Active Directory: LDAPs(636) and MSFT-GC-SSL(3269) Service
Applies To:
Windows Server 2012, Windows Server 2012 R2 Preview
DoLdapInitialize
ADDS standard ports are opened during DCPROMO mainly LDAP initiation. Ports are opened during dsa init, specifically in ' DoLdapInitialize' - If we stop the 'Active Directory Domain Service' in service.msc neither of the port is listening.
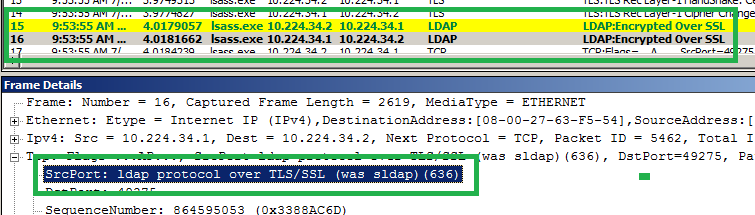
My main purpose of this article is ldaps service & msft-gc-ssl service . Port 636 & 3269 are listing after promoting a DC. We can test that using Telnet, PortQuery , Netmon or Wireshark etc. The result below is taken from newly built DC using PortQry.
PortQry output after promoting a DC for SSL ports.
TCP port 636 (ldaps service): LISTENING
portqry.exe -n msft.net -e 636 -p TCP exits with return code 0x00000000.
TCP port 3269 (msft-gc-ssl service): LISTENING
portqry.exe -n msft.net -e 3269 -p TCP exits with return code 0x00000000.
There is fantastic tool called LDP.EXE which was the part of the windows support tools in earlier version of windows OS (2003). Now days if we installed a DC automatically that is available into a DC due to RSAT. We can connect port 389 & 3268 through ldp but not 636/3269. Those SSL ports are only listened LDAPS when we put the valid certificate into DCs. We need valid SAN, Intended purpose for that certificate (EKU).
LDP.EXE output after connecting the SSL ports.
If your certificate server itself a DC then you no need to worry for SSL ports. Those ports are connected through LDP.EXE.
ld = ldap_sslinit("ADS01HAMLOK.ms.net", 636, 1);
Error 0 = ldap_set_option(hLdap, LDAP_OPT_PROTOCOL_VERSION, 3);
Error 0 = ldap_connect(hLdap, NULL);
Error 0 = ldap_get_option(hLdap,LDAP_OPT_SSL,(void*)&lv);
Host supports SSL, SSL cipher strength = 128 bits
Established connection to ADS01HAMLOK.ms.net.
Retrieving base DSA information...
Getting 1 entries:
Dn: (RootDSE)
configurationNamingContext: CN=Configuration,DC=ms,DC=net;
currentTime: 7/6/2013 7:39:46 PM India Standard Time;
defaultNamingContext: DC=ms,DC=net;
dnsHostName: ADS01HAMLOK.ms.net;
domainControllerFunctionality: 4 = ( WIN2008R2 );
domainFunctionality: 2 = ( WIN2003 );
dsServiceName: CN=NTDS Settings,CN=ADS01HAMLOK,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=ms,DC=net;
forestFunctionality: 2 = ( WIN2003 );
highestCommittedUSN: 24762;
isGlobalCatalogReady: TRUE;
isSynchronized: TRUE;
ldapServiceName: ms.net:ads01hamlok$@MS.NET;
namingContexts (5): DC=ms,DC=net; CN=Configuration,DC=ms,DC=net; CN=Schema,CN=Configuration,DC=ms,DC=net; DC=DomainDnsZones,DC=ms,DC=net; DC=ForestDnsZones,DC=ms,DC=net;
rootDomainNamingContext: DC=ms,DC=net;
schemaNamingContext: CN=Schema,CN=Configuration,DC=ms,DC=net;
serverName: CN=ADS01HAMLOK,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=ms,DC=net;
subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=ms,DC=net;
