Defining the Private Cloud Security Problem Domain
As previous sections in this document outline, security is a universal component of cloud service provisioning. To help consider this requirement logically, this series considers the key security differences in private cloud environments, which result from the unique features of a cloud-based service.
Note:
This document is part of a collection of documents that comprise the Reference Architecture for Private Cloud document set. The Solution for Private Cloud is a community collaboration project. Please feel free to edit this document to improve the quality of this document. If you would like to be recognized for your work on improving this document, please include your name and any contact information you wish to share at the bottom of this page
Key Security Differences in Private Cloud Environments
As mentioned earlier in this paper, cloud security enhances and refines rather than replaces current models for IT security design and operation. However, there are certain areas where there are some noticeable changes, starting with the area of responsibility.
Security Responsibility
In a traditional data center environment, the demarcation of security responsibilities between the data center operator and the service user was relatively well defined. Generally, the responsibility was aligned with ownership of the physical component, whether that was a server, a networking device or the overall network infrastructure; if the IT department owned and administered the server, then that department also managed and updated security on that asset.
With cloud models, security responsibility has altered, in that departments may be responsible for a portion of the security on the service that they pay for, depending on the service provisioning model in use. Figure 4 shows the split of security responsibility for the three main cloud provision models.
Figure 1. Division of security responsibility for private cloud service models
Security Attack Targets
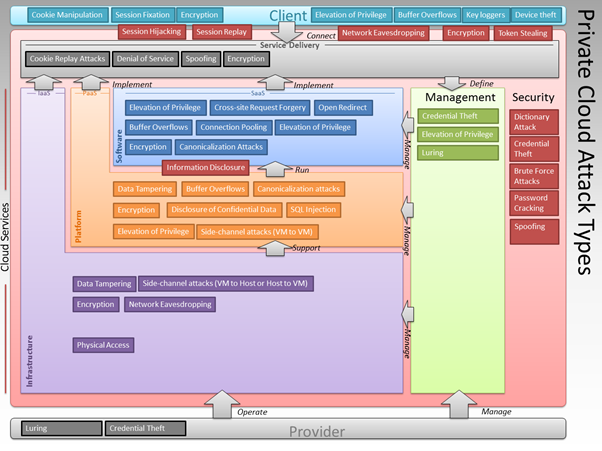
Taking the private cloud reference model as the basis for analysis, you can identify threats to the private cloud infrastructure and place these threats into appropriate places within the model. This approach provides a basis for threat modeling and risk analysis.
Hence, you can classify attacks according to the layer or stack that the attack targets. Figure 5 highlights the primary areas in the private cloud where these individual attack types can target. Note that this diagram is not showing responsibilities but listing the different types of attacks that might take place against the management stack, the infrastructure layer and so on.
You should also note that some of these areas may be out of control of the private cloud provider, such as client security. A later section discusses the implications of changes to the client security relationship.
Figure 2: Security Threats to Private Cloud Architectures
Note: This figure only summarizes the threats that may exist at the different levels of the cloud architecture. For an explanation of each of these threats and applicable countermeasures, see Cloud Security Threats and Countermeasures at a Glance, at http://blogs.msdn.com/b/jmeier/archive/2010/07/08/cloud-security-threats-and-countermeasures-at-a-glance.aspx.
Shared Tenant Model
A key differentiator with public cloud environments is that the service is provided on a shared tenant basis and multiple tenants use the same services. The public cloud implementation then applies authentication, authorization, and access controls to create logical partitions between the tenants so that individual tenants are isolated from each other and cannot see other tenants’ data.
Note: In private cloud terminology, a tenant is a client, typically a business unit within the organization, who is using the private cloud to run their applications and services.
The perception of a private cloud is that it is only hosting one organization, and in consequence, security partitioning is not required. In reality, organizations may have good reasons to want to implement such partitioning, such as between different business groups or between the finance department and the rest of the organization. In consequence, a private cloud model may also be a shared tenant model with similar requirements for effective security partitioning between different business units as with public cloud implementations.
Virtualization
Virtualization is not an absolutely essential component of private cloud architectures, as organizations can use blade server arrays or other compute-dense configurations to provide cloud-based services. However, the advantages of improved server utilization and greater operational flexibility that virtualization platforms provide have led to very high uptake of this technology in both cloud environments and in the predecessor architecture to the cloud, the dynamic data center.
Virtualization radically changes the way an organization secures and manages their data center. Because workloads are mobile and can move from host to host based on optimization algorithms that require no human involvement, security policies linked to physical location are no longer effective, so security policies must be independent of network or hardware topologies.
Although estimates of data center server virtualization indicate that this technology has reached adoption levels of over 50%, management and security tools for virtualized environments are still catching up with the physical systems that they replace. The presence of the new hypervisor layer provides additional attack vectors and new opportunities for security breaches.
One example of the new attack vectors occurs when virtual machines running on the same physical host typically use virtual networking components to communicate between these guest operating systems. In consequence, virtual machines can be communicating with each other without those communications being picked up by monitoring tools on the physical network. IT staff must be able to identify when inter-virtual machine traffic is occurring and apply policies and monitoring to that traffic.
A key factor for implementing effective security in virtualized environments will be virtualization of the security controls themselves. As these virtualized controls become available, they should as a minimum meet the following criteria:
- Fully integrate with the private cloud fabric
- Provide separate configuration interfaces
- Provide programmable, on-demand services in an elastic manner
- Consist of policies that govern logical attributes, rather than policies that are tied to physical instances
- Enable the creation of trust zones that can separate multiple tenants in a dynamic environment
In summary, security in private cloud environment must be adaptive and natively implemented into a fabric where resources are allocated dynamically. Any security functionality that is tied to a server, an internet protocol (IP) address, a media access control (MAC) address, port, or other physical instance will no longer be as effective as in purely physical environments.
Resources
- Return to Blueprint for A Solution for Private Cloud Security
- Return to A Solution for Private Cloud Security
- Return to Reference Architecture for Private Cloud
- Move forward to Cloud Security Challenges
- Table of Contents for A Solution for Private Cloud Security
** **
Acknowledgements list
If you edit this page and would like acknowledgement of your participation in the v1 version of this document set, please include your name below:
[Enter your name here and include any contact information you would like to share]
- ...