below the Default Website. Change the SSL settings to "Require SSL" and "Require Client Certificates". Restart the SMS_EXEC service.
- After the CRP is installed, the system will automatically export the certificate that will be used for NDES plugin (could take up to an hour or so) to the certmgr.box folder under inboxes on the site server. Be patient, it will be generated automatically.
- Copy this certificate the NDES server – we will need it soon.
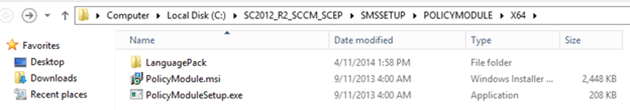
- Copy the policymodule directory containing the installation files, you will find it in the ConfigMgr installation files under SMSSETUP\PolicyModule\X64 to the NDES server. We will need it at the next step.
Back to the NDES Server
- On the NDES server, start “PolicyModuleSetup.exe” (copied earlier from the ConfigMgr installation files)
- Specify the URL for the CRP e.g. https://crp.contoso.local/CMCertificateRegistration)
- Specify the CRP port (if using something other than 443 on CRP).
- Select a PKI certificate that supports client authentication. You might already have a suitable certificate installed on the computer that you can use, or you might have to (or prefer to) deploy a certificate specifically for this purpose. Hit next.
- Select the cert that was copied from the CRP’s certmgr.box directory earlier.
- Open the registry editor and browse to HKLM\SOFTWARE\Microsoft\Cryptography\MSCEP
- Make sure that the values of “EncryptionTemplate”, “GeneralPurposeTemplate” and “SignatureTemplate” match the names of the template on your CA, triple check this!
Update 16/3/2016:
They should not all be set to the same thing. Most configurations will simply use GeneralPurposeTemplate, but they could also be using SignatureTemplate and/or EncryptionTemplate. If they do, though, those would be set to use a different template name. The mapping of Key Usage to registry key is as follows:
Encryption -> EncryptionTemplate
Signature and Encryption -> GeneralPurposeTemplate
Signature -> SignatureTemplate
- Open an elevated command prompt and run “iisreset”.
- Now open Internet Explorer on the NDES server and browse to https://ndesfqdn.com/certsrv/mscep/mscep.dll, you should no longer see the web page but instead you should see an http 403 - Forbidden error. This is expected.
Configure the Certificate Profile on ConfigMgr
- Logon to your ConfigMgr and open the console.
- Open the Assets and compliance tab -> Compliance Settings -> Company Resource Access -> Certificate Profiles
- Create a new profile, choose Trusted CA Certificate and hit next. Import your root CA certificate and hit next. Select which platforms you will be deploying this against. Hit finish at the end.
- Now deploy this profile to your choice of users or devices.
- Create a new Certificate Profile, this time a SCEP profile.
- Change the desired options in the “enrollment parameters” window, I would go for the defaults.
- Hit browse in the “Certificate template name”, remember this name must match whatever you entered in the registry on the NDES server!!
- If the template they created on CA doesn’t show when browsing from this wizard, it could be due to one of two likely causes:
- The ConfigMgr administrator does not have “Read” permissions to the template in AD (configure this on the template object from MMC on the CA).
- The template has been created, but not published to AD. (publishing to AD is done using the MMC snapin called “Certification Authority”, and you right-click “Certificate Templates” folder, and choose New -> Certificate Template to Issue”)
- At this point, be-aware that:
- iOS doesn’t support fully distinguished name as the subject name format or including e-mail address in subject name.
- You configure the settings according to what you have specified in the template (e.g. SHA-1/SHA-2/SHA-3 and the key-length).
- If the template name contains non-ASCII characters the cert will not be deployed
- Select the Root CA certificate and you should be good to go!
- Hit next, select the destination platforms and finish the wizard.
- Deploy the profile to the desired user or device collection(s).
Communication workflow
- Administrator configures policy in SCCM.
- Policy is sent to Intune service where details about the cert policy are used to create the challenge for the device(s).
- Policy is pushed to mobile device by Intune service during the next check-in. This policy contains the URL of the NDES server as well as the challenge generated by Intune.
- Device contacts the NDES server using the URL from #3 and provides the challenge response. (This is why your NDES server needs to be available externally in some way.)
- NDES Server (using our SCCM policy module) talks to the SCCM Certificate Registration Point (CRP) to validate challenge. You’ll need to make sure that 443 (SSL) is open between the NDES Server and the CRP for this validation to happen.
- CRP responds to NDES server with “true” or “false” to challenge verification. (Again, over 443 SSL.)
- If challenge is OK then the NDES server communicates with the CA to get a certificate for the device. You’ll need to make sure that the appropriate ports are open between NDES and CA for this to happen.
- NDES delivers certificate to mobile device.
Thanks Bob Roudebush for sharing.
Now what if it doesn’t work? Check these things first:
The device time should be accurate. If it’s off 5 minutes or more, you will not get SCEP certificate.
Did the Root CA (of the issuing CA) certificate you deployed in ConfigMgr got pushed to the device?
Can you access the NDES URL from the internet using a browser?
- Are you getting any certificate errors?
- Make sure the URL corresponds with what is listed on the certificate (https://ndes.yourdomain.com and not https://ndes.yourinternaldomain.local)
Visit https://ndes.externalfqdn.com/certsrv/mscep?operation=GetCACert&message=MyDeviceID You should get a response and the option to download a file.