supportedCapabilities (5): 1.2.840.113556.1.4.800 = ( ACTIVE_DIRECTORY ); 1.2.840.113556.1.4.1670 = ( ACTIVE_DIRECTORY_V51 ); 1.2.840.113556.1.4.1791 = ( ACTIVE_DIRECTORY_LDAP_INTEG ); 1.2.840.113556.1.4.1935 = ( ACTIVE_DIRECTORY_V61 ); 1.2.840.113556.1.4.2080;
supportedControl (28): 1.2.840.113556.1.4.319 = ( PAGED_RESULT ); 1.2.840.113556.1.4.801 = ( SD_FLAGS ); 1.2.840.113556.1.4.473 = ( SORT ); 1.2.840.113556.1.4.528 = ( NOTIFICATION ); 1.2.840.113556.1.4.417 = ( SHOW_DELETED ); 1.2.840.113556.1.4.619 = ( LAZY_COMMIT ); 1.2.840.113556.1.4.841 = ( DIRSYNC ); 1.2.840.113556.1.4.529 = ( EXTENDED_DN ); 1.2.840.113556.1.4.805 = ( TREE_DELETE ); 1.2.840.113556.1.4.521 = ( CROSSDOM_MOVE_TARGET ); 1.2.840.113556.1.4.970 = ( GET_STATS ); 1.2.840.113556.1.4.1338 = ( VERIFY_NAME ); 1.2.840.113556.1.4.474 = ( RESP_SORT ); 1.2.840.113556.1.4.1339 = ( DOMAIN_SCOPE ); 1.2.840.113556.1.4.1340 = ( SEARCH_OPTIONS ); 1.2.840.113556.1.4.1413 = ( PERMISSIVE_MODIFY ); 2.16.840.1.113730.3.4.9 = ( VLVREQUEST ); 2.16.840.1.113730.3.4.10 = ( VLVRESPONSE ); 1.2.840.113556.1.4.1504 = ( ASQ ); 1.2.840.113556.1.4.1852 = ( QUOTA_CONTROL ); 1.2.840.113556.1.4.802 = ( RANGE_OPTION ); 1.2.840.113556.1.4.1907 = ( SHUTDOWN_NOTIFY ); 1.2.840.113556.1.4.1948 = ( RANGE_RETRIEVAL_NOERR ); 1.2.840.113556.1.4.1974 = ( FORCE_UPDATE ); 1.2.840.113556.1.4.1341 = ( RODC_DCPROMO ); 1.2.840.113556.1.4.2026 = ( DN_INPUT ); 1.2.840.113556.1.4.2064 = ( SHOW_RECYCLED ); 1.2.840.113556.1.4.2065 = ( SHOW_DEACTIVATED_LINK );
supportedLDAPPolicies (14): MaxPoolThreads; MaxDatagramRecv; MaxReceiveBuffer; InitRecvTimeout; MaxConnections; MaxConnIdleTime; MaxPageSize; MaxQueryDuration; MaxTempTableSize; MaxResultSetSize; MinResultSets; MaxResultSetsPerConn; MaxNotificationPerConn; MaxValRange;
supportedLDAPVersion (2): 3; 2;
supportedSASLMechanisms (4): GSSAPI; GSS-SPNEGO; EXTERNAL; DIGEST-MD5;
-----------
53 = ldap_set_option(ld, LDAP_OPT_ENCRYPT, 1)
res = ldap_bind_s(ld, NULL, &NtAuthIdentity, NEGOTIATE (1158)); // v.3
{NtAuthIdentity: User='NULL'; Pwd=<unavailable>; domain = 'NULL'}
Authenticated as: 'MS\Administrator'.
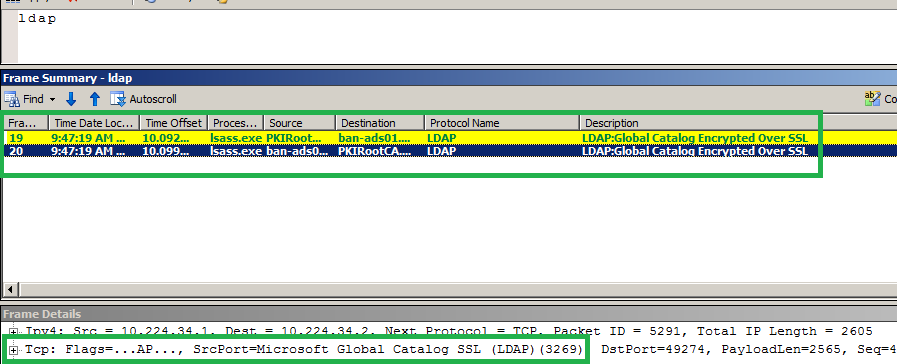
NETMON capture for SSL Ports
Also Netmon results are taken after putting the valid certificate into a Domain Controller. Used the filter " LDAP". Also you can use ".Protocol.LDAP". You will get the same result. Here I have installed the netmon in DC.
Listening the ldaps Port (636) into the below Capture
Listening the gc-ssl Port (3269) into the below Capture
Network capture without netmon
Also you can trace without the Netmon/WireShare. Using Netsh but it is applicable Windows 2008R2 and Windows 7 and upper version OS.
For starting the capture.
netsh trace start capture=yes tracefile=cap.etl
For stopping the capture
netsh trace stop
For reading the .etl file you need the netmon anywhere.
Netsh trace will be created two files. see the below snap. For reading the .etl file you need to select the Windows Parser in Netmon.
Cert server into a domain controller is not recommended.
