Large scale spoofing campaign
Over the past week or so we have seen a lot of spoofing going on with campaigns that look like the following:
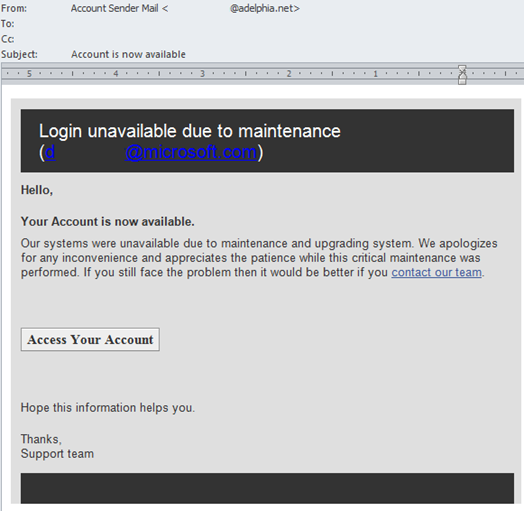
These campaigns have the following characteristics:
1.
They are high-volume zero-day campaigns.
The IPs typically end up on IP blocklists but they are successful at emitting huge blasts of spam before they are caught. This is a pattern that is more typical to 2005-2009 when spammers went with large spam campaigns before scaling back their efforts in an attempt to stay under the radar.
The URLs within the message are compromised.
In the above example, the spam URL is a legitimate site that has been compromised and is hosting malware. The top level site has been disabled (I checked). What this means is that whoever owns the site noticed they were hacked and took it down.
There isn’t a lot of other content to filter on.
The above call-to-action is a URL but the nudge in that direction contains text that has grammatical errors. It is language that might be used in a real outage. Still, the content does contain parts that are spammy although it is difficult to create content rules that are predictive of this sort of thing.
Spam campaigns like these require speed and co-ordination of efforts. If it’s a single spammer behind it, he needs a very complex infrastructure:
Spamming IPs - He has to maintain or acquire a botnet of spamming IPs.
Compromised hosts - He has to maintain or acquire a botnet of compromised URLs – he may have one but probably prefers many more for redundancy. This requires breaking into host and uploading content.
Payload – He has to maintain payload. If the payload is a drive-by download wherein the user clicks the link and gets infected, then he has to have skills writing malware and exploiting browser and OS vulnerabilities. If the payload is spam, then he has to maintain an advertising, payment processing and (most likely) pharmaceutical distribution mechanism.
Speed – The key cog in this wheel is speed. Good spammers have to do this quickly because they know their window of opportunity is small before spam filters catch up. They will set all of this up, send test emails and if they get through, crank up the speed. Their time limit only lasts maybe a few hours.
This is a lot for a single spammer to handle because it requires too many skills. More likely it is the result of an underground economy where each of the above parts (1-3) is maintained by multiple players who buy and sell services from each other.