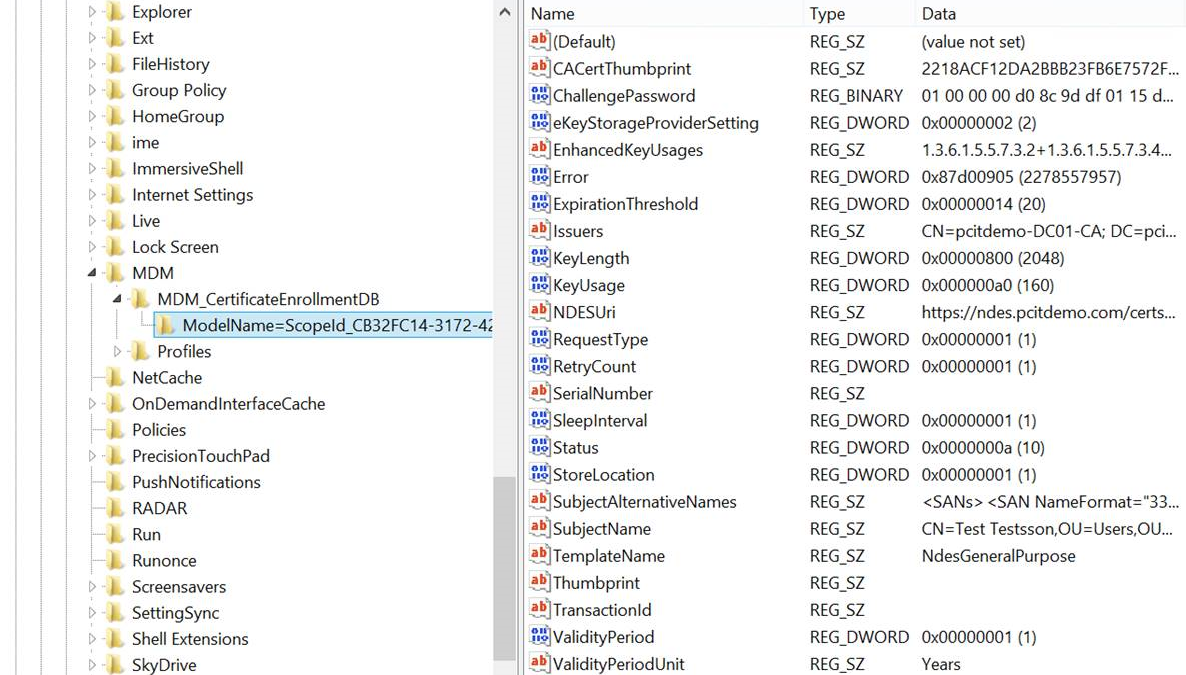
Push a certificate profile to a Windows device and check in the registry whether the request arrived.
- Open the registry editor and locate the following key: HKCU\Software\Microsoft\Windows\CurrentVersion\MDM
- The request will be visible as a subkey like shown in the screenshow below.
The certificate thumbprint will be populated when the actual certificate is received.
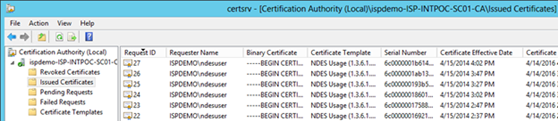
Open the CRPCTRL.LOG on the ConfigMgr server. The "previous status" should be 0.
Check out the file C:\Program Files\Configuration Manager\Logs\crpctrl.log (could also be in x86 program files folder)
There should be an entry as follows:
CRP's previous status was 0 (0 = Online, 1 = Failed, 4 = Undefined)Do you get any requests logged on the IIS server of the NDES? What is the status code? Should be 200 in most cases!
Check out the last modified log in C:\inetpub\logs\LogFiles\W3SVC1Entries should look similair to this (notice the port number 443):2014-07-07 13:45:27 10.0.0.6 GET /certsrv/mscep/mscep.dll/pkiclient.exe operation=GetCACert&message=MDM 443 - 80.81.82.83 - - 200 0 0 0
Do you see any requests logged in the NDES.log?
Check out the the log at C:\Program Files\Microsoft Configuration Manager\Logs\NDESPlugin.log
Entries should look similair to this:
<![LOG[==========[ NDES policy module started in process 2332 ]==========]LOG]!><time="22:37:15.204+00" date="03-18-2014" component="NDESPlugin" context="" type="1" thread="1356" file="ndesplugin.cpp:195">
<![LOG[Calling Initialize...]LOG]!><time="22:37:15.204+00" date="03-18-2014" component="NDESPlugin" context="" type="1" thread="1356" file="ndesplugin.cpp:226">
<![LOG[certificate registration point web server is sccm.internaldomain.local]LOG]!><time="22:37:15.204+00" date="03-18-2014" component="NDESPlugin" context="" type="1" thread="1356" file="ndesplugin.cpp:250">
<![LOG[NDES thumbprint is 874b8e5864139ad337be36fdd86937fbce1aff9f.]LOG]!><time="22:37:15.204+00" date="03-18-2014" component="NDESPlugin" context="" type="1" thread="1356" file="ndesplugin.cpp:272">
<![LOG[certificate registration point webservice URL is CMCertificateRegistration]LOG]!><time="22:37:15.204+00" date="03-18-2014" component="NDESPlugin" context="" type="1" thread="1356" file="ndesplugin.cpp:314">
<![LOG[CA Issuer Name is ca01.internaldomain.local\\pcitdemo-CA01-CA]LOG]!><time="22:37:15.204+00" date="03-18-2014" component="NDESPlugin" context="" type="1" thread="1356" file="ndesplugin.cpp:356">
<![LOG[Certificate registration port number is 443]LOG]!><time="22:37:15.204+00" date="03-18-2014" component="NDESPlugin" context="" type="1" thread="1356" file="ndesplugin.cpp:387">
<![LOG[Exiting Initialize with 0x0]LOG]!><time="22:37:15.204+00" date="03-18-2014" component="NDESPlugin" context="" type="1" thread="1356" file="ndesplugin.cpp:396">
<![LOG[Calling VerifyRequest ...]LOG]!><time="22:37:19.978+00" date="03-18-2014" component="NDESPlugin" context="" type="1" thread="1356" file="ndesplugin.cpp:646">
<![LOG[Sending request to certificate registration point.]LOG]!><time="22:37:19.978+00" date="03-18-2014" component="NDESPlugin" context="" type="1" thread="1356" file="httprequest.cpp:114">
<![LOG[Verify challenge returns false]LOG]!><time="22:37:20.563+00" date="03-18-2014" component="NDESPlugin" context="" type="1" thread="1356" file="ndesplugin.cpp:834">
<![LOG[Exiting VerifyRequest with 0x0]LOG]!><time="22:37:20.563+00" date="03-18-2014" component="NDESPlugin" context="" type="1" thread="1356" file="ndesplugin.cpp:874">Do you see any request logged on the IIS server of the CRP? What is the status code? Should be 200 in most cases!
