Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Important
Effective May 1, 2025, Azure AD B2C will no longer be available to purchase for new customers. Learn more in our FAQ.
In this article, we describe the scenarios for funnel-based design approach. Before starting to design, it's recommended that you review the capabilities, and performance of both funnel and region-based design approach. This article will further help determine which design may fit best for your organization.
The designs account for:
- Local Account sign up and sign in
- Federated account sign up and sign in
- Authenticating local accounts for users signing in from outside their registered region, supported by cross tenant API based authentication
- Authenticating federated accounts for users signing in from outside their registered region, supported by cross tenant API based look up
- Prevents sign up from multiple different regions
- Applications in each region have a single endpoint to connect with
Local account sign-in use cases
The following use cases are typical in a global Azure AD B2C environment. The local account use cases also cover accounts where the user travels. We provide a diagram and workflow steps for each use case.
Local user sign-up
This use case demonstrates how a user from their home country/region performs a sign-up with an Azure AD B2C Local Account.
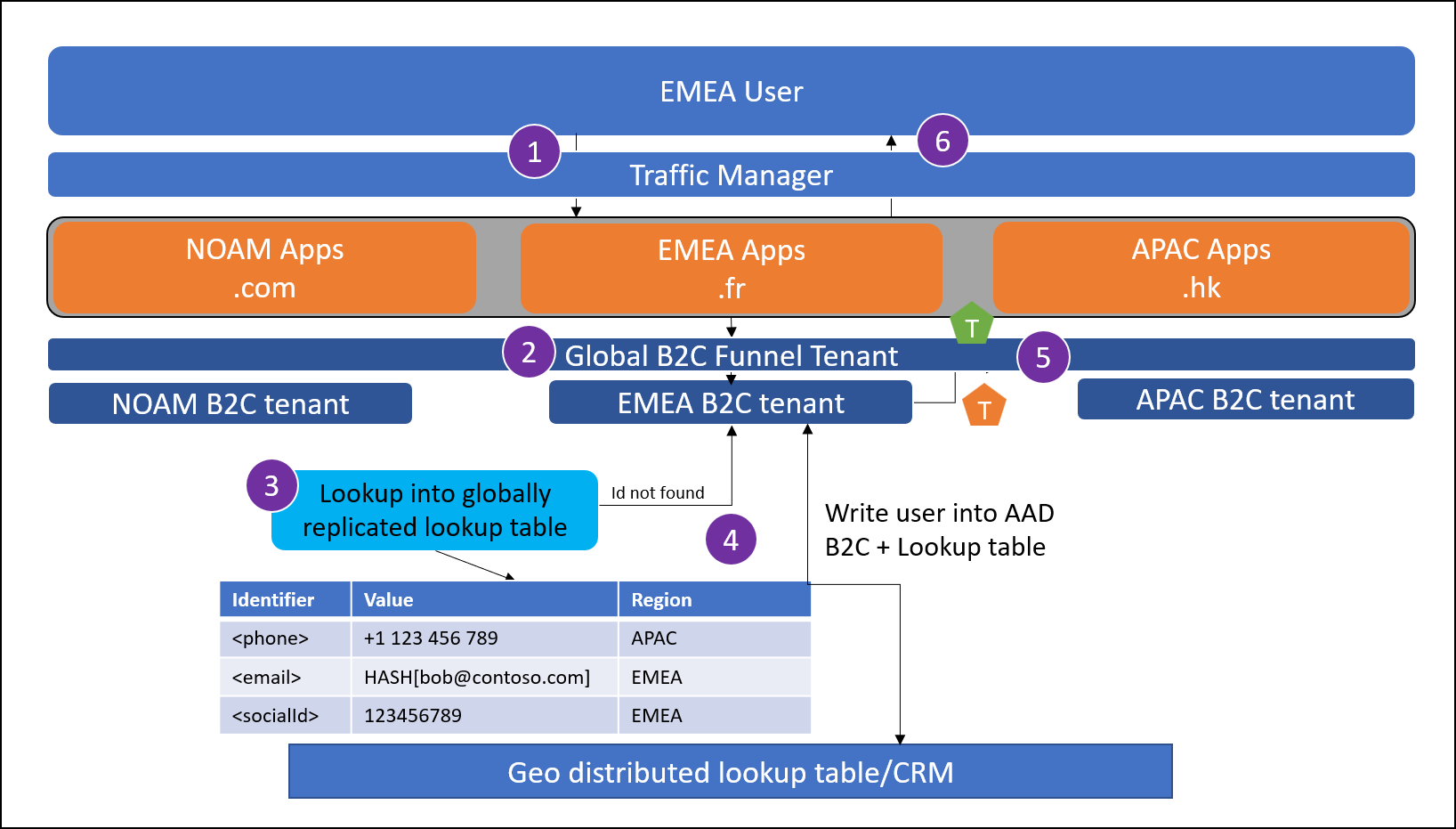
A user from Europe, Middle East, and Africa (EMEA) attempts to sign up at myapp.fr. If the user isn't being sent to their local application instance, the traffic manager enforces a redirect.
The user reaches the Global Funnel Azure AD B2C tenant. This tenant is configured to redirect to a regional Azure AD B2C tenant based on defined criteria using OpenId federation. This can be a lookup based on Application clientId.
The user attempts to sign up. The sign-up process checks the global lookup table to determine if the user exists in any of the regional Azure AD B2C tenants.
The user isn't found in the global lookup table. The user's account is written into Azure AD B2C, and a record is created into the global lookup table to track the region in which the user signed-up.
The regional tenant issues a token back to the funnel tenant.
The funnel tenant issues a token to the application.
Existing local user attempts sign up
This use case demonstrates how a user re-registering the same email from their own country/region, or a different region, is blocked.
