Azure Networking: Private links
Introduction
In this post, we will see a new Azure service called Azure Private Link this service, comes to be added to all the others offered by Microsoft to us to have a secure endpoint. Before Azure Private Link service appears in the Azure Portal there was another one called Azure Private Endpoint service and below we will also read about the differences between them and which of them feets better to our scenarios.
Private Link Key Benefits
Azure Private Link service offers some beneficial features, these are:
- Secure access to Azure PaaS services via a Private IP
- Access Azure PaaS services from on-premises over VPN, Express Route, and peered VNet's using private endpoints.
- Ability to communicate private services between different regions.
- Enable Azure Private Link service for custom services, by placing this service behind an Azure Load Balancer.
- Data are protected from leakage risks because the private endpoint is mapped to a specific resource (e.g. Azure storage blob but not a table, files, and queue) keeping all the other resources blocked.
The availability
The table below informs us about the supported services, the availability per region, and the status of the service.
| Scenario | Supported services | Available regions | Status |
Private Link for customer-owned services |
Private Link service behind standard Azure Load Balancer |
All public regions |
GA |
Private Link for Azure PaaS services Private Link for Azure PaaS services |
Azure Storage, Azure Data Lake Storage Gen2, Azure SQL Database, Azure Synapse Analytics, Azure Cosmos DB, Azure Database for PostgreSQL(Single Server), Azure Database for MySQL, Azure Database for MariaDB, Azure Key Vault, Azure Kubernetes |
All public regions |
GA |
| Azure Container Registry, Azure App Configuration, Azure Event Hub, Azure Service Bus, Azure Relay | All public regions |
GA |
|
| Azure Search, Azure Backup, Azure Event Grid, Azure Web Apps, Azure Machine Learning | East US, West US 2, South Central US | Preview |
Azure Private Link vs Azure Service Endpoint
At the table below we can read what are the differences between Azure Private Link vs Azure Service Endpoint services.
| Azure Private Link | Azure Service Endpoint |
| Access to the Azure PaaS service over private IP | Access to the Azure PaaS service over public IP |
| On-premises traffic can be achieved via VPN tunnel or Express route | On-premises traffic restriction is not easily |
| Data exfiltration protection is built-in | Data exfiltration protection is available via firewall |
| VNet to PaaS resource available via MS backbone | VNet to PaaS resource available via MS backbone |
| There is no need to configure NSG | Need to configure NSG |
Let's create an Azure Private Link
The steps below explain how we can create an Azure Private Link service and how we can test to check if it works.
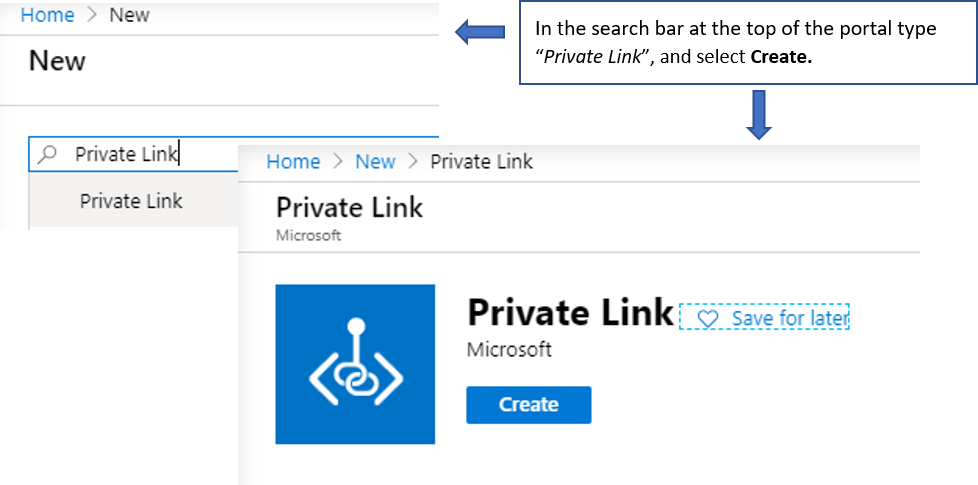
Step 1. Search & Create the Private Link service
In the Azure portal search bar at the top, type "Private Link", and then select the Create button.