Check out the last modified log in C:\inetpub\logs\LogFiles\W3SVC1Do you see any request logged in the CRP log on the CRP server?
C:\Program Files\SMS_CCM\CRP\Logs\crp.logAre you getting this error:
CRP's previous status was 1 (0 = Online, 1 = Failed, 4 = Undefined)
Health check request failed, status code is 403, 'Forbidden'.Make sure you change IIS on your ConfigMgr server - CMCertificateRegistration SSL Settings to Ignore Client Certificates
Do you see a certificate being issued on the issuing CA?
14. Are you getting this output in the ndes logfile?
<![LOG[Failed to retrieve client certificate. Error -2147467259]LOG]!><time="20:48:44.215+00" date="08-17-2015" component="NDESPlugin" context="" type="3" thread="4064" file="httprequest.cpp:240">
<![LOG[Exiting VerifyRequest with 0x80004005]LOG]!><time="20:48:44.215+00" date="08-17-2015" component="NDESPlugin" context="" type="1" thread="4064" file="ndesplugin.cpp:874">
The client auth cert needs to have the internal dns name to present to the CRP.The easiest way to do this is to put both DNS names in the SAN of the certificate. See this technet post for more info.
14. Are you getting Event ID 29 in the NDES Plugin Log? The eventlog might give you this entry:
Event ID: 29The password in the certificate request cannot be verified. It may have been used already. Obtain a new password to submit with this request.
Internal Name: EVENT_MSCEP_INVALID_PASSWORD
Source: Microsoft-Windows-NetworkDeviceEnrollmentService
Description: The Network Device Enrollment Service failed to process a client device's request because the submitted password is invalid.
Diagnose: Check the IIS log to find out what query string was submitted.
Check the device configuration to ensure that the correct password is being submitted as part of the request.
Use certutil to check whether the PKCS7 package from the client is valid (certutil -v p7request.txt, where p7request.txt is a file in which the query string is captured).
Otherwise, enable CAPI2 diagnostics and, if possible, reproduce the error. Resolve: If necessary, contact the vendor of the SCEP client and ensure that the request is being submitted correctly.
So what's up with that? Your service certificate (e.g. for Client Authentication) expired or was revoked.
Note: the registry value of HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\MSCEP\Modules\NDESPolicy\NDESCertThumbprint needs to be MANUALLY update with the thumbprint of the new service certificate, replacing the old certificate’s thumbprint, else NDES will continue trying to use the old certificate, even if it’s archived. Thanks Mr. Hammami for getting to this solution.
--------------
Hope this post helped you implement NDES with Microsoft Intune, please consider leaving a reply if it did!
Comments
- Anonymous
January 01, 2003
Thanks, great guide. Got the infrastructure working to push certificates to iOS devices :)- Anonymous
January 26, 2018
Having a little trouble sending certs to iOS. Successfully delivered a cert to an enrolled Windows client PC so seems the system is working in principle. Would you be able to share your certificate template settings, obvs with any sensitive information redacted? And maybe also the SCEP profile settings from SCCM?
- Anonymous
- Anonymous
January 01, 2003
Great interesting posts about different servers - Anonymous
January 01, 2003
Hi Joel, the 200 is expected (success). This means the device will reach out to the correct NDES server and perform 3 GET requests. You should be able to see at least two of them. The third request is huge in size, about 31kb and could be blocked by many reasons (do you have a reverse proxy in front of the NDES? Did you change the registry and IIS 65543 entries correctly?). If you see the first two 200 success messages but the third one is not shown in IIS logs, the request is blocked - either by the NDES server itself or something in front of it (reverse proxy/firewall etc.). - Anonymous
January 01, 2003
If the IIS log doesn't show any request at all, it means that 1) the URL to your NDES server in the configuration of the CRP (https://ndes.contoso.com/) is incorrect/not resolvable 2) Something in between like a proxy or firewall is blocking the requests.
Enroll a Windows 8.1 tablet and look in the registry what the NDES URL is, paste that in your browser and check the IIS logs on the NDES servers. Something is preventing that part of the communication. - Anonymous
January 01, 2003
Q: Must my NDES web server certificate be publicly trusted??
A: No, but you must deploy the root certificate via Intune/ConfigMgr to the device. The 403 error forbidden is expected, the test device (windows 8.1 in this case) should trust the certificate in Internet Explorer, if it's not trusted the issuing root CA certificate has not arrived yet, which is very unlikely. - Anonymous
January 01, 2003
Hi Phil S, there are a few locations to troubleshoot that, first of all the eventlog (to see if the CRP is running without issues). The open NDESConnector_2015-04-29_XXXXX.svclog with svctraceviewer.exe (seperate download) to decode the contents. Also check the ndesplugin.log. If you see any major errors in those logs, thats where to investigate. - Anonymous
May 12, 2014
Hello! Thanks for the great article. Hoping you can help with a problem I'm seeing: SCCM 2012 R2 (sIngle site/primary). When attempting to choose my enterprise CA, I can select it from the list and also select the template name, but the wizard gives me a red exclamation point saying I need to select an enterprise CA. The CA is published in AD. The only difference I see is that other CA's we've created are published with the FQDN while this particular CA is published as the short name. Thoughts? Thanks for your time!! - Anonymous
May 23, 2014
Thank you for this very timely article! I'm not sure how it would be possible to setup NDES without it.