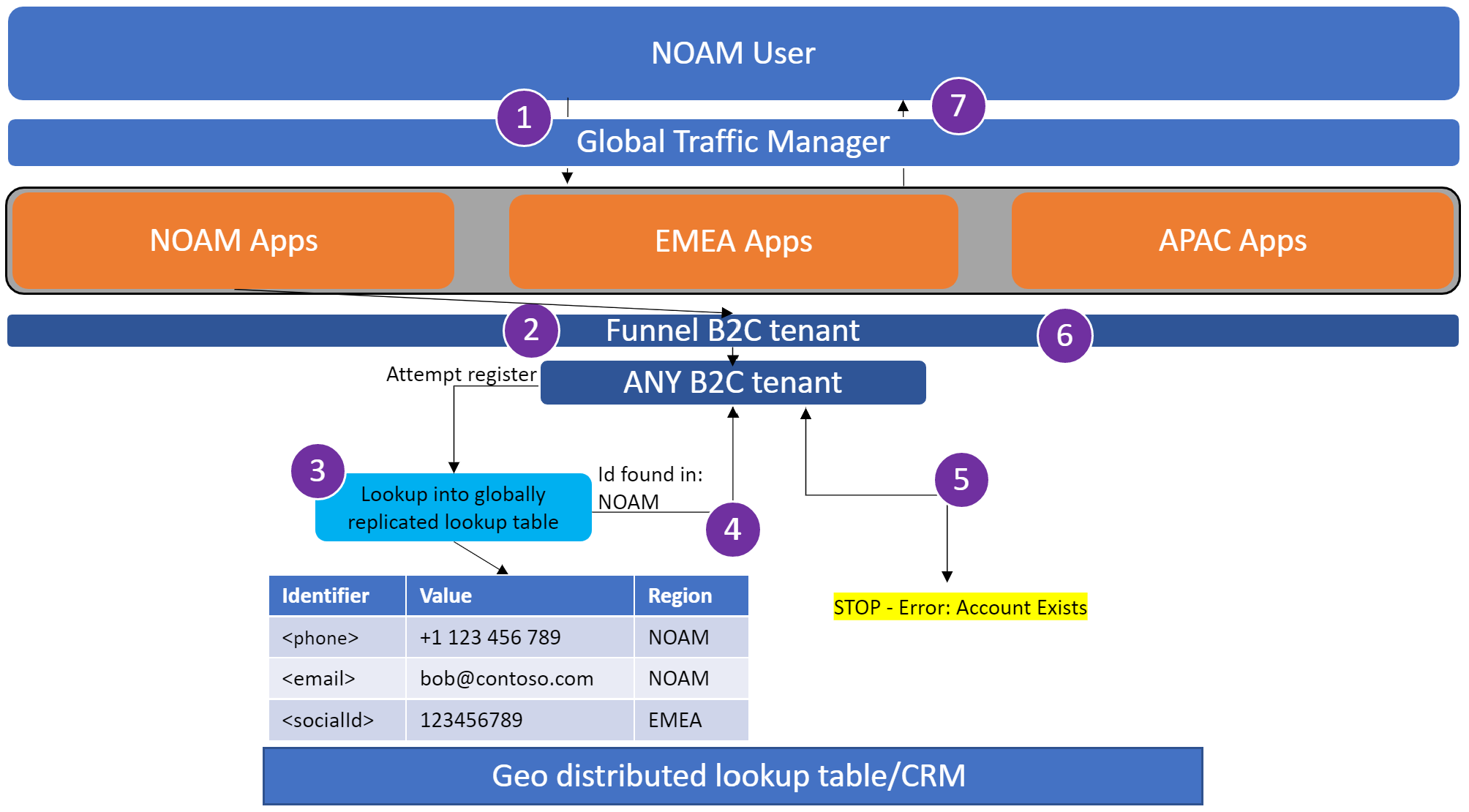
A user from EMEA attempts to sign up at myapp.fr. If the user isn't being sent to their local application instance, the traffic manager enforces a redirect.
The user reaches the Global Funnel Azure AD B2C tenant. This tenant is configured to redirect to a regional Azure AD B2C tenant based on some criteria using OpenId federation. This can be a lookup based on Application clientId.
The user attempts to sign up. The sign-up process checks the global lookup table to determine if the user exists in any of the regional Azure AD B2C tenants.
The user's email is found in the global lookup table, indicating the user has registered this email in the solution at some prior point in time.
The user is presented with an error, indicating their account exists.
Local user sign-in
This use case demonstrates how a user from their home country/region performs a sign-in with an Azure AD B2C local account.
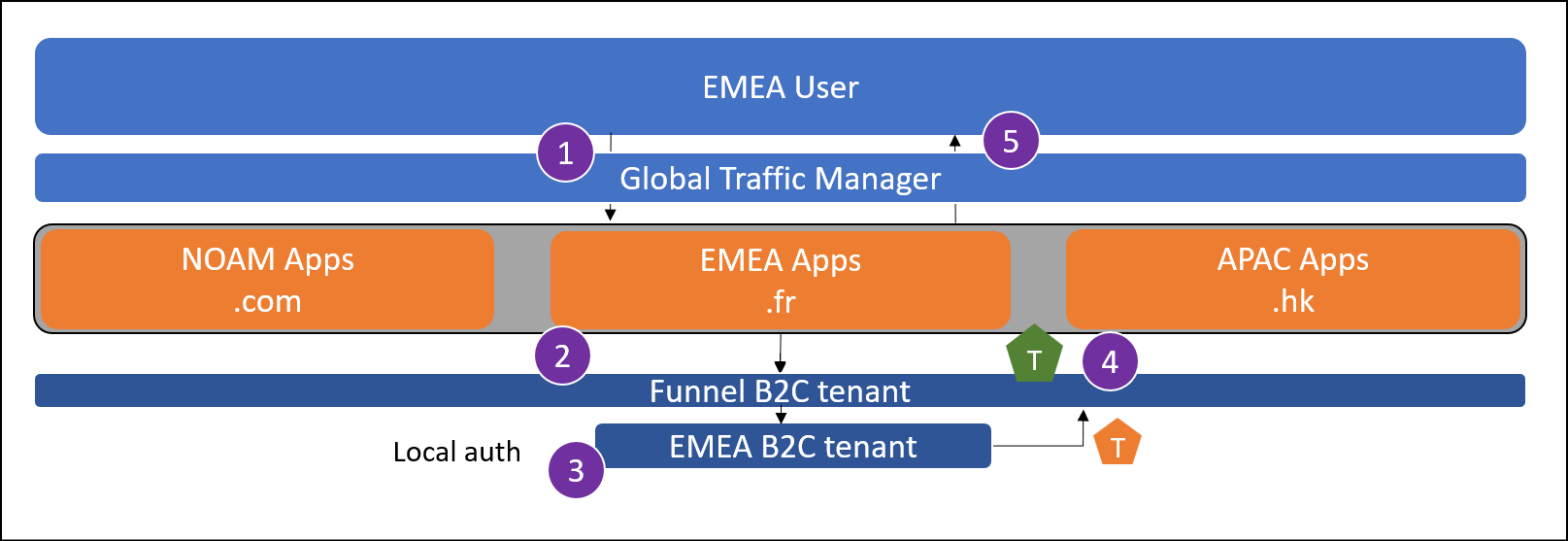
A user from EMEA attempts to sign in at myapp.fr. If the user isn't being sent to their local application instance, the traffic manager enforces a redirect.
