Configure Azure Active Directory B2C with Akamai Web Application Protector
Learn to enable Akamai Web Application Protector (WAP) for Azure Active Directory B2C (Azure AD B2C) tenant using custom domains. Akamai WAP helps organization protect their web applications from malicious attacks that aim to exploit vulnerabilities such as SQL injection and Cross site scripting.
Learn more on akamai.com: What Is a Web Application Firewall (WAF)?
Benefits of using WAF:
- Control traffic management to your services
- Configure in front of an Azure AD B2C tenant
- Manipulate traffic to protect and secure your identity infrastructure
This article applies to:
WAP: Web Application Protector KSD: Kona Site Defender
Prerequisites
- An Azure subscription
- If you don't have one, get an Azure free account
- An Azure AD B2C tenant linked to your Azure subscription
- An Akamai WAP account
- Go to akamai.com for Explore all Akamai products and trials
Scenario description
Akamai WAP integration includes the following components:
- Azure AD B2C – the authorization server that verifies user credentials with custom policies in the tenant. Also known as the identity provider (IdP).
- Azure Front Door – enables custom domains for the Azure B2C tenant
- Traffic from Akamai WAP routs to Azure Front Door then goes to the Azure AD B2C tenant
- What is Azure Front Door?
- Akamai WAP – The web application firewall that manages traffic sent to the authorization server
Integrate with Azure AD B2C
For custom domains in Azure AD B2C, use the custom domain feature in Azure Front Door.
See, Enable custom domains for Azure AD B2C.
When the custom domain for Azure AD B2C is configured using Azure Front Door, use the following instructions to test the custom domain.
See, Test your custom domain, then proceed to the next section.
Create an Akamai account
- Go to akamai.com.
- Select Learn more.
- On the Cloud Computing Services page, select Create account.
Create and configure a property
A property is a configuration file that tells our edge servers how to handle and respond to incoming requests from your end users. Properties are created and maintained in Property Manager.
To learn more, go to techdocs.akamai.com for What is a Property?
- Go to control.akamai.com to sign in: Akamai Control Center sign in page.
- Go to Property Manager.
- For Property version, select Standard or Enhanced TLS (recommended).
- For Property hostnames, add a property hostname, your custom domain. For example,
login.domain.com.
Important
Create or modify certificates with correct custom domain name settings.
Go to techdocs.akamai.com for Configure HTTPS hostnames.
Origin server property configuration settings
Use the following settings for origin server.
- For Origin type, enter your type.
- For Origin server hostname enter your hostname. For example,
yourafddomain.azurefd.net - For Forward host header, use Incoming Host Header.
- For Cache key hostname use Incoming Host Header.
Configure DNS
Create a Canonical Name (CNAME) record in your DNS, such as login.domain.com, which points to the Edge hostname in the Property hostname field.
Configure Akamai WAP
To get started with WAP configuration, go to techdocs.akamai.com for App & API Protector.
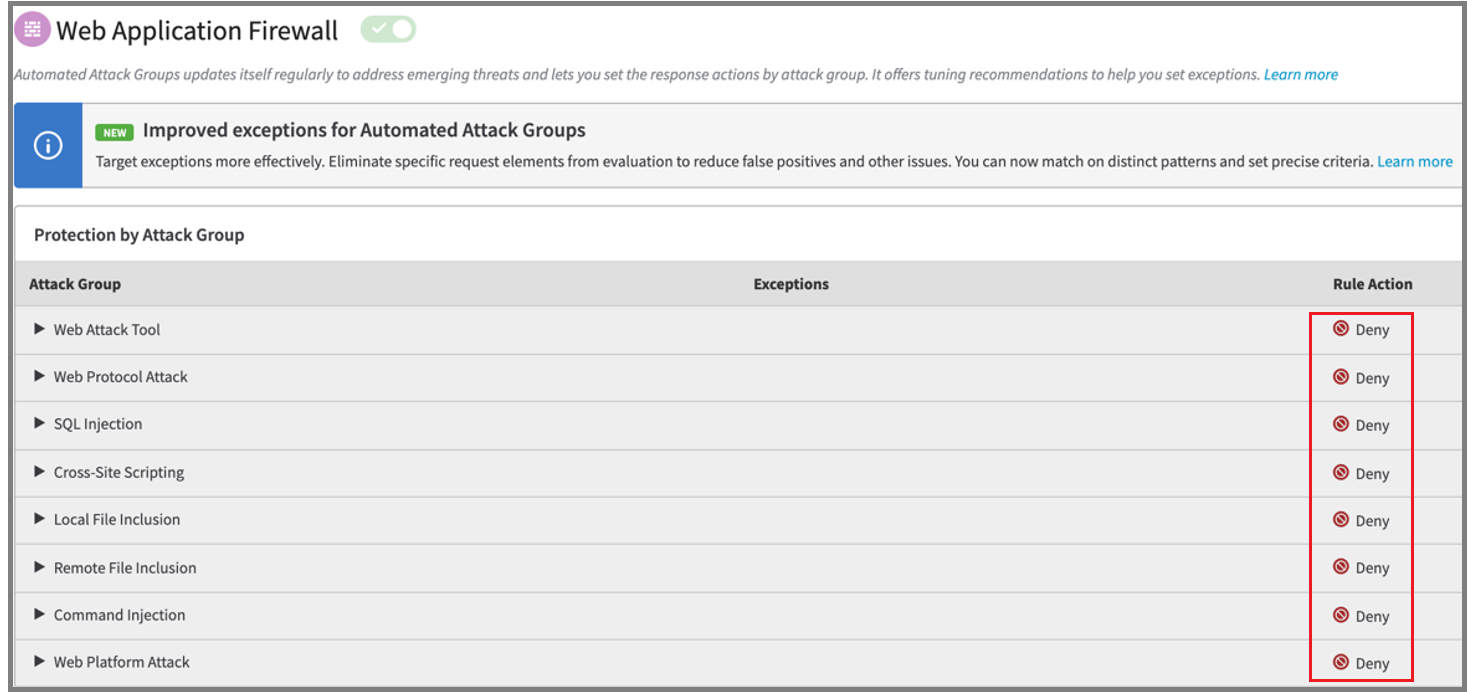
During configuration, for items in Attack Group, under Rule Actions, select Deny.
Test the settings
To ensure traffic to Azure AD B2C goes through the custom domain:
- Confirm WAP routes incoming requests to the Azure AD B2C custom domain
- Ensure a valid TLS connection
- Ensure Azure AD B2C sets cookies correctly for the custom domain
- The WAP dashboard in Defender for Cloud console has WAP traffic charts
- Attack traffic also appears