Regarding the two certificates needed for NDES (1 client, 1 server, or 1 client and server), it is not very clear how those certificates are meant to be obtained. I'm not sure if what I did is correct, but here are my steps:
-On the CA, duplicate the Web Server certificate, name the new template NDES Server.
-Extension Tab, Application Policies: Add Client Authentication (Server is already part of the Web Server template).
-Security: Add NDES server with Read and Enroll.
-Subject Name: Supply in the request.
Publish the new certificate template.
Then on the NDES server, I manually requested a new certificate using the MMC Snapin, Local computer.
-Personal, Request new certificate
-Choose NDES Server template, expand Details, Properties
-Subject Name: Common Name, Value: Public-facing FQDN
These steps seemed to work for me, but I'm not sure if they are all needed or even if they are the correct steps. I'd appreciate any comments. Thank you! - Anonymous
July 07, 2014
I'd just like to extend my thank you for this excellent guide. - Anonymous
July 31, 2014
Thanks for the great guide! I get folliwing error in IIS log: 2014-07-30 22:07:26 112.14.0.1 GET /certsrv/mscep/mscep.dllhttps:/externalFQDN.cloudapp.net/certsrv/mscep/mscep.dll/pkiclient.exe operation=GetCACert&message=MDM 443 - 158.12.123.185 - - 404 0 2 73
All other logs OK, bitt CRP.log shows only "Perf Test Hook, Challenge is read from registry"
Testlab: SCCM 2012 R2 /CU2; CA; NDES with SCEP and Policy Modul
Can anyone help? - Anonymous
August 01, 2014
Hi Christoph, It sounds like the device is not going to the correct URL (error 404). Check the URL you provided during the CRP configuration. - Anonymous
August 02, 2014
Hy Pwigle! Thanks for reply. Yes it was a wrong URL :( copy paste.... Now i have no errors in the log
2014-08-02 18:57:41 fe80::10b7:f62:ec3c:605d%12 POST /CMCertificateRegistration/certificate/generatechallenge - 443 - fe80::10b7:f62:ec3c:605d%12 SMS_CERTIFICATE_REGISTRATION_POINT - 201 0 0 3502
2014-08-02 14:07:40 172.16.0.8 GET /certsrv/mscep/mscep.dll/pkiclient.exe operation=GetCACert&message=MDM 443 - 144.11.115.119 - - 200 0 0 68
But in SCCM i have following error: 0X87D1FDE8 Remediation failed (Certificate Profile - Deployment)
I copied the IPSec (offline request) Certificate, edit the 3 registry entries to the template Name (CustomIPSecV2). In the security tab i added the NDES Service Account for read and enrol).
I deployed the Certificate Profile in SCCM. - Anonymous
August 06, 2014
Hi Pieter,
Very good article. I was curious if you could eleborate (perhaps a link to an article/KB) on why the NDES service should be seperated from the CA issuing server as the policy module would behave unexpectedly? I was not able to find any references about that.
Cheers,
Roy - Anonymous
August 06, 2014
The comment has been removed - Anonymous
August 20, 2014
Fantastic article - thx alot!!!! - Anonymous
September 24, 2014
Thanks for the article, perhaps the fullest I seen for this type of deployment. I do have a question, I have an error in the CRPMSI log file as follows; ERROR: Certificate is not configured on the website for SSL.. The MSI fails to run. I think this is because of SSL not being enabled on the CM server? You mention a CRP certificate, does this need to have any specific EKU? - Anonymous
September 25, 2014
Hi S. Mason, I've seen that error. If i remember correctly you have to make sure a normale webserver certificate is imported on the configmgr server. Try adding a https binding to iis with that cert if it isn't there already. - Anonymous
September 26, 2014
Quick note of thanks. Your comment against my last post sorted the issue I had, CRP certificate created and policy module installed. fingers crossed the testing goes without further issue. - Anonymous
October 02, 2014
Hi, I did have some serious issues to generate certificates to my devices (iOS8, Android 4.4). Then I changed the policy to "include email address in subject name" and then it all started to work just fine. - Anonymous
October 04, 2014
The comment has been removed - Anonymous
October 04, 2014
The comment has been removed - Anonymous
October 06, 2014
I have the same Problem than Christoph:
All logs OK, but CRP.log shows only "Perf Test Hook, Challenge is read from registry"
Any ideas?
thanks,
ckuever - Anonymous
November 13, 2014
Hi,
This hasn't been noted anywhere that I could see but to get my NDES service to function correctly I had to give the NDES service account permission to the private keys assigned to the NDES server. Before this I was getting Windows Event Viewer Schannel errors.
Thanks,
Andrew - Anonymous
December 16, 2014
In portion "Add CRP SSL certificate. (It should be already listed in the drop-down) " you don't specify where this certificate comes from, is it the one created prior with client/server authentication OID's or one generated elsewhere, can you please elaborate - Anonymous
December 16, 2014
Matt D, if I remember correctly this is a default webserver certificate, depending on previous sccm usage already configured (else do that manually). If the cert is ok for usage you will see this in the crpctrl.log as selected (thumbprint). - Anonymous
December 16, 2014
"Perf Test Hook, Challenge is read from registry" is not an error. Its waiting for action. Could be that the larger request doesn't make it through IIS, check all required registry and IIS adjustments. - Anonymous
December 16, 2014
@pwigle thanks for the reply, we have a requirement to split the CRP portion of SCCM off to a separate server so we'll proceed with creating a certificate for that for use in section -> "Specify the URL for the CRP e.g.https://crp.contoso.local/CMCertificateRegistration" - Anonymous
March 31, 2015
Hi Pieter,
I'm stuck in a bit of a loop... Hope you can enlighten me:
After installing the CRP, I get this error:
CRP's previous status was 1 (0 = Online, 1 = Failed, 4 = Undefined)
Health check request failed, status code is 403, 'Forbidden'
So I followed your troubleshooting instructions - Make sure you change IIS on your ConfigMgr server - CMCertificateRegistration SSL Settings to Ignore Client Certificates
But then when I browse thttps://fqdn.contoso.com/CMCertificateRegistration, I get a 404 error, which you advise to bypass by changing CMCertificateRegistration SSL Settings to Require Client Certificates.