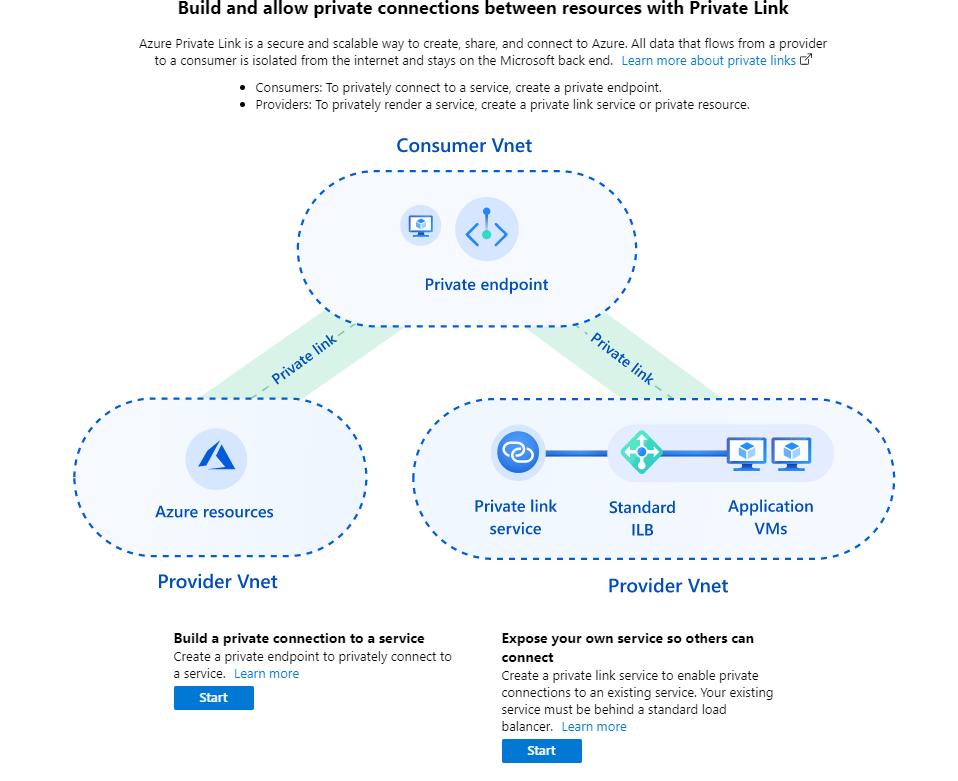
Select Start [Build a private connection to a service].
Step 2. Configuration of the service
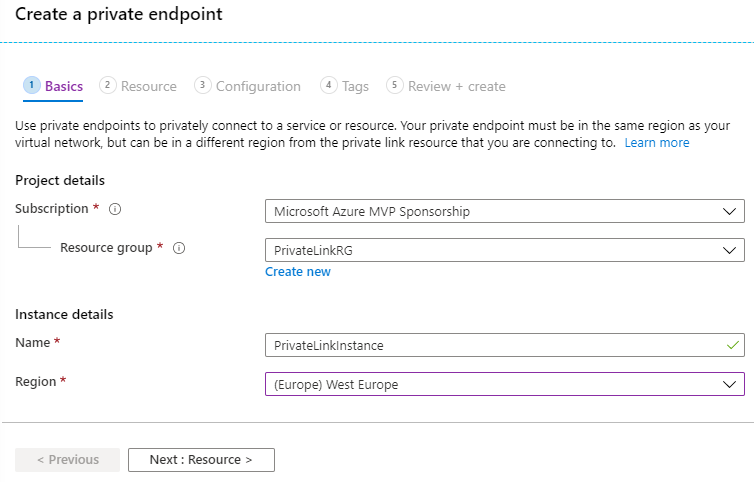
01 - Tab [Basics]
At the [Basics] tab, we select a valid Azure Subscription, create or select an existing Resource group, type a valid Name for the service, select a Region and click the button Next: Resource >
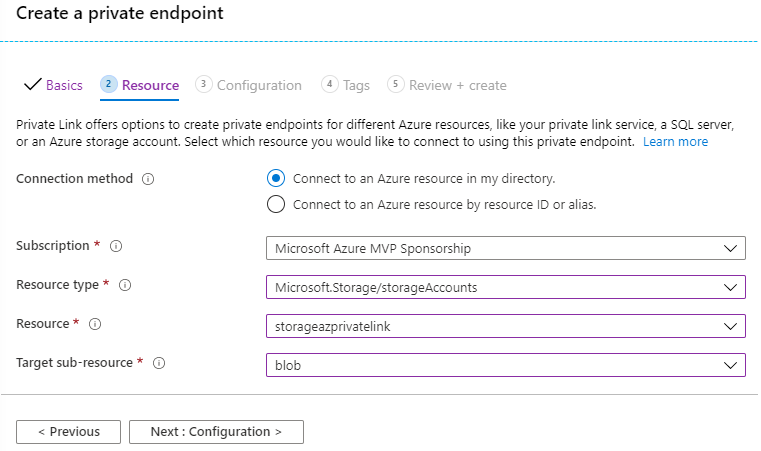
02 -Tab [Resource]
At the second tab [Resource] we have to select the Resource type e.g storage Account and then we must define the Resource and the sub-resource where the private endpoint will allow access. When we complete the selections we can proceed with the wizard by selecting Next: Configuration >
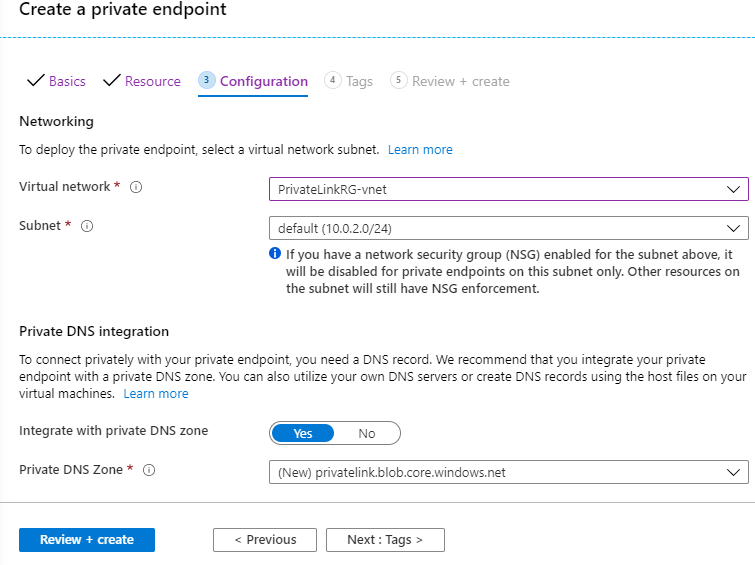
03 - Tab [Configuration]
The next tab [Configuration] is about the Network configuration, at this step, we must select the Virtual network and the subnet where the endpoint will be deployed.