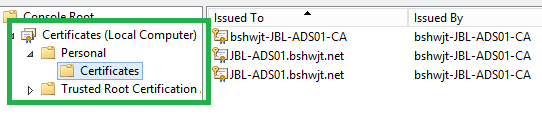
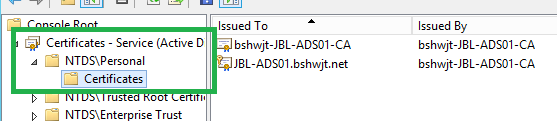
We need additional steps for listening the ssl ports for DCs If cert server in a member server .We need to publish the certificate template into the cert server & that certificate template need to put DC’s local computer->personal or NTDS->Personal store.
Local computer->personal store
NTDS->Personal store
(This store is available only in DC. When we have more than one cert template for Server Authentication, we can use this store for avoiding the conflict)
Publish a cert Template
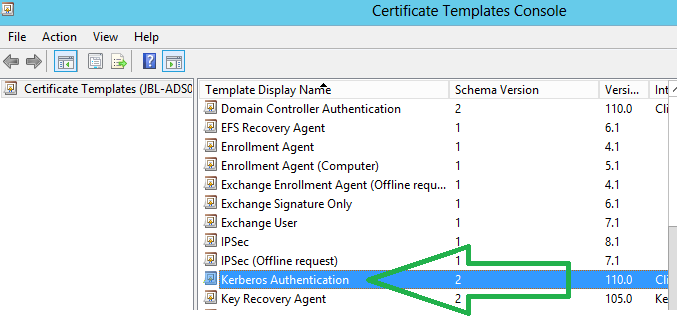
Here I have used "Kerberos Authentication" template for publishing the new certificate template.
Log into the certificate server . Run " certtmpl.msc" & chose the Kerberos Authentication Template.
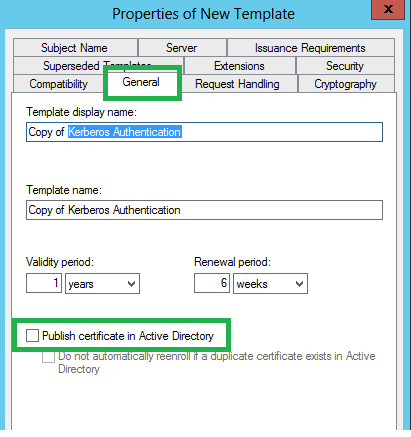
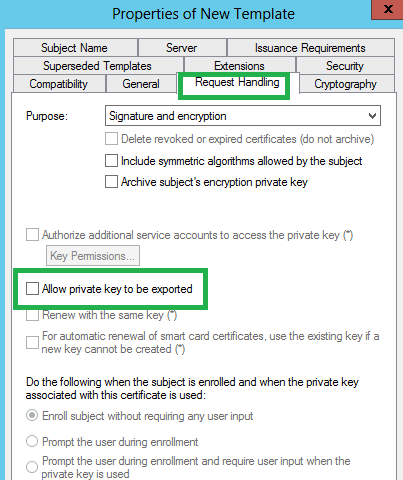
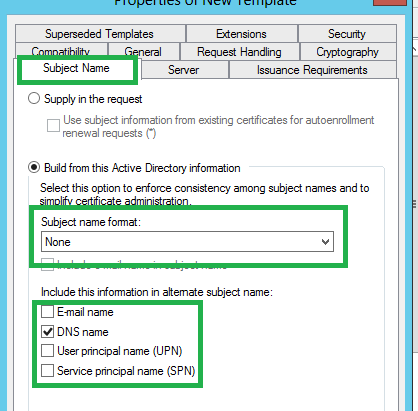
We need to set few properties before publishing a certificate template. Those are marked as green.
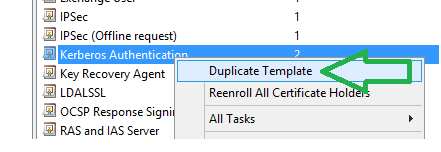
Click on Duplicate Templete.
Publish cert in AD.
Allow Pvt. key to be exported.
Subject Name format
After publishing that cert you can check the properties using " certutil -v -template <Template_Name>". Here my cert template name is LDAPSSL. See the following output.