The user reaches the global funnel Azure AD B2C tenant. This tenant is configured to redirect to a regional Azure AD B2C tenant based on some criteria using OpenId federation. This can be a lookup based on application clientId.
The user enters their credentials at the regional tenant.
The regional tenant issues a token back to the funnel tenant.
The funnel tenant issues a token to the application.
Traveling user sign-in
This use case demonstrates how a user can travel across regions and maintain their user profile and credentials stored in their regional tenant respective to their sign-up.
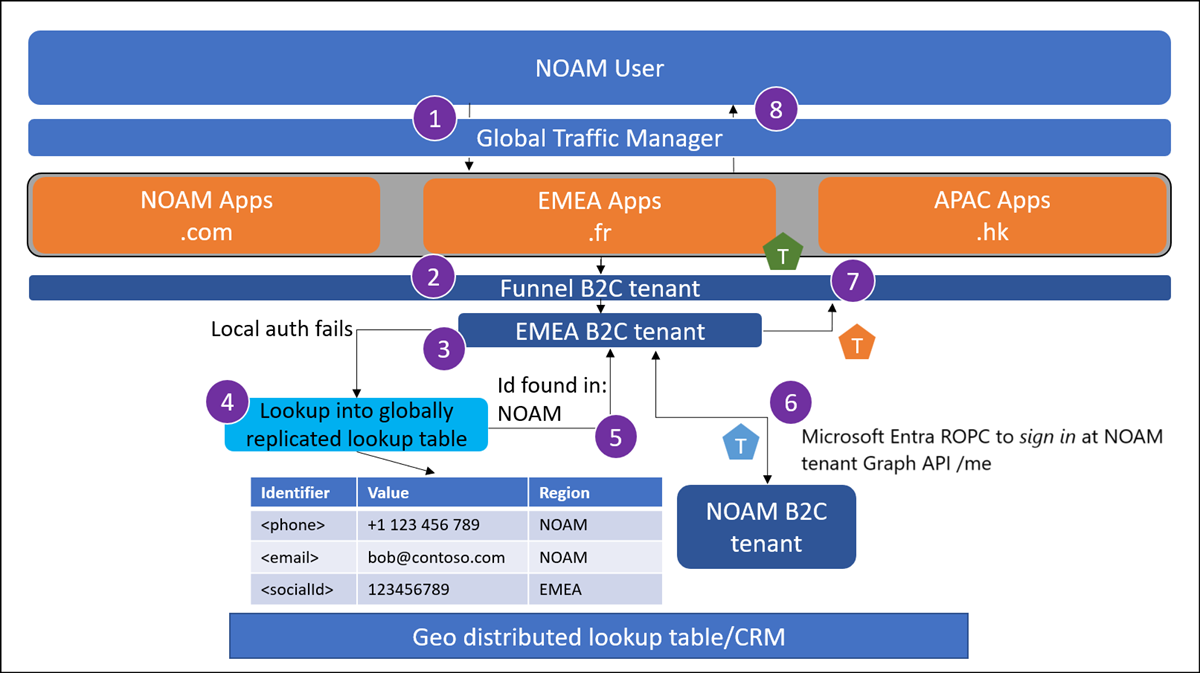
A user from North America (NOAM) attempts to sign in at myapp.fr while they are on holiday in France. If the user isn't being sent to their local application instance, the traffic manager enforces a redirect.
The user reaches the global funnel Azure AD B2C tenant. This tenant is configured to redirect to a regional Azure AD B2C tenant based on some criteria using OpenId federation. This can be a lookup based on Application clientId.
The user enters their credentials at the regional tenant.
The regional tenant performs a lookup into the global lookup table, since the user's email wasn't found in the EMEA Azure AD B2C directory.
The user's email is located to have been signed up in NOAM Azure AD B2C tenant.
The EMEA Azure AD B2C tenant performs a Microsoft Entra ROPC flow against the NOAM Azure AD B2C tenant to verify credentials.
Note
This call will also fetch a token for the user to perform a Graph API call. The EMEA Azure AD B2C tenant performs a Graph API call to the NOAM Azure AD B2C tenant to fetch the user's profile. This call is authenticated by the access token for Graph API acquired in the last step.
The regional tenant issues a token back to the funnel tenant.
The funnel tenant issues a token to the application.
Local user forgot password
This use case demonstrates how a user can reset their password when they are within their home country/region.

A user from EMEA attempts to sign in at myapp.fr. If the user isn't being sent to their local application instance, the traffic manager enforces a redirect.
The user reaches the global funnel Azure AD B2C tenant. This tenant is configured to redirect to a regional Azure AD B2C tenant based on some criteria using OpenId federation. This can be a lookup based on application clientId.
The user arrives at the EMEA Azure AD B2C tenant and selects forgot password. The user enters and verifies their email.
Email lookup is performed to determine which regional tenant the user exists in.
The user provides a new password.
The new password is written into the EMEA Azure AD B2C tenant.
The regional tenant issues a token back to the funnel tenant.
The funnel tenant issues a token to the application.
Traveling user forgot password
This use case demonstrates how a user can reset their password when they're traveling away from the region in which they registered their account.