My second issue gets resolved, but the first one comes back.. Anyway - you see my problem
What's the best thing to do?
Cheers,
Sean - Anonymous
April 01, 2015
Hi Sean, which OS are you using? I've seen that issue when using Server 2008 (not tested/supported). - Anonymous
April 01, 2015
Hi Pieter,
Unfortunately I'm using Server 2012 R2 on all devices!
It may be worth noting that the issue is raised by asp.net, not by iis? Although I'm not sure how to interpret this - Anonymous
April 09, 2015
Greetings
Excellent blogpost, thank you so much for all this useful information.
I believe I am close to the end.. I followed your instructions and it seems everything is working as per what is written here, but it seems my NDES Server never gets requests for the SCEP certificate.
The IIS logs show no requests beside my manual test ones, and the NDESplugin.log only shows:
Calling Initialize...
(...)
Exiting Initialize with 0x0
Never calls "Verify Request", never sends anything to the CRP.
Which other logs can I check to understand why my SCEP profile is not getting deployed? (The RootCA gets deployed correctly)
Regards - Anonymous
April 13, 2015
The comment has been removed - Anonymous
April 19, 2015
Thanks for your help! All working now.
Turns out the CN on my NDES server certificate was faulty. - Anonymous
April 29, 2015
Do you have a similar walk through for standalone Intune with NDES and Azure App Proxy? I've gone through essentially the same process as you detail, but the CA is not issuing device certs to the iOS devices and I'm having trouble tracking down where the process is failing. Instead of being a ConfigMgr site role, the CRP appears to be handled by the NDES server in IIS (CertificateRegistrationSvc directory, using Microsoft Intune CRP Service Pool app pool).
I can hit the NDES server externally via the Azure App Proxy. I can verify that the iOS device has received the root cert from our internal CA, but it doesn't appear to be completing the SCEP process to received a device cert. Any ideas? - Anonymous
April 29, 2015
Thanks, Pieter. Just to update, I was actually able to resolve the issue. I had only put the public URL for the NDES server itself in the SCEP server URL field for the SCEP policy...not the full path to the mscep.dll (https:///certsrv/mscep/mscep.dll). Once I updated the policy, I saw the successful requests come through in the IIS logs and verified that the certs were issued by the CA and were installed on the device.
Tons of great info in these posts and comments. Many thanks for your patience and support! - Anonymous
August 16, 2015
Have there been any changes regarding SCEP in Windows 10, it doesn't get deployed in our case but works for 8.x, iOS, WP, Android. We're using SCCM 2012 R2 SP1.
I don't even see anything related to certificate deployment under HKCU...MDM, VPN profile gets deployed as does the root CA. I created a new Certificate Profile and made sure Windows 10 is under Supported Platforms, but nothing happens. - Anonymous
August 17, 2015
Hi all,
Everything seems to be working just fine (Root CA and Wireless Profile are sent to ios device). However, the SCEP cert is not being issued and i see the below errors in the NDESPlugin.log file. Any idea what those errors are referencing? - Anonymous
August 17, 2015
Not sure why its not accepting my log file but here is the link to the techNet forum post I made
https://social.technet.microsoft.com/Forums/windows/en-US/6665e971-d2d9-422b-b8a5-80f059595a5f/ndes-sccm-intune-certificate-provisioning?forum=winserversecurity - Anonymous
August 22, 2015
Hi,
In our NDES Server we have this error:
Event ID 29 - 'The password in the certificate request cannot be verified'
Can you help?
Regards,
Bechir - Anonymous
September 22, 2015
Hi all,
I have set up our environment according to this excellent post and SCEP certs are issued to iPADs but my problem is that SCEP certificates are issued twice every time when a device is enrolled or re-mediated non-compliant devices according to policy. On FW I can see that device is hitting twice URL for NDES certificate request and on CA that it issued two certificates for same user, from same SCEP certificate template, for same requester(SCEP service account) and issued in same minute. Have anybody encountered same behavior with certificate issuance? - Anonymous
September 30, 2015
Bechir-
When the policymodule for SCCM or Intune is installed onto an NDES server, then Event ID 29 usually means that the CRP has denied the request. If you are using Intune Hybrid with SCCM, check the CRP.log on the SCCM server where CRP is installed. If you are using Intune Standalone, check the CertificateRegisrationSvc_xxx.svclog (viewable using svctraceviewer.exe - separate download) to see why it was denied.
DanielSt-
I believe you are hitting known issue with iOS devices due to the way cert profile must be embedded inside the VPN or Wifi profile for which you are using it for authentication. This means the devices get the SCEP profile, plus a 2nd SCEP profile embedded inside your wifi or VPN profile. Not sure there's much you can do about it though.
Kevin - Anonymous
October 08, 2015
Hi,
someone seen these Errors in NDESPLugin.log?
Failed to retrieve client certificate. Error -2147024809
Exiting VerifyRequest with 0x80070057
thanks
Phil - Anonymous
October 14, 2015
Hallo Guys,
i have a similar problem as Daniel...only worse. My certificates for iOS devices are also being multiply issued but additionally they are being constantly renewed. One device requests up to 30 certificates a day.
