SubInACL: A complete solution to configure security permission
Introduction
Managing security permission in a Windows environment is a challenging task.
The task becomes more complex if any / all of the below scenarios are true:
- There are large folders with size in TBs or GBs, along with numerous sub-folders with a deep folder hierarchy.
- Permission inheritance is disabled in many subfolders and exclusive permissions are defined on those subfolders.
- The owners of many subfolders have been changed and our account is removed from ACL, so we are not able to see the existing ACL. We are also not able to see that subfolder size (Might be in TBs ! )
- There are a few thousand users, who are using those folders.
In this scenario, the first thing to remember is: We will NOT try to change the ACL of the parent folder (or any big subfolder) through GUI. Things will go worse if we try to do so in a complex folder structure, and there will be a huge impact. We have faced this scenario in production for a big folder, and it took 1 week to restore the permission and resolve the issue! For this kind of scenario, we should always go for a command line utility rather than GUI.
Also, we should enable logging; so that we can refer the log file and know what ACEs got changed. The log file would help us to troubleshoot and mitigate any possible issue.
Note
SubInACL is a little-known command line tool from Microsoft, yet it is one of the best tools to work with security permissions in Windows. This tool is capable of changing permissions of files, folders, registry keys, services, printers, cluster shares and various other types of objects.
Some of the notable advantages of SubInACL are:
- If used properly, it does not tamper any existing permission.
- Can change permission/ owner to those subfolders where inheritance is disabled.
- Can change permission even if we do not have access to a folder/subfolder.
- **Output log and error log can be enabled. **
Installation
SubInACL is not an inbuilt windows tool, we need to download it from the Microsoft website. It is a free tool from Microsoft.
Installation is simple, and in our lab, we have installed it in “C:\SubInACL” folder.
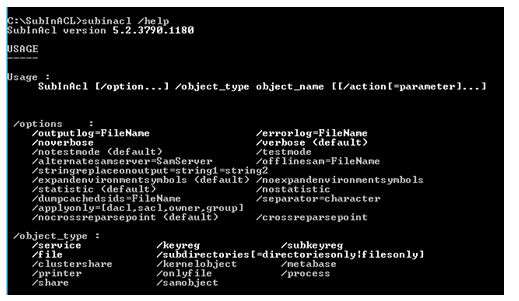
Once we go to that directory and run “subinacl /help”, it should display command syntax and arguments. This ensures that installation is successful.
Understanding the Syntax
SubInACL is not difficult to use. However, we strongly recommend testing it before executing it in production.
If we see the help menu of the command, we will notice there are three major sections in this command:
SubInAcl <options> <object_type> <action>
• <options> : This is an optional parameter. Here we can enable different kind of logging and verbose mode.
• <object_type> : This is a mandatory parameter. As mentioned before, SubInAcl can change ACL of folder, file, registry key, service, process etc. Here we are specifying the object type.
** /file:** Stands for a single folder or file. We generally use it to specify the parent folder.
**/subdirectories **: Stands for subfolders. When applied with <Parent_foldername>\.*, it stands for all subfolders and files within the parent folder.
/service : Stands for a Windows Service
**/keyreg : **Stands for a Registry Key
**• <action> : **This is a mandatory parameter. This defines the required action on the specified object.
Ex: /setowner= domain/user1 : Will set the owner to user1.
Similarly, there are other actions like Grant, Revoke, Deny etc.
The type of action depends upon the type of object which we have specified before. Not all actions are valid for all object type.
Case Studies
Now that we have the basic understanding of the SubInACL tool, we will do some hands-on and will configure permission based on multiple scenarios.