certutil -v -template LDAPSSL
PS C:\> certutil -v -template LDAPSSL
``Name: Active Directory Enrollment Policy
``Id: {32376692-6063-4EDC-A375-572FED78C626}
``Url: ldap:
34 Templates:
``Template[21]:
``TemplatePropCommonName = LDAPSSL
``TemplatePropFriendlyName = LDAPSSL
``TemplatePropEKUs =
4 ObjectIds:
``1.3.6.1.5.2.3.5 KDC Authentication
``1.3.6.1.4.1.311.20.2.2 Smart Card Logon
``1.3.6.1.5.5.7.3.1 Server Authentication
``1.3.6.1.5.5.7.3.2 Client Authentication
``TemplatePropCryptoProviders =
``0: Microsoft RSA SChannel Cryptographic Provider
``TemplatePropMajorRevision = 64 (100)
``TemplatePropDescription = Computer
``TemplatePropSchemaVersion = 2
``TemplatePropMinorRevision = 1
``TemplatePropRASignatureCount = 0
``TemplatePropMinimumKeySize = 800 (2048)
``TemplatePropOID =
``1.3.6.1.4.1.311.21.8.1546289.5796744.12012220.14775765.9035062.224.8004685.4056790 LDAPSSL
``TemplatePropV1ApplicationPolicy =
4 ObjectIds:
``1.3.6.1.5.2.3.5 KDC Authentication
``1.3.6.1.4.1.311.20.2.2 Smart Card Logon
``1.3.6.1.5.5.7.3.1 Server Authentication
``1.3.6.1.5.5.7.3.2 Client Authentication
``TemplatePropEnrollmentFlags = 28 (40)
``CT_FLAG_PUBLISH_TO_DS -- 8
``CT_FLAG_AUTO_ENROLLMENT -- 20 (32)
``TemplatePropSubjectNameFlags = 18c00000 (415236096)
``CT_FLAG_SUBJECT_ALT_REQUIRE_DOMAIN_DNS -- 400000 (4194304)
``CT_FLAG_SUBJECT_ALT_REQUIRE_SPN -- 800000 (8388608)
``CT_FLAG_SUBJECT_ALT_REQUIRE_DNS -- 8000000 (134217728)
``CT_FLAG_SUBJECT_REQUIRE_DNS_AS_CN -- 10000000 (268435456)
``TemplatePropPrivateKeyFlags = 10 (16)
``CT_FLAG_EXPORTABLE_KEY -- 10 (16)
``TemplatePropGeneralFlags = 20060 (131168)
``CT_FLAG_AUTO_ENROLLMENT -- 20 (32)
``CT_FLAG_MACHINE_TYPE -- 40 (64)
``CT_FLAG_IS_MODIFIED -- 20000 (131072)
``TemplatePropSecurityDescriptor = O:LAG:EAD:PAI(OA;;RPCR;0e10c968-78fb-11d2-90d4-00c04f79dc55;;RO)(OA;;RPCR;a05b8cc2
bc-4802-a710-e7c15ab866a2;;RO)(OA;;RPWPCR;0e10c968-78fb-11d2-90d4-00c04f79dc55;;DA)(OA;;RPWPCR;0e10c968-78fb-11d2-90d
0c04f79dc55;;DD)(OA;;RPWPCR;0e10c968-78fb-11d2-90d4-00c04f79dc55;;EA)(OA;;RPWPCR;a05b8cc2-17bc-4802-a710-e7c15ab866a2
D)(OA;;RPWPCR;0e10c968-78fb-11d2-90d4-00c04f79dc55;;ED)(OA;;RPWPCR;a05b8cc2-17bc-4802-a710-e7c15ab866a2;;ED)(A;;CCDCL
RPWPDTLOSDRCWDWO;;;DA)(A;;CCDCLCSWRPWPDTLOSDRCWDWO;;;EA)(A;;CCDCLCSWRPWPDTLOSDRCWDWO;;;LA)(A;;LCRPLORC;;;AU)
`` Allow Enroll CONTOSO\Enterprise Read-only Domain Controllers
``Allow ``Auto``-Enroll CONTOSO\Enterprise Read-only Domain Controllers
``Allow Enroll CONTOSO\Domain Admins
``Allow Enroll CONTOSO\Domain Controllers
``Allow Enroll CONTOSO\Enterprise Admins
``Allow ``Auto``-Enroll CONTOSO\Domain Controllers
``Allow Enroll NT AUTHORITY\ENTERPRISE DOMAIN CONTROLLERS
``Allow ``Auto``-Enroll NT AUTHORITY\ENTERPRISE DOMAIN CONTROLLERS
``Allow Full Control CONTOSO\Domain Admins
``Allow Full Control CONTOSO\Enterprise Admins
``Allow Full Control CONTOSO\Administrator
``Allow Read NT AUTHORITY\Authenticated Users
``TemplatePropExtensions =
4 Extensions:
``Extension[0]:
``1.3.6.1.4.1.311.21.7: Flags = 0, Length = 30
``Certificate Template Information
``Template=LDAPSSL(1.3.6.1.4.1.311.21.8.1546289.5796744.12012220.14775765.9035062.224.8004685.4056790)
``Major Version Number=100
``Minor Version Number=1
``Extension[1]:
``2.5.29.37: Flags = 0, Length = 2b
`` Enhanced Key Usage
``KDC Authentication (1.3.6.1.5.2.3.5)
``Smart Card Logon (1.3.6.1.4.1.311.20.2.2)
``Server Authentication (1.3.6.1.5.5.7.3.1)
``Client Authentication (1.3.6.1.5.5.7.3.2)
``Extension[2]:
``2.5.29.15: Flags = 1(Critical), Length = 4
``Key Usage
``Digital Signature, Key Encipherment (a0)
``Extension[3]:
``1.3.6.1.4.1.311.21.10: Flags = 0, Length = 33
``Application Policies
``[1]Application Certificate Policy:
``Policy Identifier=KDC Authentication
``[2]Application Certificate Policy:
``Policy Identifier=Smart Card Logon
``[3]Application Certificate Policy:
``Policy Identifier=Server Authentication
``[4]Application Certificate Policy:
``Policy Identifier=Client Authentication
`` TemplatePropValidityPeriod = 1 Years
``TemplatePropRenewalPeriod = 6 Weeks
CertUtil: -Template command completed successfully.