NDES and CRP servers are working properly (certificates are corrrectly issued) - the only question is why are they requested in the first place. What is more, the "old" certificates are not revoked, thus users have multiple active certificates.
Here is my SCEP certificate template info:
1) Purpose - Signature and Encryption
2) Application Policies - Client Authentication
3) Key usage - Digital Signature, non-repudiation
4) Key Size = 2048
5) Windows 2003 Compatible
I use this certificate for our company VPN (F5). Conncetion is possible with these certificates and VPN works perfectly, but only until a new certificate arrives (the user has to type in his logon and password).
Any ideas what could be the cause of the problem?
Thanks in advance
Karol
PS. we also used this guide to configure our environment - thanks:) - Anonymous
December 21, 2015
Hey @kar.koziel.
I know it's been a while since this comment was posted (Oct 2015), however there was a bug with the F5 VPN app that caused continual SCEP certificate requests. It has been fixed in November though, so you shouldn't be seeing multiple certs issued anymore. Please raise a free Intune support case if you're still having issues. Matt - Anonymous
January 07, 2016
For the Issue on MaxQueryString Setting the maxQueryString and maxUrl is not enough. We need to set the httpruntime maxUrlLength and maxQueryStringLength. The compete web.config in this case will look like below
- Anonymous
February 08, 2017
Santhosh,By following the steps exactly above, changing the registry for http service, and the properties in IIS, then restarting the server (http service doesn't pick up the changes until the service is restarted, which is most easily done by simply rebooting the server), everything works end to end. You should not need to do any extra changes in web.config, especially not manually.
- Anonymous
- Anonymous
July 18, 2016
Thanks for the great article it did help get everything working :-) - Anonymous
September 02, 2016
Hi Pieter,We're experiencing the "missing third get" that you've highlighted. Our NDES server is behind a TMG so we're in the processes of checking whether it is bouncing that 32kb get that you reference. Out of interest - and so we can establish what to look for - what does the successful 32kb get look like (or just a portion of it)? - Anonymous
September 15, 2016
Thank you. excellent guide. - Anonymous
November 18, 2016
Thanks for the great tutorial! I'm troubleshooting a Certificate response processing failed error, and I noticed in the section above Configure the Certificate Profile on ConfigMgr where you have a screenshot of the certificate profile wizard, you appear to have selected the server certificate template instead of the client certificate template. Is the screenshot a mistake, or does the profile need the server template? The screenshot appears to contradict your text in that step. - Anonymous
December 13, 2016
HiIs it possible to have such functionality without INTUNE? - Anonymous
December 25, 2016
Hi Pieter,Thanks for the article and it was really fruitful.Just followed your article and configured all required settings. All outputs were resulted as expected except the below URL. https://uslndesprd01.corp.usl.in/certsrv/mscep/mscep?operation=GetCACert&message=MyDeviceIDIt gives 404 error and does not download cert file. Can you please help?crpctrl.logChecking CRP service availability state SMS_CERTIFICATE_REGISTRATION_POINT 12/26/2016 10:07:07 AM 22376 (0x5768) Machine name is 'SCCMPMRPRD01.CORP.USL.IN'. SMS_CERTIFICATE_REGISTRATION_POINT 12/26/2016 10:07:08 AM 22376 (0x5768) Begin validation of Certificate [Thumbprint ede92580190188371ab3416ff3ecee6362538397] issued to 'SCCMPMRPRD01.CORP.USL.IN' SMS_CERTIFICATE_REGISTRATION_POINT 12/26/2016 10:07:08 AM 22376 (0x5768) Certificate has "SSL Client Authentication" capability. SMS_CERTIFICATE_REGISTRATION_POINT 12/26/2016 10:07:08 AM 22376 (0x5768) Completed validation of Certificate [Thumbprint ede92580190188371ab3416ff3ecee6362538397] issued to 'SCCMPMRPRD01.CORP.USL.IN' SMS_CERTIFICATE_REGISTRATION_POINT 12/26/2016 10:07:08 AM 22376 (0x5768) Begin validation of Certificate [Thumbprint 79231e2ba317d9d142710a5b0dda668612c6f6f8] issued to 'SCCMPMRPRD01.CORP.USL.IN' SMS_CERTIFICATE_REGISTRATION_POINT 12/26/2016 10:07:08 AM 22376 (0x5768) Certificate doesn't have "SSL Client Authentication" capabilities. SMS_CERTIFICATE_REGISTRATION_POINT 12/26/2016 10:07:08 AM 22376 (0x5768) Completed validation of Certificate [Thumbprint 79231e2ba317d9d142710a5b0dda668612c6f6f8] issued to 'SCCMPMRPRD01.CORP.USL.IN' SMS_CERTIFICATE_REGISTRATION_POINT 12/26/2016 10:07:08 AM 22376 (0x5768) Skipping this certificate which is not valid for ConfigMgr