Scenario 1 : Change owner of Folder, Subfolders, and Files
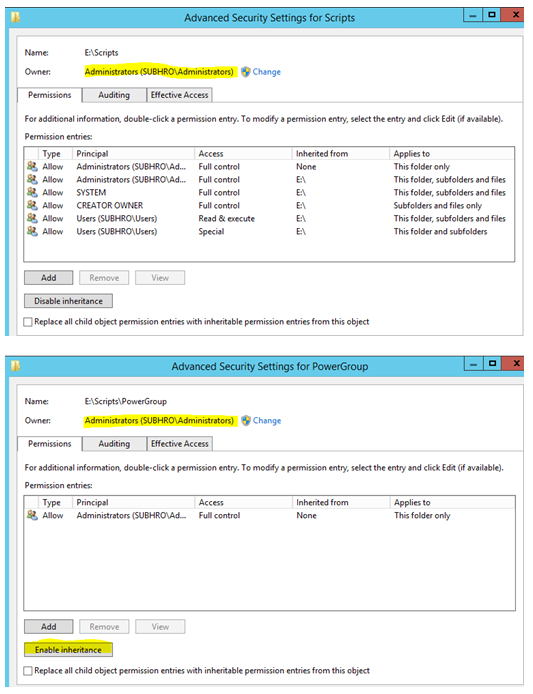
We have created a folder “E:\scripts”, which contains other subfolders and files.
Permission inheritance is disabled for one of the subfolder “PowerGroup”. For other subfolders , permission inheritance is enabled.
At present, the owner of the scripts folder (and all subfolders) is “subhro\administrator”.
We will change the owner to the AD group ‘AWSAdmins”, for the parent folder as well as for all subfolders. It should also change the owner of the subfolder PowerGroup, where inheritance is disabled.
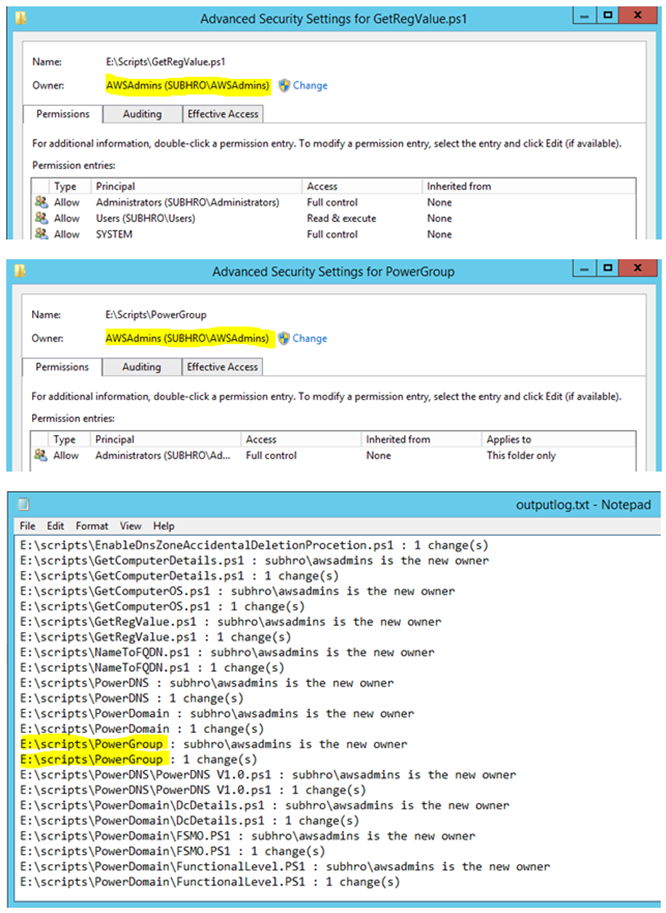
So we will execute below command first, which will change the owner to “subhro/awsadmins” on the folder “E:\scripts”. It will also create output and error log files at the specified location.
subinacl /errorlog="c:\temp\errorlog.txt" /outputlog="c:\temp\outputlog.txt" /file "E:\scripts" /setowner=subhro\awsadmins
Please note, that above command has not changed the owner of subfolders and files, it has only changed the owner of the parent folder “E:\Scripts”.
Now, we want to set the owner to subfolders of “E:\Scripts”. To do that, we need to execute below command:
subinacl /errorlog="c:\temp\errorlog.txt" /outputlog="c:\temp\outputlog.txt" /subdirectories "E:\scripts\*.*" /setowner=subhro\awsadmins
This command will change the owner of all subfolders and files within “E:\scripts”, including the folder “PowerGroup” where permission inheritance is blocked.