PS C:\
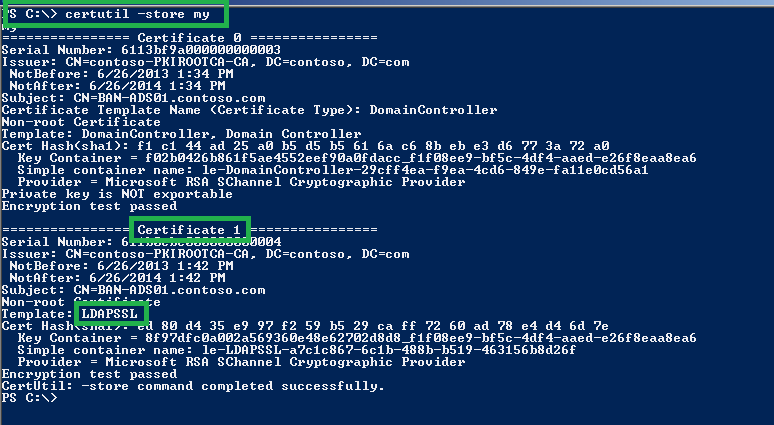
Find that Template from computer store using "certutil -store my". See the below snap.
Find the Template Details using "V" switch.
PS C:\> certutil -store -v my 1
my
================ Certificate 1 ================
X509 Certificate:
Version: 3
Serial Number: 611b0cbe000000000004
Signature Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.5 sha1RSA
Algorithm Parameters:
05 00
Issuer:
CN=contoso-PKIROOTCA-CA
DC=contoso
DC=com
NotBefore: 6/26/2013 1:42 PM
NotAfter: 6/26/2014 1:42 PM
Subject:
CN=BAN-ADS01.contoso.com
Public Key Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.1 RSA (RSA_SIGN)
Algorithm Parameters:
05 00
Public Key Length: 2048 bits
Public Key: UnusedBits = 0
0000 30 82 01 0a 02 82 01 01 00 d2 97 d0 1d 7d 8a 2a
0010 f9 1f ac 21 b2 ae 0b e7 b8 69 83 5c e5 d3 52 0c
0020 91 ed 6f cf c6 33 25 f2 b3 2a 47 da 66 2e 82 f9
0030 17 65 f8 ee 83 27 e6 64 9c 13 70 bb 2a 5e 6b 9c
0040 ed d6 a4 1a 1f de 7d 82 73 4b 98 38 ec 85 f0 f1
0050 fc ed 01 74 2b dc 93 19 e8 d1 21 c7 2c ff e4 8d
0060 03 67 f7 ce b6 01 e1 86 29 91 55 d1 0c d5 73 a6
0070 84 ad 78 5f c3 38 60 43 20 6b 72 25 42 90 df bf
0080 44 93 d8 09 f9 19 93 05 b3 98 8d b3 d6 a3 cd be
0090 86 1d d7 db 57 db 29 36 27 8f f6 84 d0 5b 1e f5
00a0 c1 01 fc d4 a6 6e 1e c7 77 ed 28 d5 98 3e 9f 45
00b0 99 fc 9c f7 dc 9d 05 70 dd 69 5f b1 83 26 a8 51
00c0 cd ae f5 f6 83 5b d7 67 bf 0b dc 89 1b 40 77 cc
00d0 df 87 99 83 77 a4 61 4d c9 78 ce be 75 bf b4 60
00e0 9b 39 1a 96 ff bf 98 9f c2 8d 89 1d 7c 28 33 09
00f0 33 e1 cc 8c f9 6e 83 10 d3 2c 42 99 57 d6 4d cf
0100 45 05 44 21 70 e1 ad c4 3d 02 03 01 00 01
Certificate Extensions: 9
1.3.6.1.4.1.311.21.7: Flags = 0, Length = 30
Certificate Template Information
Template=LDAPSSL(1.3.6.1.4.1.311.21.8.1546289.5796744.12012220.14775765.9035062.224.8004685.4056790)
Major Version Number=100
Minor Version Number=1
2.5.29.37: Flags = 0, Length = 2b
Enhanced Key Usage
KDC Authentication (1.3.6.1.5.2.3.5)
Smart Card Logon (1.3.6.1.4.1.311.20.2.2)
Server Authentication (1.3.6.1.5.5.7.3.1)
Client Authentication (1.3.6.1.5.5.7.3.2)
2.5.29.15: Flags = 1(Critical), Length = 4
Key Usage
Digital Signature, Key Encipherment (a0)
1.3.6.1.4.1.311.21.10: Flags = 0, Length = 33
Application Policies
[1]Application Certificate Policy:
Policy Identifier=KDC Authentication
[2]Application Certificate Policy:
Policy Identifier=Smart Card Logon
[3]Application Certificate Policy:
Policy Identifier=Server Authentication
