Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
This is an extension of this blog: Signing Windows 8 applications using an Internal PKI which mentions you can use Windows Server 2008 R2 to create a code signing certificate but does not tell you exactly how. Please read that previous article first for an overview. Then you can follow these steps to create a Code Signing template on your Windows Server 2008 R2 Certificate Authority.
Creating a Certificate for signing Windows Store apps on Windows Server 2008 R2
This process is nearly identical to the 2012 instructions.
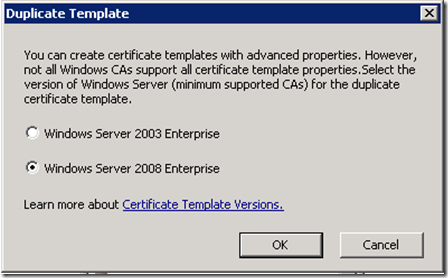
To MMC add the Certificate Templates add-in. Right click on ‘Code Signing’ and choose ‘Duplicate Template’ from the context menu:
In the next dialog choose ‘Windows Server 2008 Enterprise’ and hit ‘OK’:
In the General Tab, give your Template a name…
In the Request Handling tab, check ‘Allow private key to be exported’
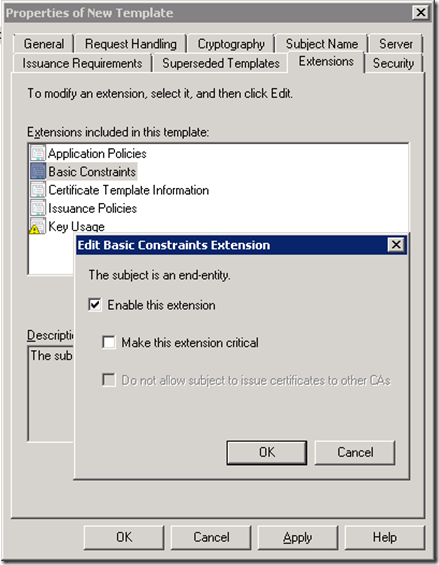
In the Extensions tab, click on ‘Basic Constraints’ and hit the ‘Edit’ button, then check ‘Enable this extension’ (hit ‘OK’)
In the Subject Name tab choose ‘Supply in the request’ and accept the warning in the dialog that appears
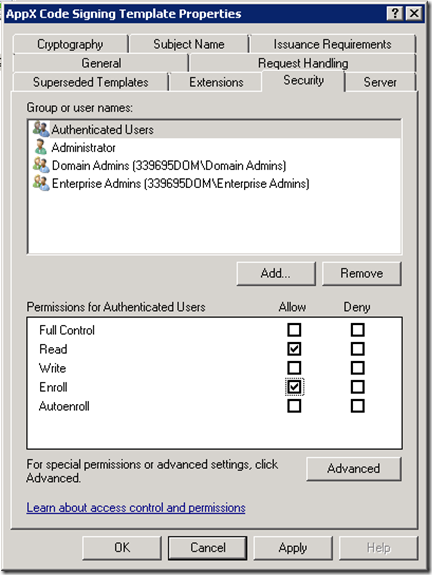
In the Security Tab, assign ‘Read’ and ‘Enroll’ permissions for the group that you want to be able to request this certificate. In my case, any authenticated user but you may want to have a development group created for this.
Hit ‘OK’ and your template will be created.
Now using the Certification Authority Add-In (this is different from the Certificate Templates) you need to allow this template to be issued by the CA
Right click on the ‘Certificate Templates’ node of your CA and choose ‘New’ and ‘Certificate Template to Issue’
Choose the template you just created:
Hit ‘OK’ and you will see the new certificate template added:
Now that the template has been added you can request a Code Signing certificate and use it to sign the APPX package. See the original post for this process:
Signing Windows 8 applications using an Internal PKI
GPO Settings for App Packaged Deployment on Windows Server 2008 R2
The next step is to get the new GPO settings in your Domain controller. You need to do this because Windows Server 2008 R2 does not include the GPO setting for Windows 8.0 or later. Without them you cannot use the previous post to create the GPO exceptions you need to install and run your app. To do this follow the two links below to understand what ADMX files are and where to download the 8.1 admx files.
Managing Group Policy ADMX Files Step-by-Step Guide
Administrative Templates (.admx) for Windows 8.1 and Windows Server 2012 R2
Once you install the admx files you simply need to copy the ones you want to your policy definition store so that the GPO editor will pick them up. In my case I copied these files from:
C:\Program Files (x86)\Microsoft Group Policy\Windows 8.1-Windows Server 2012 R2\PolicyDefinitions\AppxPackageManager.admx
to:
C:\Windows\PolicyDefinitions\AppxPackageManager.admx
and from:
C:\Program Files (x86)\Microsoft Group Policy\Windows 8.1-Windows Server 2012 R2\PolicyDefinitions\en-us\appxpackagemanager.adml
to:
C:\Windows\PolicyDefinitions\en-US\appxpackagemanager.adml
Then these will appear in your GPO editor and you can follow the original post.
Installing Windows Store app by side loading on Windows 8.1 Enterprise
Finally after following the original post you need to ensure the client computer gets this new policy. You can force this from an administrative command prompt with this command: gpupdate /force
Next I simply removed some code from the install file created by visual studio: Add-AppDevPackage.ps1 and uses that to install the package:
I changed this function and added this so the developer license check does nothing:
function CheckIfNeedDeveloperLicense
{
$Result = $false
return $Result
}
Note: You could also just use Add_AppxPackage but the ps1 file has some cool error checking etc…
Conclusion
I hope you found this a useful extension to the original post. Please let me know if this helped you out! Be sure to follow my and our team on twitter @jsandersrocks and @WSDevSol.
Comments
- Anonymous
August 25, 2014
When I did New Certificate Template to Issue, my template didn't show up in the list. I had to run the following command for some reason instead: certutil -SetCAtemplates +AppXCodeSigningTemplate Any idea on why I had to do that?