Scenario 2 : Add permission of Folder, Subfolders, and Files
Now we are going to add an ACE (Access Control Entry) in the ACL (Access Control List) of the folder “E:\Scripts”, and all its subfolders.
We will grant Full Control to the group “subhro\AwsAdmins”. We will execute below two commands one by one:
subinacl /errorlog="c:\temp\errorlog.txt" /outputlog="c:\temp\outputlog.txt" /file "E:\scripts" /grant=subhro\awsadmins=F
subinacl /errorlog="c:\temp\errorlog.txt" /outputlog="c:\temp\outputlog.txt" /subdirectories "E:\scripts\*.*" /grant=subhro\awsadmins=F
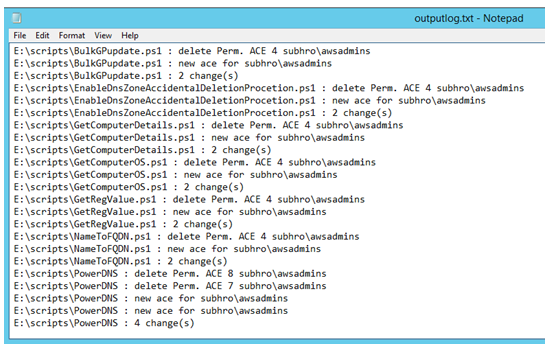
As we can see, it has changed ACL for the parent folders, subfolders, and files; including the subfolder where inheritance is disabled.
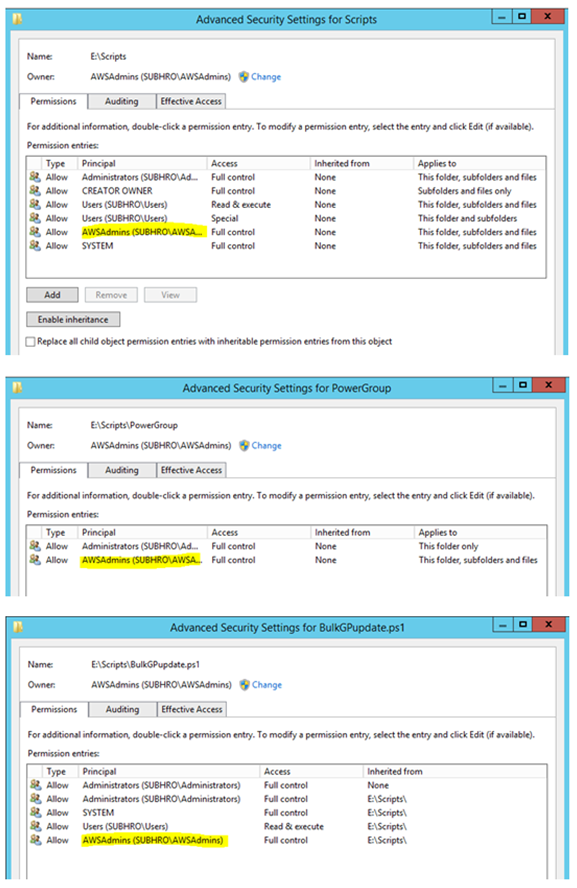
Scenario 3 : Change existing permission of Folder, Subfolders, and Files
If the previous example, we have granted the group “subhro\AwsAdmins” full control access on the folder “E:\Scripts”, including subfolders and files.
Now, if we want to change the permission from “Full Control” to “Modify”, what should we do?
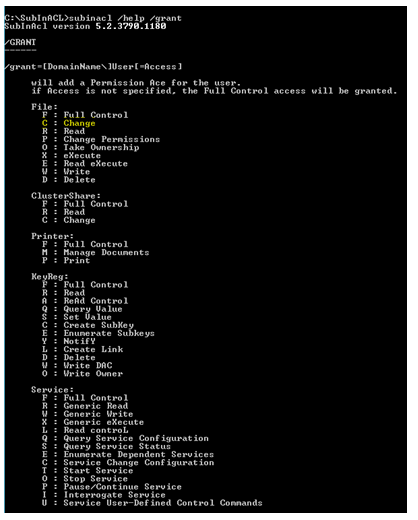
First, let’s run a command subinacl /grant /help. This is a useful command, which lists all permission options for action “Grant”, for each type of object.