[4]Application Certificate Policy:
Policy Identifier=Client Authentication
2.5.29.14: Flags = 0, Length = 16
Subject Key Identifier
ae 5f a1 12 09 ef c9 35 2c e7 31 89 38 e1 f9 2a c2 78 5e f4
2.5.29.35: Flags = 0, Length = 18
Authority Key Identifier
KeyID=36 e5 92 e8 53 3b 14 fe 23 ec 64 d3 22 49 0b eb cb a8 45 f6
2.5.29.31: Flags = 0, Length = cc
CRL Distribution Points
[1]CRL Distribution Point
Distribution Point Name:
Full Name:
URL=ldap:///CN=contoso-PKIROOTCA-CA,CN=PKIRootCA,CN=CDP,CN=Public%20Key%20Services,CN=Services,CN
=Configuration,DC=contoso,DC=com?certificateRevocationList?base?objectClass=cRLDistributionPoint
1.3.6.1.5.5.7.1.1: Flags = 0, Length = b9
Authority Information Access
[1]Authority Info Access
Access Method=Certification Authority Issuer (1.3.6.1.5.5.7.48.2)
Alternative Name:
URL=ldap:///CN=contoso-PKIROOTCA-CA,CN=AIA,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=
contoso,DC=com?cACertificate?base?objectClass=certificationAuthority
2.5.29.17: Flags = 0, Length = 57
Subject Alternative Name
Other Name:
Principal Name=BAN-ADS01$@contoso.com
DNS Name=BAN-ADS01.contoso.com
DNS Name=contoso.com
DNS Name=CONTOSO
Signature Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.5 sha1RSA
Algorithm Parameters:
05 00
Signature: UnusedBits=0
0000 b4 40 8b 4c f9 83 ae c0 68 8b 05 1f a2 37 f8 a1
0010 14 42 5b ae 2c 37 60 9b 3c 95 24 c4 ed 86 ee b5
0020 22 f7 e3 90 bd 74 e2 f9 0f 51 bd 72 f6 03 75 53
0030 fb dd 70 3f 5c 44 11 2b 3b f8 a4 f8 91 59 73 f4
0040 b2 bb 04 00 4d 80 34 be db 65 31 2a 96 f7 7f ef
0050 bf 1d 42 56 9d 98 b2 be f3 7d 21 47 fb 94 12 6f
0060 ee 42 89 64 a2 c1 38 a3 db 75 a5 02 48 e1 44 c5
0070 af d3 48 ba 33 ed 49 1c ec dd f2 35 83 8b c6 61
0080 db 24 bc fc 38 27 8c 0d d7 df e1 1a f7 dd c1 22
0090 aa 4e 4c b5 b5 ad f1 f7 b3 fe 6e e5 e2 e3 53 cf
00a0 2f 57 27 bf 8a c6 f5 87 b0 79 43 24 3b a3 35 db
00b0 0b 6a b2 9c d6 e4 e9 c3 77 85 e9 07 e4 2e 15 fc
00c0 2d 24 13 fa e9 7e f9 37 f2 96 10 41 f3 ae 26 e1
00d0 22 a3 1b 87 13 71 04 02 b3 f0 10 bb 36 3a a9 cb
00e0 f4 a8 9e dc 27 56 7a a1 2c 69 dc 61 e6 6f bc 8f
00f0 5a 67 f1 34 1c 9e c9 e2 9e f4 b9 54 3e 93 87 7f
Non-root Certificate
Key Id Hash(rfc-sha1): ae 5f a1 12 09 ef c9 35 2c e7 31 89 38 e1 f9 2a c2 78 5e f4
Key Id Hash(sha1): c7 c8 c4 4c 19 84 b8 11 45 03 6d 78 f0 0f 85 a3 61 a2 45 30
Cert Hash(md5): 46 78 5a 30 c8 67 58 33 d0 59 7b 8a 55 89 a2 ac
Cert Hash(sha1): ed 80 d4 35 e9 97 f2 59 b5 29 ca ff 72 60 ad 78 e4 d4 6d 7e