usage. SMS_CERTIFICATE_REGISTRATION_POINT 12/26/2016 10:07:08 AM 22376 (0x5768) >>> Selected Certificate [Thumbprint ede92580190188371ab3416ff3ecee6362538397] issued to 'SCCMPMRPRD01.CORP.USL.IN' for HTTPS Client Authentication SMS_CERTIFICATE_REGISTRATION_POINT 12/26/2016 10:07:08 AM 22376 (0x5768) CRP's previous status was 0 (0 = Online, 1 = Failed, 4 = Undefined) SMS_CERTIFICATE_REGISTRATION_POINT 12/26/2016 10:07:08 AM 22376 (0x5768) Completed the CRP availability check against local computer. SMS_CERTIFICATE_REGISTRATION_POINT 12/26/2016 10:07:08 AM 22376 (0x5768)crpctrl.loginetpub logs#Software: Microsoft Internet Information Services 8.5 #Version: 1.0 #Date: 2016-12-26 02:31:18 #Fields: date time s-ip cs-method cs-uri-stem cs-uri-query s-port cs-username c-ip cs(User-Agent) cs(Referer) sc-status sc-substatus sc-win32-status time-taken 2016-12-26 02:31:18 ::1 GET /certsrv/mscep/mscep.dll operation=GetCACert&message=SCEP%20Authority 443 - ::1 profiled/1.0+CFNetwork/808.2.16+Darwin/16.3.0 - 200 0 0 0 2016-12-26 02:31:20 ::1 GET /certsrv/mscep/mscep.dll operation=GetCACaps&message=SCEP%20Authority 443 - ::1 profiled/1.0+CFNetwork/808.2.16+Darwin/16.3.0 - 200 0 0 0 2016-12-26 02:31:21 ::1 GET /certsrv/mscep/mscep.dll ... 443 - ::1 profiled/1.0+CFNetwork/808.2.16+Darwin/16.3.0 - 200 0 0 158 2016-12-26 02:31:25 ::1 GET /certsrv/mscep/mscep.dll operation=GetCACert&message=SCEP%20Authority 443 - ::1 profiled/1.0+CFNetwork/808.2.16+Darwin/16.3.0 - 200 0 0 0 2016-12-26 02:31:25 ::1 GET /certsrv/mscep/mscep.dll operation=GetCACaps&message=SCEP%20Authority 443 - ::1 profiled/1.0+CFNetwork/808.2.16+Darwin/16.3.0 - 200 0 0 0 2016-12-26 02:31:30 ::1 GET /certsrv/mscep/mscep.dll ... 443 - ::1 profiled/1.0+CFNetwork/808.2.16+Darwin/16.3.0 - 200 0 0 109 #Software: Microsoft Internet Information Services 8.5 #Version: 1.0 #Date: 2016-12-26 03:53:05 #Fields: date time s-ip cs-method cs-uri-stem cs-uri-query s-port cs-username c-ip cs(User-Agent) cs(Referer) sc-status sc-substatus sc-win32-status time-taken 2016-12-26 03:53:05 ::1 GET /certsrv/mscep/mscep.dll operation=GetCACert&message=SCEP%20Authority 443 - ::1 profiled/1.0+CFNetwork/808.2.16+Darwin/16.3.0 - 200 0 0 562 2016-12-26 03:53:08 ::1 GET /certsrv/mscep/mscep.dll operation=GetCACaps&message=SCEP%20Authority 443 - ::1 profiled/1.0+CFNetwork/808.2.16+Darwin/16.3.0 - 200 0 0 0 2016-12-26 03:53:11 ::1 GET /certsrv/mscep/mscep.dll ... 443 - ::1 profiled/1.0+CFNetwork/808.2.16+Darwin/16.3.0 - 200 0 0 173 2016-12-26 03:53:16 ::1 GET /certsrv/mscep/mscep.dll operation=GetCACert&message=SCEP%20Authority 443 - ::1 profiled/1.0+CFNetwork/808.2.16+Darwin/16.3.0 - 200 0 0 0 2016-12-26 03:53:17 ::1 GET /certsrv/mscep/mscep.dll operation=GetCACaps&message=SCEP%20Authority 443 - ::1 profiled/1.0+CFNetwork/808.2.16+Darwin/16.3.0 - 200 0 0 0 2016-12-26 03:53:19 ::1 GET /certsrv/mscep/mscep.dll ... 443 - ::1 profiled/1.0+CFNetwork/808.2.16+Darwin/16.3.0 - 200 0 0 109 #Software: Microsoft Internet Information Services 8.5 #Version: 1.0 #Date: 2016-12-26 04:14:07 #Fields: date time s-ip cs-method cs-uri-stem cs-uri-query s-port cs-username c-ip cs(User-Agent) cs(Referer) sc-status sc-substatus sc-win32-status time-taken 2016-12-26 04:14:07 ::1 GET /certsrv/mscep/mscep.dll operation=GetCACaps&message=ca 443 - ::1 Dalvik/2.1.0+(Linux;+U;+Android+6.0;+Lenovo+A7020a48+Build/MRA58K) - 200 0 0 1533 2016-12-26 04:14:11 ::1 GET /certsrv/mscep/mscep.dll operation=GetCACaps&message=ca 443 - ::1 Dalvik/2.1.0+(Linux;+U;+Android+6.0;+Lenovo+A7020a48+Build/MRA58K) - 200 0 0 15 2016-12-26 04:14:15 ::1 GET /certsrv/mscep/mscep.dll operation=GetCACert&message=ca 443 - ::1 Dalvik/2.1.0+(Linux;+U;+Android+6.0;+Lenovo+A7020a48+Build/MRA58K) - 200 0 0 31 2016-12-26 04:14:20 ::1 GET /certsrv/mscep/mscep.dll operation=GetCACaps&message=ca 443 - ::1 Dalvik/2.1.0+(Linux;+U;+Android+6.0;+Lenovo+A7020a48+Build/MRA58K) - 200 0 0 0 2016-12-26 04:14:25 ::1 GET /certsrv/mscep/mscep.dll operation=GetCACert&message=ca 443 - ::1 Dalvik/2.1.0+(Linux;+U;+Android+6.0;+Lenovo+A7020a48+Build/MRA58K) - 200 0 0 0 2016-12-26 04:14:31 ::1 GET /certsrv/mscep/mscep.dll operation=GetCACaps&message=ca 443 - ::1 Dalvik/2.1.0+(Linux;+U;+Android+6.0;+Lenovo+A7020a48+Build/MRA58K) - 200 0 0 0 2016-12-26 04:14:44 ::1 GET /certsrv/mscep/mscep.dll ... 443 - ::1 Dalvik/2.1.0+(Linux;+U;+Android+6.0;+Lenovo+A7020a48+Build/MRA58K) - 200 0 0 3219 2016-12-26 04:14:49 ::1 GET /certsrv/mscep/mscep.dll operation=GetCACaps&message=ca 443 - ::1 Dalvik/2.1.0+(Linux;+U;+Android+6.0;+Lenovo+A7020a48+Build/MRA58K) - 200 0 0 0 2016-12-26 04:14:54 ::1 GET /certsrv/mscep/mscep.dll operation=GetCACaps&message=ca 443 - ::1 Dalvik/2.1.0+(Linux;+U;+Android+6.0;+Lenovo+A7020a48+Build/MRA58K) - 200 0 0 0 2016-12-26 04:15:23 ::1 GET /certsrv/mscep/mscep.dll operation=GetCACert&message=SCEP%20Authority 443 - ::1 profiled/1.0+CFNetwork/808.2.16+Darwin/16.3.0 - 200 0 0 0 2016-12-26 04:15:23 ::1 GET /certsrv/mscep/mscep.dll operation=GetCACaps&message=SCEP%20Authority 443 - ::1 profiled/1.0+CFNetwork/808.2.16+Darwin/16.3.0 - 200 0 0 0 2016-12-26 04:15:25 ::1 GET /certsrv/mscep/mscep.dll ... 