Using this command, we can see that the syntax for “Modify” option is “C”.
So we will execute below two commands:
subinacl /errorlog="c:\temp\errorlog.txt" /outputlog="c:\temp\outputlog.txt" /file "E:\scripts" /grant=subhro\awsadmins=C
subinacl /errorlog="c:\temp\errorlog.txt" /outputlog="c:\temp\outputlog.txt" /subdirectories "E:\scripts\*.*" /grant=subhro\awsadmins=C
As we can see, now the permission “Full Control” has been changed to “Modify” for parent folder and all subfolders.

If we examine the log file carefully, we will notice that the command has actually deleted the old permission and then added new permission.
Scenario 4 : Completely remove an existing ACE from an ACL
Now, there is a requirement to remove the entry “subhro\AWSAdmins” from the permission list of “E:\Scripts”, including all its subfolders and files.
So, instead of the “/grant” switch, we need to use “/revoke” switch here.
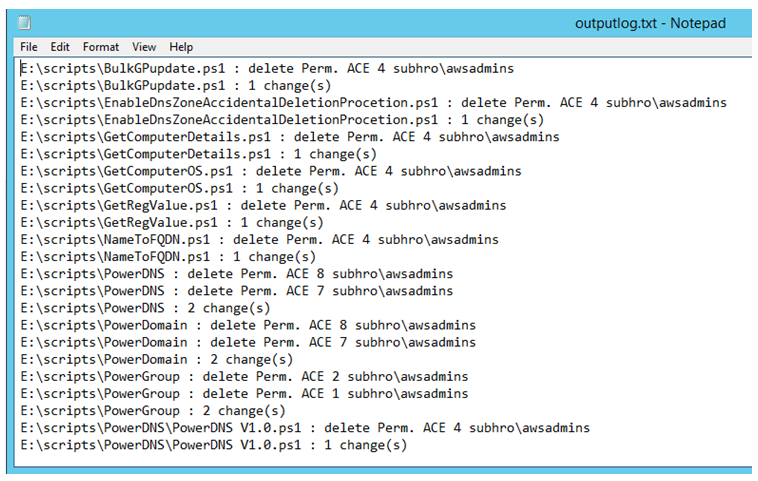
subinacl /errorlog="c:\temp\errorlog.txt" /outputlog="c:\temp\outputlog.txt" /file "E:\scripts" /revoke=subhro\awsadmins
subinacl /errorlog="c:\temp\errorlog.txt" /outputlog="c:\temp\outputlog.txt" /subdirectories "E:\scripts\*.*" /revoke=subhro\awsadmins
This would revoke the ACE of “subhro\awsadmins” from the permission list.
Scenario 5 : Set Windows Service Permission
So far, we have changed owner and configured permissions on files and folders. Although file and folder permission is the most common scenario, there are various other scenarios where the SubInACL utility can be used.
Sometimes, we need to control who can (or cannot) start or stop specific services. In this example, we are going to configure that.
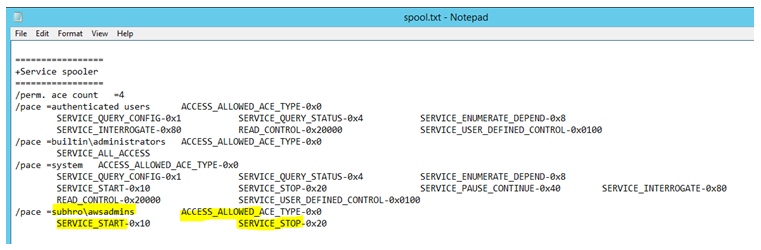
First, we will check the current ACL of the “spooler” service using the below command:
subinacl /service "spooler" /display=dacl > c:\spool.txt
(We have redirected the output to a text file so that it would be easy to read the output).
