Installing a Two Tier PKI Hierarchy in Windows Server 2012: Part I, Installing a Root Certification Authority with PowerShell
In this blog posting I will cover installing a Root Certification Authority with PowerShell in Windows Server 2012. With this Blog Series I am not going to get into the details of best practices. In other words I am not going to get into the “Why?” of the configuration decisions I have made. In some future blog posts I will talk about best practices. For now I am just going to cover installing the Roles and Role Services.
In this article I will talk about the steps required to install a standalone Root Certification Authority with PowerShell. In this article I will not performing the post-configuration, I will however, cover that in a follow up blog.
In this example I am going to install a Certification Authority with the following base configuration:
- · CA Type: Standalone Root Certification Authority
- · Common Name: FourthCoffee Root Certification Authority
- · Key Storage Provider: RSA#Microsoft Software Key Storage Provider
- · Public Key Algorithm: RSA
- · Hashing Algorithm: SHA1
- · Key Length: 2048
- · Validity Period: 20 Years
I will be installing the ADCS Role with PowerShell. Additional documentation for these steps can found https://technet.microsoft.com/en-us/library/hh848390 and https://technet.microsoft.com/en-us/library/hh848389.
Launching PowerShell
The first step of course is to launch PowerShell. This can be accomplished by starting a command prompt and typing powershell and pressing the Enter key or by clicking on the PowerShell icon on the taskbar.
Import Server Manager Module
The first step is to import the Server Manager Module for PowerShell which will then allow you to add the ADCS feature. To import the Server Manager Module for Powershell type: Import-Module ServerManager and press Enter .
Installing ADCS Binaries
The next step is to install the ADCS binaries so that we can install ADCS. To install the ADCS binaries type: Add-WindowsFeature Adcs-Cert-Authority and press Enter.
Install Certification Authority Role
To install the Certification Authority Role you will need to use the Install-AdcsCertificationAuthority cmdlets. The options for the Install-AdcsCertificationAuthority cmdlets is available here: https://technet.microsoft.com/en-us/library/hh848390.aspx.
Below is the entire command that I will be using to install Active Directory Certificate Services in my environment:
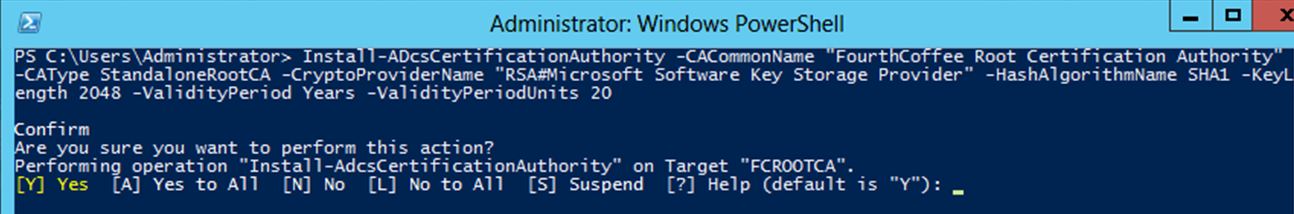
Install-ADcsCertificationAuthority -CACommonName "FourthCoffee Root Certification Authority" -CAType StandaloneRootCA -CryptoProviderName "RSA#Microsoft Software Key Storage Provider" -HashAlgorithmName SHA1 -KeyLength 2048 -ValidityPeriod Years -ValidityPeriodUnits 20
I am using the CACommonName option to specify a Common Name of “FourthCoffee Root Certification Authority”. Then I am specifying the CAType option to set the CA Type to a Standalone Root CA. Next I am selecting my Key Storage Provider of “RSA#Microsoft Software Key Storage Provider” with the CryptoProviderName option. I have decided to use SHA1 as the hashing algorithm and therefore am using SHA1 with the HashAlgorithmName option. Then I am setting the RSA Key Length to 2048-bit with the KeyLength option. And finally, I am giving the Root CA a validity period of “20 Years” with the Validity Period and ValidityPeriodUnits options.
After you run the Install-AdcsCertificationAuthority cmdlet you will be prompted to accept the changes as seen in the screenshot below:
After running the Install-AdcsCertificationAuthority cmdlet I have successfully installed Certificate Services. However, the Certification Authority management tools are still not installed.
Installing the Certification Authority Management Tools
To Install the Certification Authority Management Tools type the following command in PowerShell and hit enter: Install-WindowsFeature RSAT-ADCS-Mgmt.
Conclusion
In this article I have covered how to Install a Standalone Root Certification Authority with PowerShell on Windows Server 2012. I have not covered configuring the CA after installation. However, I will be covering the configuration of the CA in an upcoming blog posting.