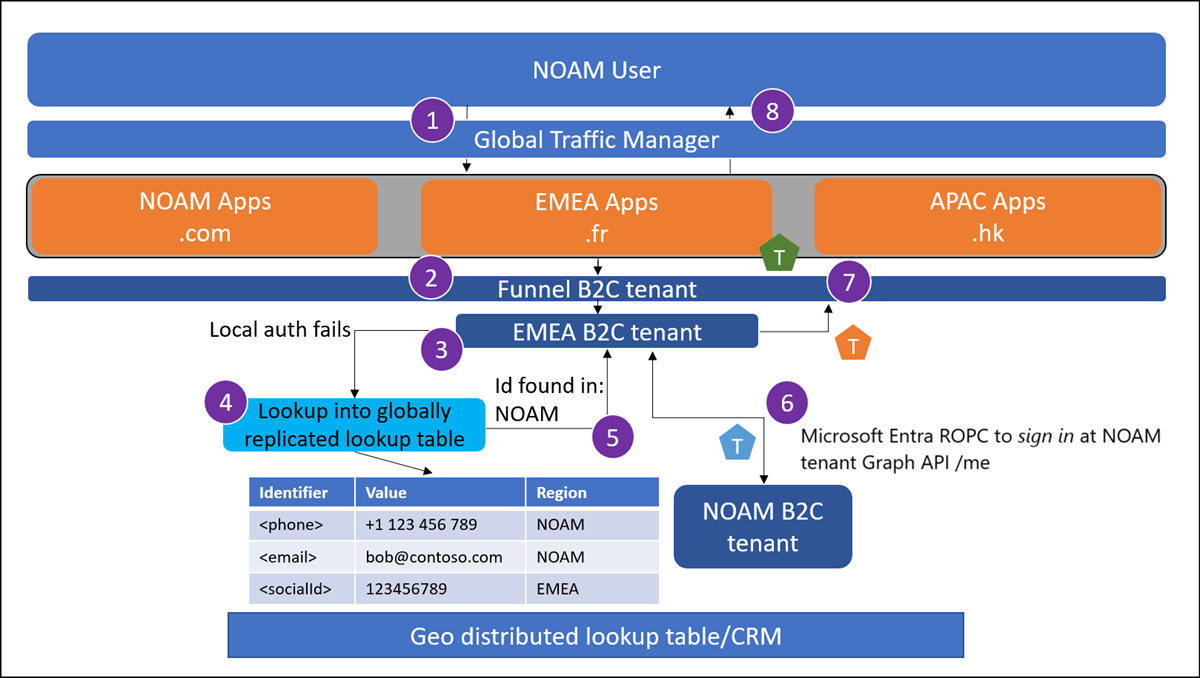
A user from NOAM attempts to sign in at myapp.fr since they are on holiday in France. If the user isn't being sent to their local application instance, the traffic manager enforces a redirect.
The user reaches the global funnel Azure AD B2C tenant. This tenant is configured to redirect to a regional Azure AD B2C tenant based on some criteria using OpenId federation. This can be a lookup based on application clientId.
The user arrives at the EMEA Azure AD B2C tenant and selects forgot password. The user enters and verifies their email.
Email lookup is performed to determine which regional tenant the user exists in.
The email is found to exist in the NOAM Azure AD B2C tenant. The user provides a new password.
The new password is written into the NOAM Azure AD B2C tenant through a Graph API call.
The regional tenant issues a token back to the funnel tenant.
The funnel tenant issues a token to the application.
Local user password change
This use case demonstrates how a user can change their password after they've logged into the region in which they registered their account.
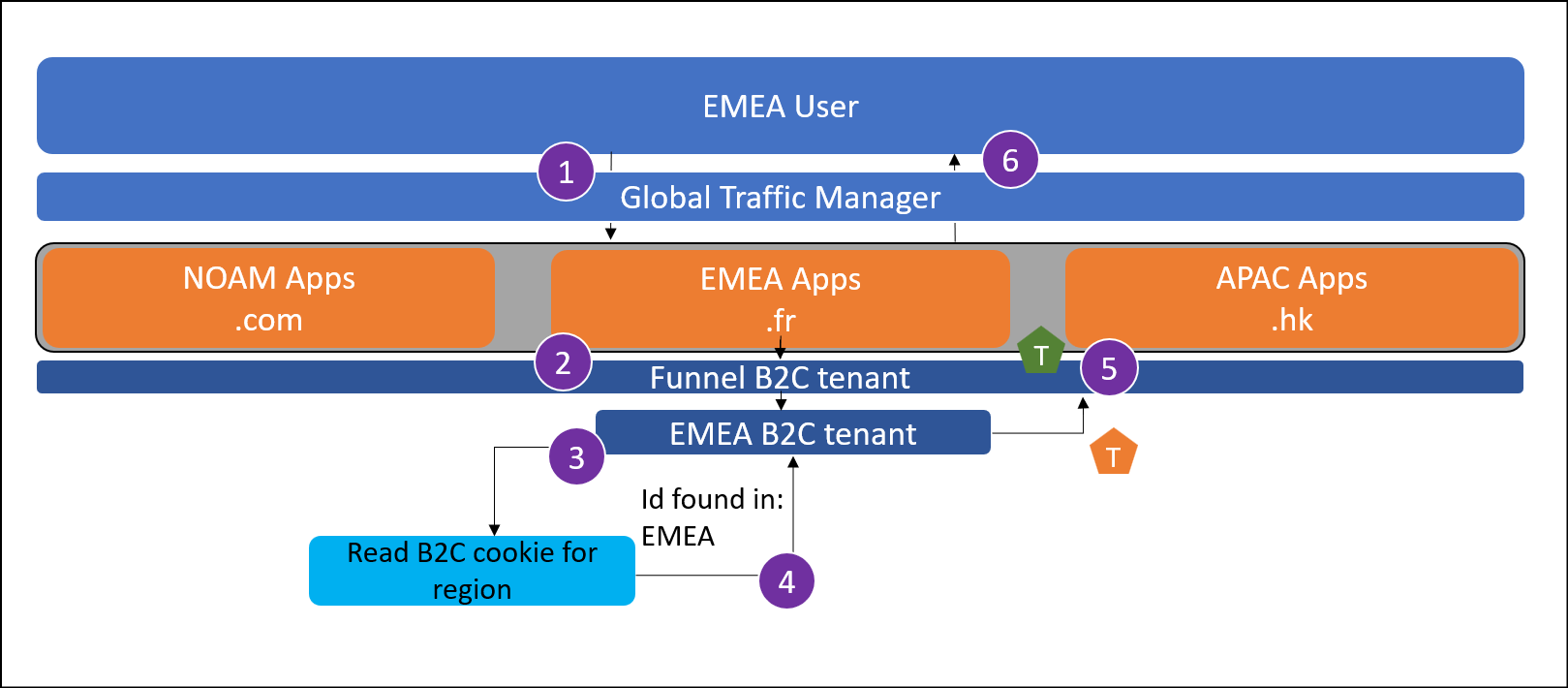
A user from EMEA attempts selects change password after logging into myapp.fr.