CERT_REQUEST_ORIGINATOR_PROP_ID(71):
BAN-ADS01.contoso.com
CERT_CEP_PROP_ID(87):
Enrollment Policy Url: ldap:
Enrollment Policy Id: {32376692-6063-4EDC-A375-572FED78C626}
Enrollment Server Url: PKIRootCA.contoso.com\contoso-PKIROOTCA-CA
Request Id: 4
Flags = 0
DefaultNone -- 0
Url Flags = 20 (32)
PsfAllowUnTrustedCA -- 20 (32)
Authentication = 2
Kerberos -- 2
Enrollment Server Authentication = 2
Kerberos -- 2
CERT_KEY_PROV_INFO_PROP_ID(2):
Key Container = 8f97dfc0a002a569360e48e62702d8d8_f1f08ee9-bf5c-4df4-aaed-e26f8eaa8ea6
Simple container name: le-LDAPSSL-a7c1c867-6c1b-488b-b519-463156b8d26f
Provider = Microsoft RSA SChannel Cryptographic Provider
ProviderType = c
Flags = 20
KeySpec = 1 -- AT_KEYEXCHANGE
CERT_ISSUER_PUBLIC_KEY_MD5_HASH_PROP_ID(24):
ac 47 4e aa 5d 0a 63 d4 0c 90 09 8f b8 09 b2 97
CERT_SUBJECT_PUBLIC_KEY_MD5_HASH_PROP_ID(25):
27 40 4a d2 6b 5f 0e a9 48 bc 24 00 91 1c c9 e9
CERT_KEY_IDENTIFIER_PROP_ID(20):
ae 5f a1 12 09 ef c9 35 2c e7 31 89 38 e1 f9 2a c2 78 5e f4
CERT_SIGNATURE_HASH_PROP_ID(15):
f2 2f 01 a4 6e 1d 2f 1b 96 a8 95 41 5e 2b d2 fc 80 5a 4c 21
CERT_MD5_HASH_PROP_ID(4):
46 78 5a 30 c8 67 58 33 d0 59 7b 8a 55 89 a2 ac
CERT_SHA1_HASH_PROP_ID(3):
ed 80 d4 35 e9 97 f2 59 b5 29 ca ff 72 60 ad 78 e4 d4 6d 7e
Simple container name: le-LDAPSSL-a7c1c867-6c1b-488b-b519-463156b8d26f
PP_KEYSTORAGE = 1
CRYPT_SEC_DESCR -- 1
KP_PERMISSIONS = 3f (63)
CRYPT_ENCRYPT -- 1
CRYPT_DECRYPT -- 2
CRYPT_EXPORT -- 4
CRYPT_READ -- 8
CRYPT_WRITE -- 10 (16)
CRYPT_MAC -- 20 (32)
D:PAI(A;;GAGR;;;SY)(A;;GAGR;;;BA)
Allow Full Control NT AUTHORITY\SYSTEM
Allow Full Control BUILTIN\Administrators
Private Key:
PRIVATEKEYBLOB
Version: 2
aiKeyAlg: 0xa400
CALG_RSA_KEYX
Algorithm Class: 0xa000(5) ALG_CLASS_KEY_EXCHANGE
Algorithm Type: 0x400(2) ALG_TYPE_RSA
Algorithm Sub-id: 0x0(0) ALG_SID_RSA_ANY
0000 52 53 41 32 RSA2
0000 ...
048c
Encryption test passed
CertUtil: -store command completed successfully.PS C:\>
Enabling/Disabling CryptoAPI 2.0
Enabling CryptoAPI 2.0 Diagnostic Logging
wevtutil sl microsoft-windows-capi2/operational /e:True
Disabling CryptoAPI 2.0 Diagnostic Logging
wevtutil sl microsoft-windows-capi2/operational /e:False
More details for Troubleshooting PKI Problems on Windows
Troubleshooting PKI Problems on Windows
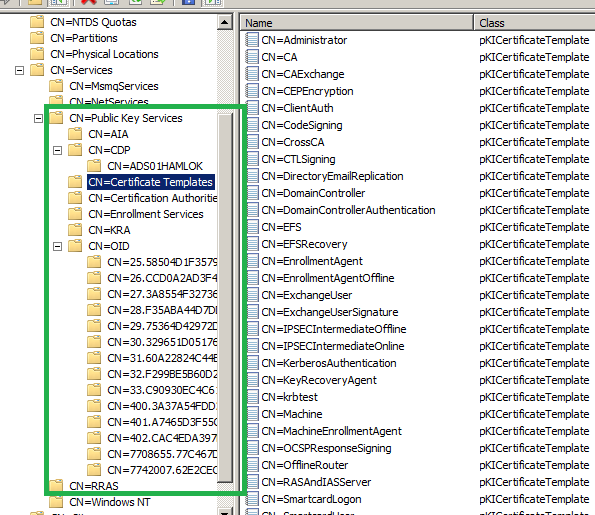
PKI Info; those are stored in AD ; See the following Snap.using ADSIEDIT.MSC
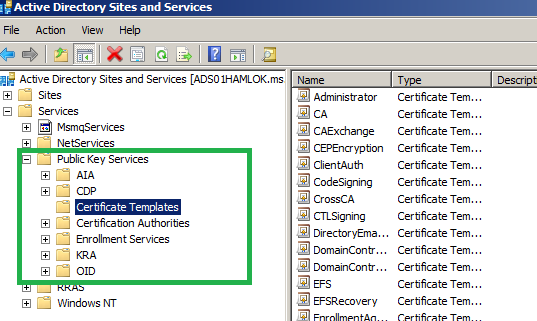
Also you can see the ADCS info using DSSITE.MSC
Some key Points.