At this point, it would help a lot to say that it is recommended to integrate the private endpoint with a private DNS zone, in a case we have a custom DNS server then we need to add this record to the Windows VM host file.
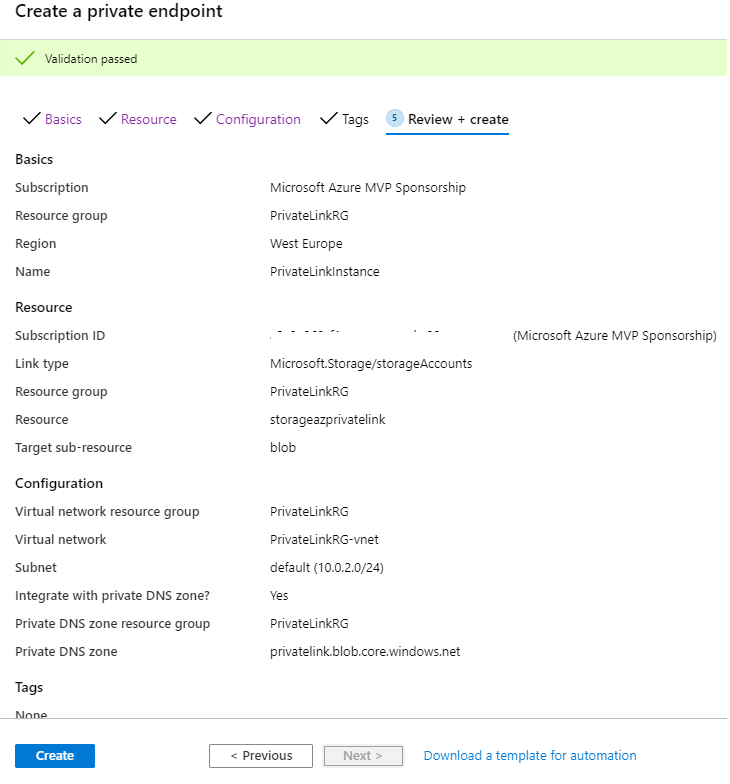
05 - Tab [Review + create]
And at the final tab [Review + create] we just check if the validation of the deployment is passed and then click the button Create.
Step 3. Test the Private Link
On the private endpoint Overview page, we can see the FQDN for the private link with the private IP
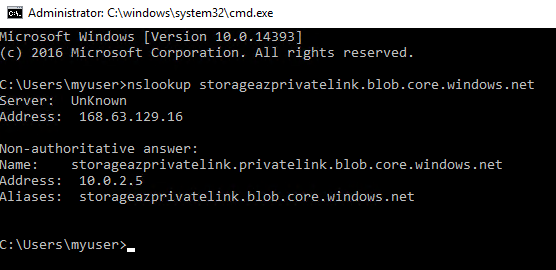
Let's make a quick test using the nslookup command to confirm that the private links address is this private IP.
From the VM we execute the nslookup command, and from the output, we can understand that the private link storageazprivatelink.blob.core.windows.net DNS name is registered with the private IP 10.0.2.5.
Something to keep in mind
Moving storage resource containing private endpoints is not supported.
See Also
General Information
How To
- Connect privately to a storage account
- Connect privately to an Azure Cosmos account
- Connect privately to a Web App using Azure Private Endpoint (Preview)
- Disable network policies for private endpoints
- Disable network policies for Private Link service source IP
- Manage a Private Endpoint connection