The user reaches the global funnel Azure AD B2C tenant. This tenant is configured to redirect to a regional Azure AD B2C tenant based on some criteria using OpenId federation. This can be a lookup based on application clientId.
The user arrives at the EMEA Azure AD B2C tenant, and the Single-Sign On (SSO) cookie set allows the user to change their password immediately.
New password is written to the users account in the EMEA Azure AD B2C tenant.
The regional tenant issues a token back to the funnel tenant.
The funnel tenant issues a token to the application.
Traveling user password change
This use case demonstrates how a user can change their password after they've logged in, away from the region in which they registered their account.
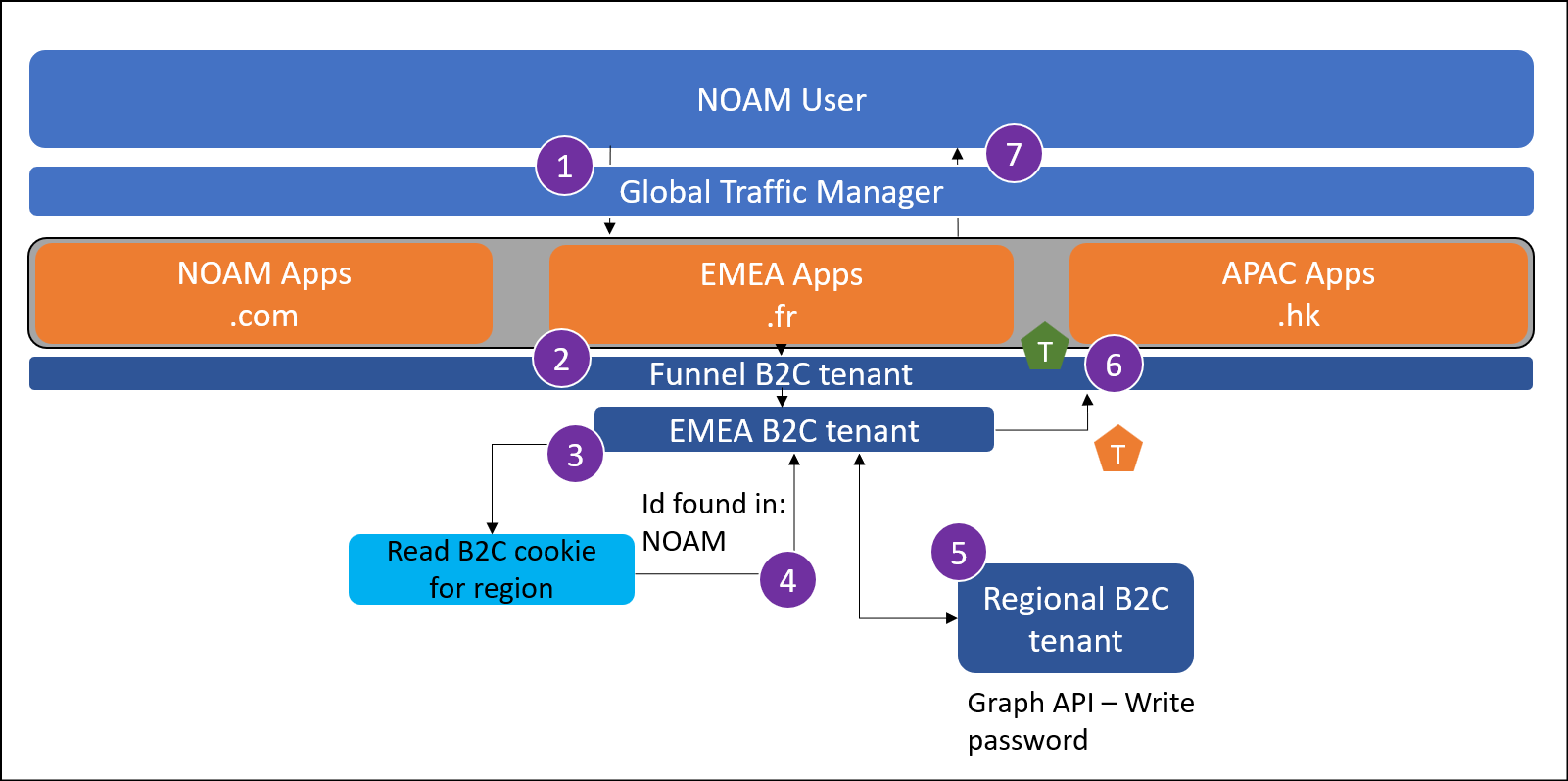
A user from NOAM attempts change password after logging into myapp.fr.
The user reaches the global funnel Azure AD B2C tenant. This tenant is configured to redirect to a regional Azure AD B2C tenant based on some criteria using OpenId federation. This can be a lookup based on application clientId.
The user arrives at the EMEA Azure AD B2C tenant, and the SSO cookie set allows the user to change their password immediately.
The user's email is found to be in the NOAM tenant after checking the global lookup table.
The new password is written to the users account in the NOAM Azure AD B2C tenant by MS Graph API call.
The regional tenant issues a token back to the funnel tenant.
The funnel tenant issues a token to the application.
Federated Identity Provider authentications
The following use cases show examples of using federated identities to sign up or sign in as an Azure AD B2C client.
Local federated ID sign-up
This use case demonstrates how a user can sign up to the service from their local region using a federated ID.
