Windows 7 DirectAccess Explained
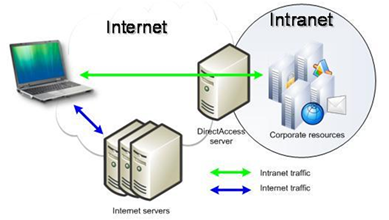 The Windows® 7 and Windows Server® 2008 R2 operating systems introduce DirectAccess, a new solution that provides users with the same experience working remotely as they would have when working in the office. With DirectAccess, remote users can access corporate file shares, Web sites, and applications without connecting to a virtual private network (VPN). Further DirectAccess separates intranet traffic from Internet traffic as shown on the right and reduces unnecessary traffic on the corporate network.
The Windows® 7 and Windows Server® 2008 R2 operating systems introduce DirectAccess, a new solution that provides users with the same experience working remotely as they would have when working in the office. With DirectAccess, remote users can access corporate file shares, Web sites, and applications without connecting to a virtual private network (VPN). Further DirectAccess separates intranet traffic from Internet traffic as shown on the right and reduces unnecessary traffic on the corporate network.
DirectAccess requirements include:
- DirectAccess Server: This is a Windows Server 2008 R2 server with the server feature, DirectAccess Management Console, added. A DirectAccess server must be joined to an Active Directory® domain and cannot be behind a Network Address Translation, or NAT, device. In addition, a DirectAccess server must have two network adapters: one connected to the Intranet, and the other to the internet with at least two consecutive public IPv4 addresses.
- DirectAccess Client: Windows 7 is the supported client OS.
- At least one domain controller and Domain Name System (DNS) server running Windows Server 2008 SP2 or Windows Server 2008 R2
- A Public Key Infrastructure (PKI) for issuing computer certificates, smart card certificates, and, for Network Access Protection (NAP), health certificates
- IPsec policies to specify protection for traffic
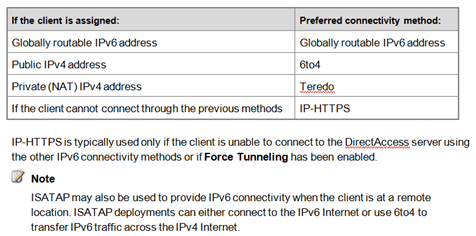
- IPv6 transition technologies, i.e. ISATAP (RFC 4214), Teredo (RFC 4380), and 6to4 (RFC 3056), for DirectAccess server
- Optionally, a non-Microsoft NAT-PT (RFC 2766) device to provide access to IPv4-only resources for DirectAccess clients
Here’s how DirectAccess works:
A DirectAccess client computer boots and detects a network connection.
The DirectAccess client computer attempts to connect to an intranet-only web site specified in DirectAccess configuration. If the web site is available, the DirectAccess client determines that it is connected to the intranet, and the DirectAccess connection process stops. And the effective DNS Name Resolution Policy revealed by the command, netsh name show effectivepolicy, should indicate DirectAccess is turned off if the client is in the intranet. On the other hand, if the Web site is not available, the DirectAccess client determines that it is connected to the Internet and the DirectAccess connection process continues. The DirectAccess client computer connects to the DirectAccess server using IPv6 and IPsec. If a native IPv6 network isn’t available, the client establishes an IPv6-over-IPv4 tunnel using 6to4 or Teredo. If a firewall or proxy server prevents the client computer using 6to4 or Teredo from connecting to the DirectAccess server, the client automatically attempts to connect using the IP-HTTPS protocol, which uses a Secure Sockets Layer (SSL) connection to ensure connectivity as shown below.
As part of establishing the IPsec session, the DirectAccess client and server authenticate each other using computer certificates for authentication. Two types of IPsec protection: end-to-end and end-to-edge are available for a DirectAccess client to connect to intranet resources.
By validating Active Directory® group memberships, the DirectAccess server verifies that the computer is authorized to connect with DirectAccess. To mitigate the risk of denial of service (DoS) attacks, IPsec on the DirectAccess server de-prioritizes key negotiation traffic using Differentiated Services Code Points (DSCPs).
If Network Access Protection (NAP) is enabled and configured for health validation, the DirectAccess client obtains a health certificate from a Health Registration Authority (HRA) located on the Internet prior to connecting to the DirectAccess server. The HRA forwards the DirectAccess client’s health status information to a NAP health policy server. The NAP health policy server processes the policies defined within the Network Policy Server (NPS) and determines whether the client is compliant with system health requirements. If so, the HRA obtains a health certificate for the DirectAccess client. When the DirectAccess client connects to the DirectAccess server, it submits its health certificate for authentication.
The DirectAccess server begins forwarding traffic from the DirectAccess client to the intranet resources to which the user has been granted access.
Notice the DirectAccess connection process happens automatically once a DirectAccess client boots up without requiring a user to log on.