The Psychology of Spamming, part 5 - Solutions
Solutions
So how do we get people to stop falling for scams?
Will Cognition Save Us?
Thinking about it - Thinking about a decision often changes people’s minds. When people are asked to justify why they like a particular choice, they ended up less happy with their choices. Analyzing our reasons “cognitivizes” our preferences and makes salient certain features about the target that may not have anything to do with why we liked or disliked it in the first place.
In other words, thinking about the emotion removes the effects of immediate emotion. The problem is that reducing emotion makes it difficult for us, as humans, to make actionable decisions. Without emotions, we would never do anything at all.
Anger - Ironically, if people got angry when they were spammed, they would be less likely to fall for scams. People who are angry are more likely to overlook mitigating conditions before assigning blame (this is a scammer trying to fleece me vs I feel sorry for his dead uncle), to perceive ambiguous behavior as hostile (this person is up to no good), and to discount the role of uncontrollable factors (I don’t care that someone broke into my account).
Learning and education - What does seem to work is that increasing the decision makers’ level of vigilance is often sufficient to attenuate the impact of weak-to-moderate immediate emotions. For higher levels, the realization that the message is a scam relieves the emotions that have been invoked. In other words, when it comes to spamming, education does work.
People learn to recognize scams and the emotional reactions that are raised become less susceptible over time. This is similar to the chess player that learns pattern recognition – they can recognize good outcomes vs bad ones because they have played so many games.
Can Technology Save Us?
On the other hand, for those of us in the tech industry, or the financial industry, or law enforcement, we can’t wait around for our brains to evolve. Education is too slow, and nobody is going to spend hours upon hours learning how to recognize phishing scams or 419 scams. While we are waiting for evolution to catch up, people are being defrauded now.
Everything is achievable through technology.
- Howard Stark
Technology has been used to bridge biological gaps. Through medical science, human life spans have been extended. Automobiles and improved agricultural techniques have increased our capacity for food production and distribution. But can technology save us from malicious intent?
There are a few techniques that software vendors employ to combat the problem of financially-motivated spam.
Visual Identification
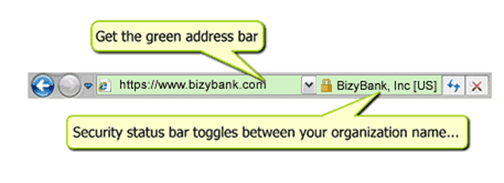
One the techniques that legitimate websites use is certificates, which allows browsers to identify web sites with an actual identifying certificate (that has been verified by a trusted 3rd party). Users can then see the padlock in the corner of the browser, or in the address bar, and the address bar is also color-coded with green in some browsers (such as newer versions of Internet Explorer). Websites that are untrusted do not have the lock and ones that are suspicious have the address bar color-coded red.
This makes use of human heuristics; from an early age we know that green means “Go” and red means “Stop.” Responsible brands make use of every legitimate identifier they can think of so that when consumers go to their page, they know that they can trust it.
Unfortunately, compliance using digital certificates isn’t uniform across many phished brands. And whether or not users actually pay attention to the color coding is up for debate when it comes to phishing.
Note that visual identification is a tool to help the end-user tell the difference between something that is real and something that is not. The end user still needs to know the difference.
Sender Authentication
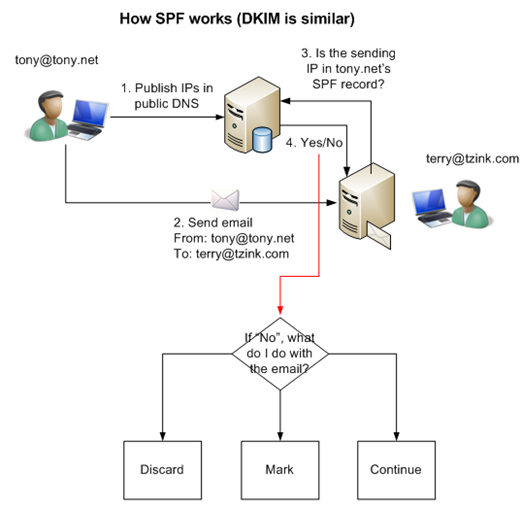
Sender authentication is a mechanism, in email, that allows a brand to set up policies that allow receivers a way to identify mail that truly comes from that brand. If the mail is trying to appear like it is, but is not in the brand’s official list of permitted senders, the brand has the ability to say what to do with that email. Thus, the receiver has instructions about what to do with spoofed email, and if they positively identify the sender, they can flag to the end user that the sender is trusted. Two technologies for doing this are SPF (Sender Policy Framework) and Domain Keys Identified Mail.
One of the main weaknesses of sender authentication is that it relies upon the sending domain to make the identification for spoofing. If a spammer puts in a domain that looks and sounds similar, like faceb00k.com, and uses visually identifying pictures, then the end user can be fooled. In fact, this is something that phishers regularly do. The actual spoofed brand is normally further on down in the URL, like https://www.fakedomain.com/facebook.com/signin.aspx.
Another weakness is that sender authentication doesn’t do anything to prevent the case where no identification is required. For example, in a 419 or lottery scam, it doesn’t matter if the sender sends from a Yahoo or Hotmail alias. Identifying the user is irrelevant because they are not relying upon visual recognition of a trusted brand, but rather, trying to invoke an emotional response from the end user tricking them into performing some action, usually sending money to the spammer.
URL Inspection
One reactive technique is URL inspection, or reputation analysis. Browsers today make use of lists of URLs. If the URL goes to a malicious site, then a message is displayed to the end user indicating that site is malicious.
URL lists are populated by a collection of volunteers. When a new link is discovered, trusted users are eligible to submit the links to a central repository where they are made available to others to use. The browsers download them and upload them to individual users.
URL inspection takes the decision away from the end user who may not be able to tell the difference between a malicious site and a legitimate one by telling them, in big red text, that they are going to some place dangerous. It’s similar to somebody automating their bill payments by having the bank pay them. If you can’t trust yourself to pay your bills on time, have someone else do it for you so you don’t get into trouble.
The drawback of URL inspection is three-fold:
- It takes much effort to maintain it. These URL lists require human and physical resources. Hardware goes down constantly. It’s not free to maintain.
- It is prone to false positives. Because of the way submissions are done, there is some automation. With automation comes false positives, and with false positives comes the blocking of legitimate sites. This degrades the user experience.
- It is reactive. Somebody has to detect and submit the malicious URL. Miscreant actors are endlessly creating new domains and in the window of time between submission, verification, download and distribution, people can still get scammed. The time delay prevents URL inspection from being a panacea to the problem of phishing.
DNS Takedowns
DNS takedowns are the next logical step of URL filtering. Once a site has been identified as malicious, brand owners can take action to have them removed from DNS. The problems associated with DNS takedowns are the same as for URL inspection, except one more is added – the amount of human effort involved, when taking out lots of domains, doesn’t scale. Humans usually have to get involved when it comes to taking domains out of DNS and that takes a lot of time and effort. Many organizations just don’t have the resources.
Part 1 - How our brains work
Part 2 - The Limbic system, cognition and affect
Part 3 - External factors that influence our decisions
Part 4 - Why we fall for scams
Parr 5 - Solutions
Part 6 - The Flynn Effect