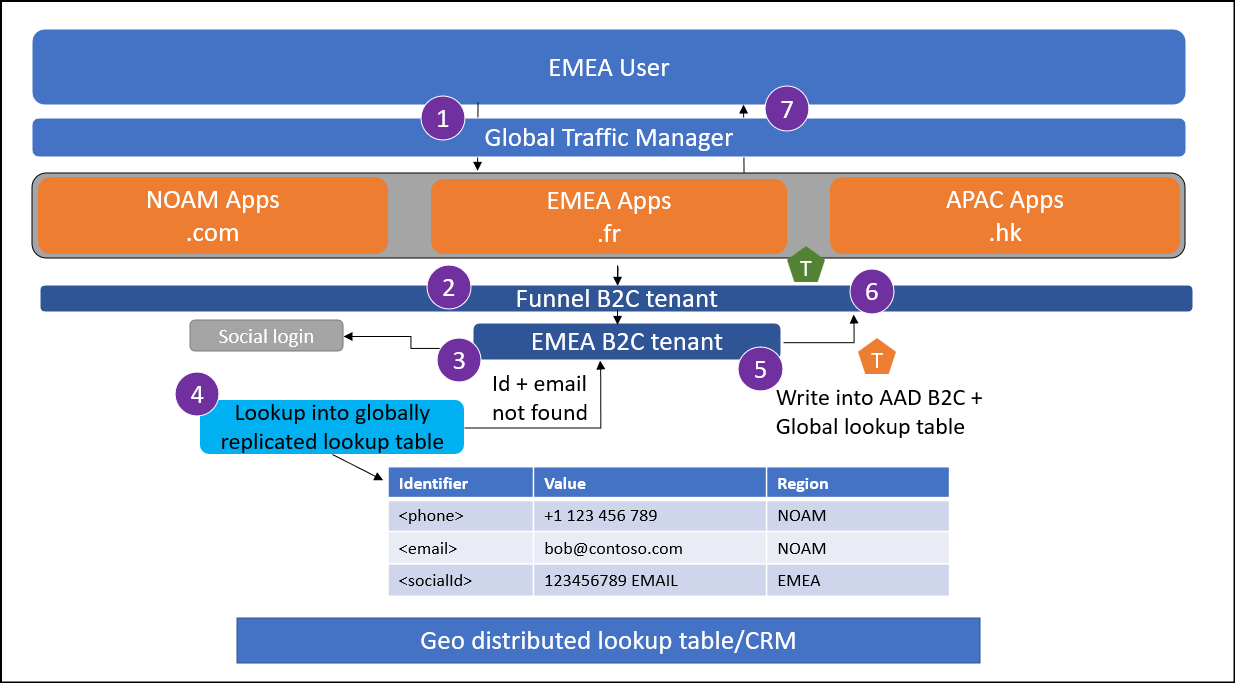
A user from EMEA attempts to sign up at myapp.fr. If the user isn't being sent to their local application instance, the traffic manager enforces a redirect.
The user reaches the global funnel Azure AD B2C tenant. This tenant is configured to redirect to a regional Azure AD B2C tenant based on some criteria using OpenId federation. This can be a lookup based on application clientId.
The user selects to sign in with a federated Identity Provider (IdP).
Perform a lookup into the global lookup table.
If account linking is in scope: Proceed if the federated IdP identifier nor the email that came back from the federated IdP doesn't exist in the lookup table.
If account linking is not in scope: Proceed if the federated IdP identifier that came back from the federated IdP doesn't exist in the lookup table.
Write the users account to the EMEA Azure AD B2C tenant.
The regional tenant issues a token back to the funnel tenant.
The funnel tenant issues a token to the application.
Local federated user sign-in
This use case demonstrates how a user from their local region signs into the service using a federated ID.
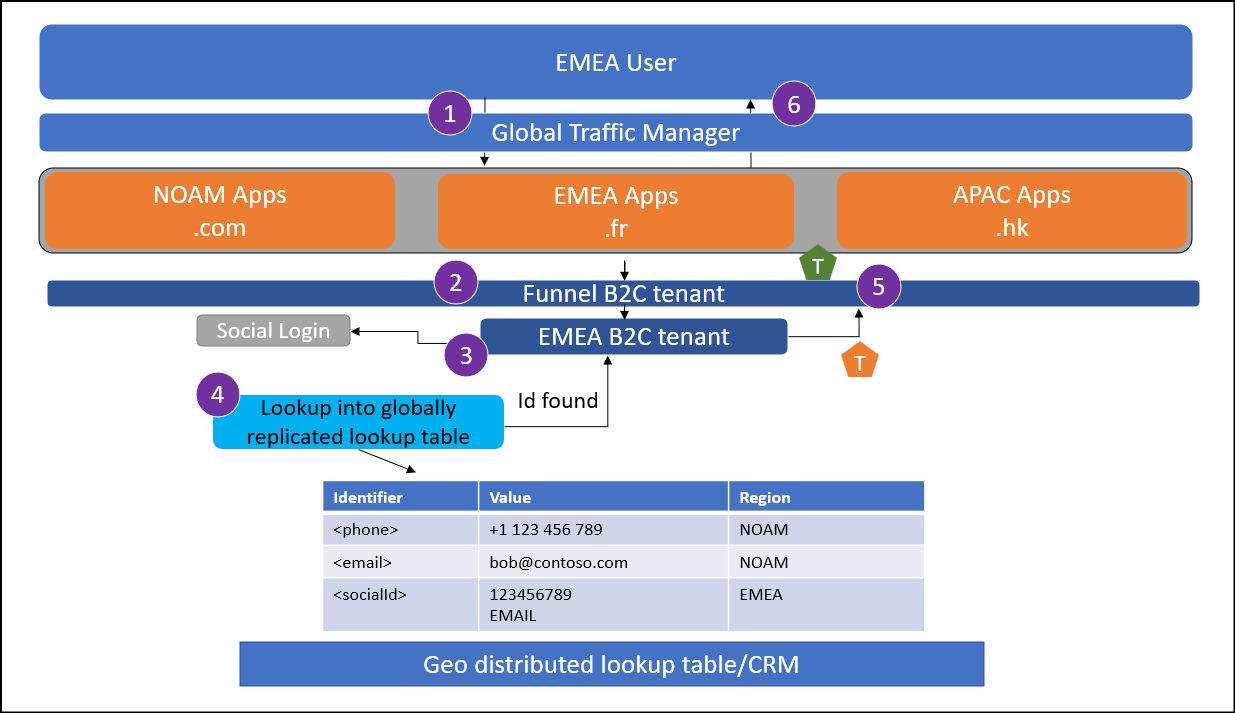
A user from EMEA attempts to sign in at myapp.fr. If the user isn't being sent to their local application instance, the traffic manager enforces a redirect.