443 - ::1 profiled/1.0+CFNetwork/808.2.16+Darwin/16.3.0 - 200 0 0 124 2016-12-26 04:15:35 ::1 GET /certsrv/mscep/mscep.dll operation=GetCACert&message=SCEP%20Authority 443 - ::1 profiled/1.0+CFNetwork/808.2.16+Darwin/16.3.0 - 200 0 0 0 2016-12-26 04:15:35 ::1 GET /certsrv/mscep/mscep.dll operation=GetCACaps&message=SCEP%20Authority 443 - ::1 profiled/1.0+CFNetwork/808.2.16+Darwin/16.3.0 - 200 0 0 0 2016-12-26 04:15:38 ::1 GET /certsrv/mscep/mscep.dll ... 443 - ::1 profiled/1.0+CFNetwork/808.2.16+Darwin/16.3.0 - 200 0 0 1242016-12-26 04:20:29 ::1 GET /certsrv/mscep/mscep operation=GetCACert&message=MyDeviceID 443 - ::1 Mozilla/4.0+(compatible;+MSIE+7.0;+Windows+NT+6.3;+WOW64;+Trident/7.0;+.NET4.0E;+.NET4.0C;+.NET+CLR+3.5.30729;+.NET+CLR+2.0.50727;+.NET+CLR+3.0.30729) - 404 0 2 2031inetpub logs - Anonymous
January 05, 2017
Look forward to implementing this. Has anyone tried with Server 2016 instead of Server 2012? Is it supported?I would prefer to use the latest OS if possible. - Anonymous
February 13, 2017
Hi Pieter - thanks for this brilliant guide, all seems to have gone well except..... I'm trying to deploy certificaes to Windows 10 mobile devices (anniversary edition) SCCM says the device is now compliant and I can see a certificate issued in the CA, but using the Certificates App on the mobile device I can't see a personal certificate. I can see the Root and Intermediate from my interal CA OK. All the logs you have suggested look OK, whihc I kind of expect as SCCM shows the device as compliant. Any thoughts please?Many thanks for any help.Graham - Anonymous
May 10, 2017
Thanks for the good article, it was very helpfulI've configured all required settings as descripted. The Devices are successfuly enrolled and the Root Certificate is getting deployed to the devices.But if I want to deploy over SCEP with NDES/Intune, I'm getting an error in the EventViewer of NDES Server and CRP.log of the SCCM Server. Error NDES Server: Event ID: 29, "The password in the certificate request cannot be verified. It may have been used already. Obtain a new password to submit with this request."Error SCCM Server CRP.log:Do you have an idea, what the problem could be or where I can find more information about this error?Thanks a lot for your help and advice.- Anonymous
May 10, 2017
The comment has been removed
- Anonymous
- Anonymous
September 04, 2017
The comment has been removed - Anonymous
October 20, 2017
In case that you get Error 404 as I was getting on SCCM, just proceed and change application pool .NET CLR Version from v4 to v2.Thanks! - Anonymous
October 30, 2017
Hi Pieter, first of all thank you for this great post!Unfortunately I am getting 2 error message at the installation step "CRP Site Server Role" in "crpctrl.log" file:- Failed in CryptAcquireCertificatePrivateKey(...): 0x80090014 (where Certificate is MS-Organization-P2P-Access)-(highlighted in red) CRP's previous status was 0 (0 = Online, 1 = Failed, 4 = Undefined) (where Certificate is my NDES Cert)open https://FQDN/CMCertificateRegistration do show me my Root Cert in a window to accept the cert followed by a 404 error message saying that "the resource can't be found"Any Kind of support is more then welcome.Many thanks, Markus - Anonymous
November 30, 2017
Hi! Thanks for a great article. After installing the CRP I get this error in crpctrl.log:CRP's previous status was 1 (0 = Online, 1 = Failed, 4 = Undefined)Health check request failed, status code is 404, 'Not Found'.I've tried to follow the troubleshooting guide but I've been unable to fix this. Any ideas what I should try?If I browse to https://FQDN/CMCertificateRegistration on the CRP server I get 403 forbidden error as I should.Thanks,Tobias - Anonymous
January 25, 2018
Hi, just need to clarify something if I might about the registry values on the NDES server.You mention to "Make sure that the values of “EncryptionTemplate”, “GeneralPurposeTemplate” and “SignatureTemplate” match the names of the template on your CA". I'm not clear which template(s) these should refer to. On our NDES server we end up with the same value in each key, for some reason it has 'IPSECIntermediateOffline' for each one. Any idea why these values were selected during installation? Should I change these to match the name of the template I want to deploy certs with? e.g. MobileDeviceCert etc.