Here is the result:
Now, we are going to add “subhro\awsadmins” group to this ACL, and this group member should be able to start and stop this service.
So we will execute below command:
subinacl /errorlog="c:\temp\errorlog.txt" /outputlog="c:\temp\outputlog.txt" /service "spooler" /GRANT=subhro\awsadmins=TO
Here, T= Start Service and O=Stop Service. Please use subinacl /grant /help for the complete list.
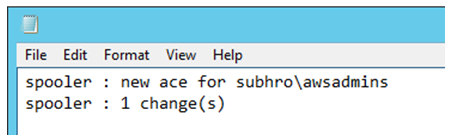
From the output log, we can see that ACL has been updated with the new ACE.
Now, if we see the ACL once again, we will find that the new ACE has been added with “Start Service” and “Stop Service” access.
If our requirement is to “deny” this group to start and stop the spooler services, then we will run below command:
subinacl /errorlog="c:\temp\errorlog.txt" /outputlog="c:\temp\outputlog.txt" /service "spooler" /deny=subhro\awsadmins=TO
We can see the ACL and verify that it has been updated with the “deny” option.
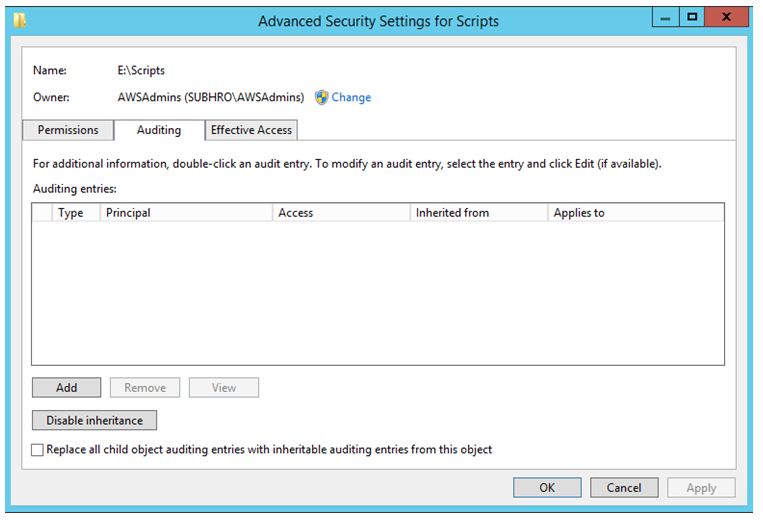
Scenario 6 : Configure Audit Permission on Folders and Files
This is another common requirement, to enable “Success” or “Failure” audit on a folder, including all subfolders and files.
We are now going to enable success and failure auditing on the folder “E\scripts” (with all subfolders) for the group “subhro\awsadmins”.
As we can see, at present no auditing is enabled for this folder.
We will execute below commands:
subinacl /errorlog="c:\temp\errorlog.txt" /outputlog="c:\temp\outputlog.txt" /file E:\scripts /sallowdeny=subhro\awsadmins=F
subinacl /errorlog="c:\temp\errorlog.txt" /outputlog="c:\temp\outputlog.txt" /subdirectories "E:\scripts\*.*" /sallowdeny=subhro\awsadmins=F
As we can see, the Auditing ACL has been updated.
Please remember below four switches in this context:
- /salllowdeny will remove all existing ACEs from the Auditing tab, and add an ACE for both Success and Failure events for the mentioned user/group.
- /sgrant will remove all existing ACEs from the Auditing tab, and add an ACE for only “Success” events for the mentioned user/group.
- /sdeny will remove all existing ACEs from the Auditing tab, and add an ACE for only “Failure” events for the mentioned user/group.
- /audit will remove all existing ACEs from the Auditing tab.
Summary
In this article, we have covered the utility SubInAcl and multiple usage scenarios. There are many other options available in this utility, which can be useful in various scenarios. We will add those scenarios and options in the forthcoming versions of this article.
As mentioned before, please do not forget to test each command before using in production.