Microsoft Reference Architecture for Private Cloud: Security Management and Monitoring
When you move from an on-premise environment to a cloud-based one, there must be a fundamental shift in how you think about provisioning and managing your IT services. Because of the increased involvement of third parties such as a CSP (cloud service provider), you have to address areas such as the shift in responsibilities, ownership of components, increased automation and standardization, integration with on-premise systems, effective operational security, comprehensive disaster recovery and delivery of these cloud-based IT services to your users.
The most effective way to address these changes is to use a recognised IT service lifecycle that connects service management principles to everyday IT tasks and activities, and ensures alignment between IT and your business. Although several frameworks exist that can support cloud-based migrations and operations, the foremost of these are the IT Infrastructure Library (ITIL) and Microsoft Operations Framework (MOF).
Note
This document is part of a collection of documents that comprise the Reference Architecture for Private Cloud document set. The Reference Architecture for Private Cloud documentation is a community collaboration project. Please feel free to edit this document to improve its quality. If you would like to be recognized for your work on improving this article, please include your name and any contact information you wish to share at the bottom of this page.
What Is ITIL?
ITIL offers a broad approach to the delivery of quality IT services. ITIL was initially developed in the 1980s and 1990s by CCTA (Central Computer and Telecommunications Agency, now the Office of Government Commerce, OGC), under contract to the UK Government. Since then, ITIL has provided not only a best practice based framework, but also an approach and philosophy shared by the people who work with it in practice.
ITIL Version 3 (2007 and 2011) approaches service management from the lifecycle of a service. The Service Lifecycle is an organization model providing insight into the way service management is structured, the way the various lifecycle components are linked to each other and to the entire lifecycle system.
The Service Lifecycle consists of five components. Each volume of the ITIL core books describes one of these components:
A key element of ITIL is that it is both vendor- and solution-agnostic—meaning, the practices encouraged by ITIL can be applied across the board regardless of the underlying technology. The result is that ITIL focuses on the management structure that makes IT successful, rather than on the technology.
What Is MOF?
First released in 1999, Microsoft Operations Framework (MOF) is Microsoft’s structured approach to helping its customers achieve operational excellence across the entire IT service lifecycle. MOF was originally created to give IT professionals the knowledge and processes required to align their work in managing Microsoft platforms cost-effectively and to achieve high reliability and security. The new version, MOF 4.0, was built to respond to the new challenges for IT: demonstrating the business value of IT, responding to regulatory requirements and improving organizational capability. It also integrates best practices from Microsoft Solutions Framework.
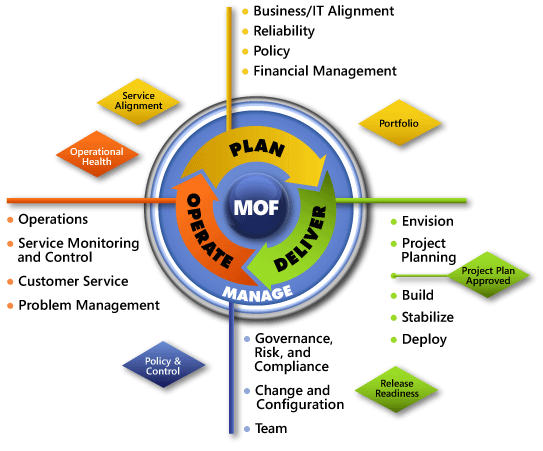
Figure 11: Microsoft Operations Framework
MOF consists of a service management lifecycle with three phases and one layer:
This structure comes about because management is something that applies to all phases.
Within that lifecycle are service management functions (SMFs) that relate to those phases. The items in the diamond shapes are management reviews, which focus on key management control points.
With the adoption of cloud-based services, you are looking to provide the following:
- Reduced IT service costs
- Improved business agility
MOF can help you achieve these goals by providing a structured framework and process for migrating from your current on-premise environment to the cloud while minimizing risks.
Although all the MOF SMFs apply to cloud migrations to some extent, ones that are particularly appropriate to cloud security are:
- Policy SMF – this SMF covers security, privacy and acceptable use policies.
- Team SMF – this SMF helps identify and define roles and responsibilities within the joint team of cloud vendor and your own personnel
- Governance, Risk and Compliance SMF – this SMF enables you to create an IT Services risk characterization report, which details possible threats and vulnerabilities to your organization’s data and helps you prioritize the risks and create the necessary controls to counterbalance those risks.
Monitoring and Reporting
Monitoring and reporting in cloud-based systems is even more important than with on-premise environments, as you will not have the same level of access to the operating system or the underlying hardware. Hence, you must plan your monitoring and reporting strategy much more carefully and consider closely what monitoring information you need from your CSP and to whom will this information be disseminated within the CSP's environment. It is important to note that because of the increased need of organizations to measure the cost and monitor the effectiveness of cloud-based environments, a CSP provides many facilities for reporting and monitoring.
Cloud early adopters such as Microsoft report that if you do move to a cloud-based environment, then the fact that you do not have such close access to the underlying environment can result in an unexpected benefit. Assuming that you are provided and implement an effective monitoring and reporting configuration, the unexpected benefit is the fact that reports about performance, costs, transactions and the like become much easier to access. Rather than waiting for a manager to report to you, you can use a CSP provided dashboard to extract data directly from the cloud environment.
Factors that you may need to consider when creating an effective monitoring plan for a cloud-based environment include:
- What information does your organization require to support effective business decisions?
- Why do you need that information?
- Where can you get that information from in a cloud-based environment?
- What mechanism can you implement to extract this information?
- Who requires access to that information (and who should not get access to it)?
- How should that information be displayed?
MOF helps you to create a structured monitoring plan through the Service Monitoring and Control SMF.
Let's look at an example of how this strategy might be implemented with a SaaS payment processing system. A company needs to know information such as:
- What is the cumulative value of all transactions to date?
- What is the current transaction value rate?
- What is the current and cumulative profit from the service?
- How much is the company being charged for the cloud hosting?
- What is the rate of return on investment when accounting for income and costs?
- How long are transactions taking on average?
- How many transaction failures have there been and what was the cause?
Note that information such as processor loadings, memory usage, data storage and network card statistics are no longer required, as these areas are all handled by the cloud service provider.
Using MOF guidance, developers can implement comprehensive application instrumentation that enable end-to-end transaction monitoring. By tying in to the existing monitoring facilities that a cloud provider can offer, a company can create a dynamic dashboard that displays different default data according to which logged-on user views the information. The result is that the organization now has enhanced visibility of its business processes and can deliver real-time monitoring information from its cloud-based environment straight to the right level of management.
REFERENCES:
Microsoft Operations Framework 4.0
The Official ITIL Site
ACKNOWLEDGEMENTS LIST:
If you edit this page and would like acknowledgement of your participation in the v1 version of this document set, please include your name below:
[Enter your name here and include any contact information you would like to share]