Unable to start Azure ATP Service
Take in consideration a scenario where you deployed Azure ATP, and after the service has worked for some time, one day the service Azure Advanced Threat Protection Sensor keeps on Starting, and after some time it quits (doesn’t show any status), it comes back to Starting, and keeps on this loop. If you go to event viewer, you an event like this one:
Log Name: System
Source: Service Control Manager
Date: 9/14/2018 10:32:52 AM
Event ID: 7031
Task Category: None
Level: Error
Keywords: Classic
User: N/A
Computer: BRUTOS.fabrikam.com
Description:
The Azure Advanced Threat Protection Sensor service terminated unexpectedly. It has done this 18 time(s). The following corrective action will be taken in 5000 milliseconds: Restart the service.
The next step in this type of situation is to look at the “Microsoft.Tri.sensor-Errors.log” file located in the “%programfiles%\Azure Advanced Threat Protection sensor\Version X\Logs” folder. Once you review this file, you may see something like this:
2018-09-14 15:35:50.9871 Error DirectoryServicesClient+<CreateLdapConnectionAsync>d__34 Microsoft.Tri.Infrastructure.ExtendedException: Failed to connect to domain controller [DomainControllerDnsName=BRUTOS.fabrikam.com ErrorCode=49] ---> System.DirectoryServices.Protocols.LdapException: The supplied credential is invalid.
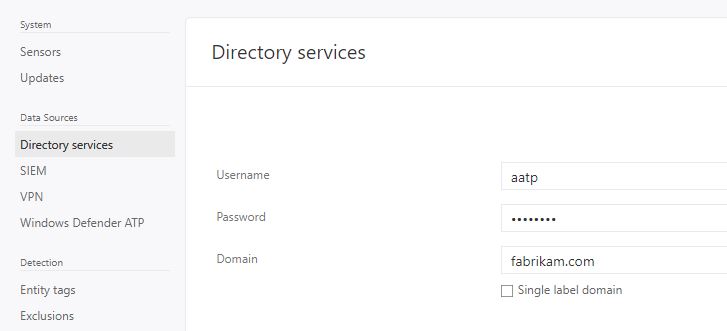
Yep, that’s ritght, it was the credential, and you know why? Because the account that it was created and used on step 2 of the Azure ATP deployment changed the password. Every time you change this account's password, you need to update the user's information on Azure ATP Portal, under Directory Services as shown below:
Lesson learned: it is imperative to always change your password, and change it according to your company’s password policy, however make sure to also update the account's information on Azure ATP portal, otherwise you will face a similar issue.
Comments
- Anonymous
January 02, 2019
The comment has been removed- Anonymous
January 03, 2019
Hello PugJ, In order to investigate this issue we would need more logs. I recommend you to post this question on our Tech Community Group (https://techcommunity.microsoft.com/t5/Azure-Advanced-Threat-Protection/bd-p/AzureAdvancedThreatProtection). This could be something as simple as multiforest not working (the version that is available today, requiring at a minimum one-way trust) or it could be that there is no trust between the two forests. Investigate those two items, and if they are okay, post your question on the Tech Community Group.
- Anonymous