- Cert Templates are stored in AD (Configuration Partition).
- Enterprise Certificate Server in a Domain controller is enabled LDAPS(636) & GC SSL(3269) ports for all the Domain controller)
- [Due to Certificate Template Domain Controller]
- If all Sub CAs host the same certificate templates for enrolment those servers we can use for Redundancy & fault tolerance.
- Also you can use Certificate server cluster for Redundancy & fault tolerance.
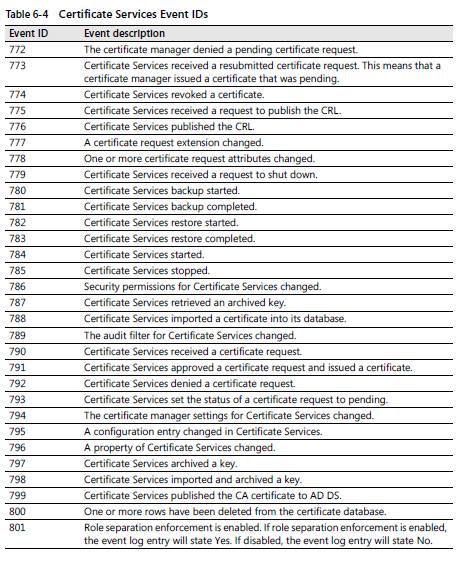
PKI Events.
(Snap is taken from Windows Server 2008 PKI - Brian Komar)
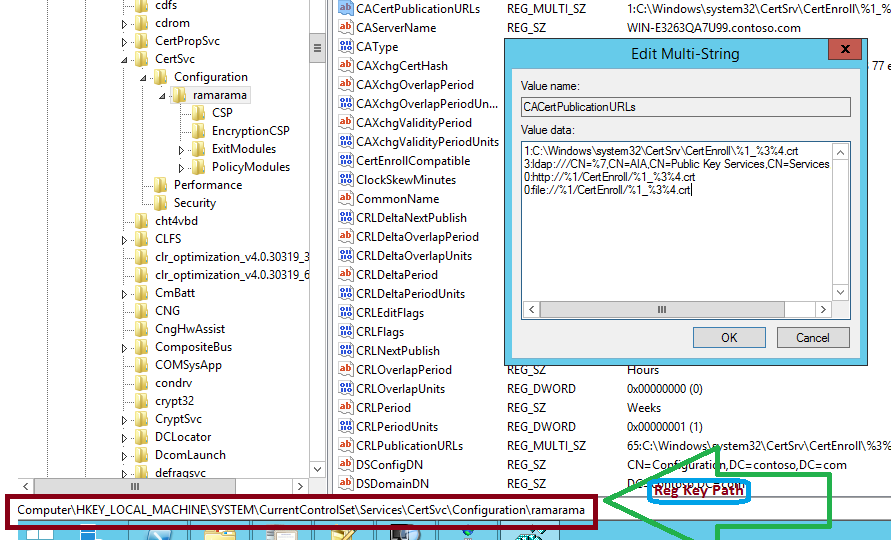
Certificate Server Registry Key (Path)
We are used "certutil -setreg" for changing those keys.
___________________________________________________
Some Useful Links
- How to enable LDAP signing in Windows Server 2008
- TroubleshootingLDAP Over SSL
- Reading LDAP SSL Network Traffic with NetMon 3.4 and NMDecrypt
- How to decrypt an SSL or TLS session by using Wireshark
- How to enable LDAP over SSL with a third-party certification authority
- Certutil Examples for Managing Active Directory Certificate Services (AD CS) from the Command Line
- Configure SSL/TLS on a Web site in the domain with an Enterprise CA
- What's New in AD CS and PKI?
- How to add a Subject Alternative Name to a secure LDAP certificate
- Custom Certificate Request in Windows Vista
- Step-by-Step Example Deployment of the PKI Certificates for Configuration Manager: Windows Server 2008 Certification Authority
- Publish certificates in a foreign Active Directory forest
- Exporting Certificates using CertUtil
- VPN Client Compatibility with Windows 7 and Windows Server 2008 R2
- Online Responder Installation, Configuration, and Troubleshooting Guide
- LDAP client tracing... using Tracelog
- HowTo: Determine if a user has logged on via smart card