The user reaches the global funnel Azure AD B2C tenant. This tenant is configured to redirect to a regional Azure AD B2C tenant based on some criteria using OpenId federation. This can be a lookup based on Application clientId.
The user selects to sign in with a federated identity provider.
Perform a lookup into the global lookup table and confirm the user's federated ID is registered in EMEA.
The regional tenant issues a token back to the funnel tenant.
The funnel tenant issues a token to the application.
Traveling federated user sign-in
This use case demonstrates how a user can sign into their account with a federated IdP, whilst located away from the region in which they signed up in.
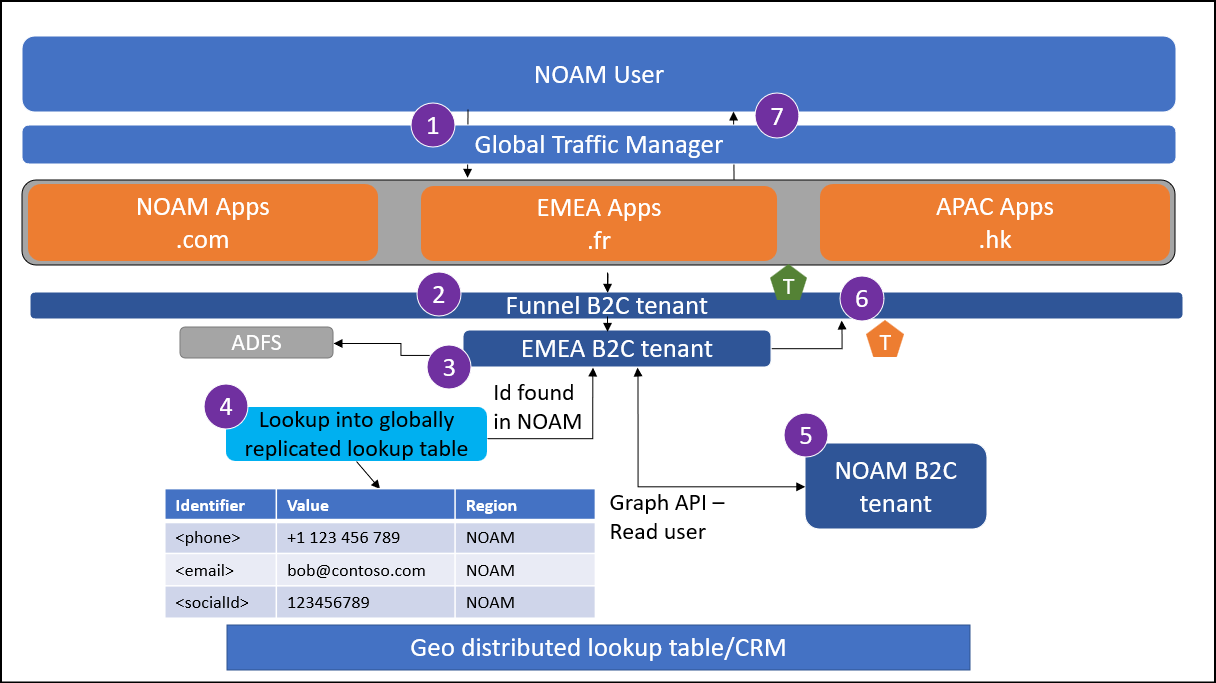
A user from NOAM attempts to sign in at myapp.fr. If the user isn't being sent to their local application instance, the traffic manager enforces a redirect.
The user reaches the global funnel Azure AD B2C tenant. This tenant is configured to redirect to a regional Azure AD B2C tenant based on some criteria using OpenId federation. This can be a lookup based on Application clientId.
The user selects to sign in with a federated identity provider.
Note
Use the same App Id from the App Registration at the Social IdP across all Azure AD B2C regional tenants. This ensures that the ID coming back from the Social IdP is always the same.
Perform a lookup into the global lookup table and determine the user's federated ID is registered in NOAM.
Read the account data from the NOAM Azure AD B2C tenant using MS Graph API.
The regional tenant issues a token back to the funnel tenant.
The funnel tenant issues a token to the application.
Account linking with matching criteria
This use case demonstrates how users are able to perform account linking when matching criteria is satisfied. The matching criteria is typically the users email address. When the matching criteria of a sign in from a new identity provider has the same value for an existing account in Azure AD B2C, the account linking process can begin.
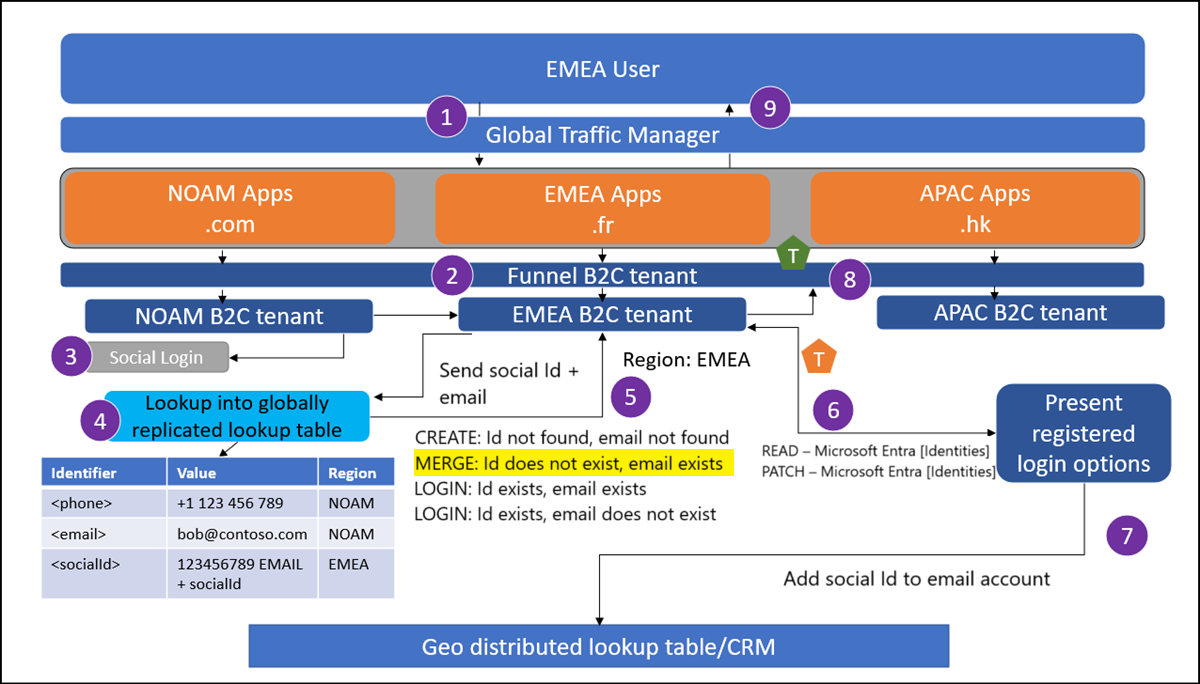
A user from EMEA attempts to sign in at myapp.fr. If the user isn't being sent to their local application instance, the traffic manager enforces a redirect.
The user reaches the global funnel Azure AD B2C tenant. This tenant is configured to redirect to a regional Azure AD B2C tenant based on some criteria using OpenId federation. This can be a lookup based on Application clientId.
The user selects to sign in with a federated identity provider/social IdP.
A lookup is performed into the global lookup table for the ID returned from the federated IdP.
Where the ID doesn't exist, but the email from the federated IdP does exist in EMEA Azure AD B2C – this is an account linking use case.
Read the user from the directory and determine which authentication methods are enabled on the account. Present a screen for the user to sign in with an existing authentication method on this account.
Once the user proves they own the account in Azure AD B2C, add the new social ID to the existing account, and add the social ID to the account in the global lookup table.
The regional tenant issues a token back to the funnel tenant.
The funnel tenant issues a token to the application.
Traveling user account linking with matching criteria
This use case demonstrates how nonlocal users are able to perform account linking when matching criteria is satisfied. The matching criteria is typically the users email address. When the matching criteria of a sign in from a new identity provider has the same value for an existing account in Azure AD B2C, the account linking process can begin.
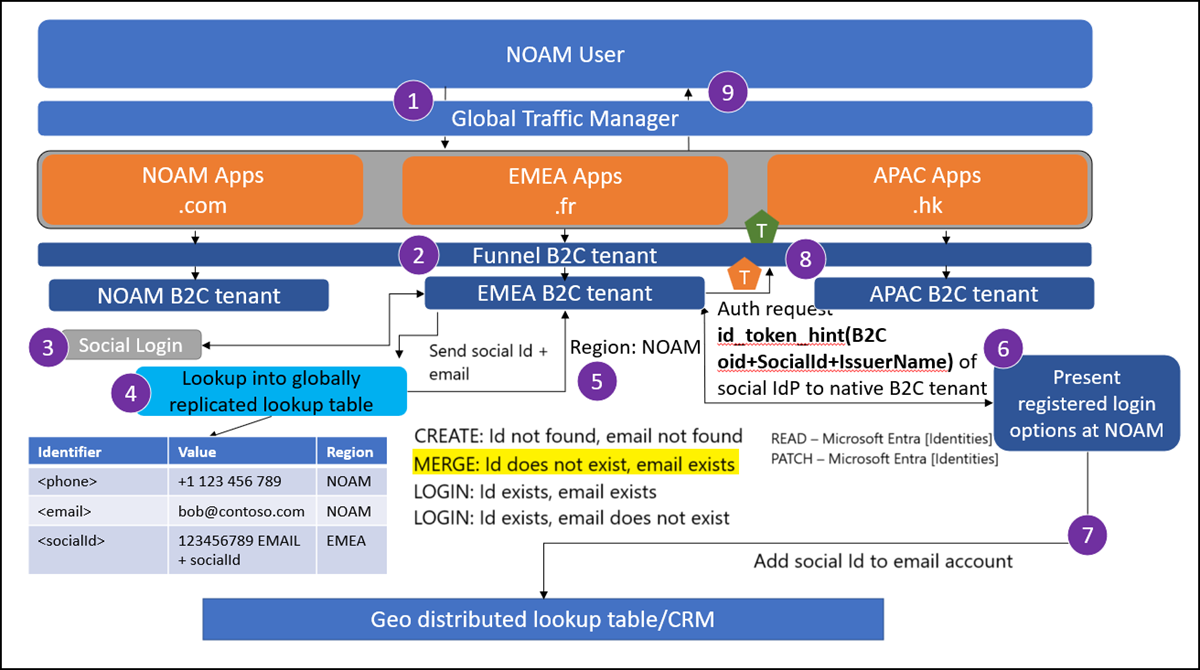
A user from NOAM attempts to sign in at myapp.fr. If the user isn't being sent to their local application instance, the traffic manager enforces a redirect.
The user reaches the Global Funnel Azure AD B2C tenant. This tenant is configured to redirect to a regional Azure AD B2C tenant based on some criteria using OpenId federation. This can be a lookup based on Application clientId.
The user selects to sign in with a federated identity provider/social IdP.
A lookup is performed into the global lookup table for the ID returned from the federated IdP.
Where the ID doesn't exist, and the email from the federated IdP exists in another region - this is a traveling user account linking use case.
Create an id_token_hint link asserting the users currently collected claims. Bootstrap a journey into the NOAM Azure AD B2C tenant using federation. The user proves that they own the account via the NOAM Azure AD B2C tenant.
Note
This method is used to re-use existing account linking logic in the home tenant and reduce external API calls to manipulate the identities collection. A custom policy sample which utilizes id_token_hint can be found here.
Once the user proves they own the account in Azure AD B2C, add the new social ID to the existing account by making a Graph API call to the NOAM Azure AD B2C tenant. Add the social ID to the account in the global lookup table.
The regional tenant issues a token back to the funnel tenant.
The funnel tenant issues a token to the application.